Network flow analysis and file extraction system and method
A network traffic and extraction method technology, applied in the field of network traffic analysis and file extraction, can solve the problems of control, inability to identify fine-grained, malicious traffic, etc., and achieve the effect of preventing network intrusion attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] The present invention will be further explained below in conjunction with the accompanying drawings and specific embodiments.
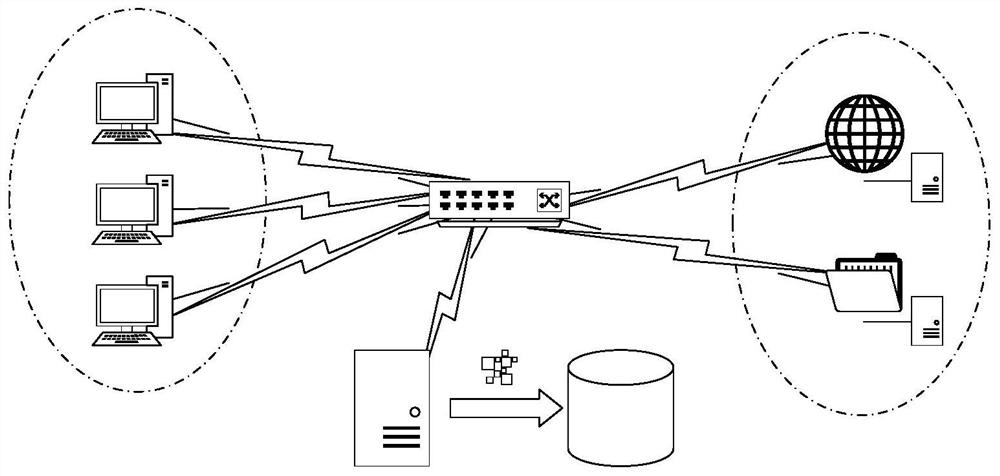
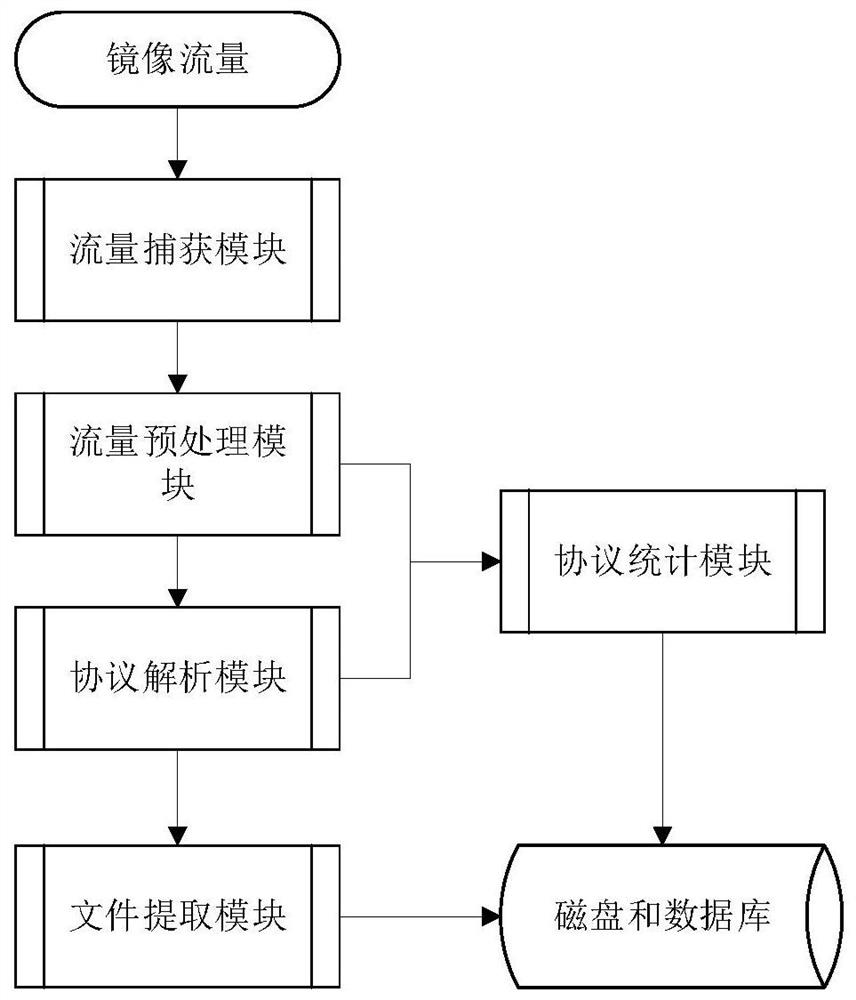
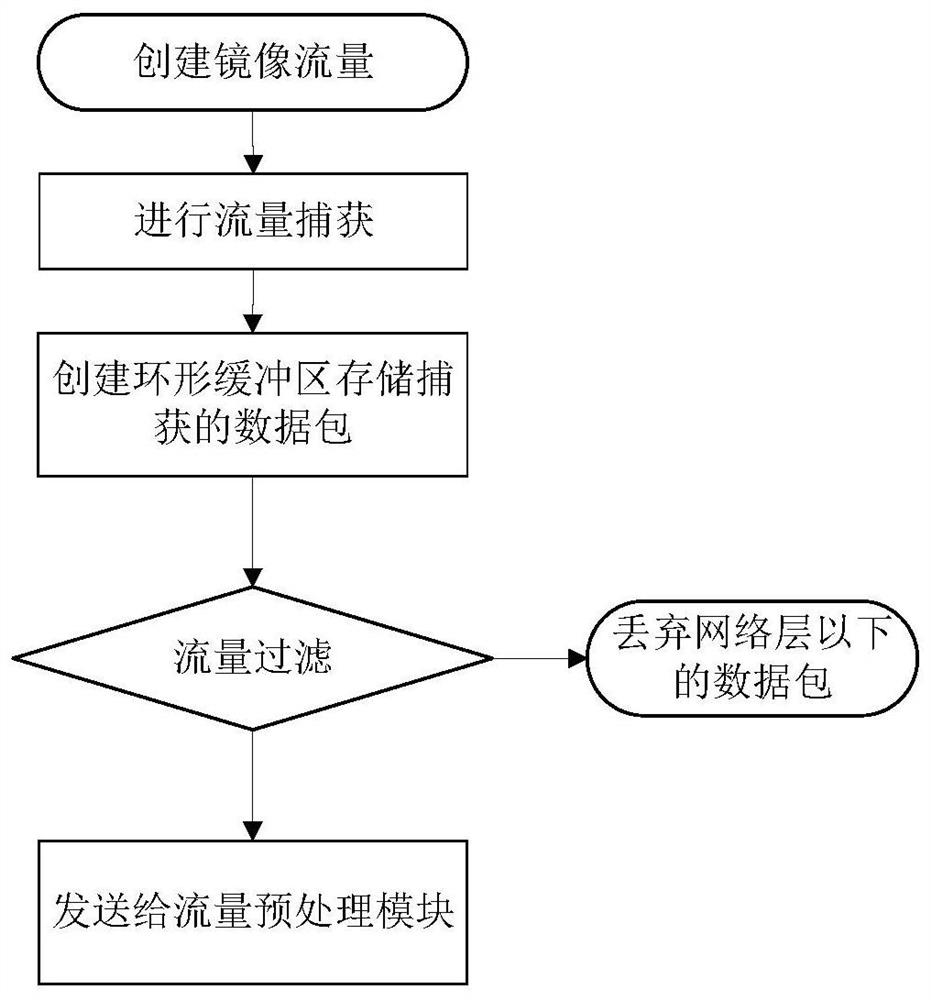
[0070] Such as figure 1 Shown: The left side is the company intranet, which contains multiple computer devices, and the right side is the public network server, including various web servers, content servers, mail servers, etc. Between the company intranet and the public network server, a network switch is often used as a communication interface, thereby effectively isolating the intranet and the extranet for access control. The deployment scheme of the embodiment of the present invention is: the method of creating mirrored traffic on the network switch, and the mirrored traffic includes the data content of the two-way communication between the company's intranet and the public network. Then transmit the mirrored traffic to the device for traffic analysis, complete the traffic analysis in this device, and write the results to the database and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com