Configuration method for generating multiple honeypot nodes by single host based on linux system, system and monitoring method
A configuration method and single-host technology, applied in transmission systems, platform integrity maintenance, electrical components, etc., can solve the problem of low camouflage, and achieve the effect of improving camouflage and saving resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
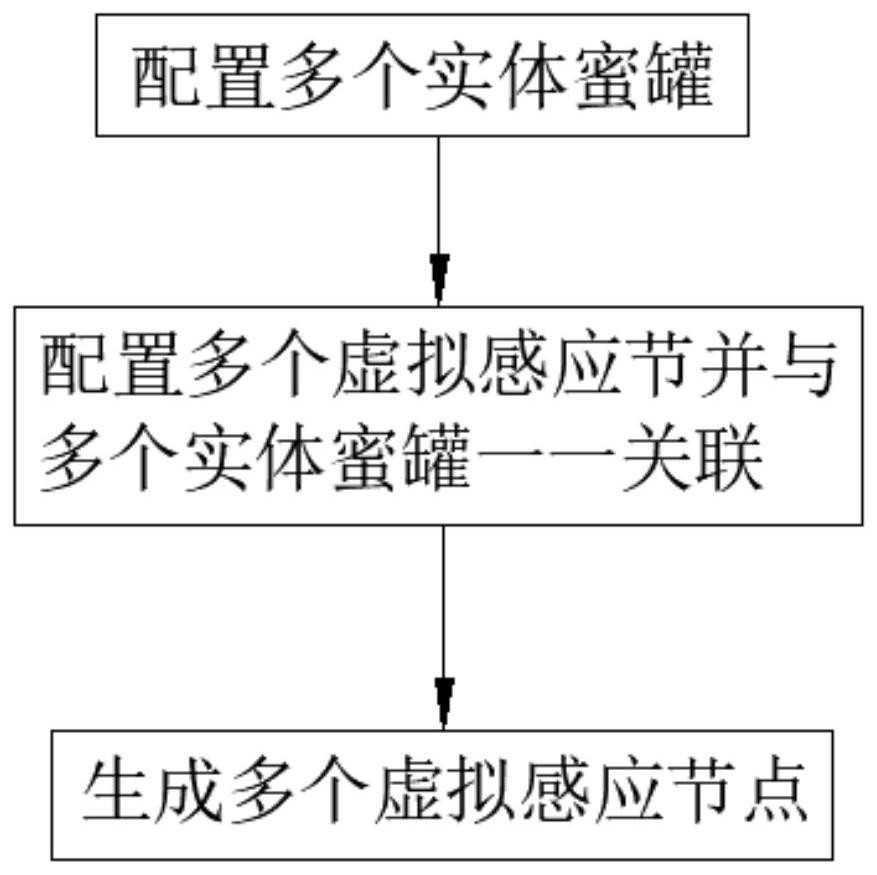
[0034] like figure 1 As shown, a single host based on linux system generates a configuration method for multiple honeypot nodes, including the following steps:
[0035] S01. Using Linux container virtualization technology, deploy multiple physical honeypots with interactive functions in the current host, each physical honeypot has an independent IP and Mac address;
[0036] S02. According to the IP information of the host where the entity honeypot is located, configure multiple virtual sensing nodes with different IP addresses on the same network segment and port opening and association policies, and configure open ports and association policies for each sensing node at the same time. The port of the sensor node is associated with the corresponding entity honeypot service; The virtual sensor node configuration list information includes: IP address, Mac address, gateway, subnet mask; The configuration information of the port opening and association strategy includes virtual Th...
Embodiment 2
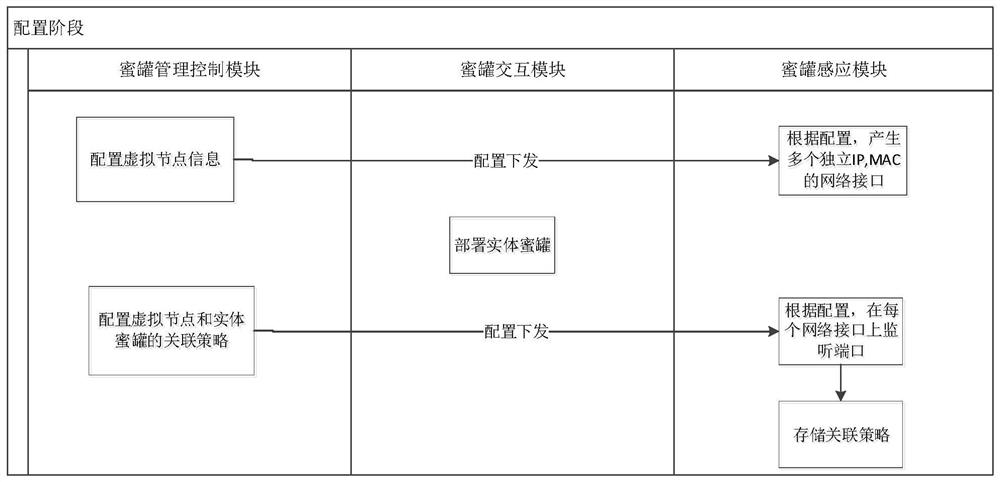
[0040] like figure 2 As shown, corresponding to Embodiment 1, this embodiment provides a honeypot system based on a linux system, which is characterized in that it includes
[0041] The honeypot response module uses Linux container virtualization technology to deploy multiple physical honeypots with interactive functions in the current host;
[0042]The honeypot management control module, according to the IP information of the host where the entity honeypot is located, configures multiple virtual sensing nodes with different IP addresses on the same network segment and port opening and association policies, and at the same time links the port of each virtual sensing node to the corresponding entity The honeypot is associated; the virtual sensing node configuration list information includes: IP address, Mac address, gateway, subnet mask. The configuration information of the port opening and association strategy includes the IP address and port of the virtual sensor node, and ...
Embodiment 3
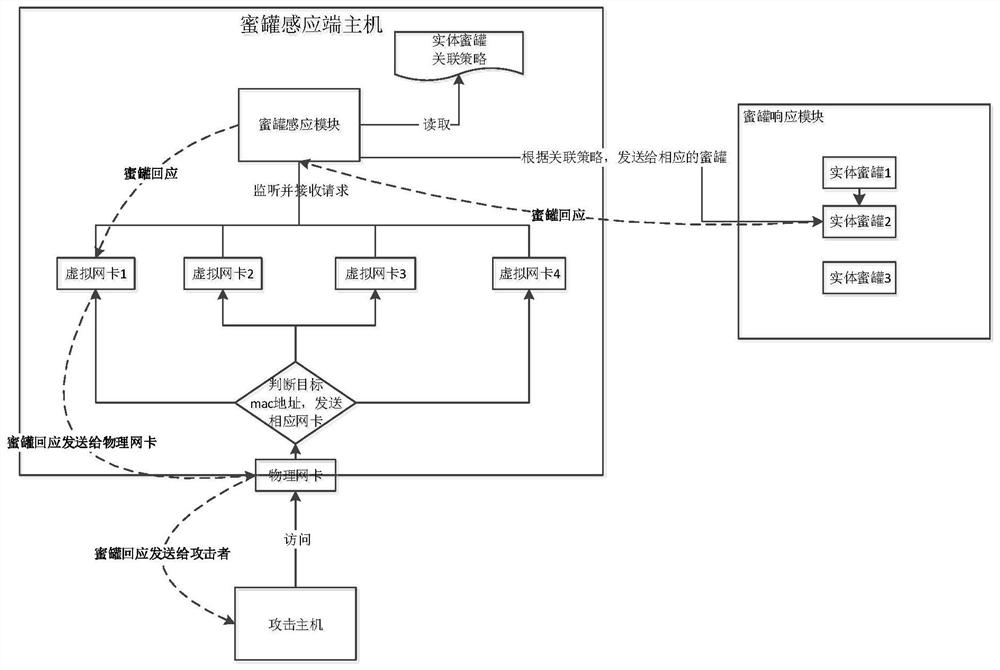
[0052] like image 3 As shown, corresponding to Embodiment 1 and Embodiment 2, this embodiment provides a monitoring method for a honeypot system based on a linux system, comprising the following steps:
[0053] S1. When an attacker accesses a virtual sensor node, the physical network card where the current host is located receives the network packet; the physical network card judges the Mac address in the request traffic packet, and if it matches a virtual network card of the current host, the traffic packet is sent to the corresponding virtual network card;
[0054] S2. The honeypot sensing module tries to monitor each virtual network card. After monitoring the traffic of the virtual network card, read the port opening and association policies of the virtual sensing node and the entity honeypot in the cache, find the address of the corresponding entity honeypot in the honeypot response module, and then forward the request traffic to the honeypot In the corresponding entity...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com