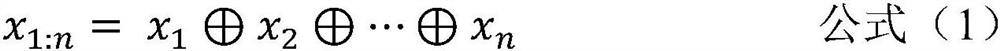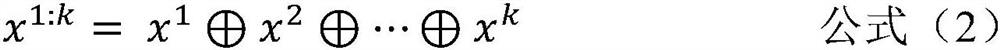Online service anomaly detection method based on log semantic analysis
An anomaly detection and semantic analysis technology, applied in semantic analysis, natural language data processing, text database clustering/classification, etc., can solve problems such as difficult parameters, difficult representation, and complex models
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
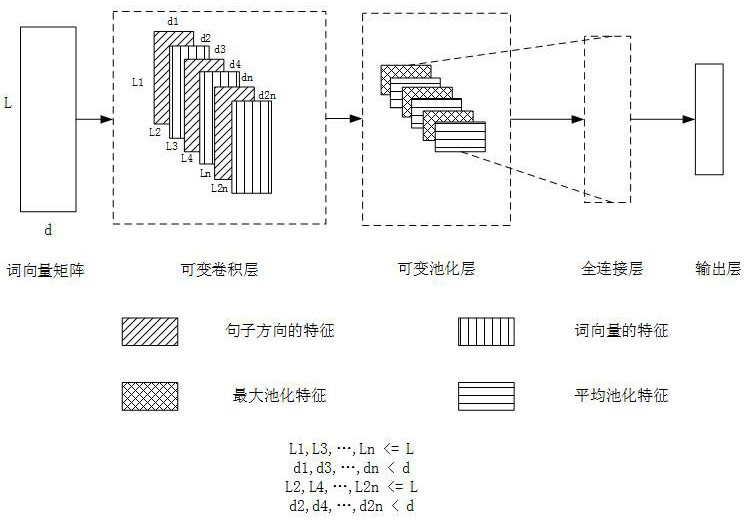
[0106] The present invention will be further described below in conjunction with accompanying drawing, please refer to figure 1 ;
[0107] figure 1 It is the VCNN mechanism. As shown in the figure, the VCNN of the present invention can be divided into three layers. Since the structure of VCNN is similar to TextCNN, the two differ only in the convolutional and pooling layers. Therefore, the present invention only introduces the convolutional and pooling layers of the improved network structure.
[0108] Suppose the input matrix of the convolutional layer is x∈R n×k , where n represents the length of the input sentence and k represents the dimensionality of the word vector. In the direction of sentence length, x i represents the word vector of the i-th word, x i:j Represents the concatenation of word vectors from the i-th word (related to) to the j-th word. The input matrix x can be represented as a concatenation of n word vectors in k dimensions.
[0109] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com