Differential privacy protection clustering method based on K-means
A technology of differential privacy and clustering methods, applied in the field of information security, can solve problems such as slow convergence speed, low level of privacy protection, and high computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings.
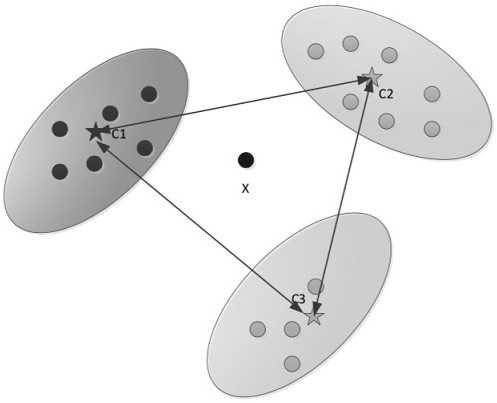
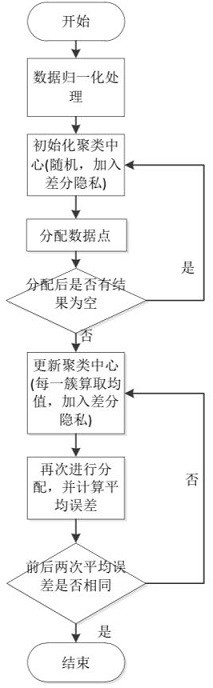
[0030] A differential privacy protection clustering algorithm based on k-means of the present invention, in each iteration process, the upper and lower bounds of the privacy budget are limited by the arithmetic sequence, according to the clustering effect U(ε) and the privacy protection effect V(ε ) to determine the allocation of the privacy budget, which is called the adaptive privacy budget allocation mechanism. When calculating the distance between the data and the center point of the cluster, the calculation time is reduced through the triangle inequality, and the efficiency is improved. The following problems need to be solved: 1. How to solve the adaptive privacy budget allocation to solve the optimal privacy budget, 2. How to solve the differential privacy protection in the process of cluster analysis. The following is divided...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com