Target database construction method, target applicant identification method, target applicant identification device and target applicant identification system
A construction method and the applicant's technology, applied in the field of data processing, can solve problems such as resource waste, tedious manual verification work, and increased search time, and achieve the effects of small system processing capacity, fast judgment process, and improved verification efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
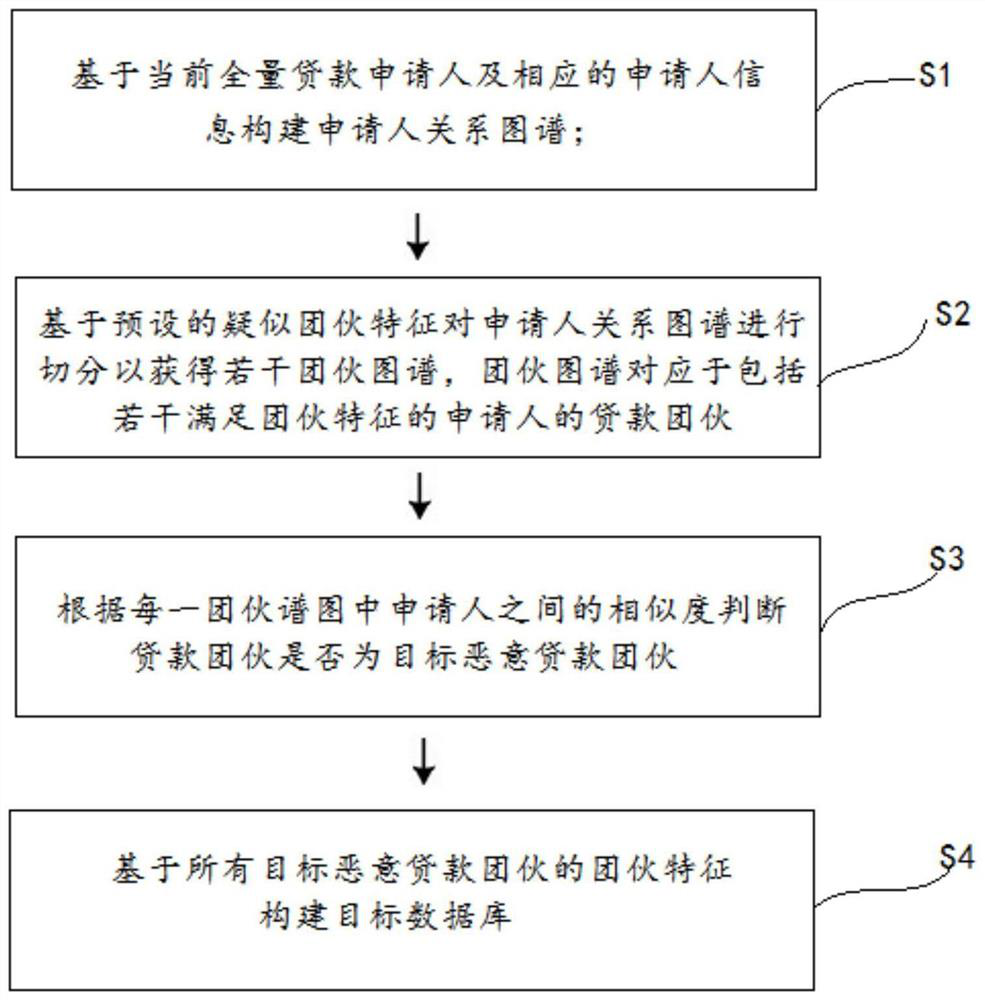
[0063] combine figure 1 As shown, the present embodiment provides a method for constructing a target database, which at least includes the following steps:
[0064] S1. Construct the applicant relationship map based on the current full loan applicants and corresponding applicant information. Specifically, S1 includes the following sub-steps:
[0065] S11. Extract the applicant information of the current full loan applicant;
[0066] S12. Obtain the relationship between any two applicants according to the information of the applicants;
[0067] S13. Taking the applicant as the target node, and the relationship between applicants as the target relationship between the target nodes to construct an applicant relationship graph.
[0068] Specifically, the association relationships in this embodiment include at least suspected fraudulent relationships that can reflect a certain degree of aggregation, such as multiple applicants whose ID numbers come from the same region, the same...
Embodiment 2
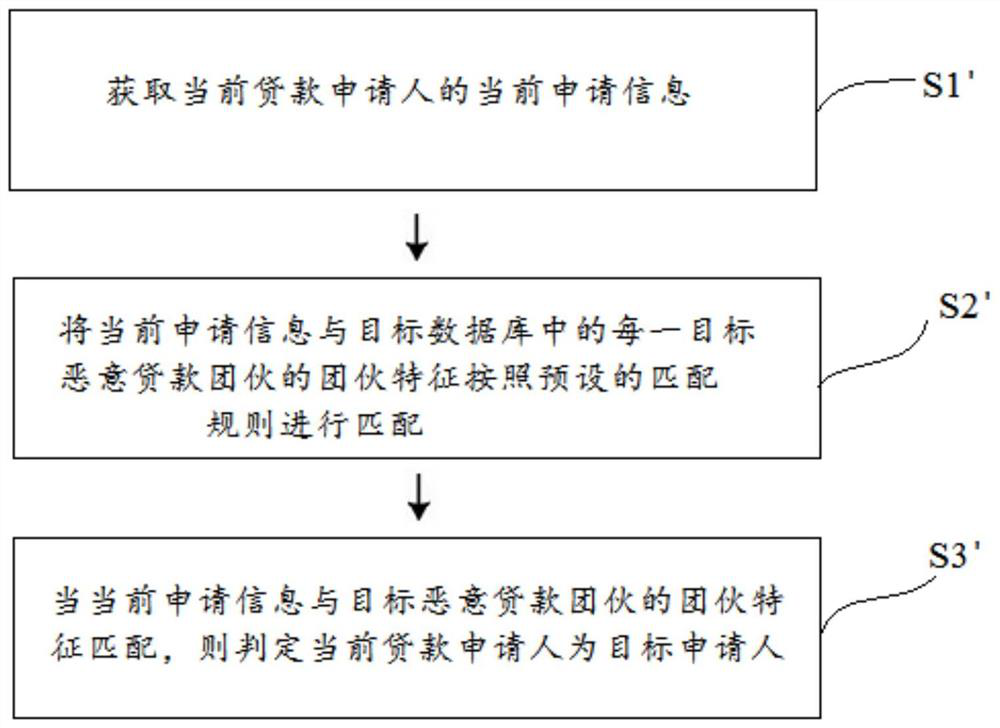
[0101] combine figure 2As shown, this embodiment provides a method for identifying a target applicant, which is implemented based on the target database constructed in Embodiment 1, and at least includes the following steps:
[0102] S1'. Obtain the current application information of the current loan applicant.
[0103] The current application information includes at least one of the structured data and unstructured data in Embodiment 1. The structured data includes at least one of the application area, application address, IP address, application equipment, password, and application page stay time. One: the unstructured data includes at least one of recorded faces, recorded voices, video backgrounds, and audio backgrounds.
[0104] S2'. Match the current application information with the group features of each target malicious lending group in the target database according to preset matching rules.
[0105] Matching rules can be set in a variety of ways, such as including a...
Embodiment 3
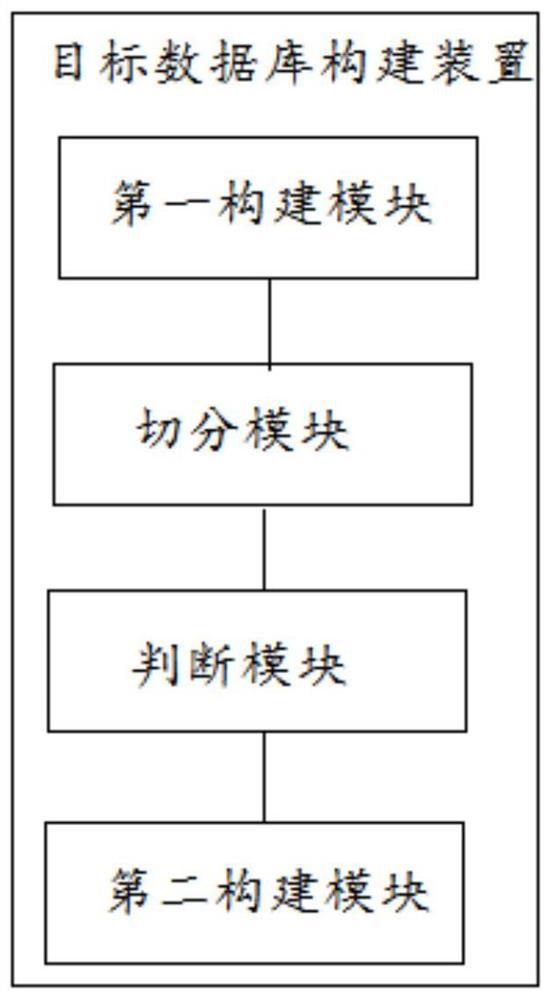
[0111] In order to implement a loan identification method in the first embodiment above, this embodiment provides a corresponding loan identification device, such as image 3 As shown, the device includes at least:
[0112] The first building block is used to construct an applicant relationship graph based on the current full loan applicant and corresponding applicant information. The first building blocks include at least:
[0113] The first extracting unit is used to extract the applicant information of the current full loan applicant;
[0114] An acquisition unit, configured to acquire the association relationship between any two applicants according to the applicant information;
[0115] The first construction unit is configured to use the applicant as a target node, and the association relationship between the applicants is the target relationship between the target nodes to construct an applicant relationship graph.
[0116] The segmentation module is configured to se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com