A software security startup method and system for software for V2X devices
A software security and equipment technology, applied in software deployment, computer security devices, program loading/starting, etc., can solve the problems of malicious modification of Linux system, affecting the normal operation of V2X equipment, implanting illegal applications, etc., to ensure legality and integrity, eliminate potential safety hazards, and ensure the effect of safe operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
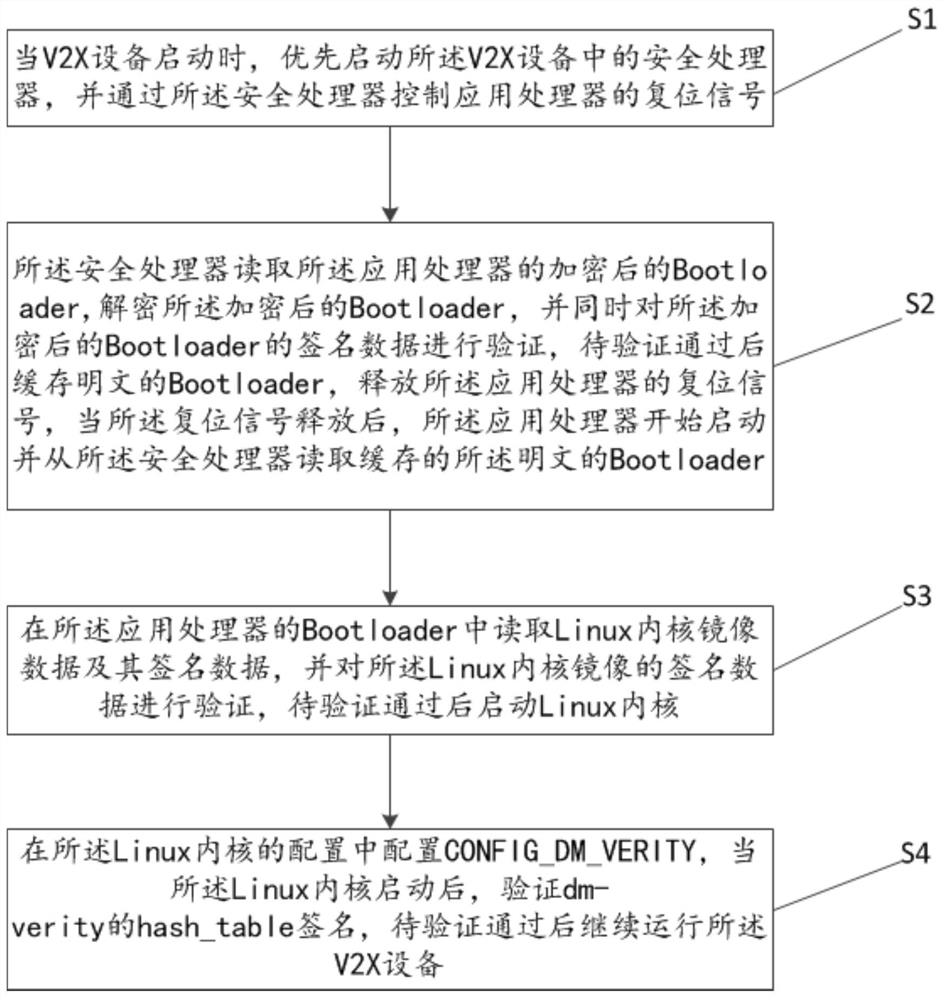
[0052] like figure 1 As shown, this embodiment provides a software security startup method for a V2X device, which is characterized in that it includes the following steps:
[0053] S1: When the V2X device is started, the security processor in the V2X device is started first, and the reset signal of the application processor is controlled by the security processor.
[0054] Specifically, when the V2X device is ready to start, it starts from the security processor first, and controls the reset signal of the application processor through the security processor, so that the application processor cannot be started until the security verification of the security processor is completed.
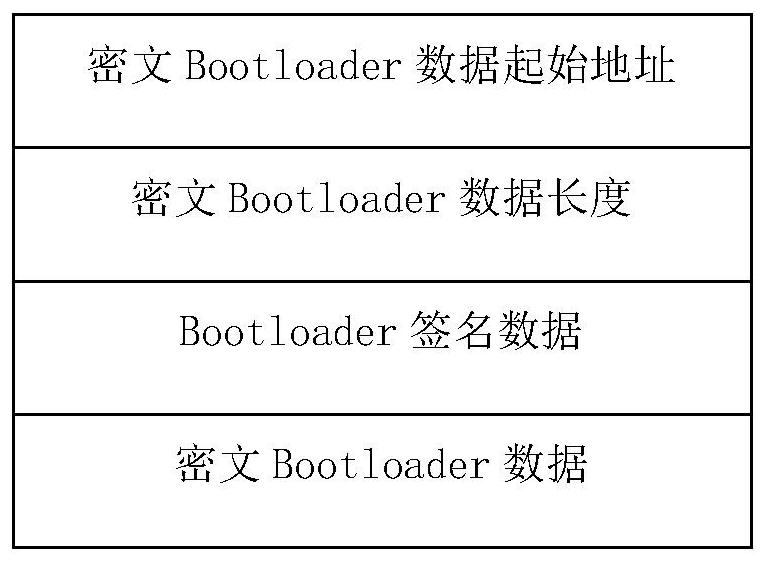
[0055] S2: The security processor reads the encrypted Bootloader of the application processor, decrypts the encrypted Bootloader, and verifies the signature data of the encrypted Bootloader at the same time, and caches the plaintext after the verification is passed. The bootloader releases the res...
no. 2 example
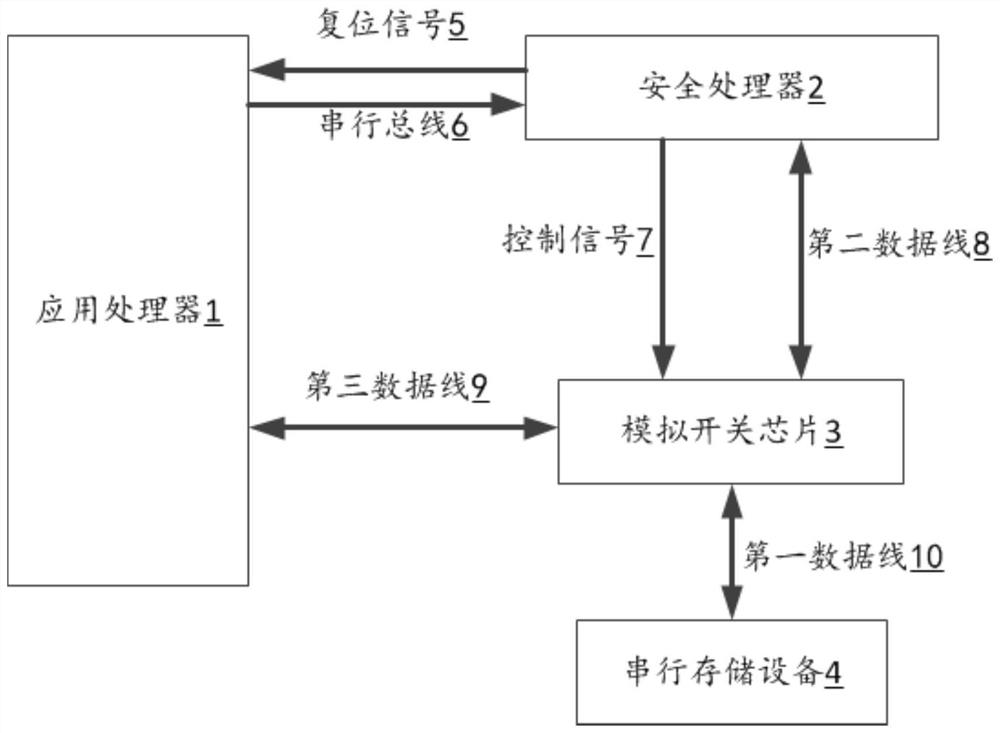
[0076] like Figure 8 As shown, this embodiment provides a corresponding software secure booting system for a V2X device for executing the method in the first embodiment, including:
[0077] The reset signal control module is used to preferentially start the security processor in the V2X device when the V2X device is started, and control the reset signal of the application processor through the security processor.
[0078] Bootloader signature verification module is used to provide the security processor to read the encrypted Bootloader of the application processor, decrypt the encrypted Bootloader, and verify the signature data of the encrypted Bootloader at the same time, After the verification is passed, the bootloader that caches the plaintext releases the reset signal of the application processor. After the reset signal is released, the application processor starts to start and reads the cached plaintext Bootloader from the security processor. .
[0079] The Linux kerne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com