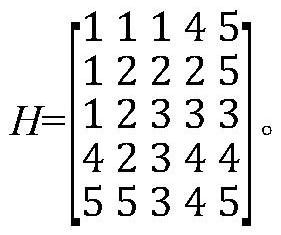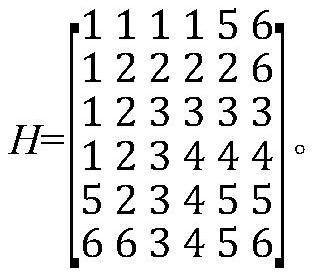Secure multi-party multiplication method and system
A multiplication operation and multi-party technology, applied in the field of distributed joint computing, can solve problems such as low efficiency, impossible sharing of medical data and bank personal credit data, etc., achieve less communication overhead, easy parallel computing, and improve computing efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0048] The invention discloses a safe multi-party multiplication operation method, including:
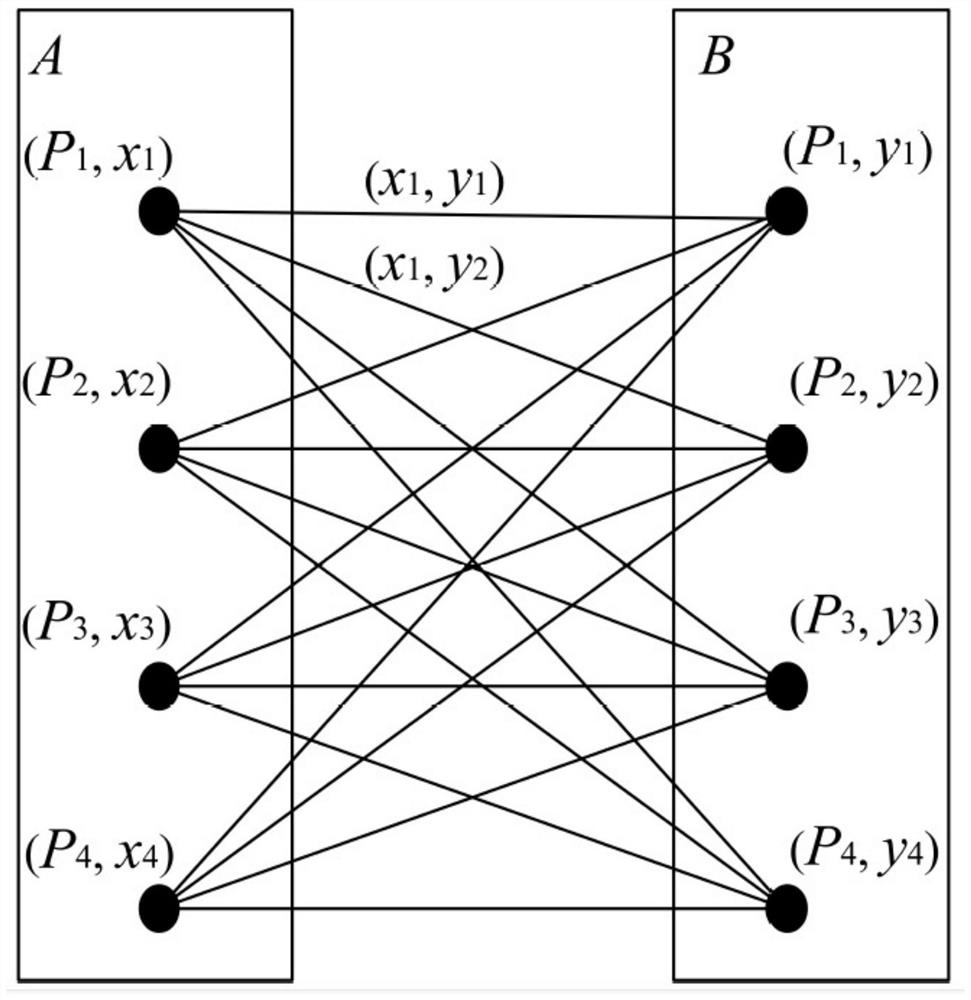
[0049] Step S1. Determine the number of multiplication sharing participants, and abstract the communication and calculation process of the shared components into a shared bipartite graph.
[0050] refer to figure 1 , with n participants P greater than or equal to 4 1 ,P 2 …P n Calculate z=xy together, share x and y with n parties, P i have (x i ,y i ); share x i Form a set A={x i}, share y i Form a set B={y i}, i=1...n, take A and B as the vertex set in graph G; take each summation component x i the y j As the corresponding edge (x i ,y j ), i, j=1...n; data sharing bipartite graph G=(V,{E}), where E={(x i ,y j )}, side (x i ,y j ) corresponding to the weight x i the y j , V={A∪B}, sum the weights corresponding to all edges to get:
[0051] z=xy=(x 1 +x 2 +…+x n )(y 1 +y 2 +…+y n ) = ∑ i,j x i the y j .
[0052] Step S2, dividing the shared bipartite ...
Embodiment 2
[0084] This embodiment discloses a secure multi-party multiplication system, which includes a memory, a processor, and a computer program stored in the memory and operable on the processor. When the processor executes the computer program, it implements the corresponding functions of the above embodiments. Method steps.
[0085] To sum up, the safe multi-party multiplication method and system respectively disclosed in the above-mentioned embodiments of the present invention have the following beneficial effects:
[0086] Based on the adjacency matrix of the present invention, the following constraints are satisfied:
[0087] E. 1 ∪E 2 ∪…∪E n =E
[0088] That is: all subgraphs can form the original bipartite graph, that is to say, after each participant calculates the multiplication share according to the division, the sum of all shares is the result of multiplication; and at the same time satisfy:
[0089]
[0090] That is: each subgraph is independent and has no commo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com