Secret sharing method and system based on visual effect
A technology of secret sharing and visual effects, applied in image communication, electrical components, etc., can solve the problems of reducing contrast, pixel problem expansion still exists, and restoring image visual quality is reduced, so as to improve performance, eliminate pixel expansion, and achieve high contrast Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0059] Such as figure 1 As shown, the present invention provides a secret sharing method based on visual effects, including:
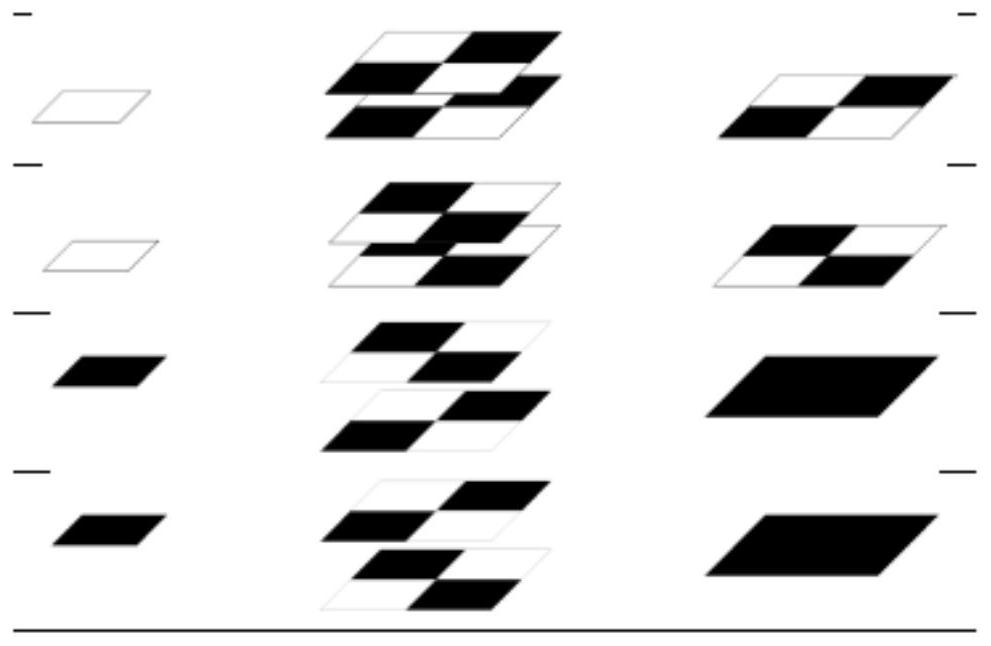
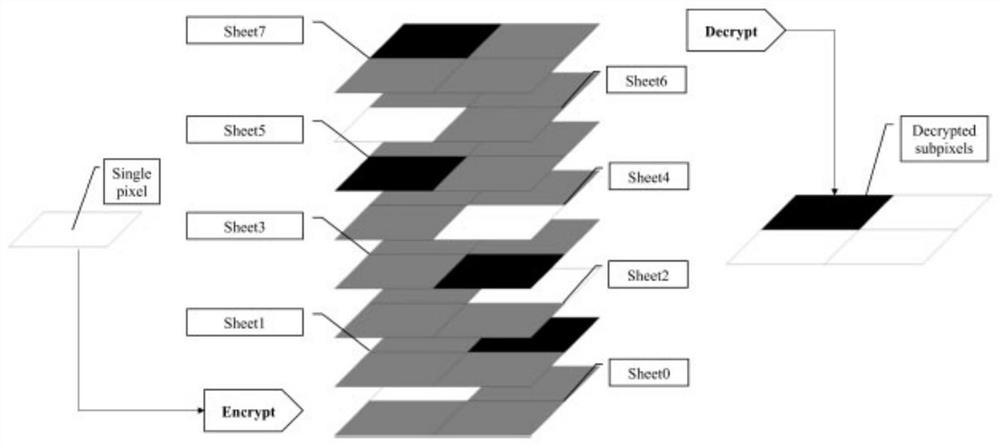
[0060] Split the original image into multiple secret images; map each secret image into a secret block; generate multiple shared image blocks block by block based on the size of the secret block; move each shared image block in a cyclic stacking manner to realize the shared Encryption of image blocks;
[0061] distribute the encrypted shared image blocks to at least two users in a stacked order;
[0062] Superimpose all shared image blocks distributed to users in order to obtain a decrypted image with the same quality as the original image;
[0063] Wherein, the secret block has a plurality of pixels.
[0064] The entire encryption, decryption and distribution process of shared image blocks will be described in detail below.
[0065] 1. Introduction to VCS visual cryptography technology
[0066] 1.1 The foundation of VCS
[0067] In order to illu...
Embodiment 2
[0172] In order to realize the above method, the present invention also provides the present invention also provides a secret sharing system based on visual effects, such as Figure 9 shown, including:
[0173] The encryption module is used to split the original image into multiple secret images; map each secret image into a secret block; generate multiple shared image blocks block by block based on the size of the secret block; move each shared image block in a circular stacking manner Encrypting the shared image block;
[0174] A distribution module, configured to distribute the encrypted shared image blocks to at least two users in a stacked order;
[0175] The decryption module is used to superimpose the shared image blocks distributed to users in order to obtain a decrypted image with the same quality as the original image;
[0176] Wherein, the secret block has a plurality of pixels.
[0177] Splitting the original image into multiple secret images in the encryption m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com