Threat intelligence access toolbox based on Tor network service
A toolbox and intelligence technology, applied in the field of network security, can solve problems such as lowering the learning threshold and difficulty in obtaining business intelligence, and achieve the effects of lowering the learning threshold, improving efficiency, and reducing time costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to make those skilled in the art better understand the technical solutions of the present invention, the present invention will be further elaborated below with reference to the accompanying drawings.
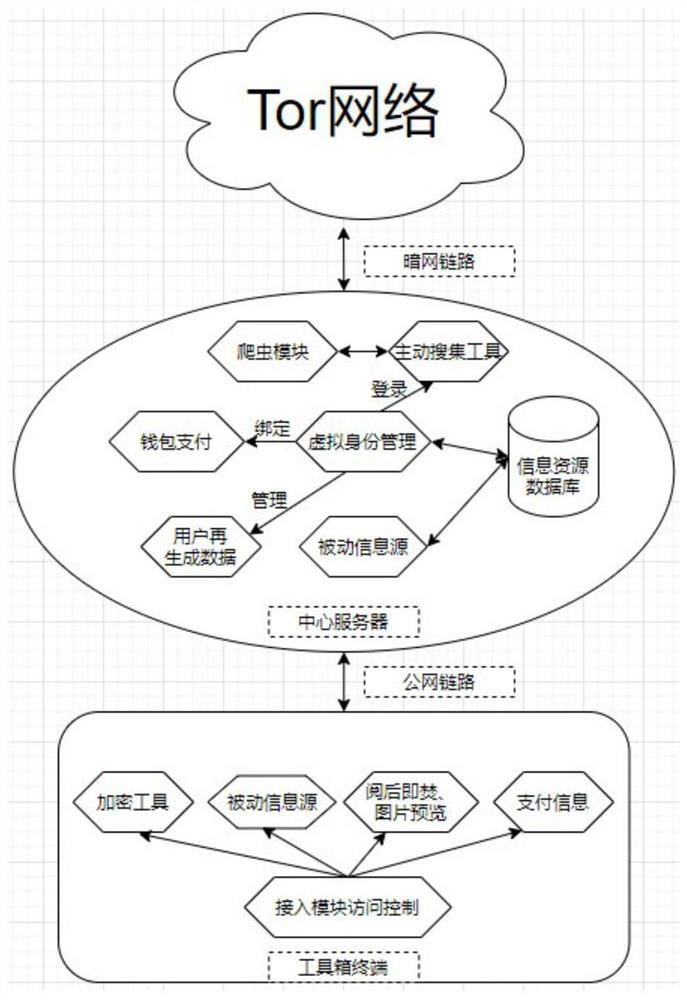
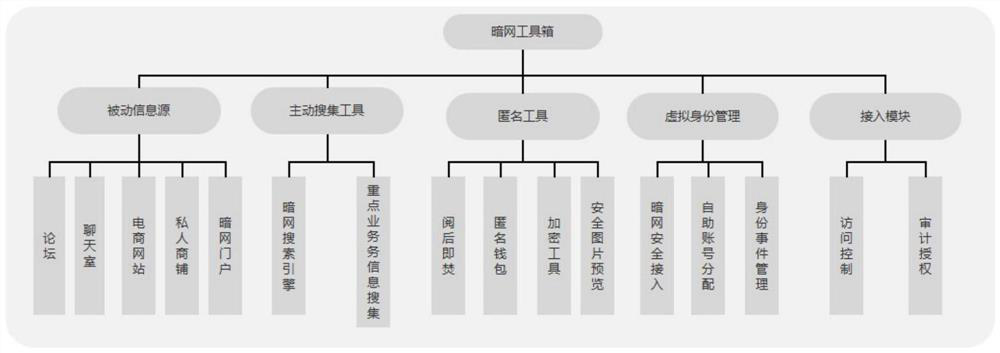
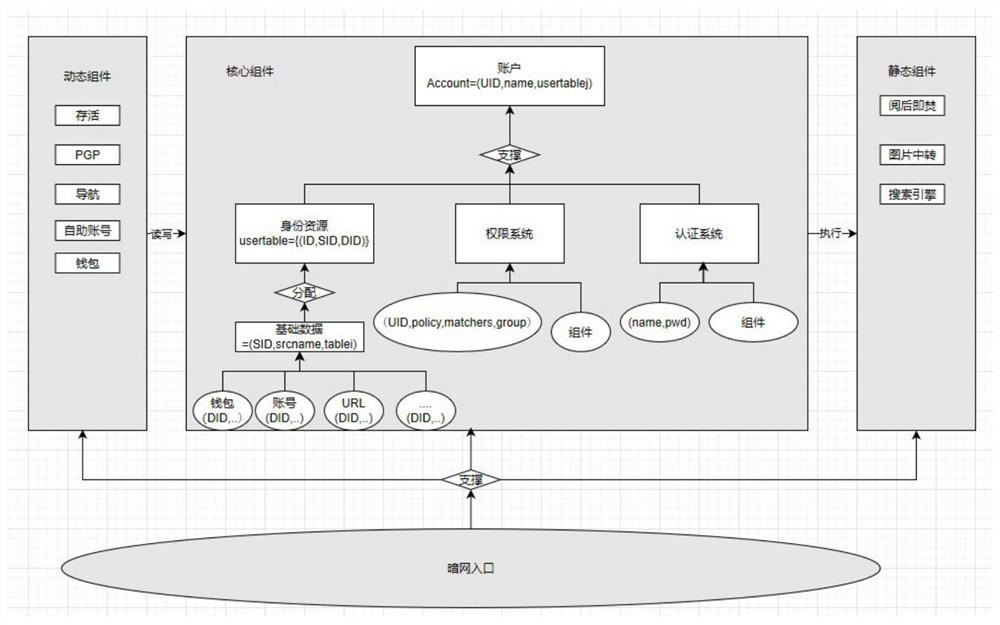
[0029] refer to figure 1 , the toolbox is implemented collaboratively by the user terminal and the remote central server figure 2 Medium function. The user first enters the special account password in the terminal to connect to the remote central server through the access control verification of the access module. Then, the central server provides the darknet link connection and passive information source of the toolbox, active collection tools, anonymity tools, and virtual identity management functions. At the same time, the access module begins to record user access operations to achieve auditing. During the user's use, the passive information source module will read the user's special information from the database for display, and the data generated by the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com