Method and equipment for recognizing messages under mass flow
A message and traffic technology, applied in the field of network security, can solve the problems of inefficient monitoring methods, low access ports and access traffic, and inability to monitor malicious messages, so as to improve efficiency, improve efficiency, and reduce performance consumption. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
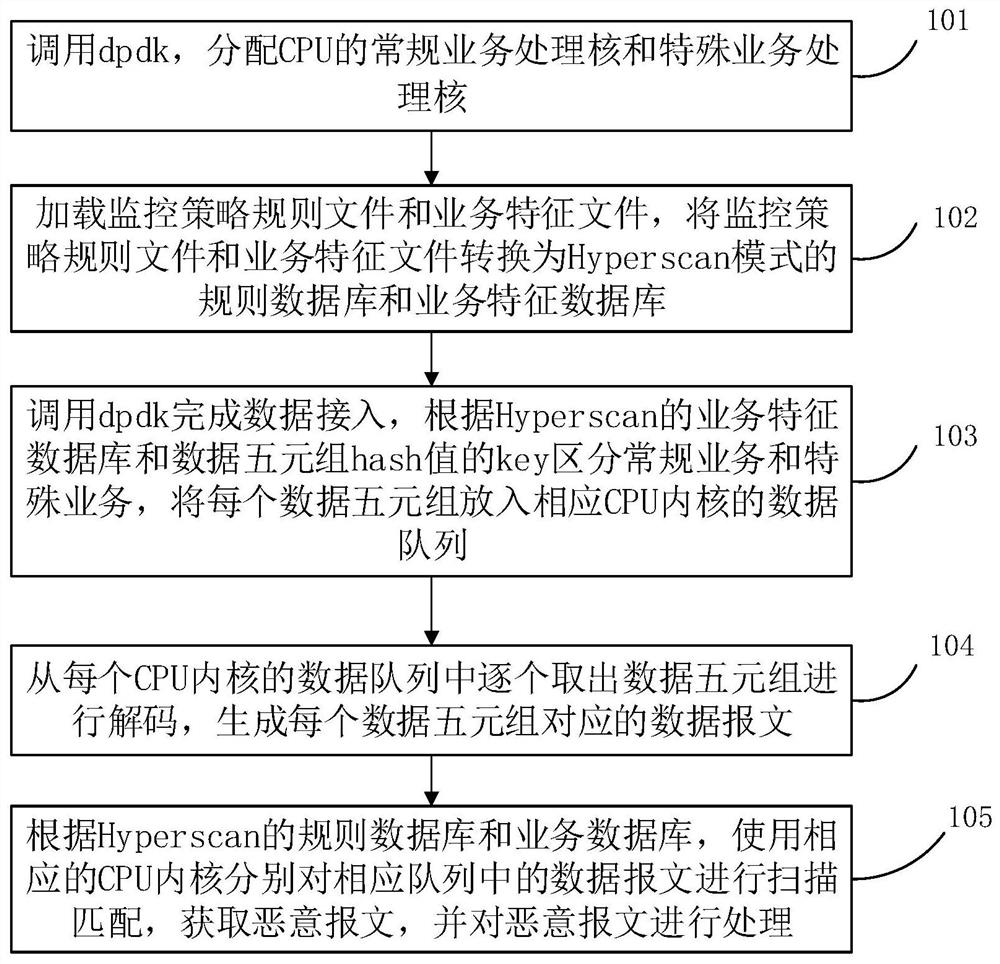
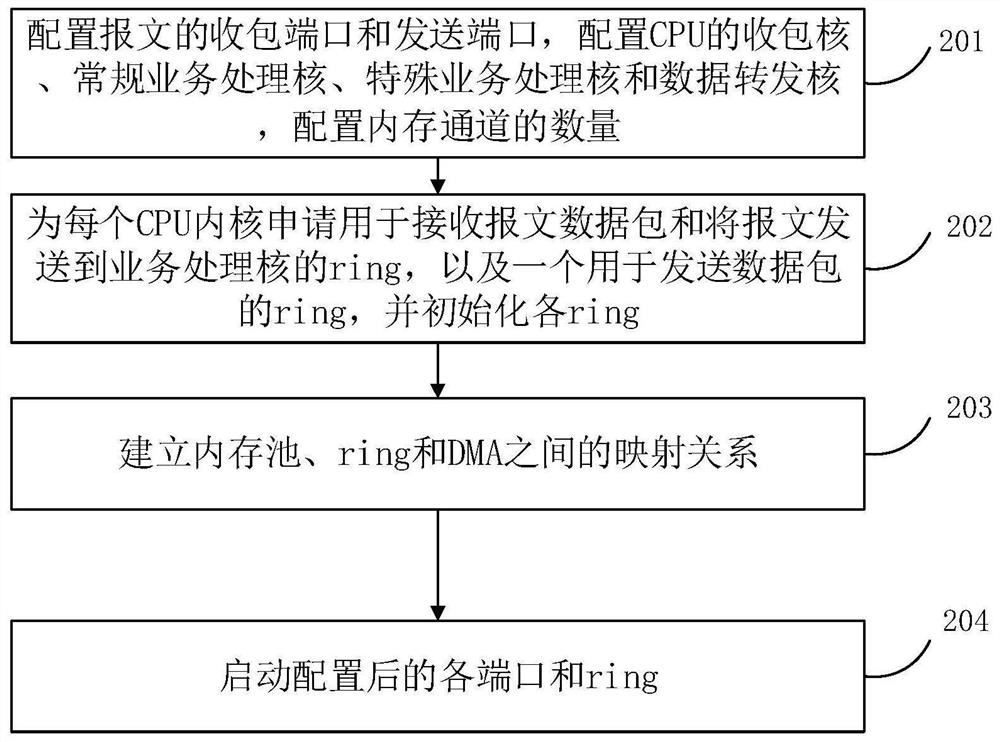
[0052] At present, the bandwidth of Internet access is increasing, and the rapid growth of network traffic is growing, and the number of network attacks is growing, and complexity is constantly improving. Therefore, there is a need for a rapid and large number of packets under mass flow to find malicious messages that may exist. In this embodiment, the DPDK is combined with HyPerscan while satisfying large flow data acquisition and efficient feature string matching, which improves the processing efficiency of large traffic.
[0053] Such as figure 1 As shown, the specific steps of different types of packet identification blocks in a massive flow provided in the embodiments of the present invention are as follows:
[0054] Step 101: Call DPDK, allocate the regular business processing cores and special business processing cores of the CPU.
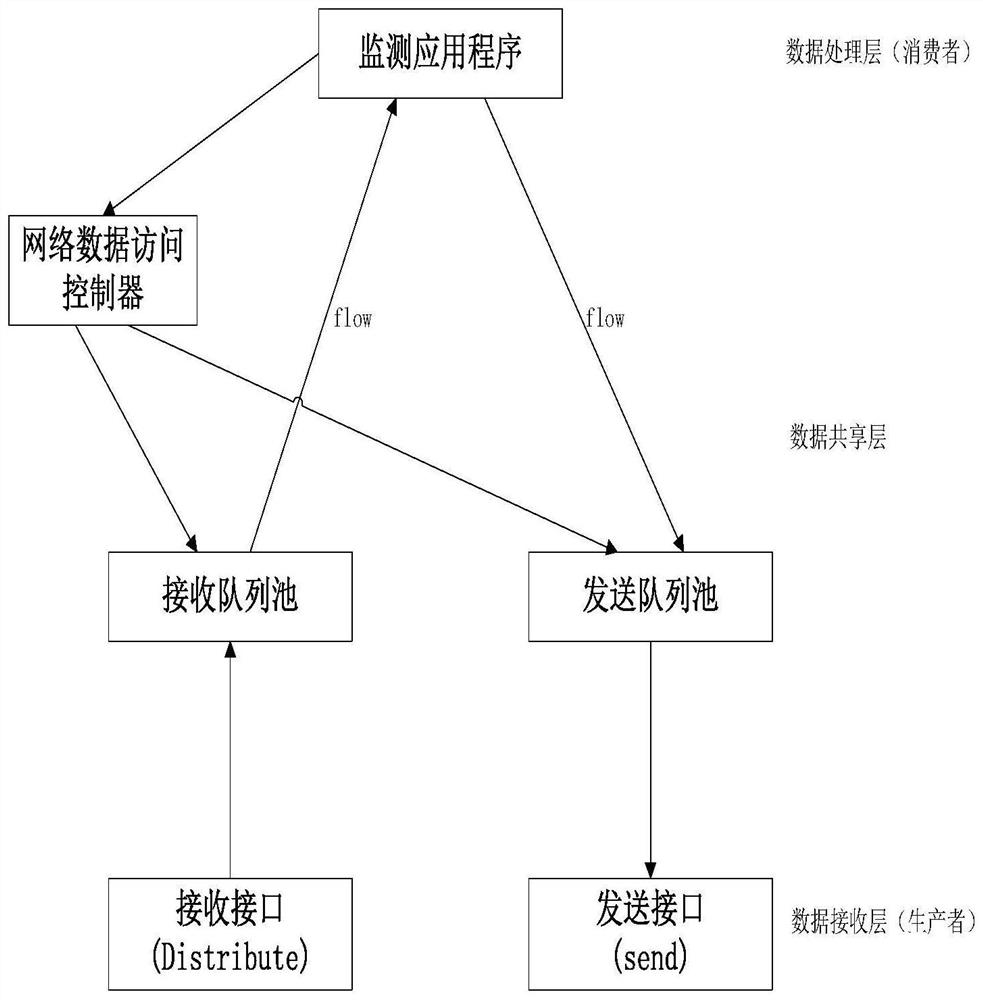
[0055] The method for packets identified in this embodiment is introduced into the network interface layer (network card driver) and the monit...
Embodiment 2
[0138] Based on the methods identified by the packets of the above-described Embodiment 1, the present invention also provides a device that can be used to achieve a massive flow rate of the above method, such as Figure 10 As shown, it is a schematic diagram of the apparatus architecture of the embodiment of the present invention. The apparatus recognized by the local volume of this embodiment includes one or more processor 21 and a memory 22. among them, Figure 10 Taking a processor 21 as an example.
[0139] The processor 21 and the memory 22 can be connected by a bus or other means. Figure 10 In connection with the bus connection.
[0140] Memory 22 is a non-volatile computer readable storage medium as a massive flow, which can be used to store non-volatile software programs, non-volatile computer executables, and modules, as massive in Example 1. Document recognition method under traffic. The processor 21 performs various functional applications and data processing of the appa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com