Vulnerability knowledge mining method and system based on graph
A knowledge mining and vulnerability technology, applied in the field of graph-based vulnerability knowledge mining, which can solve problems such as difficulty in analyzing vulnerabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] All features disclosed in all embodiments in this specification (including any appended claims, abstract and drawings), or steps in all methods or processes implicitly disclosed, except for mutually exclusive features and / or steps, can be used as Combining and / or extending, replacing in any way.
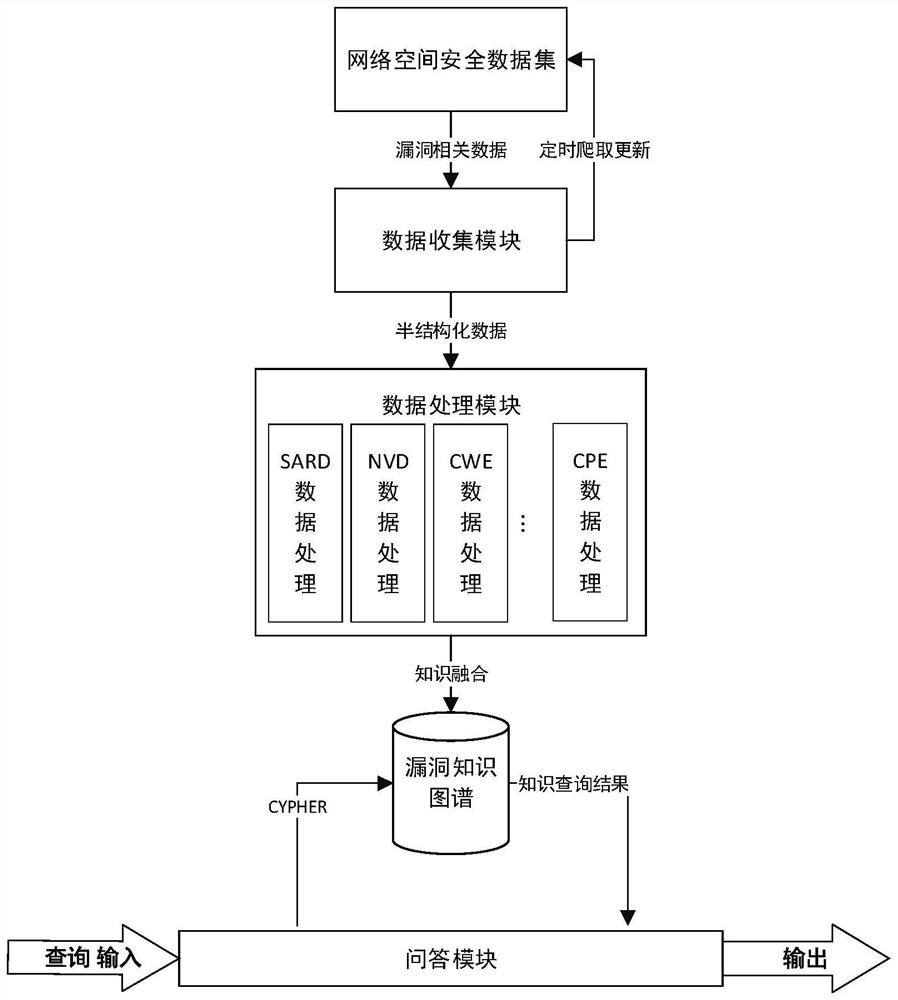
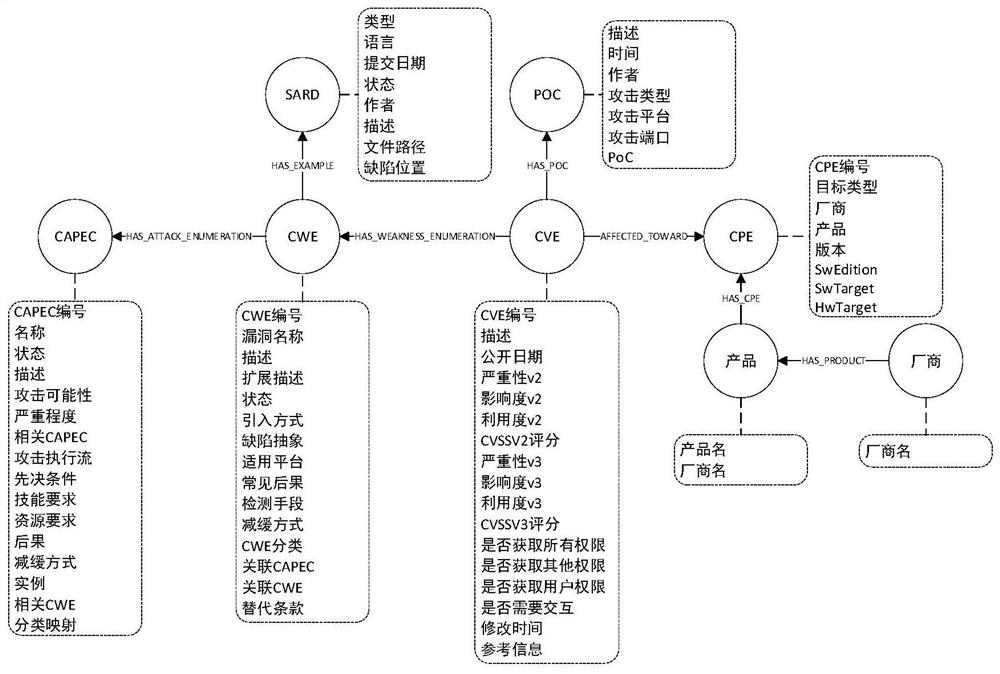
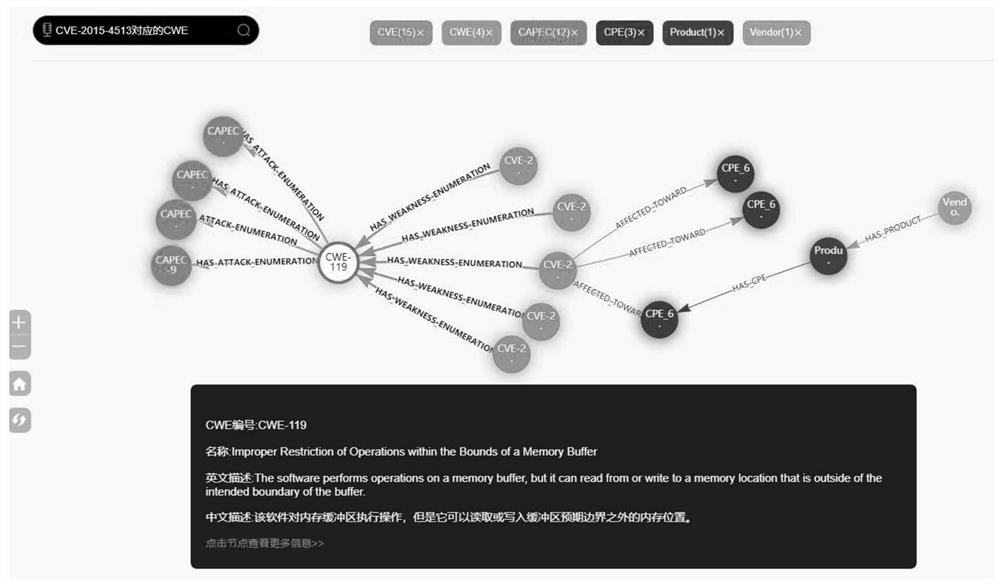
[0038] In 2012, Google proposed the concept of knowledge graph, which provides the ability to integrate, manage and analyze multi-source heterogeneous data by storing a large number of knowledge entities and the relationship between entities. The knowledge map preserves expert experience and reasoning rules, realizes cognition of the objective world through entity and relationship mining, and generates new knowledge from existing knowledge.
[0039] Based on the above information, the present invention collects vulnerability-related data published on the Internet, extracts the attributes and relationships between each vulnerability entity, constructs a cyberspace security vuln...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com