Inter-satellite authentication method, system, medium, equipment, terminal and application
An authentication method and authentication method technology, applied in the field of satellite network communication, can solve problems such as high authentication overhead, reduce communication cost and communication time, and realize the effect of fast authentication between satellites
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
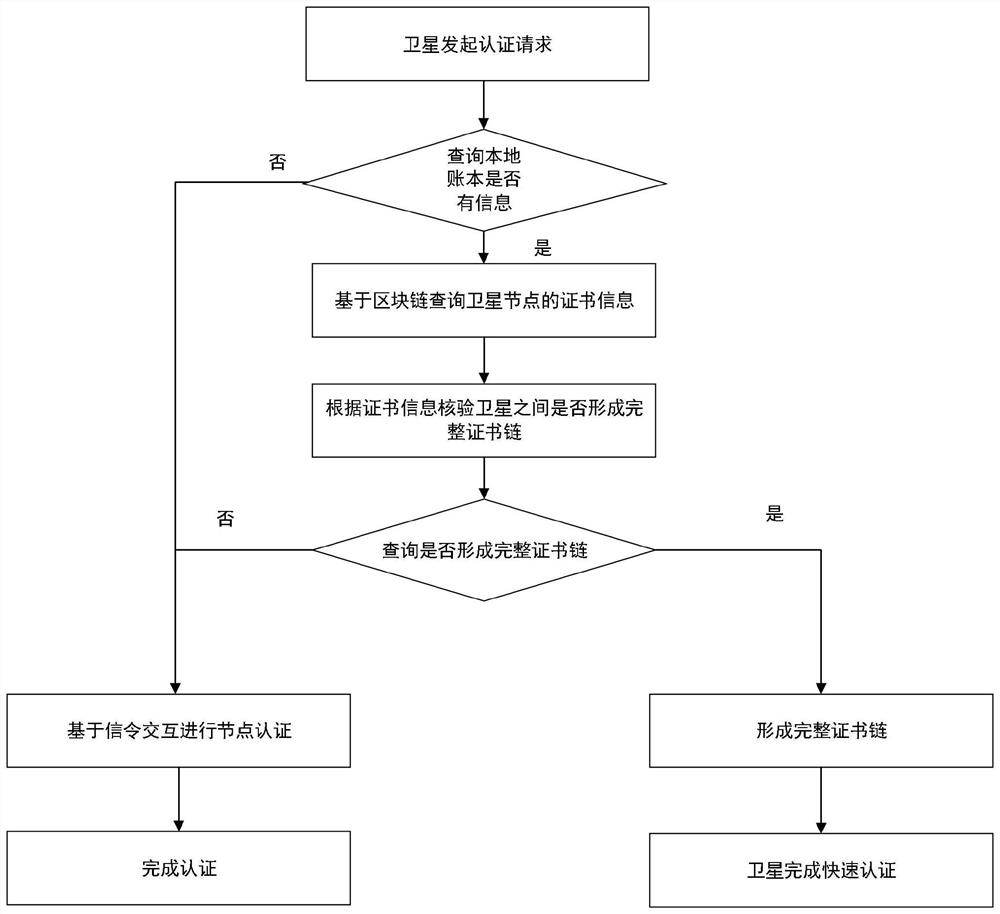
[0131] Such as image 3 As shown, the satellite network deploys the blockchain, and the formation process of the blockchain includes the following steps:
[0132] (1) Obtain satellite identity and authentication certificates;
[0133] Each satellite uses unique identity information as proof of identity to issue and sign an identity certificate for its own identity. Each satellite node communicates with its own neighbor nodes, each satellite node and other satellite nodes within the communication distance of itself, through information-based Make interactive authentication, issue authentication certificates of recognized identities to each other, and the block chain obtains the certificate information of each satellite node;
[0134] (2) According to the authentication result and certificate information, as a transaction, the satellite node packs and generates a block;
[0135] The identity and authentication information of each satellite node, as transaction information, is ...
Embodiment 2
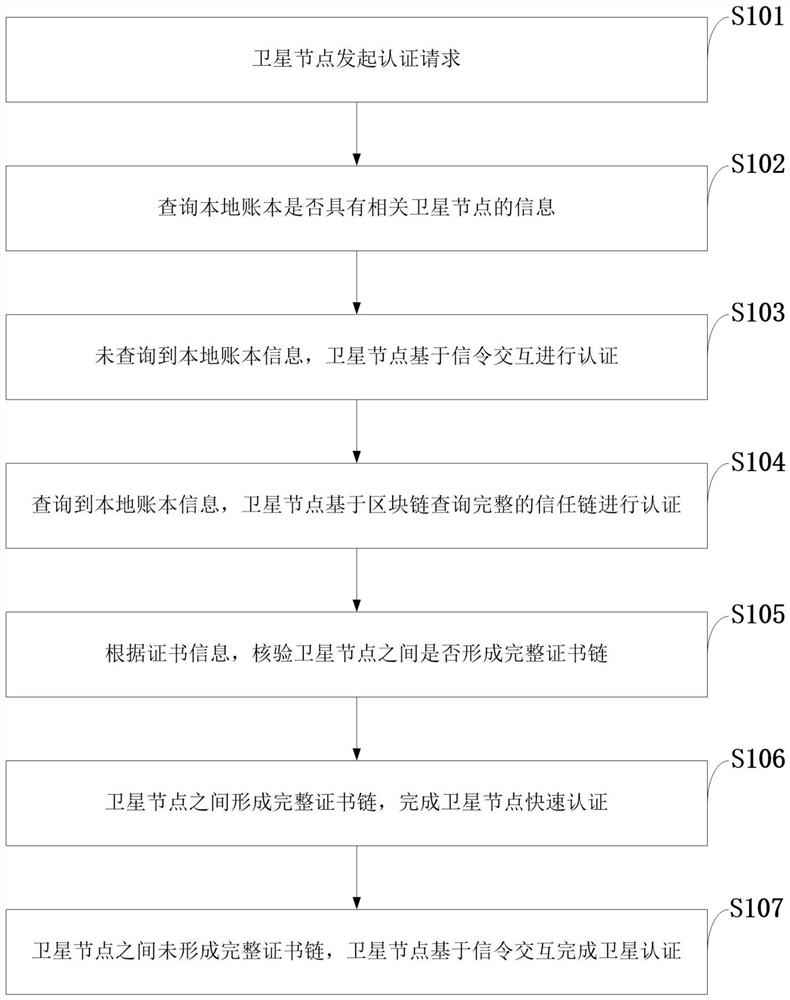
[0142] Such as figure 1As shown, the inter-satellite authentication method provided by the present invention includes the following steps:
[0143] S101: The satellite node initiates an authentication request;
[0144] S102: Query whether the local ledger has information about relevant satellite nodes;
[0145] S103: The local account book information is not queried, and the satellite node performs authentication based on signaling interaction;
[0146] S104: Query the local ledger information, and the satellite node queries the complete trust chain based on the blockchain for authentication;
[0147] S105: According to the certificate information, verify whether a complete certificate chain is formed between the satellite nodes;
[0148] S106: A complete certificate chain is formed between the satellite nodes, and the fast authentication of the satellite nodes is completed;
[0149] S107: A complete certificate chain is not formed between the satellite nodes, and the sate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com