Exception detection feature construction method, module, storage medium, device and system
A technology of anomaly detection and construction method, which is applied in transmission systems, digital transmission systems, error detection of redundant codes, etc., and can solve problems such as inability to deal with complex man-in-the-middle attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0065] All features disclosed in all embodiments in this specification, or steps in all implicitly disclosed methods or processes, except for mutually exclusive features and / or steps, can be combined and / or extended and replaced in any way.
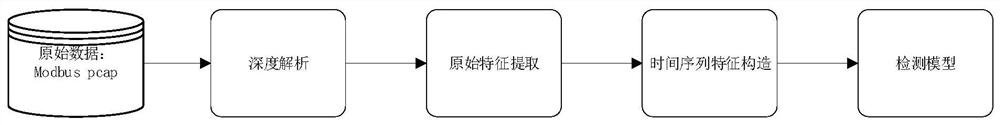
[0066] Such as Figure 1~5 As shown, a construction method of anomaly detection features includes the following steps:
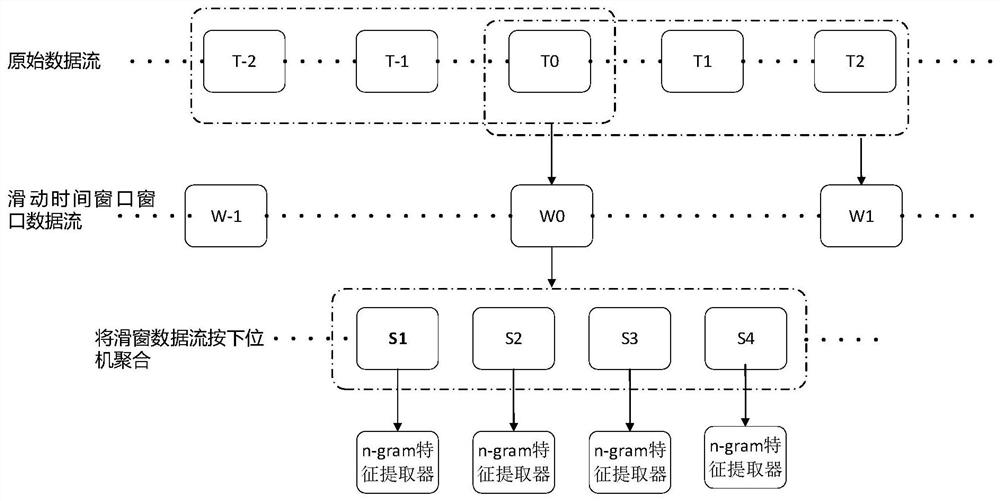
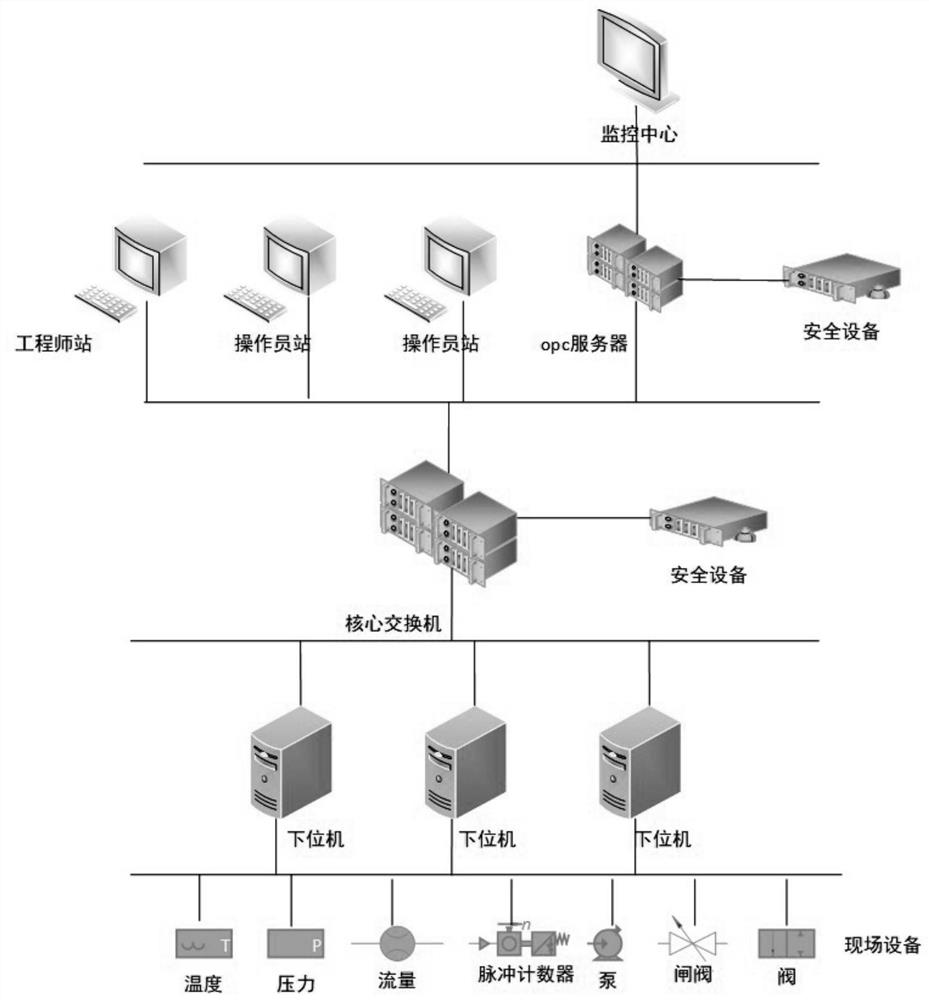
[0067] S1, extract the traffic data of the sliding time window, and aggregate the traffic with the lower computer / slave as the source address in each sliding time window;
[0068] S2, within the current sliding time window, extract the current data flow time t for each slave / slave as the source address 0 The first n pieces of traffic data are constructed with n-gram communication behavior features, n is a positive real number greater than 2, and the constructed n-gram communication behavior features are combined with the detection algorithm model to construct and adjust the abnormality detection features.
[0069] Fur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com