Method and device for generating multiplication triad based on elliptic curve, equipment and medium
An elliptic curve and triplet technology, which is used in secure communication devices, electrical components, public keys for secure communication, etc., can solve a wide range of value space waste, high cost, and large triplet value space, etc. problems, to achieve the effect of avoiding resource waste, low structural coupling, and reducing renovation and trust costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
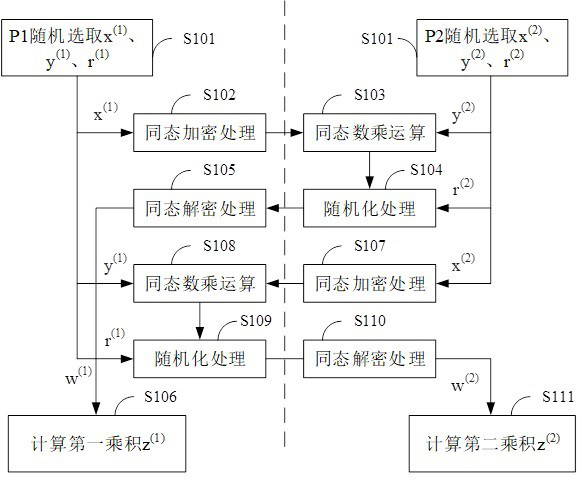
[0066] This embodiment provides a method for generating multiplication triples based on elliptic curves, such as figure 1 As shown, the method specifically includes the following steps:
[0067] S1011, participating node P1 selects the first random number r (1) , and the first random non-negative integer x whose bit length is less than or equal to the preset length threshold (1) and a second random non-negative integer y (1) .
[0068] S1012, the participating node P2 selects the second random number r (2) , and a third random non-negative integer x whose bit length is less than or equal to the preset length threshold (2) and a fourth random non-negative integer y (2) .
[0069] For example, the preset length threshold can be set to 8, and x (1) 、y (1) 、x (2) 、y (2) are smaller than the public modulus p. In this embodiment, the public modulus p is a prime number of appropriate length selected jointly by the two participating nodes P1 and P2.
[0070] S102, particip...
Embodiment 2
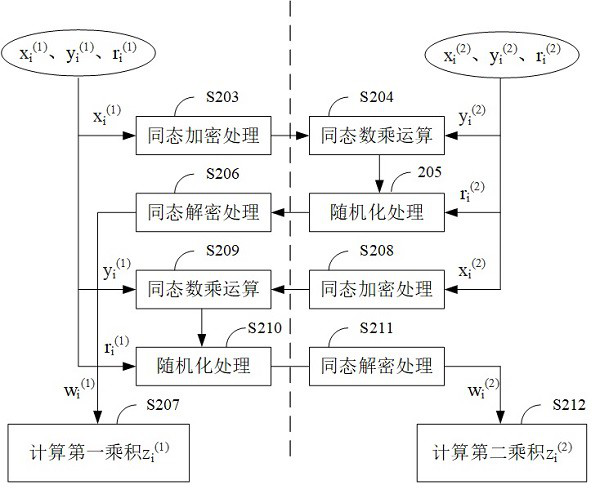
[0087] This embodiment provides a method for generating multiplication triples based on elliptic curves, such as figure 2 and 3 As shown, the method includes the following steps:
[0088] S2011, the participating node P1 selects a first random non-negative integer x with a bit length greater than a preset length threshold (1) and a second random non-negative integer y (1) , figure 2 x selected from (1) 、y (1) The bit length is shown as 256 bits.
[0089] S2012, the participating node P2 selects a third random non-negative integer x whose bit length is greater than the preset length threshold (2) and a fourth random non-negative integer y (2) , figure 2 x selected from (2) 、y (2) The bit length is shown as 256 bits.
[0090] For example, the preset length threshold can be set to 8, and the selected x (1) 、y (1) 、x (2) 、y (2) are less than N public modulus p i Product(i=1,...,N). In this embodiment, the public modulus p i A set of prime numbers with appropri...
Embodiment 3
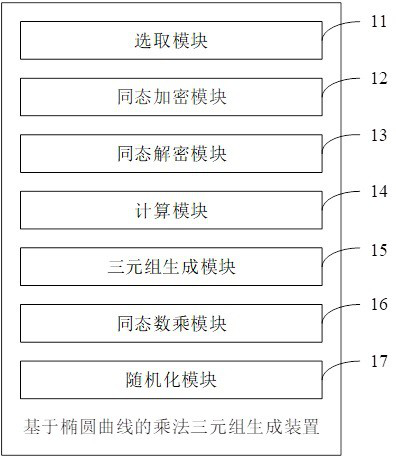
[0114] This embodiment provides a multiplication triplet generation device based on elliptic curves, which is suitable for the first participating node, such as Figure 4 As shown, the device includes:
[0115] A selection module 11, configured to select a first random non-negative integer x whose bit length is less than or equal to a preset length threshold (1) and a second random non-negative integer y (1) ;
[0116] The homomorphic encryption module 12 is used to encrypt the first random non-negative integer x (1) Perform homomorphic encryption processing based on elliptic curves to obtain the first ciphertext, and send the first ciphertext to the second participating node, and the second participating node pre-selects a bit length less than or equal to the preset length threshold The third random non-negative integer x of (2) and a fourth random non-negative integer y (2) , so that after the second participating node receives the first ciphertext, the fourth random no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com