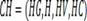Collision calculation method of chameleon hash function and tailorable blockchain account book structure
A hash function and calculation method technology, applied in the field of network security, to avoid affecting efficiency, ensure safety, and facilitate timely stop loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0027] This embodiment discloses a tailorable blockchain ledger structure, including several blocks, each of which includes a one-to-one correspondence between a block header and a block body; the block body stores transactions of the block Information; the block header includes hash value, message, nonce value and random number; the hash value is the chameleon hash value of the previous block, which is used to form a chain structure with the previous block, and so on, Until it is linked to the initial block; the message is calculated from the transaction information; the random number and the hash value are a hash pair based on the chameleon hash function.
[0028]A chameleon hash function scheme consists of four functions: key generation (Key Generation HG), hash function (HashGeneration H), verification function (Hash Verification HV) and collision function (Hash Collision HC) [10]:
[0029]
[0030] (1) : key generation algorithm, input a security parameter , output...
Embodiment 2
[0042] This embodiment discloses a tailoring method for a tailorable blockchain account book, which is used to realize the tailoring of the tailorable blockchain account book structure described in Embodiment 1, including the following steps:
[0043] Step 1: The system management node initiates trapdoor verification and synthesis based on the chameleon hash function, and obtains the system public key and trapdoor private key with the cooperation of at least t nodes;
[0044] Step 2: The system management node performs the cutting operation on the block in the area to be cut, and calculates the new message of the block body after the cutting operation;
[0045] Step 3: Based on the system public key and trapdoor private key obtained in step 1, the system management node can modify the block header of the cutting operation area in step 2, so that the blocks before and after the operation area can form a chain through the hash value structure.
[0046] further,
[0047] Step 1...
Embodiment 3
[0085] This embodiment discloses a tailoring method for a tailorable blockchain account book, which is used to realize the tailoring of the tailorable blockchain account book structure described in Embodiment 1, wherein the main steps are the same as those in Embodiment 2, the difference being:
[0086] 1)
[0087] Step 2 specifically includes:
[0088] Step 2.21: The tailorable blockchain locates and deletes the block in the work area to be trimmed;
[0089] Step 2.22: The block chain can be tailored to locate the previous block and the next block of the deleted block.
[0090] This embodiment is mainly used to delete the entire block in a large blockchain. Unlike deleting a specific transaction, in order to delete a block , need to modify the block The hash value of the , so that it can be compared with the block Normal link.
[0091] when to delete block , for block , need to change into ,to maintain Unchanged, does not affect the normal link of subsequen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com