Instant messaging system and method fusing block chain and point-to-point communication
A technology of a communication system and a communication method, applied in the field of instant communication systems, can solve the problems of long time-consuming and high network pressure to create blocks, and achieve the effects of solving resources and bandwidth, improving concurrency, and high robustness.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
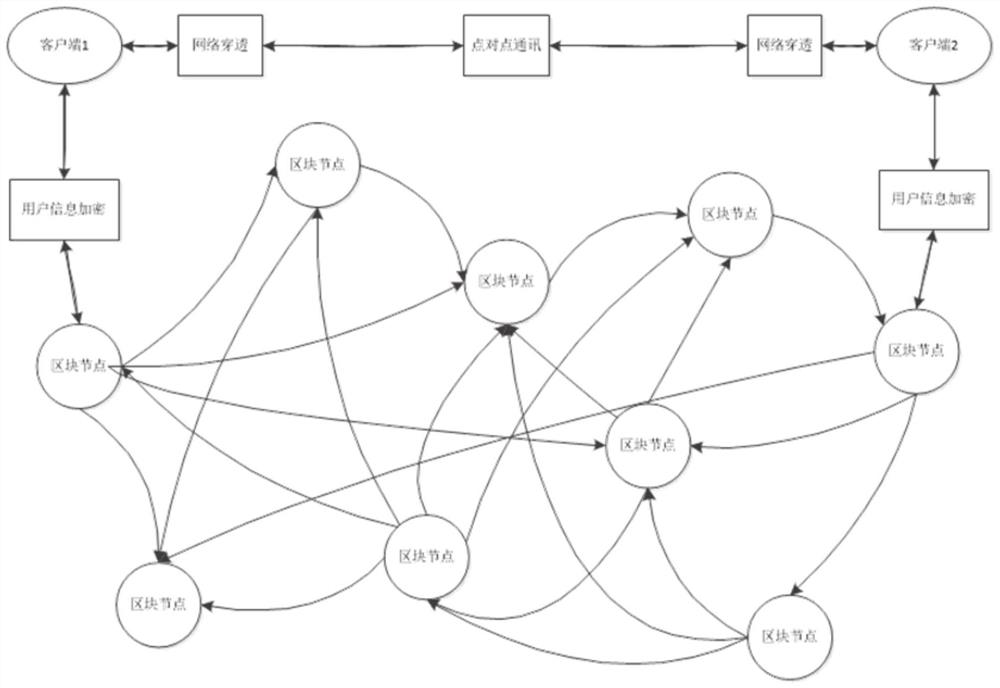
[0040] The purpose of this embodiment is to provide an instant messaging system that integrates blockchain and peer-to-peer communication technologies.
[0041] An instant messaging system that integrates blockchain and peer-to-peer communication technologies, including a data service layer, an intermediate layer, and an application layer;
[0042] The data service layer adopts block node network architecture to realize distributed storage and privacy protection for system data;
[0043] The middle layer adopts WebRTC point-to-point communication, and performs data transfer through a transfer server;
[0044] The application layer implements instant messaging between users based on the data service layer and the middle layer;
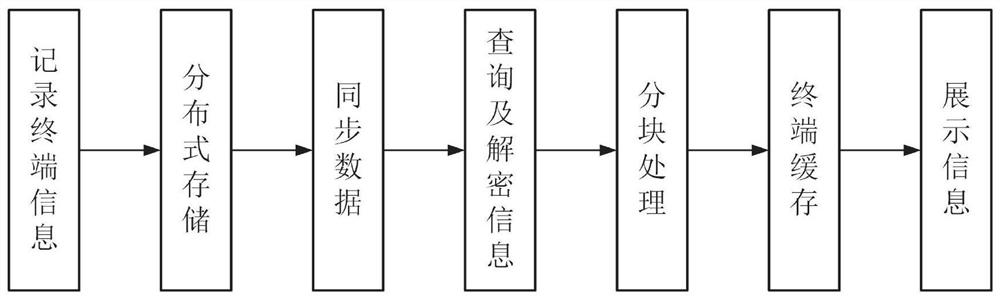
[0045] Among them, the user information is encrypted and uploaded to the chain, and the communication content is uploaded to the chain asynchronously, and the encrypted chat content is recorded using the IPFS distributed storage system; the instant mes...
Embodiment 2
[0112] The purpose of this embodiment is to provide an instant messaging method that integrates blockchain and peer-to-peer communication technologies.
[0113] An instant messaging method that integrates blockchain and peer-to-peer communication technologies, including:
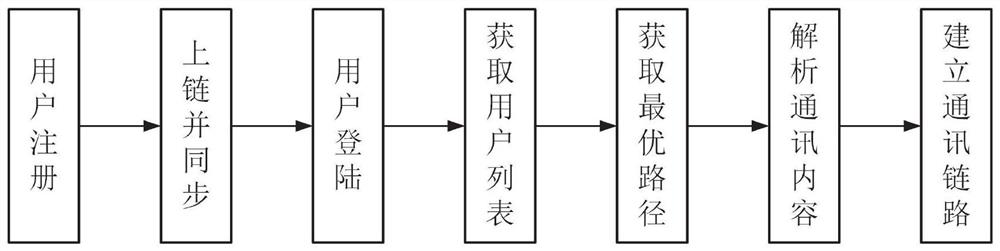
[0114]User registration through the client;
[0115] After the registration information is encrypted, block nodes are created and uploaded to the chain, and all block nodes are synchronized at the same time;
[0116] Encrypt the user's public network and internal network IP and port and synchronize it to the block nodes of the whole network;
[0117] Obtain the user list through the block node, and select friends for communication;
[0118] Synchronize the communication notification to the target node through the block node;
[0119] After receiving the notification, the target node uses its own private key to analyze the communication content, and returns its IP information synchronously;
[0120] The s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com