Non-contact user identity authentication method based on RFID and convolutional neural network
A technology of user identity authentication and convolutional neural network, applied in the field of action recognition, to achieve the effect of improving system security, simple layout, accurate and effective segmentation of actions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings.
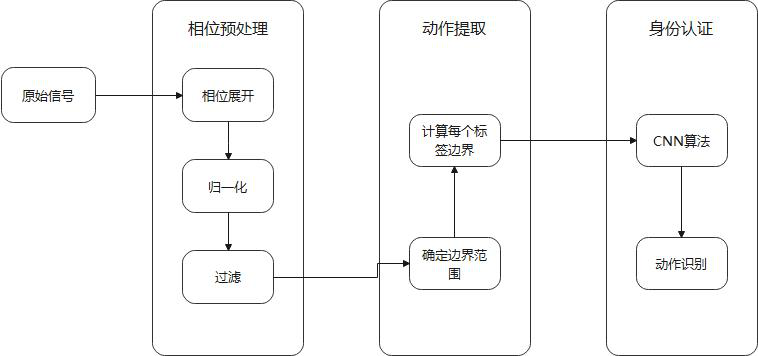
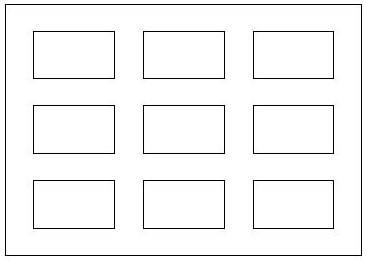
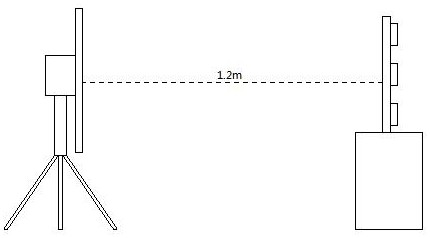
[0052] refer to figure 1 , the method includes: a phase preprocessing process, an action extraction process and an identity authentication process. Among them, the passive RFID tag matrix collects the phase data information of user identification actions, and the position layout of the tags is as follows: figure 2 and image 3 As shown; the collected phase information data includes: 5 kinds of movement modes for identity authentication. The collected actions and movement methods are as follows: Figure 4 shown. Antenna, used to send signals to passive RFID tags, while receiving signals from passive RFID tags, and sending them to RFID readers; RFID readers, used to modulate and demodulate signals, and decode data packets; phase preprocessing unit, It is used to perform phase expansion, normalization and data smoothing processing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com