Efficient equipment instruction authentication system and method based on certificateless signature
A technology of device instructions and authentication methods, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as private key leakage, achieve the effects of improving security, improving authentication efficiency, and ensuring integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to facilitate those of ordinary skill in the art to understand and implement the present invention, the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the implementation examples described here are only used to illustrate and explain the present invention, and are not intended to limit this invention.
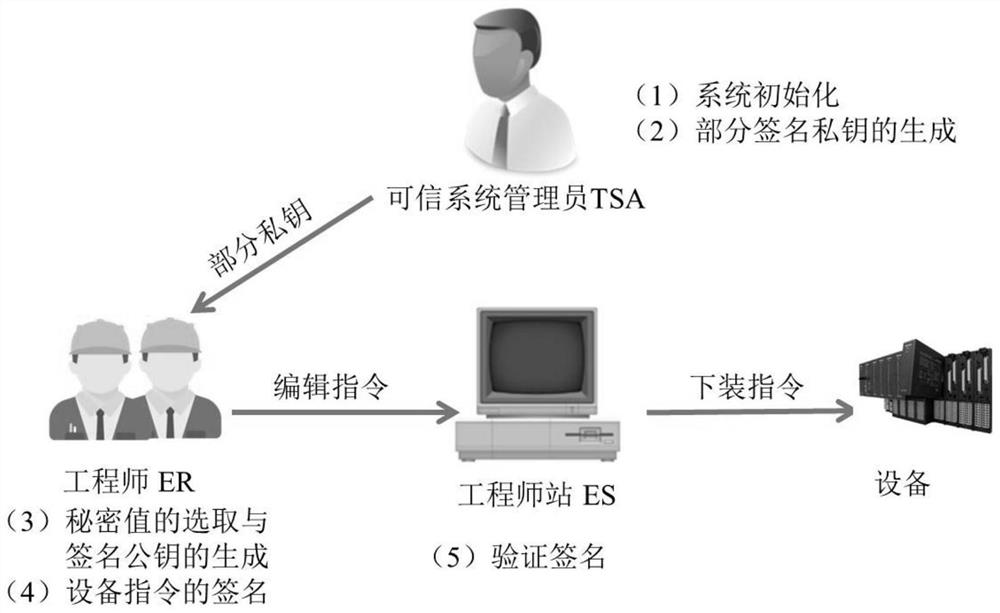
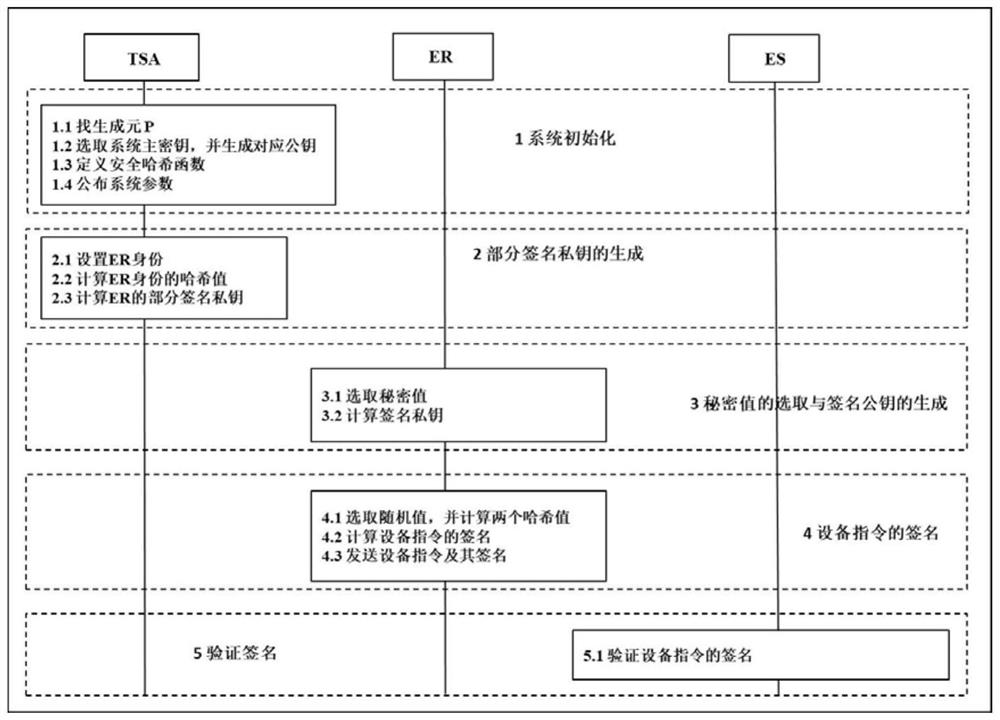
[0020] please see figure 1 , an efficient device instruction authentication system based on certificateless signatures provided by the present invention mainly includes three components, namely a trusted system administrator (Trusted System Administrator, hereinafter referred to as TSA), an engineer station (Engineer Station, hereinafter referred to as ES) ) and engineer (Engineer, hereinafter referred to as ER); ER signs the edited device command and sends it to ES; after ES receives the command, it verifies the legitimacy of the command signature, and only ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com