Two-factor identity authentication method for smart home scene
A smart home, identity authentication technology, applied in the field of information security, to solve forward security problems and resist node capture attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described in detail with reference to the accompanying drawings and embodiments.
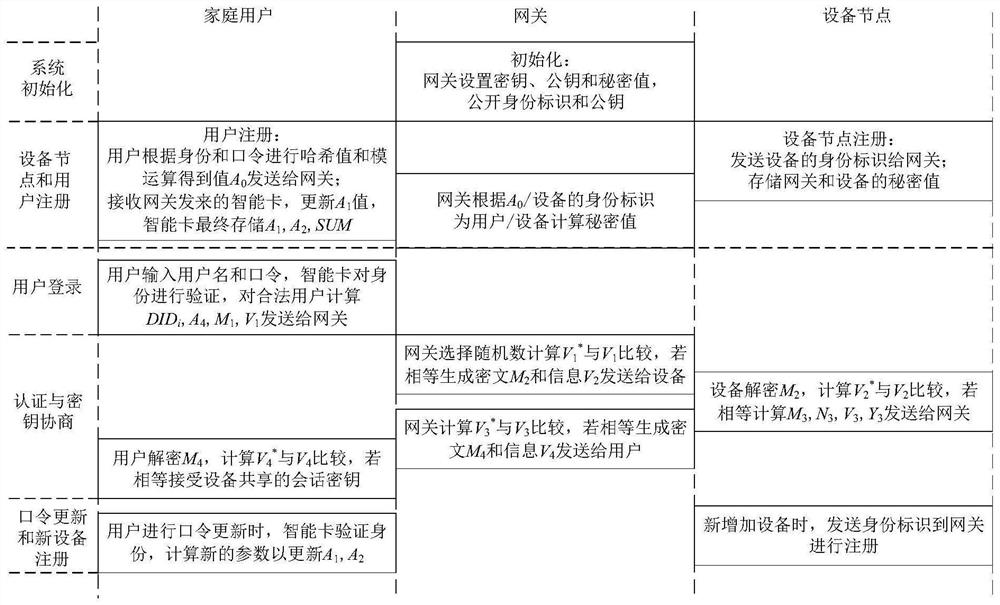
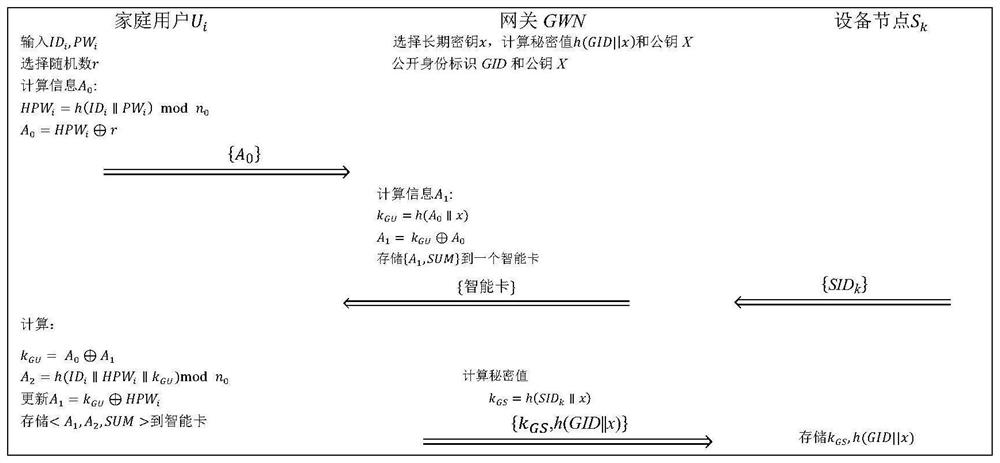
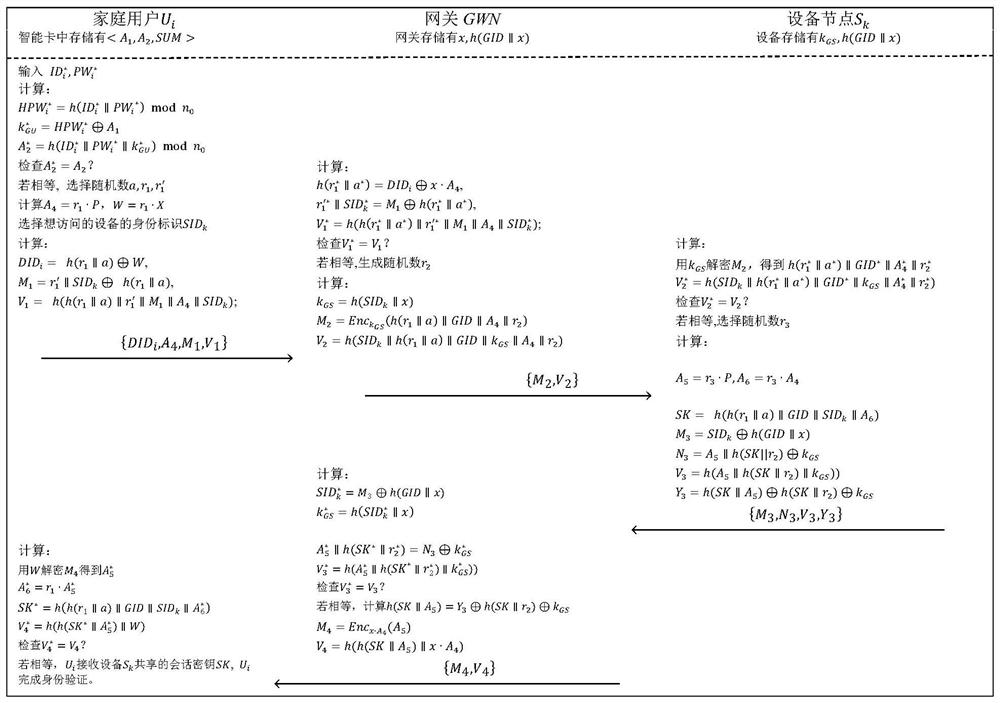
[0031] In the smart home scenario, the limited computing power of device nodes and various security issues emerge in an endless stream are the main problems that the two-factor authentication method needs to solve. In order to design a technical solution capable of solving the above six security issues and a storage issue, the present invention considers the following implementation techniques:
[0032] 1) When a legal user registers at the gateway, he only needs to use the user's own identity and password for the modulo calculation, and store the result in the smart card. The periodicity of the modulo calculation directly prevents the attacker from effectively guessing the user's password, thereby avoiding offline password guessing attacks based on smart cards or mobile devices; legitimate users are equivalent to home users;
[0033] 2) When the leg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com