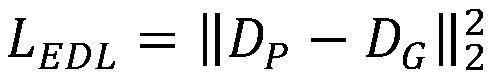Face representation attack detection method based on full-size depth map supervision
An attack detection and depth map technology, which is applied in the fields of image processing and biosecurity, can solve the problems of multi-label information volume, loss, and network inability to make full use of depth map labels, etc., and achieve high detection accuracy and strong robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
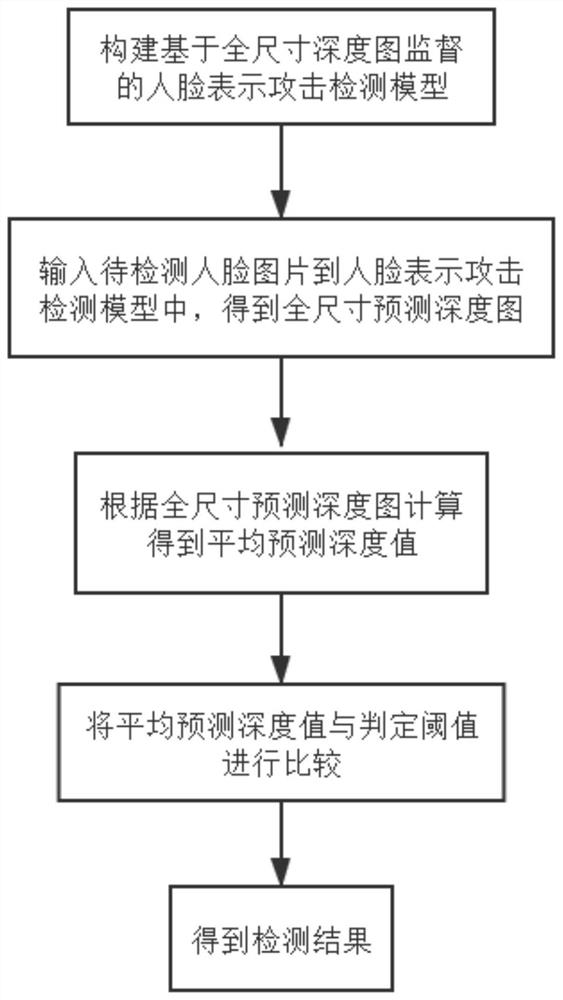
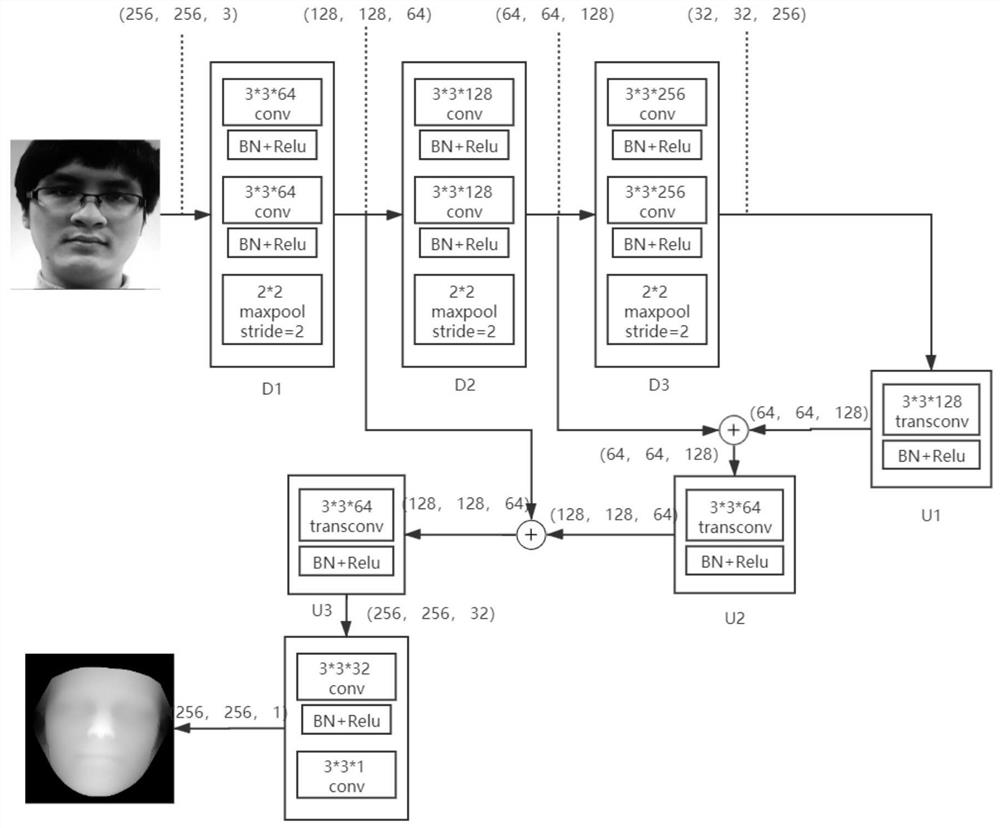
[0036] Such as figure 1 with figure 2 As shown, this embodiment provides a face representation attack detection method based on full-size depth map supervision, and the process is as follows:
[0037] S1. Construct a training set. The training set includes real face pictures and attack face pictures. Each face picture corresponds to two kinds of labels, which are binary classification labels and full-size label depth maps. The binary classification labels indicate the The category value of whether the face picture belongs to the real face picture or the attack face picture; the full-size label depth map indicates the depth label value corresponding to each pixel in the face area part of the face picture. In this embodiment, the full-size label depth map of the real face picture is obtained by the PRNet algorithm, one of the face depth map generation algorithms in the field of 3D face reconstruction, and the full-size label depth map of the attack face picture is set to be th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com