Encryption method based on AES encryption algorithm
An encryption algorithm and encryption method technology, applied in encryption devices with shift registers/memory, digital transmission systems, electrical components, etc., can solve the leakage of plaintext data information, increase the cost of obtaining sensitive data, and increase the strength of ciphertext problems, to achieve the effect of improving security performance and increasing the difficulty of cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
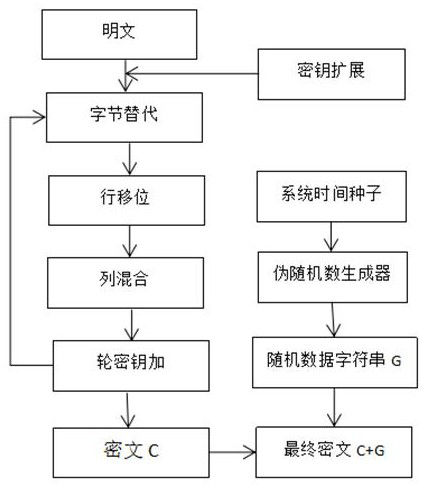
[0034] A kind of encryption method based on AES encryption algorithm, this method comprises the steps: at first, plaintext is input in the AES encryption algorithm in the form of parameter, carries out the key expansion operation and obtains the round key; Carries out the circular iterative operation of round encryption: byte Substitution, row shifting, column mixing and round key addition to get the ciphertext C; execute the pseudo-random number generation function and use the system time as the seed to generate a random data string G; the final ciphertext consists of ciphertext C and random data characters The string G is composed of two parts; the randomness of the ciphertext is realized, the difficulty of cracking is increased, and the security performance of the encryption algorithm is improved.
Embodiment 2
[0036] According to a kind of encryption method based on AES encryption algorithm described in embodiment 1, the concrete steps of described encryption method are as follows:
[0037] Step 1: The plaintext is passed into the AES encryption algorithm in the form of parameters to obtain the system time;
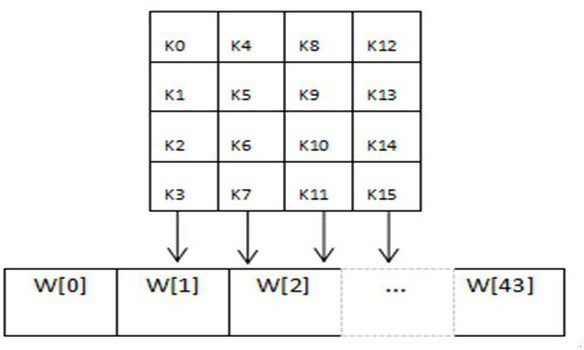
[0038] Step 2: Execute the key expansion algorithm to obtain the round key;
[0039] Step 3: Execute the byte substitution algorithm;
[0040] Step 4: Execute the row shift algorithm;
[0041] Step 5: Execute the column mixing algorithm;
[0042] Step 6: Execute the round key addition algorithm;
[0043] Step 7: Judging whether the number of loop iterations has been reached, if yes, go to 8 to obtain the ciphertext C, otherwise go to 3;
[0044] Step 8: Execute the pseudo-random number generation function to obtain the random data string G;
[0045] Step 9: Output the final ciphertext C+G.
Embodiment 3
[0047] According to a kind of encryption method based on AES encryption algorithm described in embodiment 2, use AES encryption algorithm to encrypt plaintext data to obtain ciphertext C, pseudo-random number generator generates random data string G, and final ciphertext is composed of ciphertext C and random The data string G consists of two parts. The resulting ciphertext is random.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com