Secure hidden three-element query method
A query method and three-element technology, which is applied in the field of safe and hidden three-element query, can solve problems such as exposure of user privacy, data leakage, and easy leakage of query data, and achieve the effect of protecting user privacy and avoiding data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
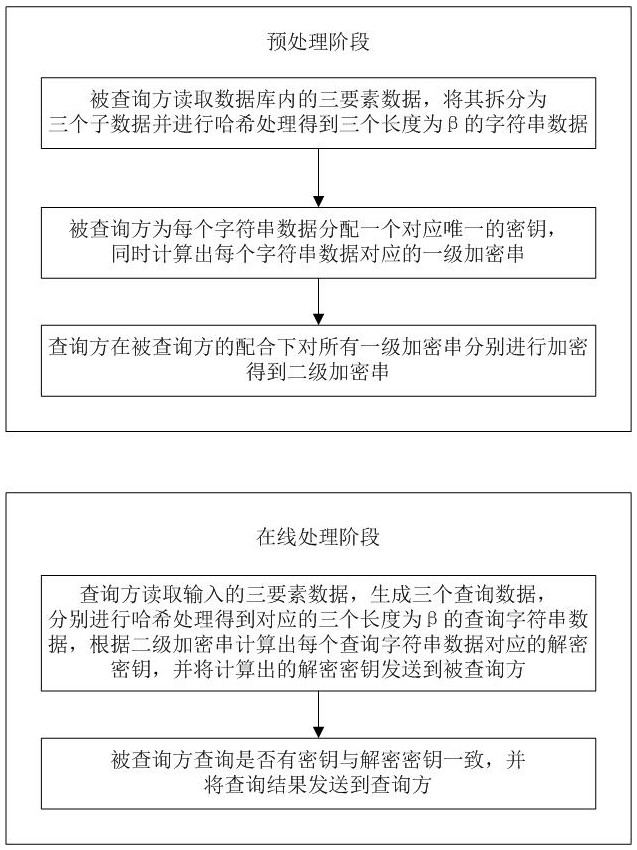
[0052] Embodiment 1: A kind of security hidden three-element query method of this embodiment, such as figure 1 As shown, including the preprocessing stage and the online processing stage;
[0053] The preprocessing phase includes the following steps:
[0054] M1: The inquired party reads the three-element data in the database. Each set of three-element data includes the name, ID number, and mobile phone number belonging to the same person. The inquired party processes each set of three-element data as follows: The element data generates three corresponding sub-data, the three sub-data are mobile phone number, (name, mobile phone number), (ID card number, mobile phone number), and these three sub-data are hashed to obtain the corresponding three lengths of The string data of β, store the obtained string data;
[0055] The method of performing hash processing on the three data of mobile phone number, (name, mobile phone number), (ID card number, mobile phone number) to obtain...
Embodiment 2
[0093] Embodiment 2: the method of this embodiment is basically the same as embodiment 1, the difference is:
[0094] Step M3 comprises the following steps:
[0095] M31: The queried party generates a parameter g p and send it to the querying party, g is an integer, p is a prime number, and the querying party generates a vector S, , convert the vector S into a vector L as follows: if the jth bit of the vector S is 0, then the jth bit of the vector L , if the jth bit of the vector S is 1, then the jth bit of the vector L , q is an integer, ;
[0096] M32: The querying party sends the vector L to the queried party, and the queried party generates a corresponding intermediate parameter group for each string data according to the vector L, the i-th string data b i The corresponding intermediate parameter group is C i , the intermediate parameter group C i The generation method of is as follows: According to each bit of the vector L, two corresponding parameters are gene...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com