Decentralized identity authentication system based on block chain
A decentralization, identity authentication technology, applied in the field of computer and computer network, decentralized identity authentication system, can solve the problem of server credibility affecting identity authentication results, being tampered with, authentication results being wrong, etc., to reduce leakage risk, avoid tampering and forgery, improve stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
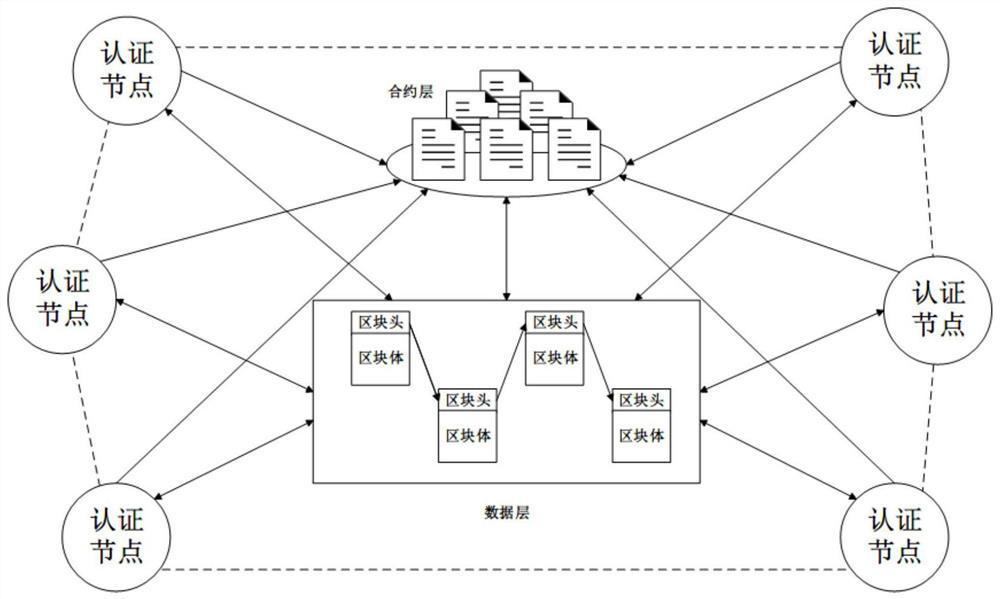
[0039] refer to figure 1 , this example consists of six server nodes with identical functions and permissions, that is, authentication nodes. Each authentication node includes a contract layer and a data layer. The authentication nodes communicate through the P2P network, and the system coordinates the work between the authentication nodes through a consensus mechanism. The contract layer deploys the blockchain real-name authentication smart contract and the blockchain access authentication smart contract, and provides a calling interface for the real-name authentication module and the access verification module. The data layer stores user information in the form of "block + chain".
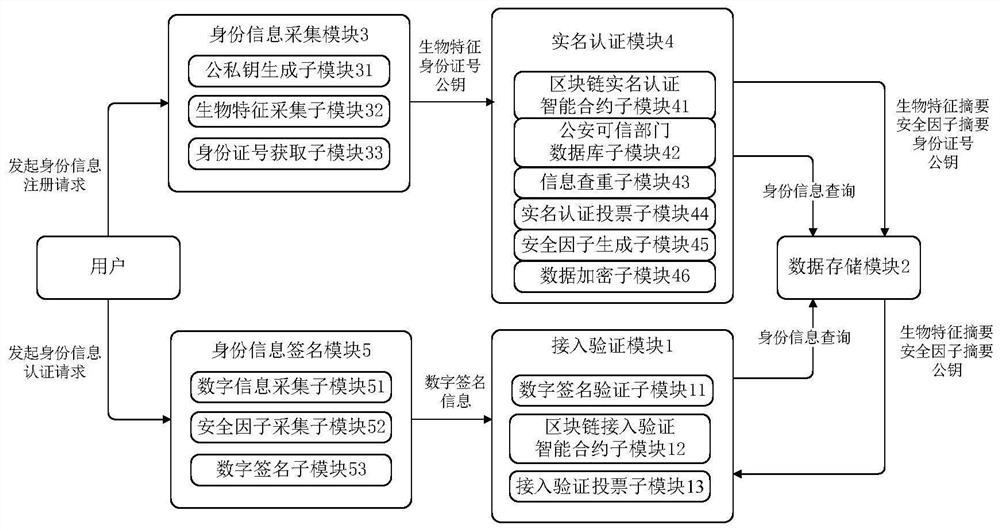
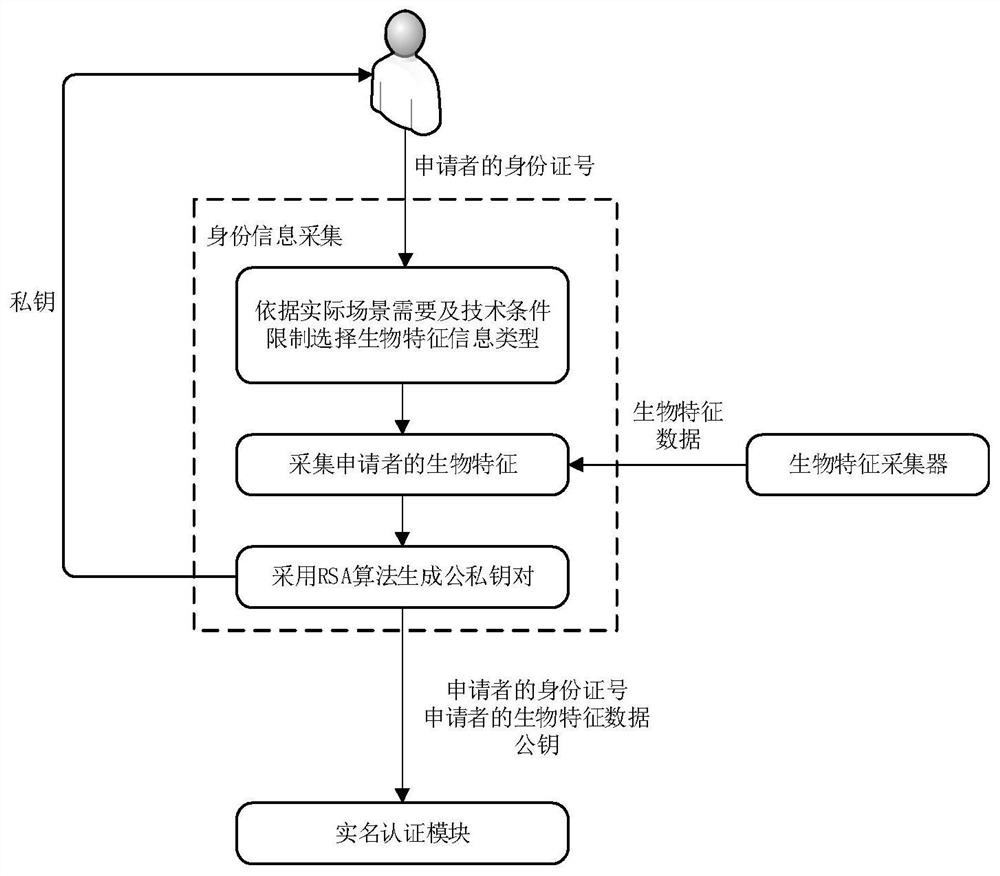
[0040] refer to figure 2 , each authentication node in this example is composed of multiple functional modules, including: access verification modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com