Patents
Literature
76results about How to "Reduce the risk of being leaked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
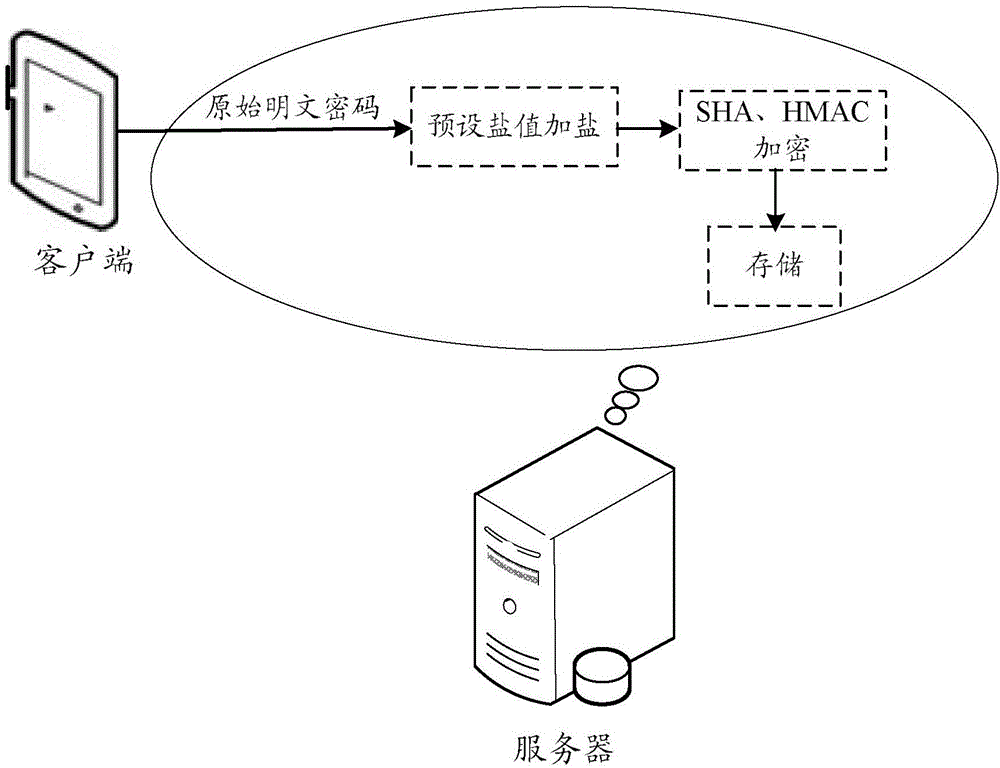
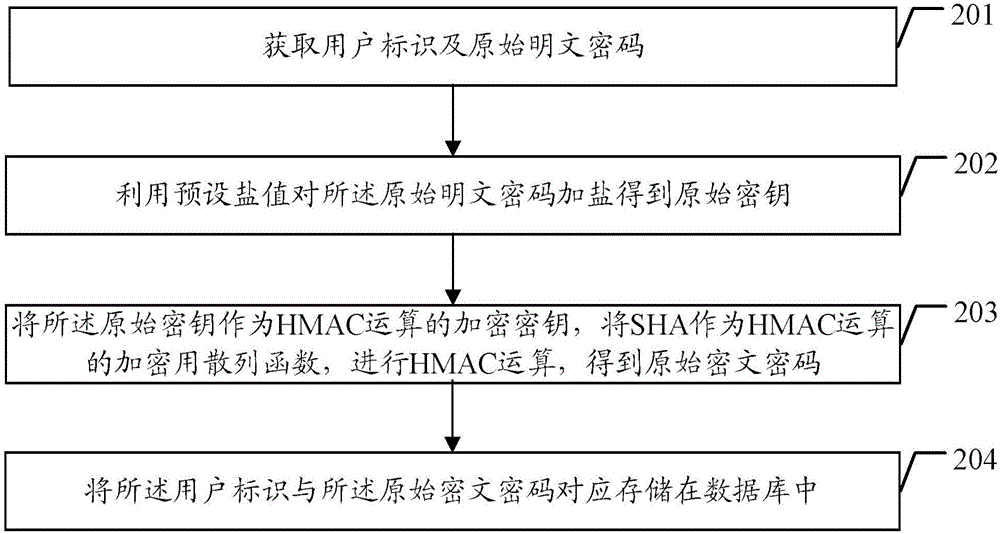
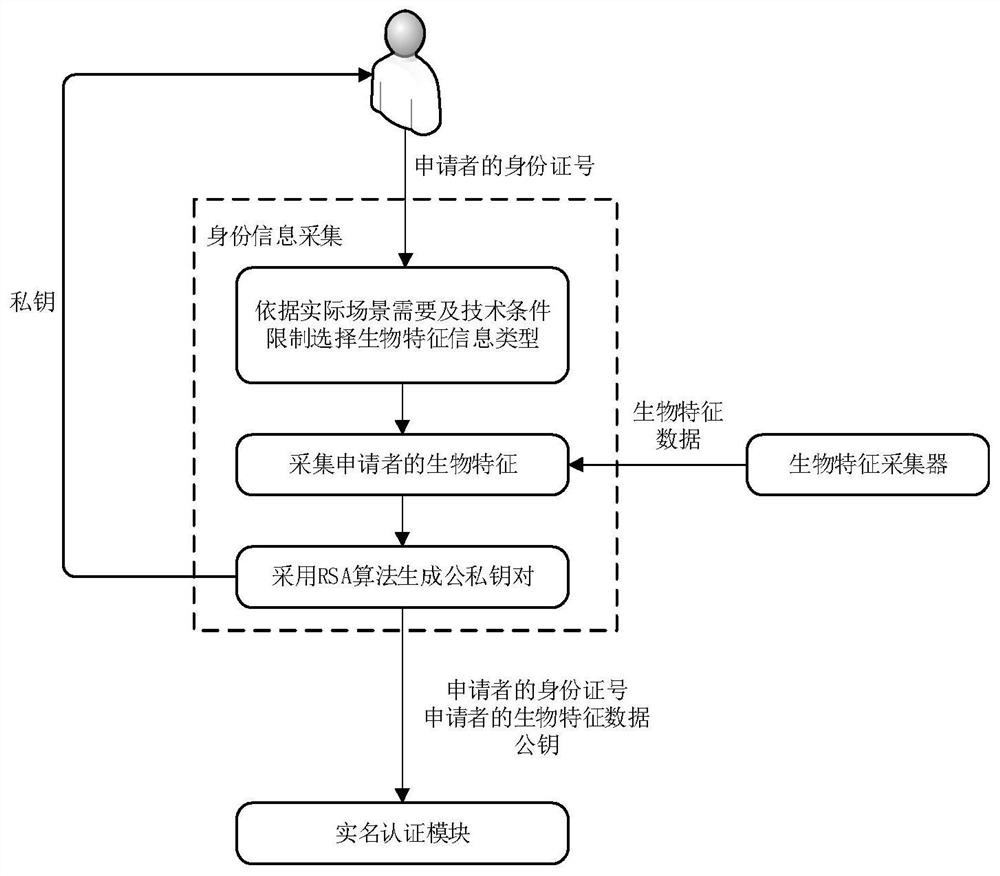
Password protecting method and device
ActiveCN106656476AEnsure safetyReduce the risk of being leakedKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionPassword
The embodiment of the present invention discloses a password protecting method and device, wherein, the password protecting method comprises: obtaining user identification and an original clear text password; adding salts to the original clear text password with a preset salt value to obtain an original key; using the original key as an encryption key of Hash-based message authentication code HMAC operation; using a secure Hash algorithm SHA as an encryption hash function of the HMAC operation to carry out the HMAC operation to obtain an original cryptograph password; and storing the user identification and the original cryptograph password correspondingly in a database. The embodiment of the present invention is able to assure the password security, and reduce the risk of password disclosing.
Owner:TENCENT TECH (SHENZHEN) CO LTD
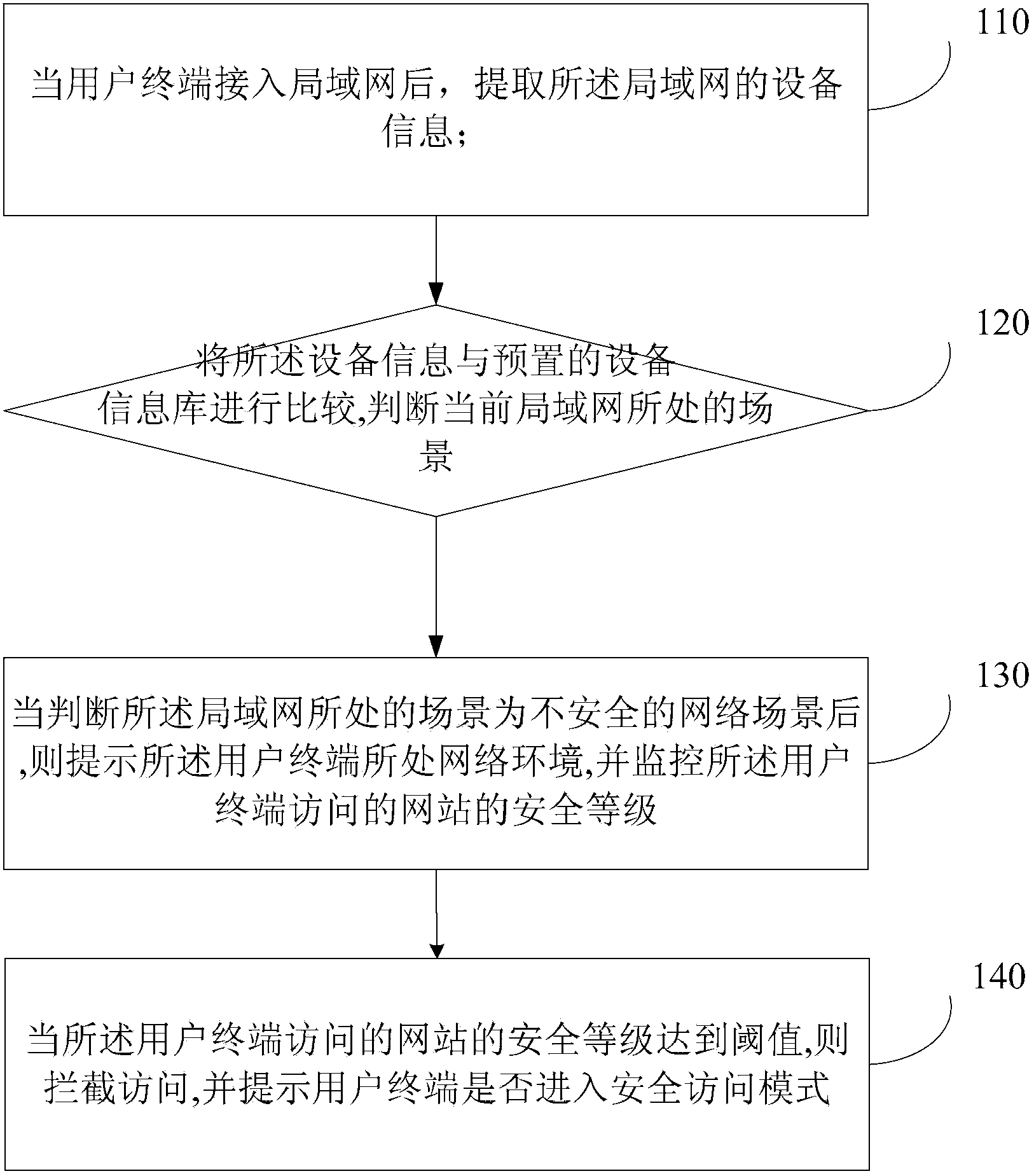
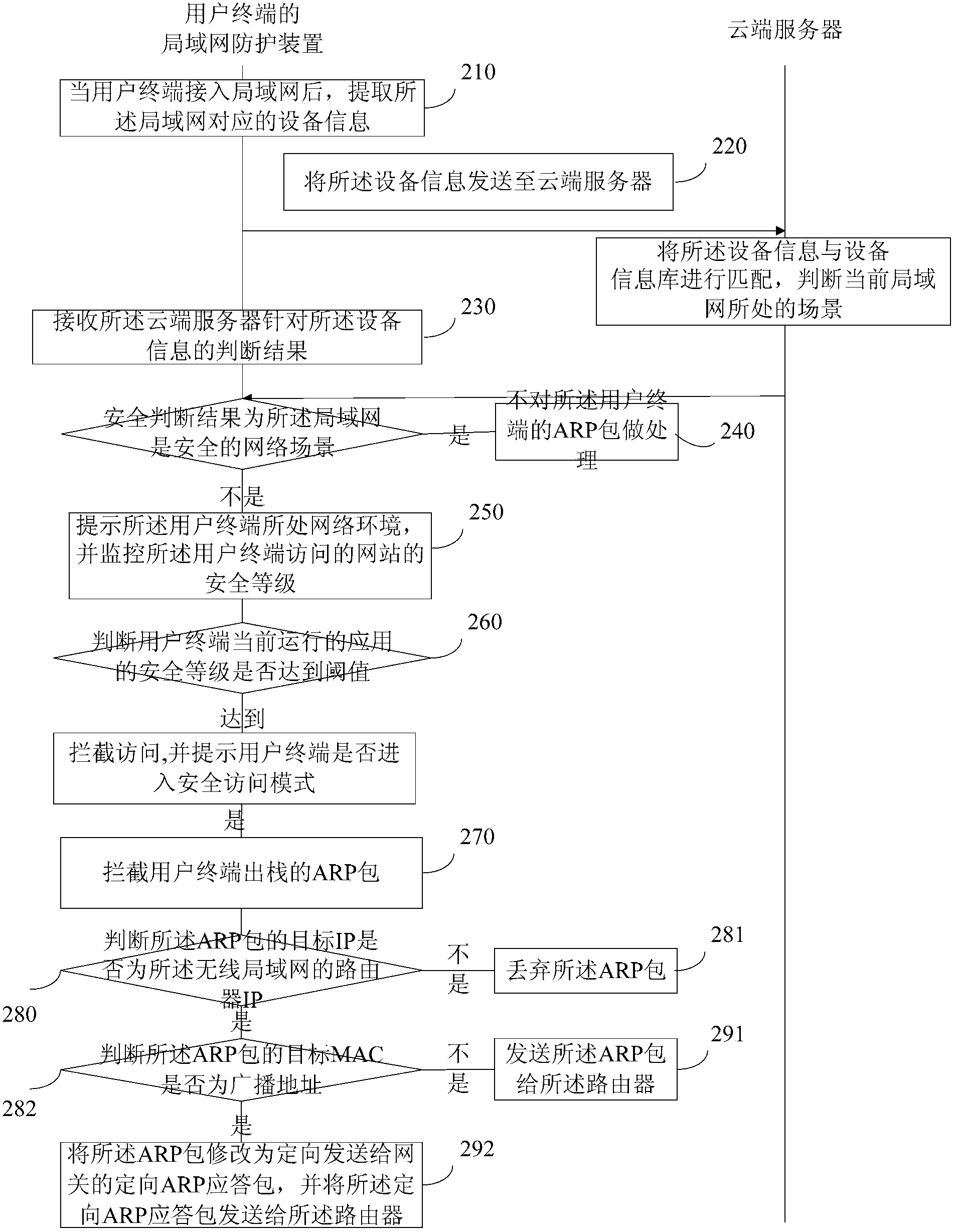
User network access scenario-based protection method and device
ActiveCN103368941ASolve the problem of exposure to other terminals in the LANFix security issuesTransmissionSecurity arrangementScenario basedWeb environment
The invention discloses a user network access scenario-based protection method and device and relates to the field of computer safety. The method comprises the following steps of extracting a device identification which corresponds to a local area network after a user terminal is accessed to the local area network; comparing the device identification with a preset device identification library to judge a scenario in which the current local area network is located; prompting a network environment in which the user terminal is located after the scenario in which the local area network is located is judged to be an unsafe scenario, and monitoring the safety level of the network accessed by the user terminal; and intercepting access when the safety level of the network accessed by the user terminal reaches a threshold value, and promoting whether the user terminal enters a safety access mode. The method and the device disclosed by the invention have the beneficial effects that the risk that the information of the user terminal leaks is lowered, and the safety of the information of the user terminal is enhanced.
Owner:BEIJING QIHOO TECH CO LTD
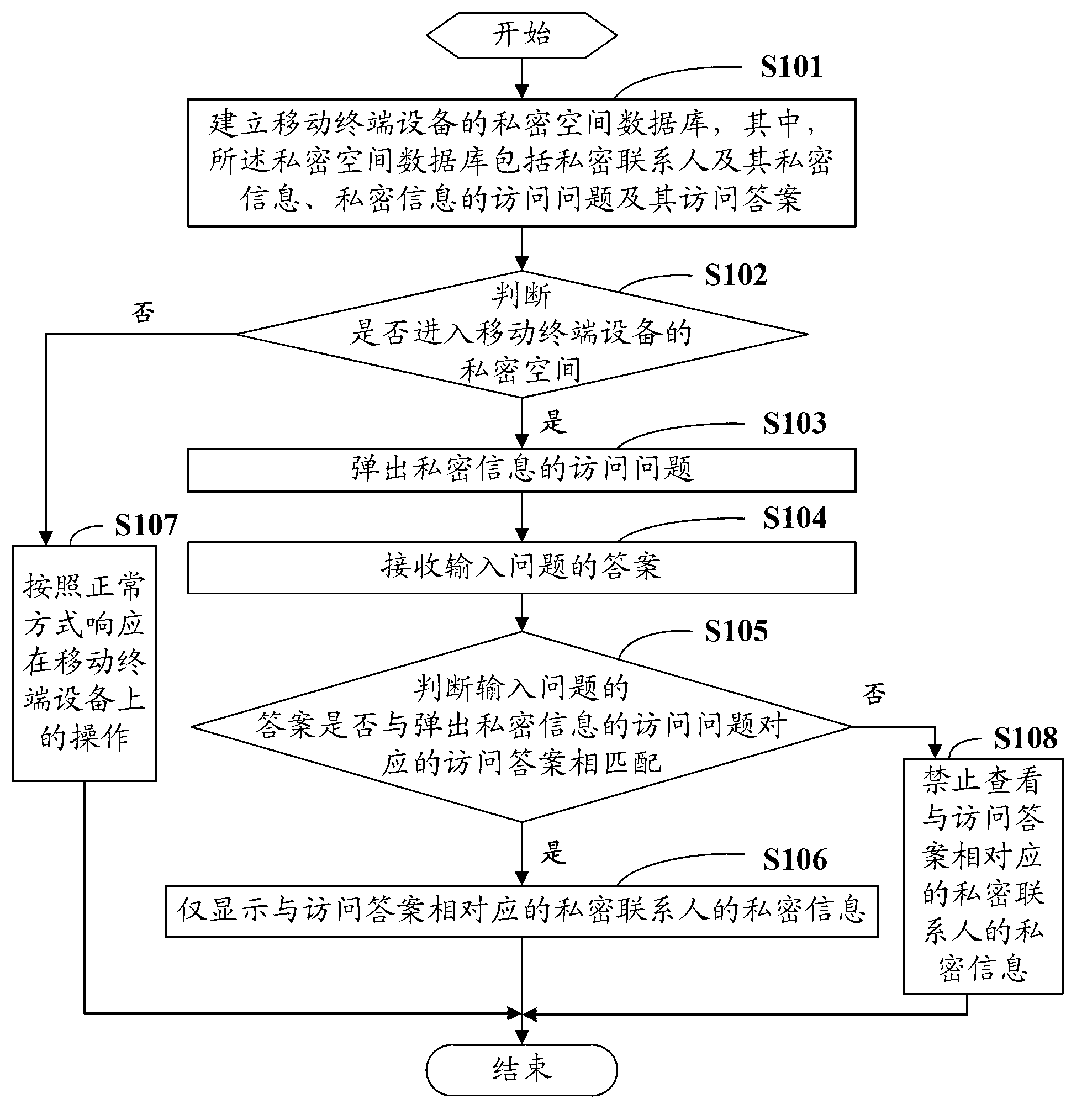
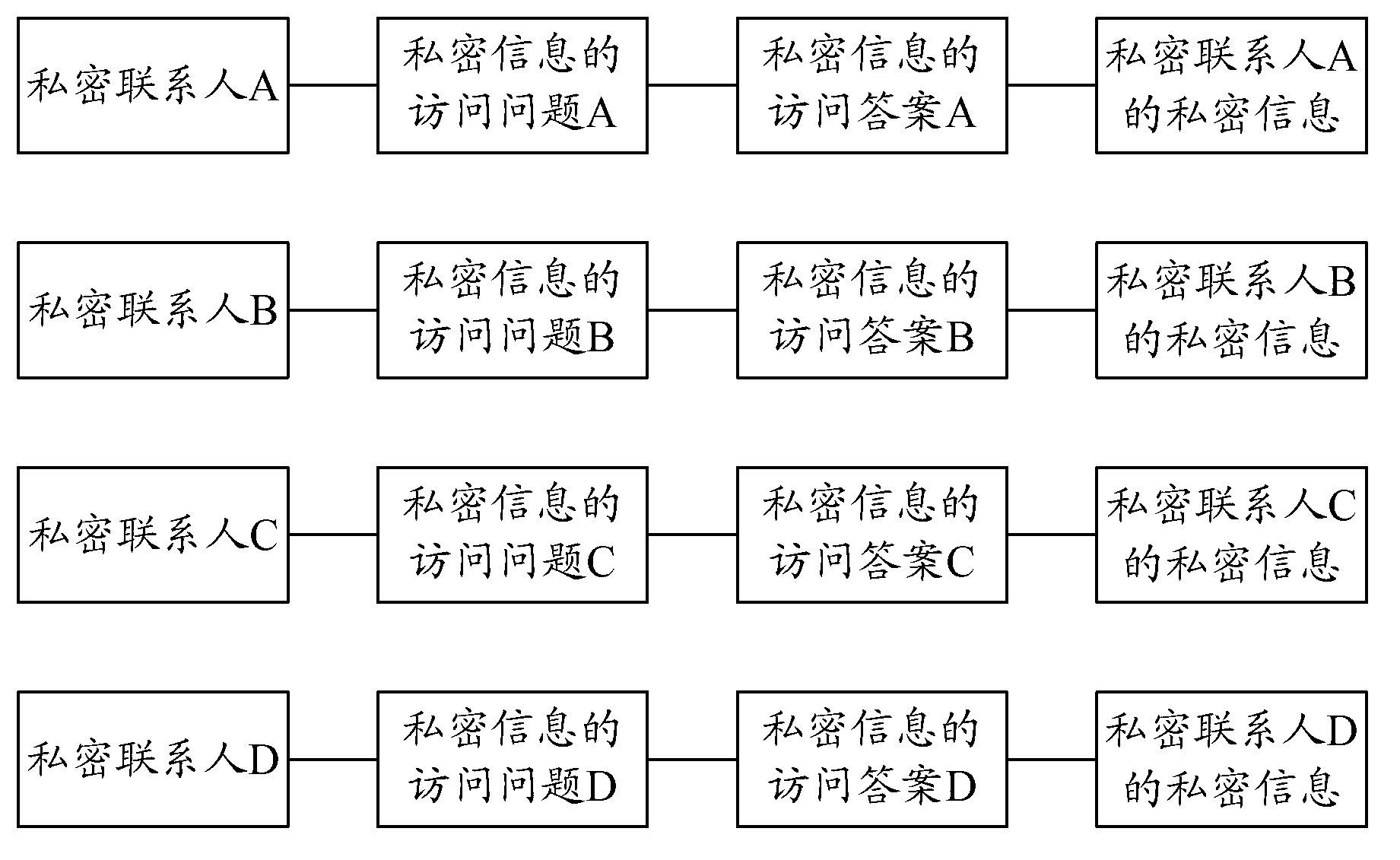
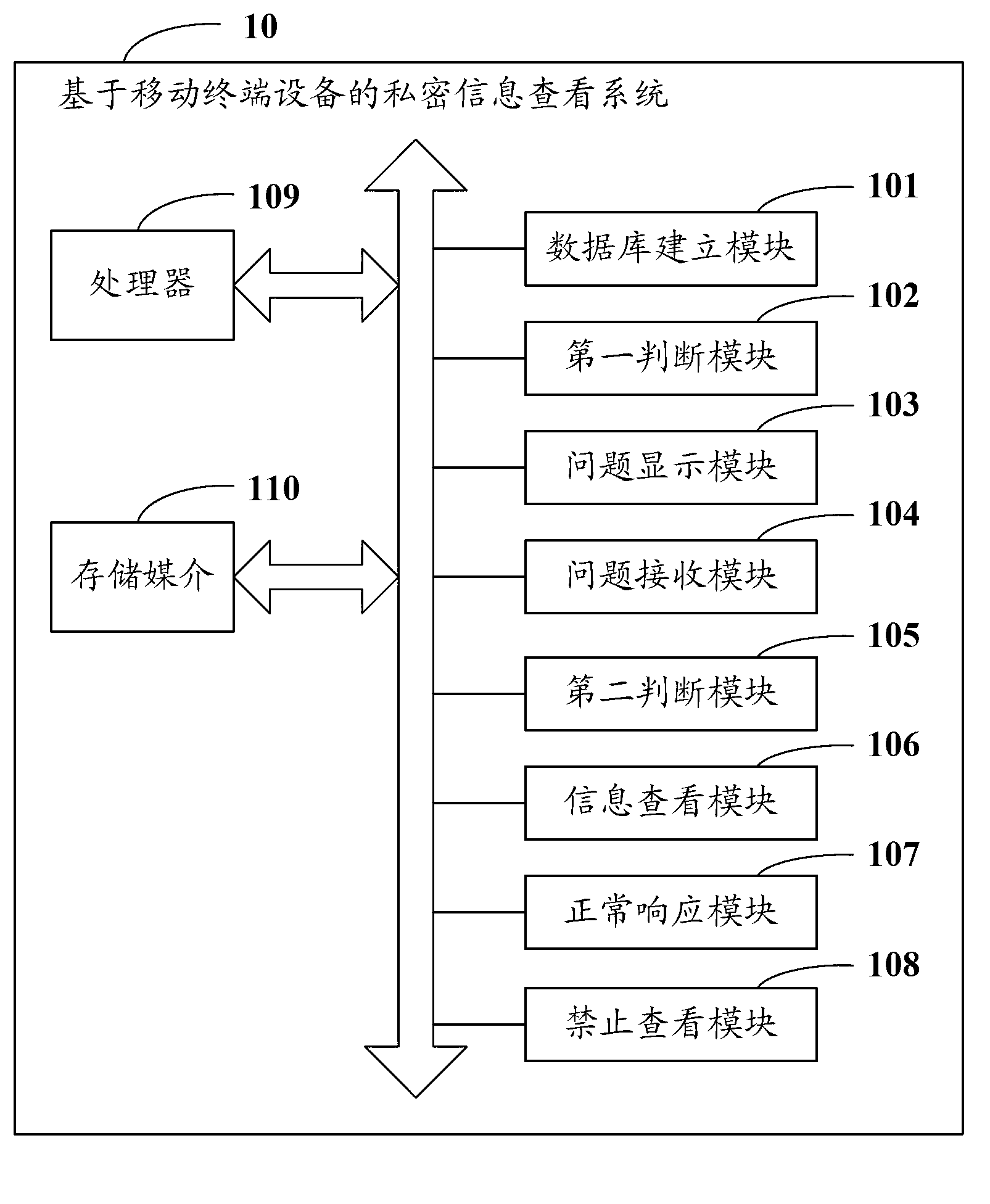
Private information viewing method and system based on mobile terminal equipment
InactiveCN103067612AImprove protectionImprove securitySubstation equipmentTerminal equipmentSpatial database
The invention is suitable for the field of communication and provides a private information viewing method. The private information viewing method comprises the following steps of: establishing a private space database of the mobile terminal equipment, wherein the private space database comprises private linkmen and private information thereof, access problems of private information and access answers of access problems; judging whether to enter a private space of the mobile terminal equipment; if entering the private space of the mobile terminal equipment, propping out an access problem of private information; receiving an answer of the input problem; judging whether the answer of the input problem is matched with the access answer corresponding to the access problem of the private information; and if so, only displaying the private information of the private linkmen corresponding to the access answer. The invention also provides a private information viewing system based on the mobile terminal equipment. The private information viewing method and system based on the mobile terminal equipment, provided by the invention, can be used for better protecting the private information of the private linkmen of the users.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
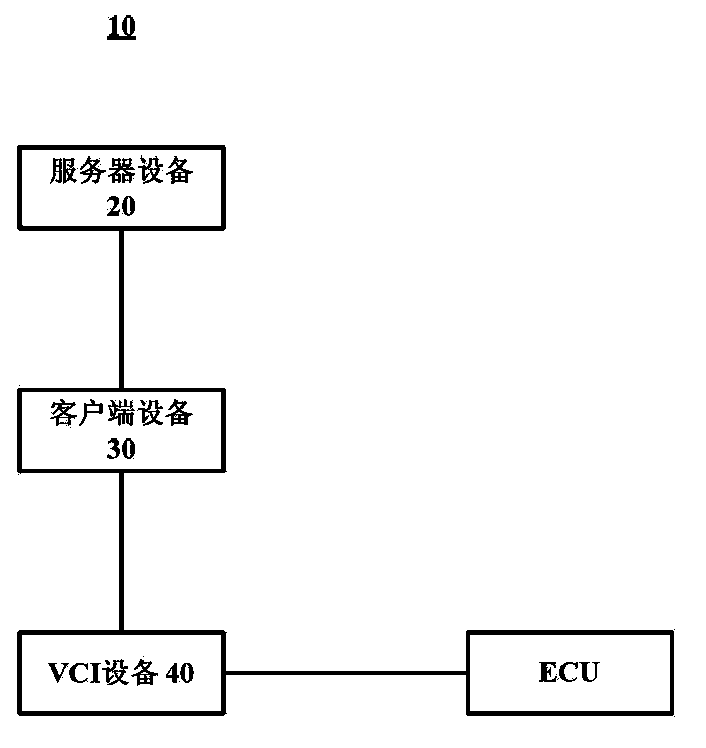
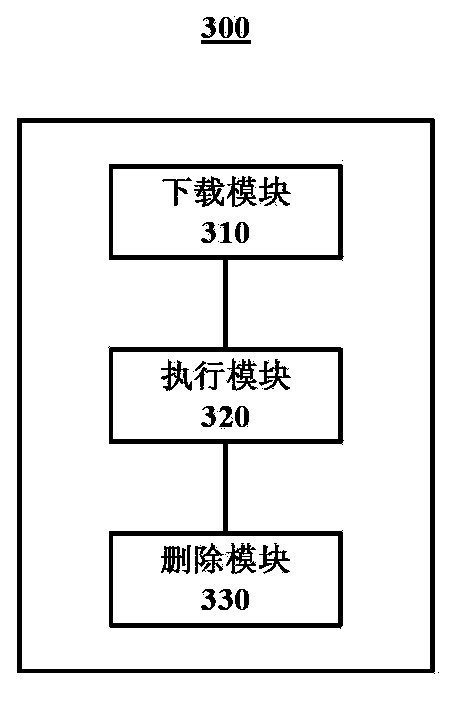
Method and device for vehicle diagnosis
InactiveCN103576668AReduce the risk of being leakedImprove securityElectric testing/monitoringReal-time computingServer appliance
The invention relates to a method and device for vehicle diagnosis. The device comprises a downloading module, an execution module and a deletion module, wherein the downloading module is used for downloading a database containing data of a vehicle model which a specified vehicle belongs to from a server device when the vehicle diagnosis is conducted on the specified vehicle; the execution module is used for conducting the vehicle diagnosis on the specified vehicle according to the downloaded database; the deletion module is used for deleting the downloaded database after the vehicle diagnosis is completed. By means of the method and device for the vehicle diagnosis, the security of the vehicle diagnosis can be enhanced.
Owner:博世汽车服务技术(苏州)有限公司
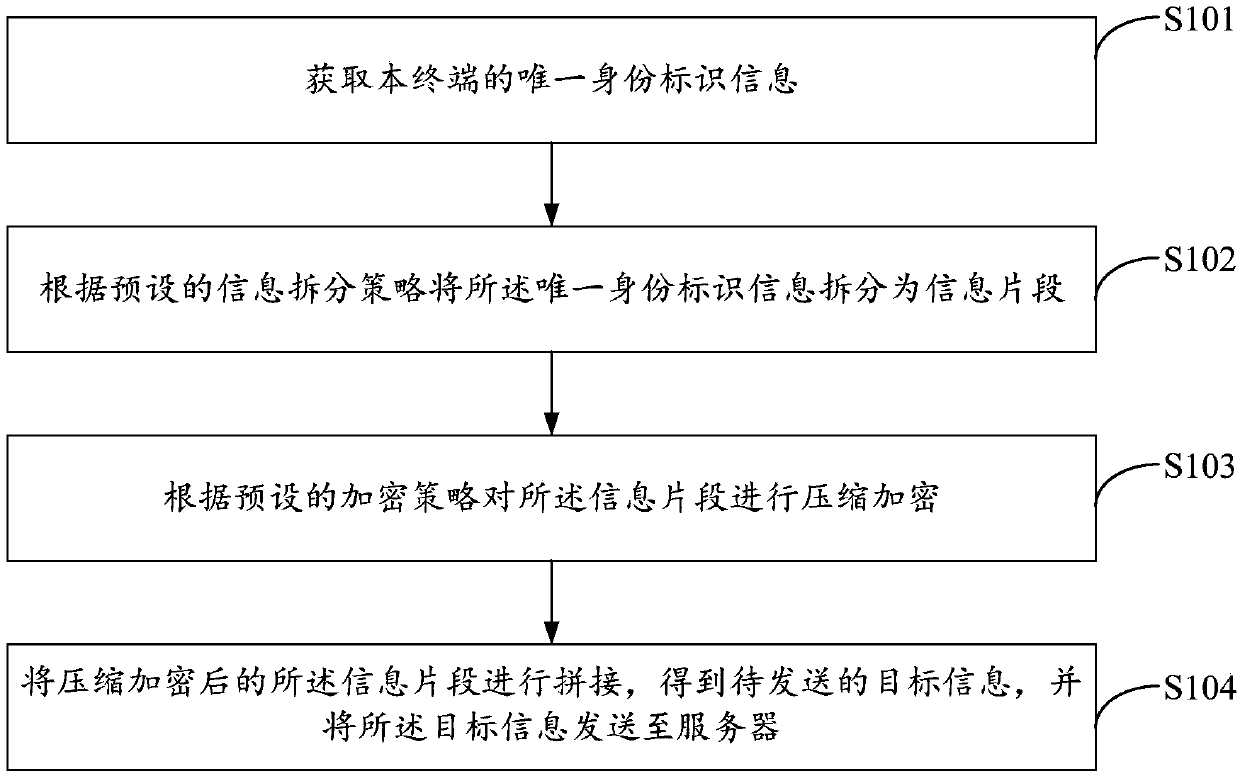
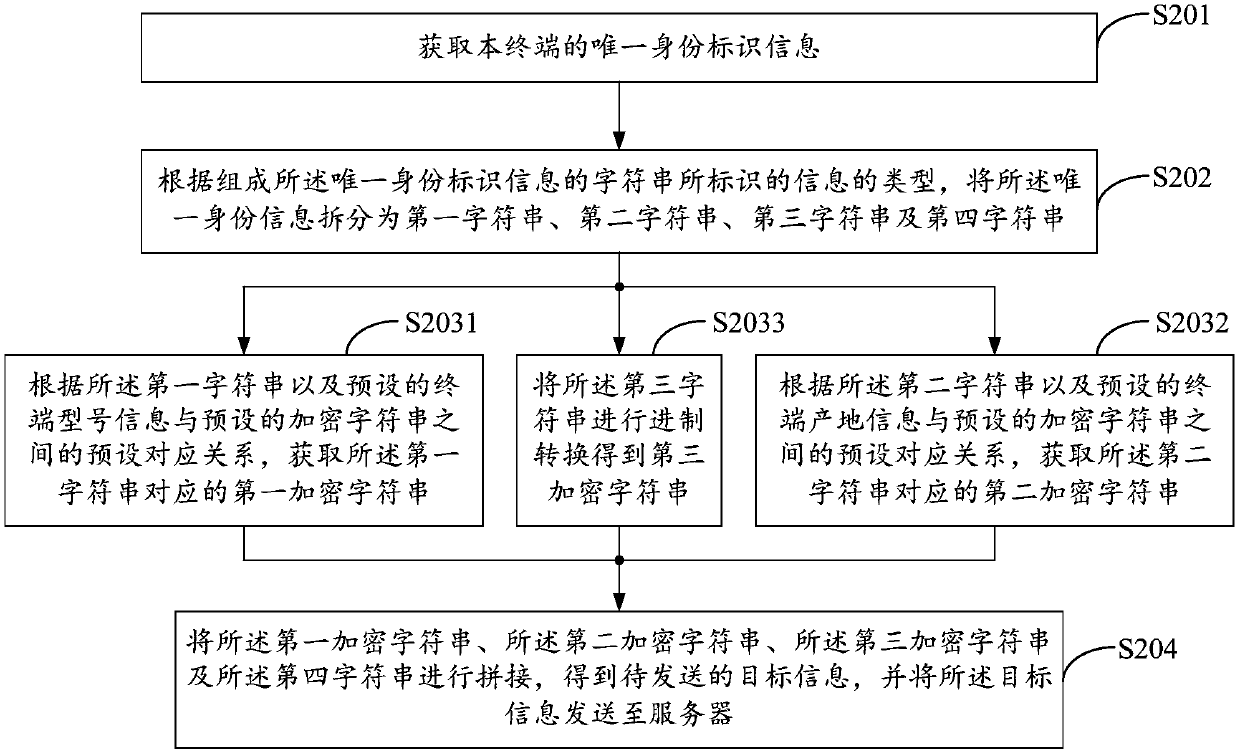
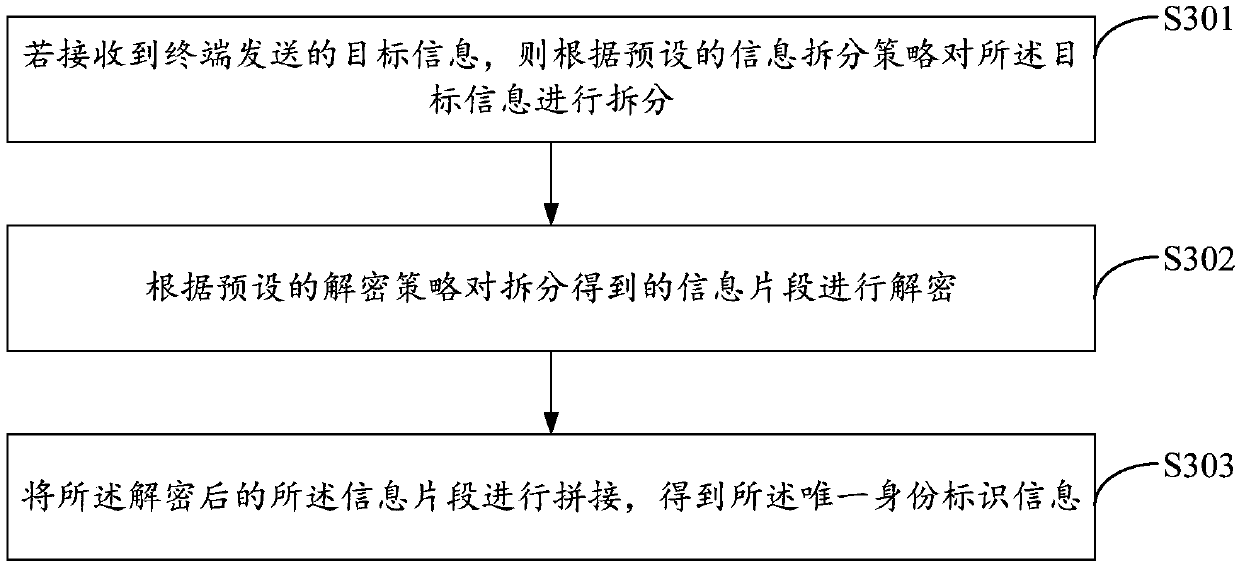
Method for processing information, terminal, and server
InactiveCN107592636AImprove securityReduce the risk of being leakedSecurity arrangementTraffic volumeUnique identifier
The embodiment of the invention discloses a method for processing information, a terminal, and a server. The method comprises: unique identifier information of a terminal is obtained; according to a preset information splitting strategy, the unique identifier information is split into information segments; compression and encryption are carried out on the information segments according to a presetencryption strategy; and then the compressed and encrypted information segments are spliced to obtain to-be-sent target information and then the target information is sent to a server. When the terminal sends own unique identifier information to the server, the unique identifier information is compressed and encrypted and then the compressed and encrypted information is sent out, so that the dataflow needed for sending information by the terminal is saved; and safety of the unique identifier information is improved and the risk of leak of the unique identifier information is reduced.
Owner:深圳市诚壹科技有限公司
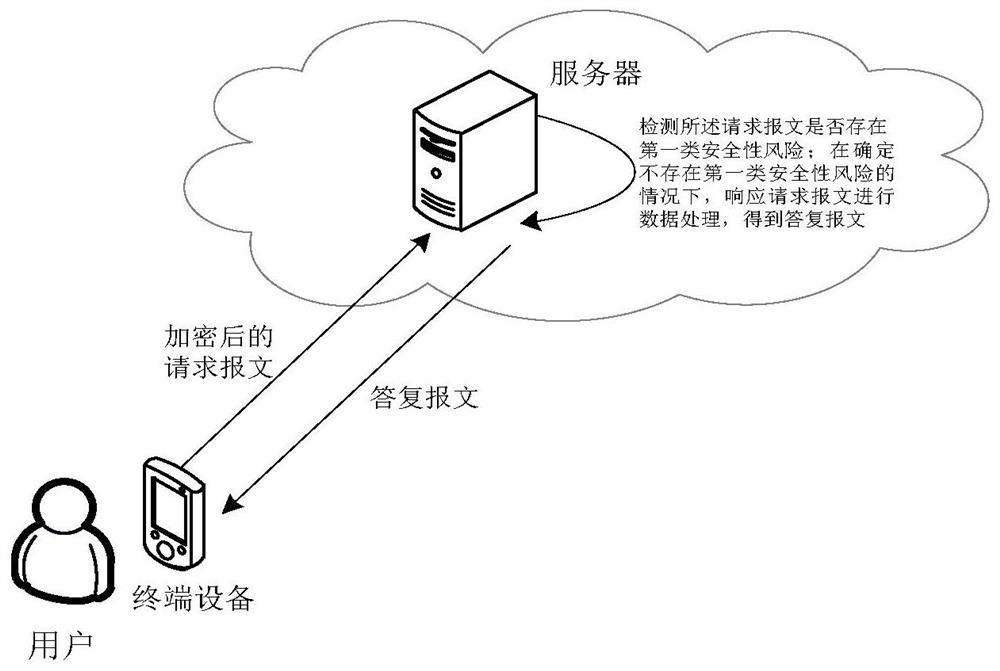
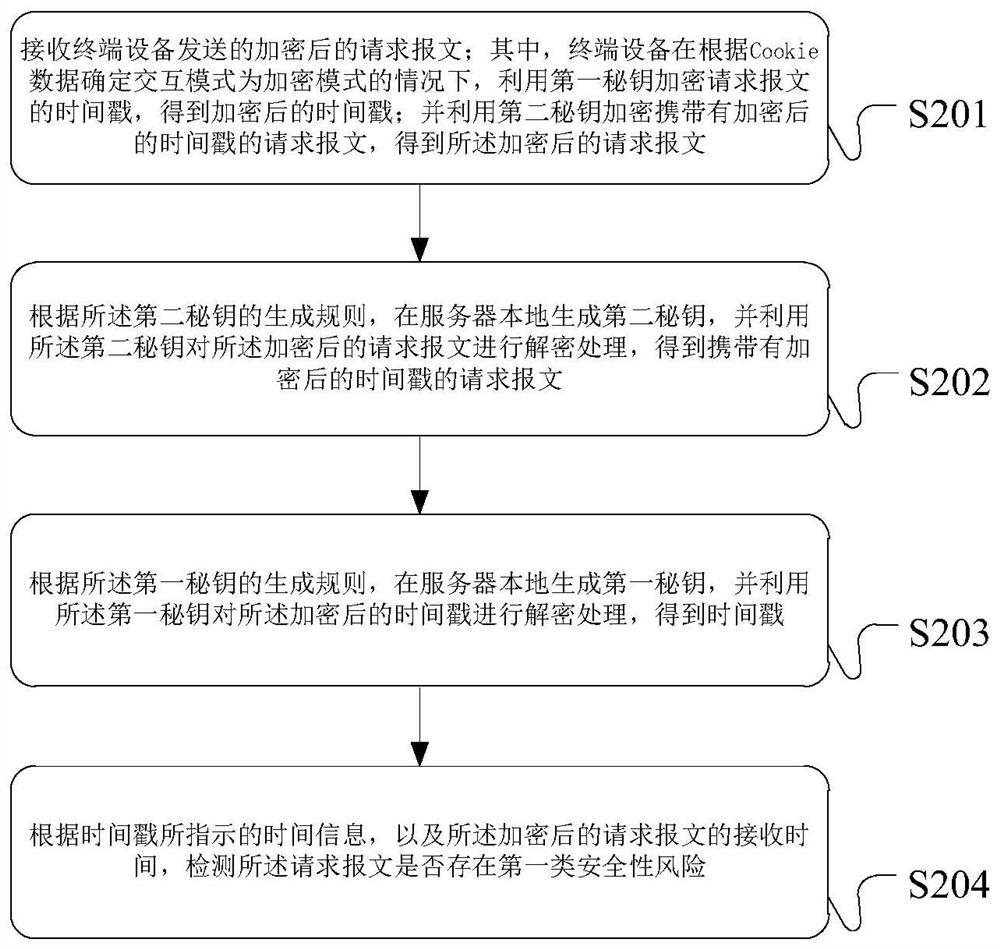
Message data processing method and device, server and terminal equipment
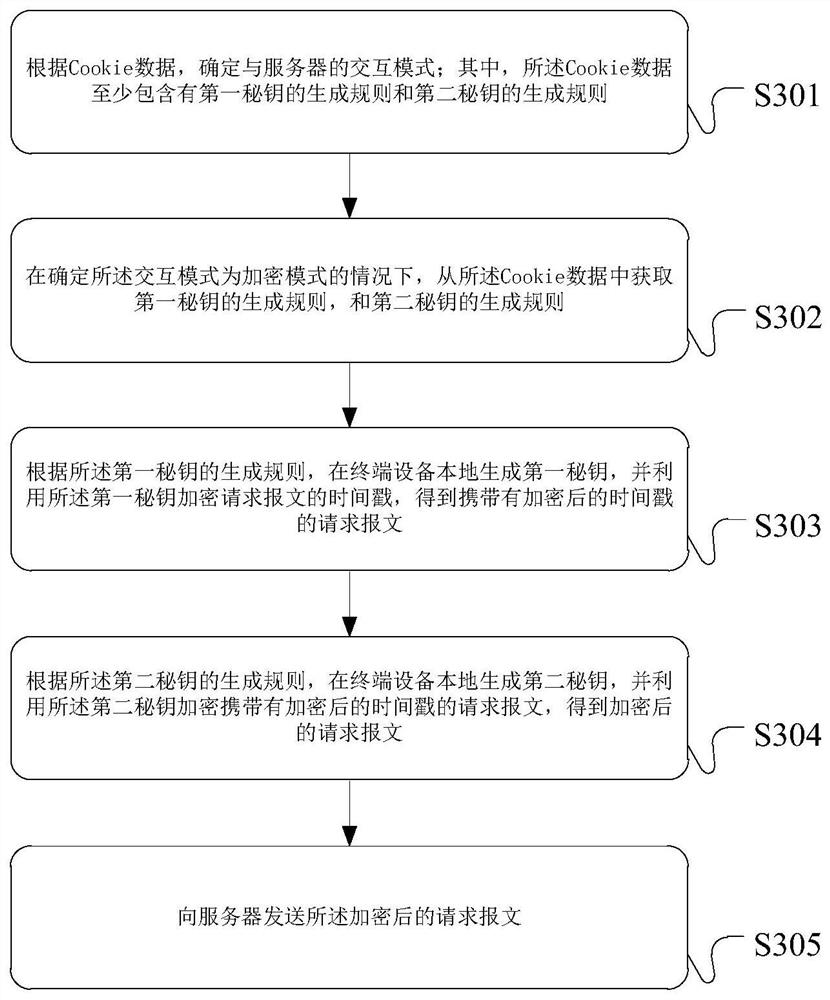
ActiveCN112217835APrevent tamperingPrevent leakageEncryption apparatus with shift registers/memoriesUser identity/authority verificationTime informationTerminal equipment
The invention provides a message data processing method and device, a server and terminal equipment. Based on the method, a server sends Cookie data at least containing a generation rule of a first secret key and a generation rule of a second secret key to the terminal equipment in advance; in this way, the server and the terminal equipment can generate the first secret key and the second secret key locally, interactive transmission of the secret keys is not needed, and the risk that the secret keys are leaked is reduced; moreover, before sending the request message, the terminal equipment encrypts the request message carrying the timestamp by using the first secret key and the second secret key; after receiving the encrypted request message, the server decrypts the encrypted request message by using the first secret key and the second secret key to obtain a timestamp; whether the request message has the security risk or not is detected according to the time information indicated by the timestamp and the receiving time of the encrypted request message, so that the request message with the security risk can be accurately detected with relatively low processing cost, and the data security is protected.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Processing method and device for file / application program on mobile communication terminal
ActiveCN103514396AReduce the risk of being leakedEasy to operateDigital data protectionPlatform integrity maintainanceTime rangeApplication software
The invention discloses a processing method and device for a file / application program on a mobile communication terminal. The method includes the steps that events which change in distance relative to the mobile communication terminal of other objects except the mobile communication terminal and operated events of the file / application program are monitored; if the events of the file / application program are monitored, and the events which change in distance are monitored within a preset time range, the operated file / application program is determined as an object needing to serve as privacy information to be protected; corresponding protection operation is carried out on the operated file / application program according to a preset privacy protection operating mode to prevent the operated file / application program to be revealed. Through the processing method and device, privacy information of users can be effectively protected in a process that files / application programs needing to serve as privacy information on terminal equipment are protected.
Owner:BEIJING QIHOO TECH CO LTD
Method and device for controlling call transfer
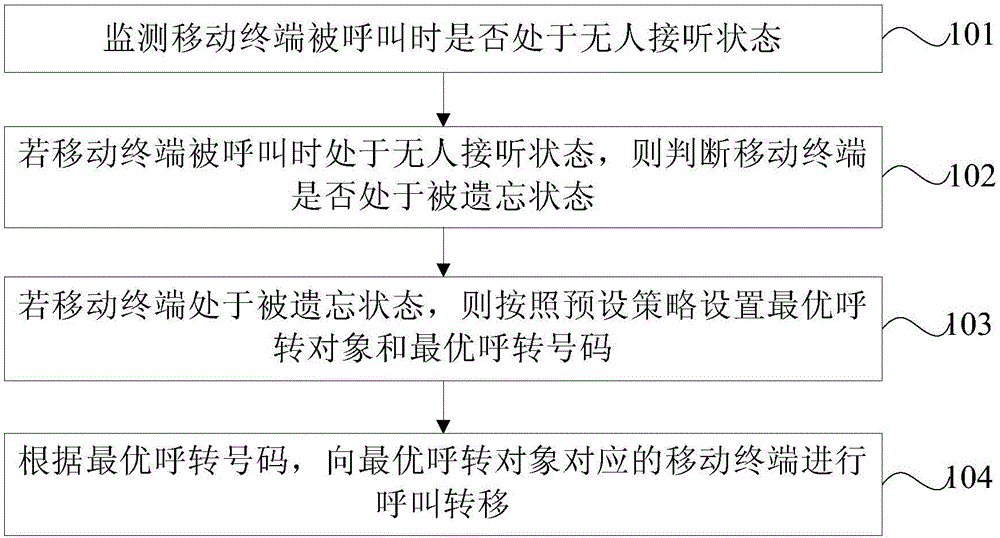
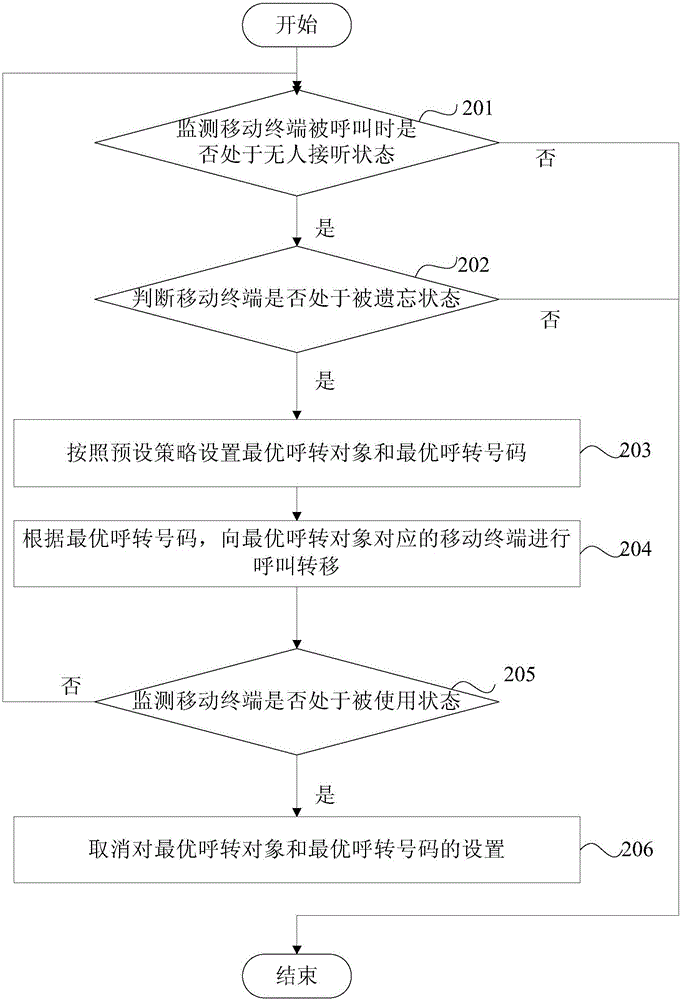
InactiveCN106332031ARealize intelligent controlReduce the risk of being leakedSpecial service for subscribersCommmunication supplementary servicesCall forwardingIntelligent control
The invention provides a method and device for controlling call transfer. The method comprises the following steps: monitoring whether a mobile terminal is in a no answer state when being called; if the mobile terminal is in the no answer state when being called, judging whether the mobile terminal is in a forgotten state; if the mobile terminal is in the forgotten state, setting an optical call transfer object and an optimal call transfer number according to a preset strategy; and carrying out call transfer on the mobile terminal corresponding to the optical call transfer object according to the optimal call transfer number. When the mobile terminal is monitored to be in the forgotten state, the optical call transfer object and the optimal call transfer number are automatically set, and the call transfer is carried out on the mobile terminal corresponding to the optical call transfer object to realize the intelligent control f the cal transfer. Moreover, the others are not contacted necessarily to help to configure the call transfer number, thereby simplifying the operations, reducing the leakage risk of personal information and improving the user experience.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
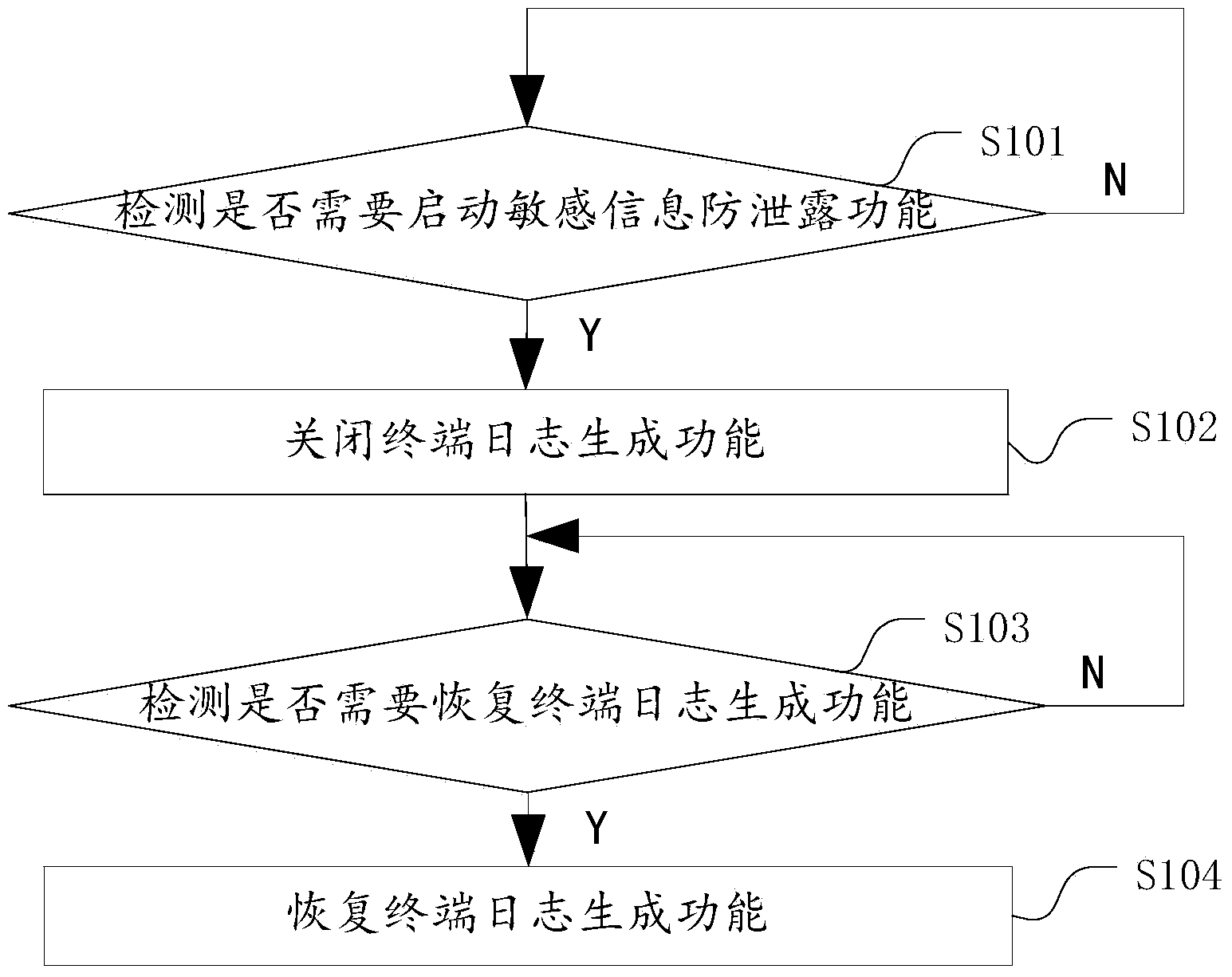
Terminal and method for preventing sensitive information leakage
ActiveCN103778377AMeet needsAvoid gettingHardware monitoringDigital data protectionComputer scienceInformation leakage
The invention discloses a terminal and a method for preventing sensitive information leakage. The terminal comprises a detection module and a log generating function control module, wherein the detection module is used for detecting whether starting a sensitive information leakproof function is needed or not; the log generating function control module is used for closing the terminal log generating function when a detecting result of the detection module is that starting the sensitive information leakproof function is needed. The method comprises the following steps: detecting whether starting the sensitive information leakproof function is needed or not; closing the terminal log generating function if starting the sensitive information leakproof function is needed. According to the technical scheme, the problem that conventional methods for preventing sensitive information leakage are not thorough is solved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
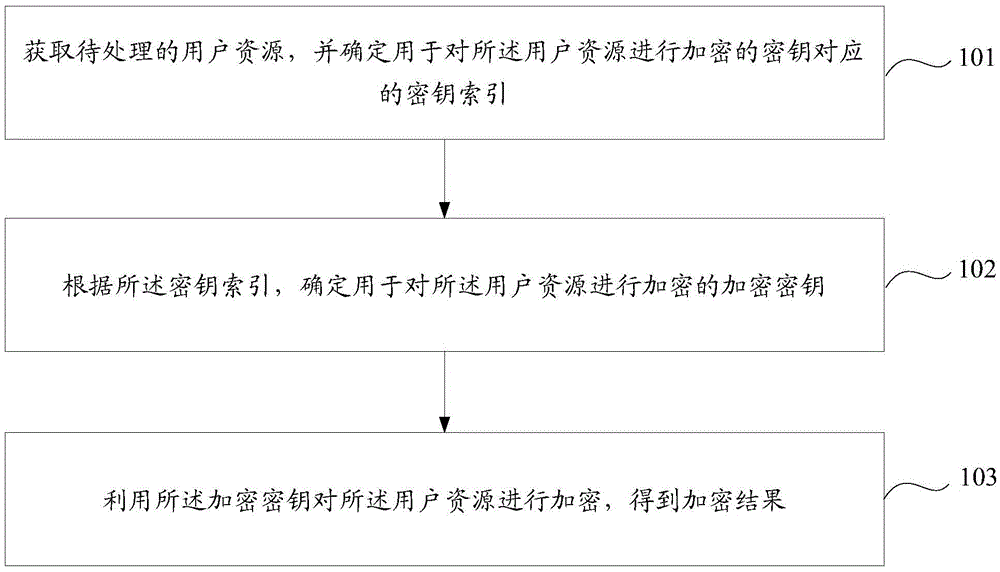
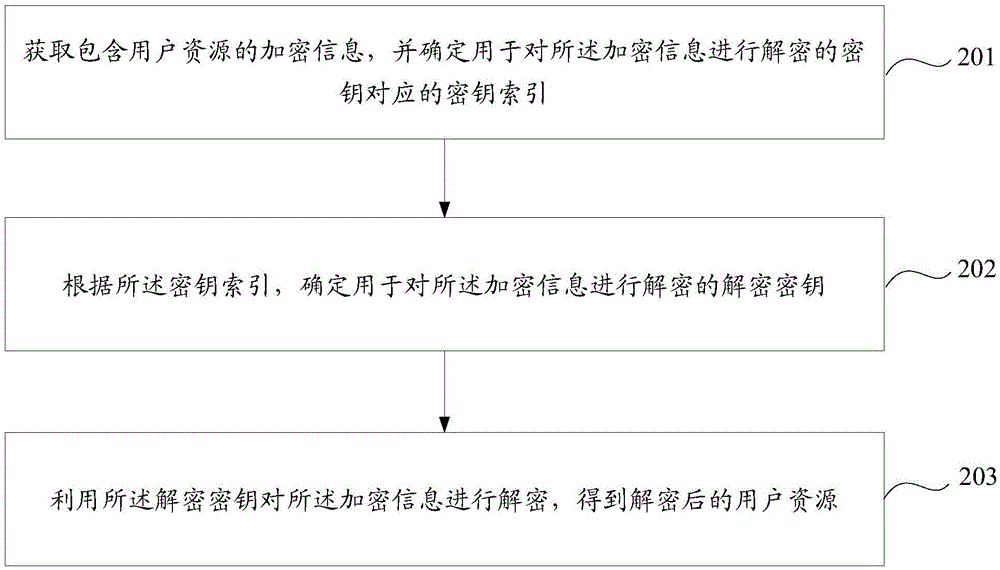
Encryption and decryption method and equipment for user resource
ActiveCN106817358AImprove securityReduce the risk of being leakedTransmissionEncryptionUser information
The invention discloses an encryption method, a decryption method, encryption equipment and decryption equipment for a user resource. The encryption method comprises the steps of: acquiring the user resource to be processed, and determining a key index corresponding to secret keys used for encrypting the user resource; determining an encryption key used for encrypting the user resource according to the key index; and utilizing the encryption key to encrypt the user resource to obtain an encryption result. Through determining the key index for the user resource, and determining the encryption key used for encrypting the user resource according to the secret keys corresponding to the key index, the probability that the encryption keys determined by the system for different user resources are different is increased, further the problem that the risk of leakage of user information in an application platform is increased because an encryption method adopted for transmitting user information between application platforms between which a cooperative relationship is established is relatively fixed in the prior art can be effectively avoided, the security of the user resources is effectively improved, and the risk of leakage of the user resources is reduced.
Owner:ADVANCED NEW TECH CO LTD
Card/ticket management method, device and equipment and computer readable storage medium
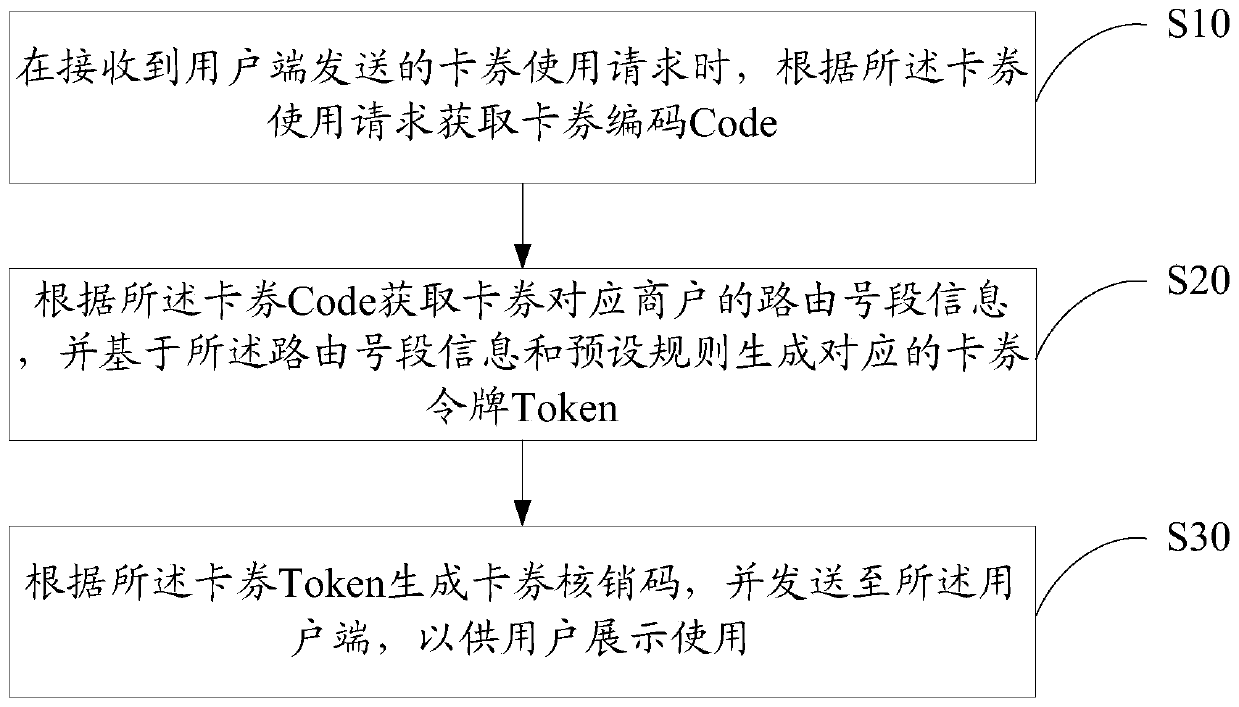
PendingCN109993524AReduce the risk of being leakedImprove securityPayment protocolsVoucherComputer science
The invention discloses a coupon management method. The card / coupon management method comprises the following steps: when a card / coupon use request sent by a user side is received, obtaining a card / coupon code Code according to the card / coupon use request; obtaining routing number segment information of a merchant corresponding to the card / coupon according to the card / coupon Code, and generating acorresponding card / coupon token based on the routing number segment information and a preset rule; and generating a coupon verification code according to the coupon Token, and sending the coupon verification code to the user side for display and use by the user. The invention further discloses a coupon management device and equipment and a computer readable storage medium. According to the invention, the security and flexibility of card voucher verification and sale can be improved.
Owner:WEBANK (CHINA)
Electronic bidding system and method
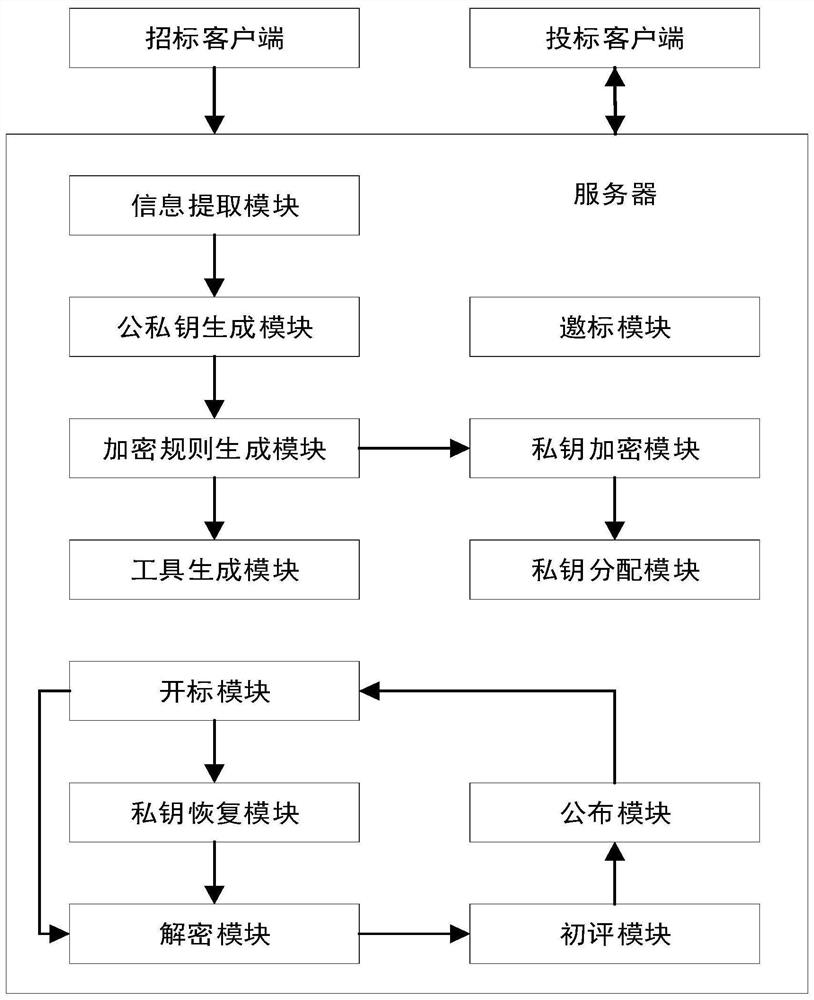
PendingCN111861473ARealize generationEasy to uploadKey distribution for secure communicationDigital data protectionInternet privacyCiphertext
The invention relates to the technical field of digital information security transmission, and particularly relates to an electronic bidding and tendering system and method. The system comprises a server, and the server is used for obtaining bid inviting information; the server is further used for generating public and private key pairs according to the bid inviting information, encrypting privatekey certificates in the public and private key pairs based on a Shamir threshold to obtain a plurality of private key ciphertext, and generating a bidding tool according to the public key certificates in the public and private key pairs; the server is also used for updating the bidding tools according to any private key ciphertext during bidding, and the updated bidding tools are in one-to-one correspondence with the private key ciphertexts; the bidding tool is used for obtaining bidding information, encrypting the bidding information to obtain a bidding ciphertext, and uploading the biddingciphertext and the private key ciphertext to the server; and the server is also used for generating a private key certificate according to the plurality of private key ciphertext based on the Shamir threshold during bid opening, and decrypting the bidding ciphertext according to the private key certificate. By adopting the scheme, the security of the private key certificate can be effectively ensured.
Owner:光奕科数据技术有限公司
Blockchain-based data sharing system
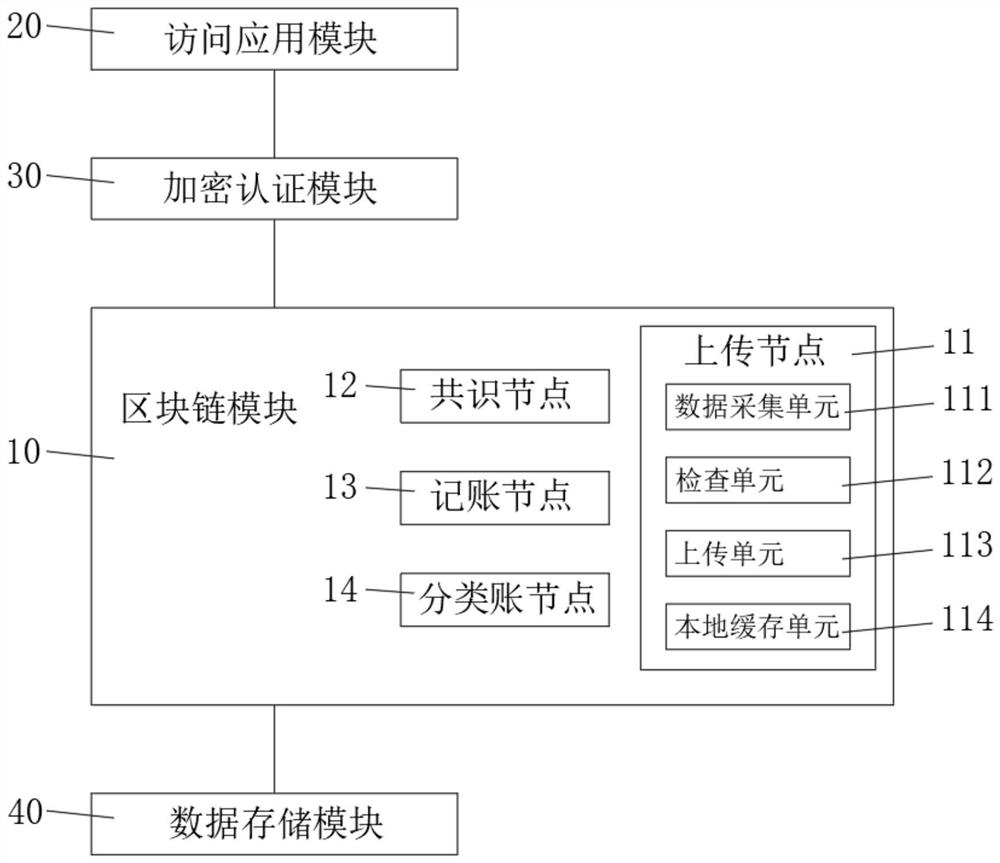
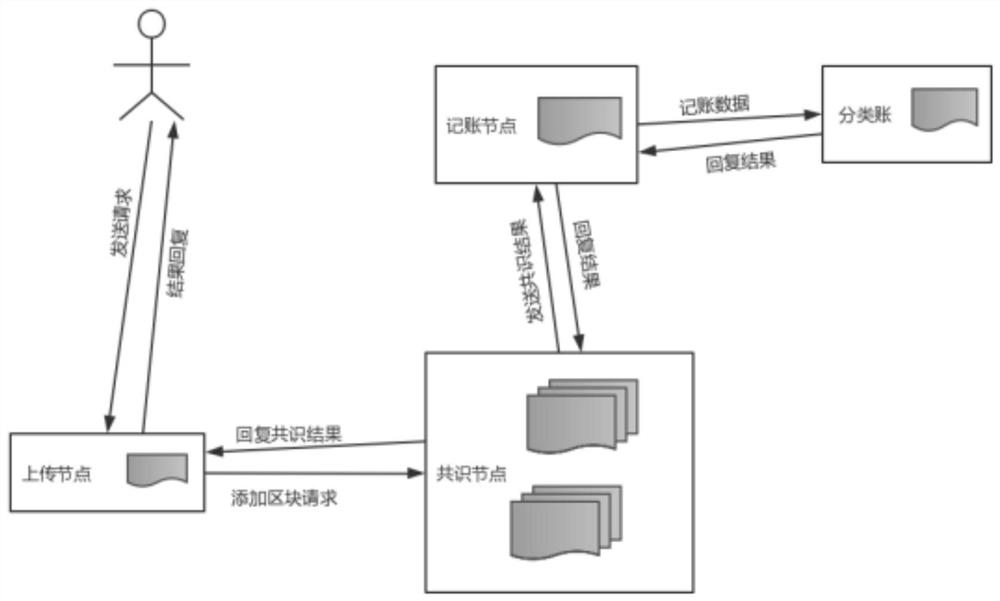
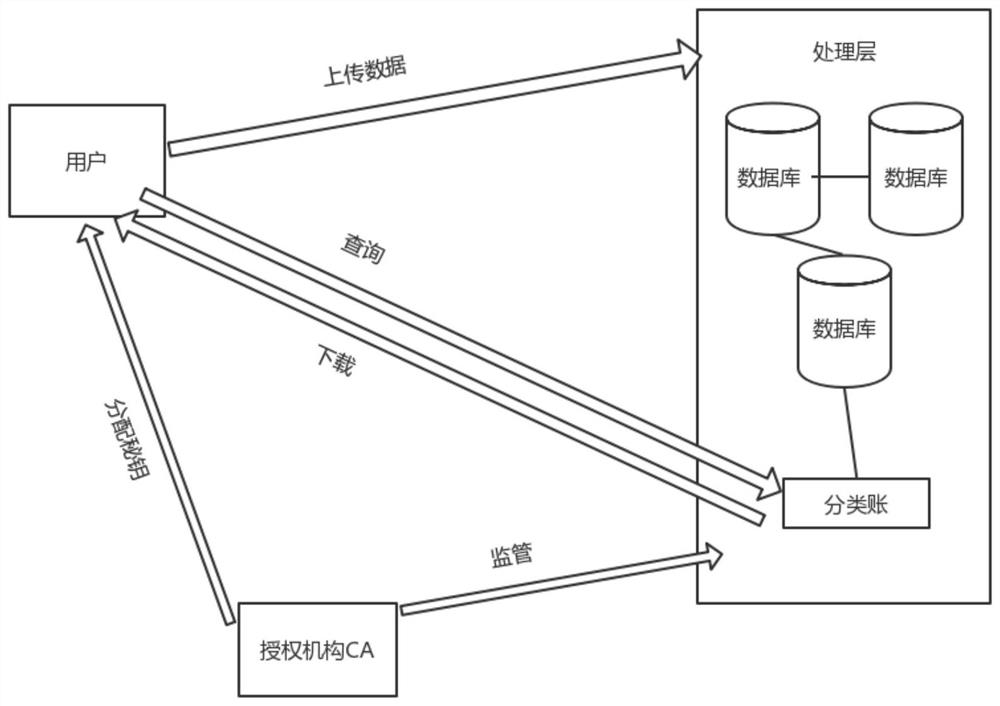
PendingCN112100665AAchieve sharingAvoid the risk of tamperingDatabase distribution/replicationDigital data protectionData accessData store
The invention belongs to the technical field of data sharing, and discloses a blockchain-based data sharing system, which comprises: a blockchain module comprising a plurality of mutually matched blockchain nodes and realizing data sharing through the blockchain nodes; an access application module which is used for providing a data access node with permission setting for a user of the sharing system, wherein the user accesses the shared data in the block chain module through the data access node; an encryption authentication module which is used for verifying whether a blockchain node in the blockchain module and a data access node in the access application module are valid or not, deleting invalid blockchain nodes and performing encryption authentication on the valid blockchain nodes; anda data storage module which is used for carrying out distributed storage on the shared data in the blockchain module and the user information in the shared system based on IPFS. In conclusion, on thebasis of the blockchain technology, data sharing is achieved, and the risk that data is tampered can be effectively avoided.
Owner:江苏四象软件有限公司
Method and device for processing document/application program on mobile communication terminal
ActiveCN103530549AEasy to operateReduce the risk of being leakedDigital data protectionPlatform integrity maintainanceTime rangePrivacy protection
The invention discloses a method and device for processing a document / application program on a mobile communication terminal. The method comprises the steps of monitoring an audio input signal of the mobile communication terminal and an operated event of the document / application program, determining the operated document / application program as an object needing to be protected as privacy information if the operated event of the document / application program is monitored and the audio input signal meeting a preset condition is monitored within a preset time range, and carrying out corresponding protection operation on the operated document / application program according to a preset privacy protection operation method to prevent the operated document / application program from being revealed. According to the method and device for processing the document / application program on the mobile communication terminal, privacy information of a user can be protected more effectively during protection of information needing to be protected as privacy information on terminal equipment.
Owner:BEIJING QIHOO TECH CO LTD
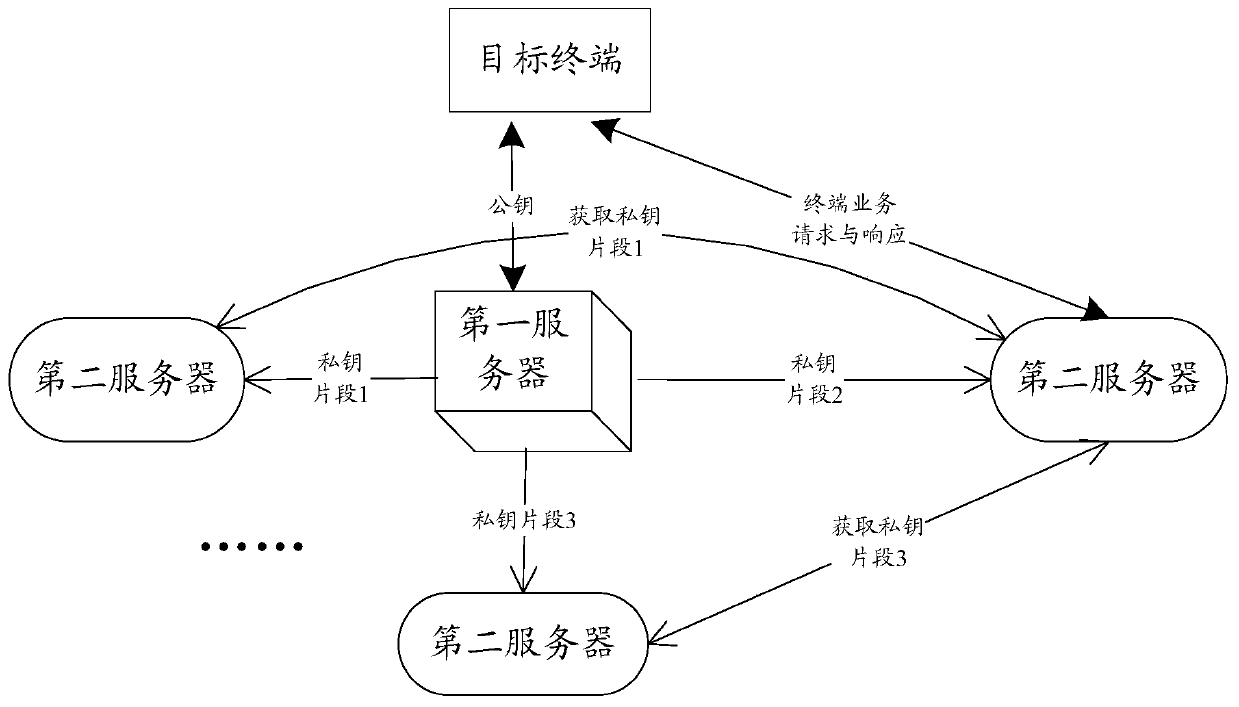
Key generation and management method and server
PendingCN110830242AIncrease the difficultyReduce the risk of being leakedKey distribution for secure communicationUser identity/authority verificationEngineeringKey generation
The invention relates to the technical field of computers, in particular to a key generation and management method and a server, which are used for solving the technical problem that a key is easy toleak. The secret key generation method comprises the steps that a corresponding secret key pair is generated at set intervals, and the secret key pair comprises a private key and a public key; and dividing the generated private key into a plurality of private key segments, respectively storing the private key segments into a plurality of second servers, and sending the generated public key to thetarget terminal. The key management method comprises the following steps: storing a corresponding private key segment; receiving a service request which is sent by the target terminal and is encryptedby adopting a public key, and determining a terminal identifier of the target terminal; obtaining private key segments corresponding to the target terminal from other second servers, and splicing theprivate key segments to obtain a complete private key; and performing decryption verification based on the private key. According to the key generation and management method and the server, the safety of the user key information is improved.
Owner:JUHAOKAN TECH CO LTD
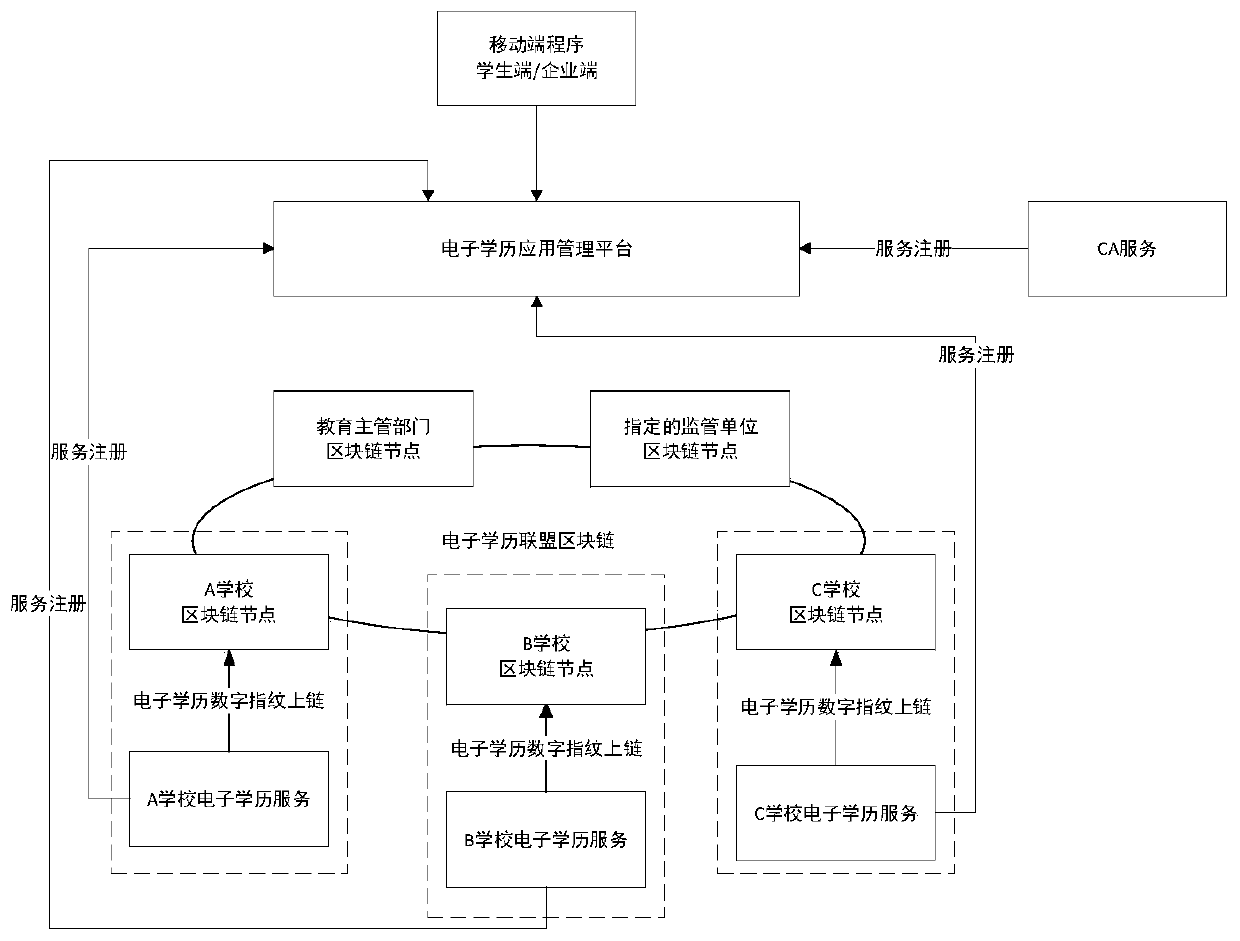
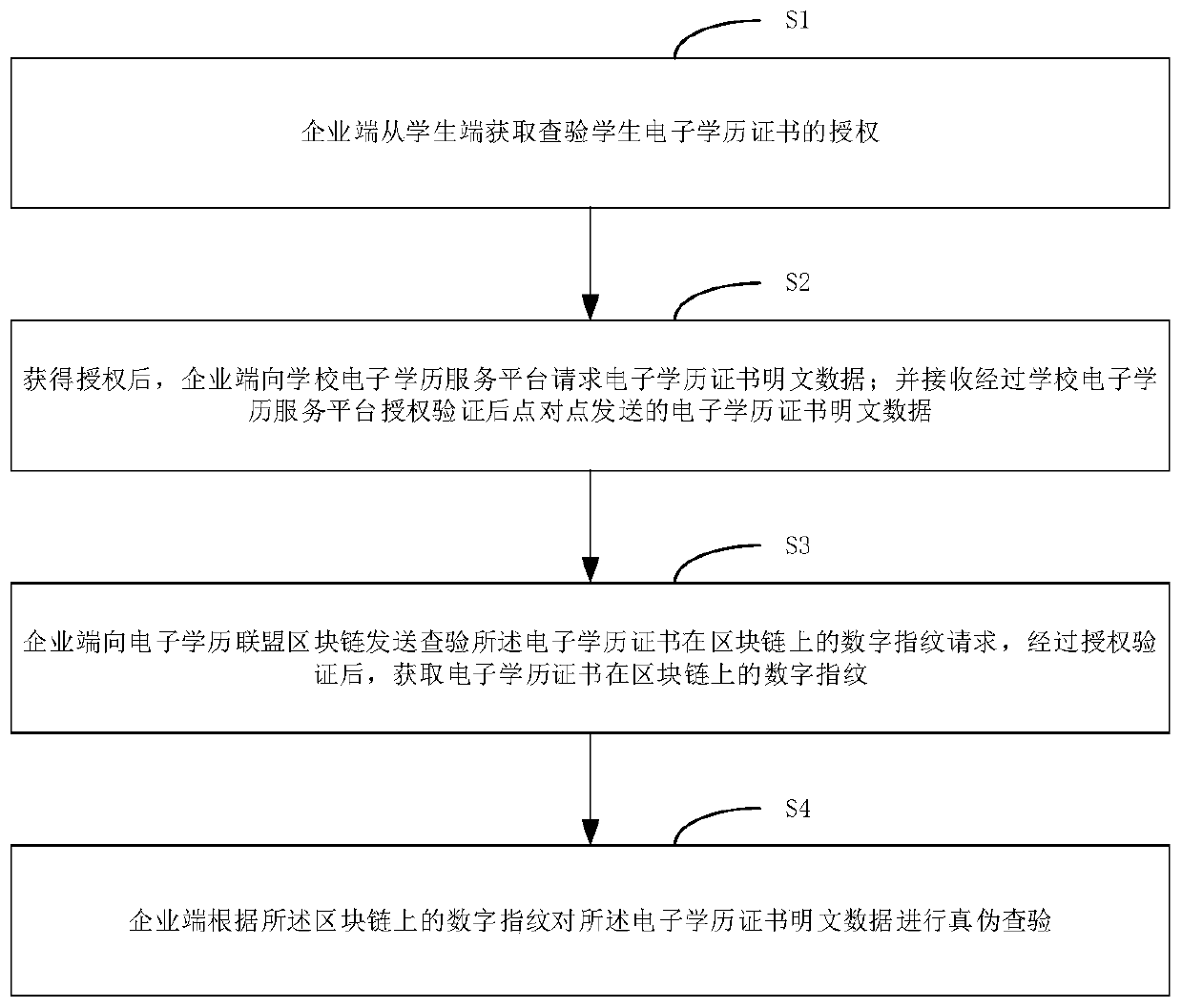
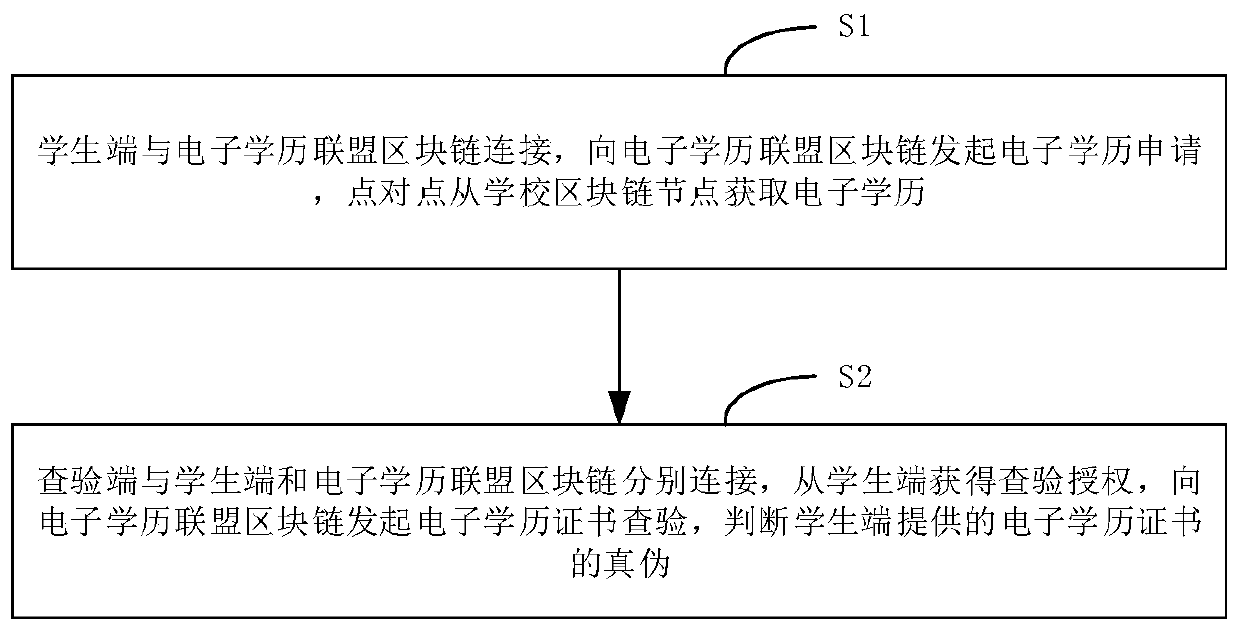
Decentralized electronic academic certificate checking method and system
ActiveCN110955699AAddressing the risks of centralizationImprove securityDatabase distribution/replicationCommercePlaintextInternet privacy
The invention relates to a decentralized electronic academic certificate checking method and system, belongs to the technical field of electronic academic certificate acquisition, and solves the problem of electronic academic certificate checking. The method comprises the following steps: acquiring authorization for checking an electronic academic certificate of a student from a student terminal;requesting electronic academic certificate plaintext data from a school electronic academic certificate service platform; receiving electronic academic certificate plaintext data sent in a point-to-point manner after being authorized and verified by the school electronic academic certificate service platform; sending a request for checking the digital fingerprint of the electronic academic certificate on the block chain to an electronic academic certificate alliance block chain, and obtaining the digital fingerprint of the electronic academic certificate on the block chain after authorizationverification; and checking the authenticity of the plaintext data of the electronic academic certificate according to the digital fingerprint on the blockchain. According to the invention, decentralization is realized, an application mode of a traditional centralized educational background authentication platform based on data collection is changed, the risk of electronic academic certificate plaintext data uploading is solved, and the security is improved.
Owner:YGSOFT INC
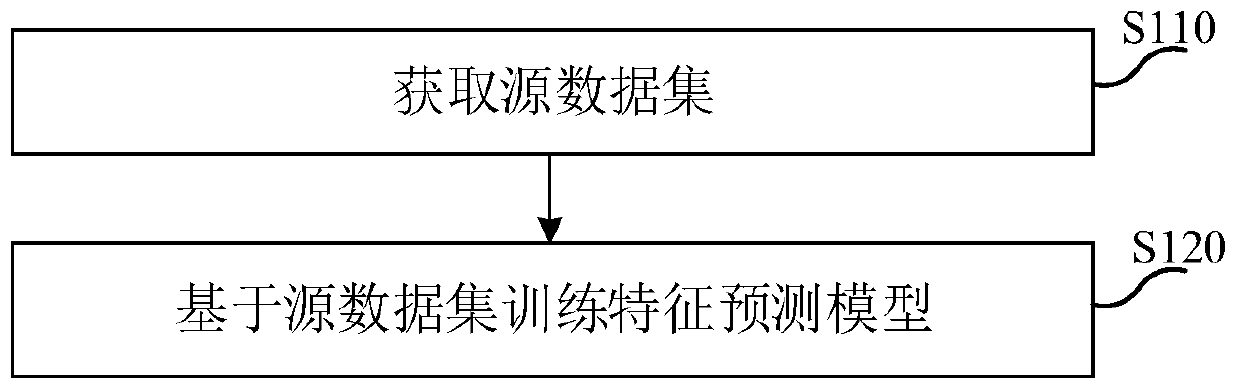
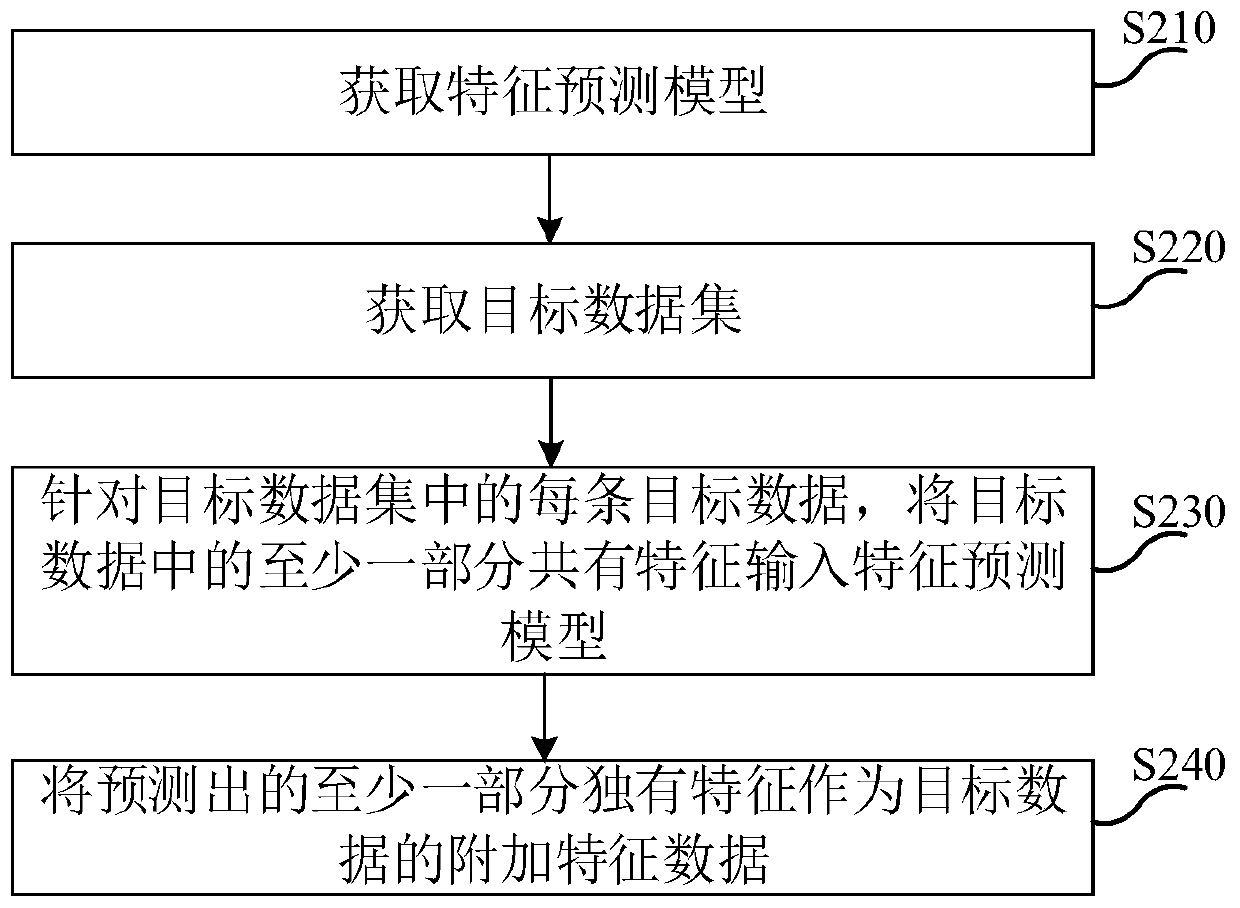
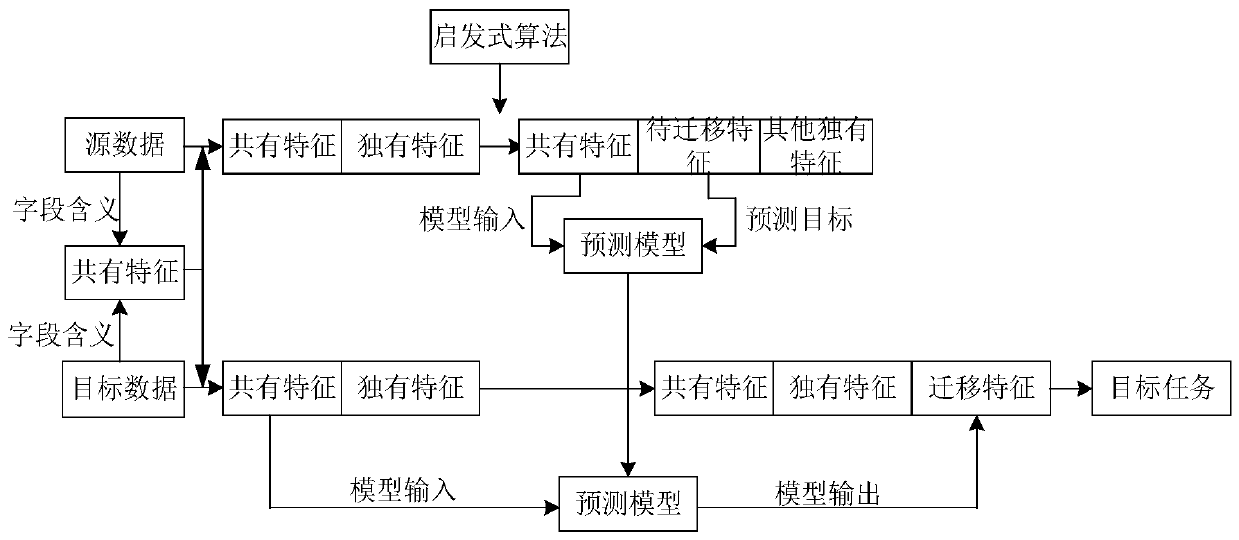
Model training method and device, additional feature data obtaining method and device, equipment and medium
PendingCN110858326AReduce the risk of being leakedDigital data protectionMachine learningData setEngineering
The invention provides a model training method and device, an additional feature data obtaining method and device, equipment and a medium. Obtaining a feature prediction model, the feature predictionmodel being trained based on the source data set, the feature prediction model being used for predicting at least one part of unique features of the source data based on at least one part of common features between the source data and the target data; obtaining a target data set; for each part of target data in the target data set, inputting at least one part of common features in the target datainto the feature prediction model to obtain at least one part of unique features predicted by the feature prediction model for at least one part of input common features; and taking at least one partof the predicted unique features as additional feature data of the target data. According to the method, the common features are taken as springboards, the unique features of the source data are migrated to the target data in a model migration mode, and the source data and the target data are not contacted in the process, so that the leakage risk of the source data is greatly reduced.
Owner:THE FOURTH PARADIGM BEIJING TECH CO LTD
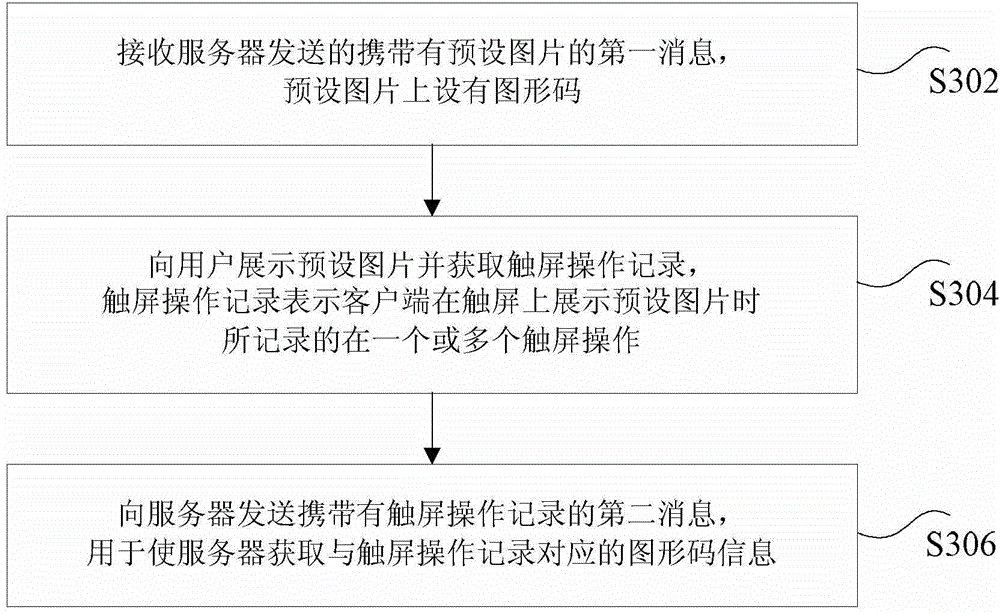
Server, client, interaction system, and information transmitting and receiving method
InactiveCN105227518AIncrease the difficultyReduce the risk of being leakedSecuring communicationInteraction systemsGraphics
The invention discloses a server, a client, an interaction system, and an information transmitting and receiving method. The method comprises the steps: transmitting a first message containing a preset image to the client, wherein the preset image is provided with a graphic code; receiving a second message, transmitted by the client, containing a touch screen operation record, wherein the touch screen operation record represents one or more touch screen operations recorded when the client displays the preset image; and obtaining a graphic code corresponding to the touch screen operation record according to the preset image. The invention solves a technical problem that the information safety is poor in a conventional information transmission scheme because the client has to-be-transmitted information plaintext.
Owner:SUMAVISION TECH CO LTD
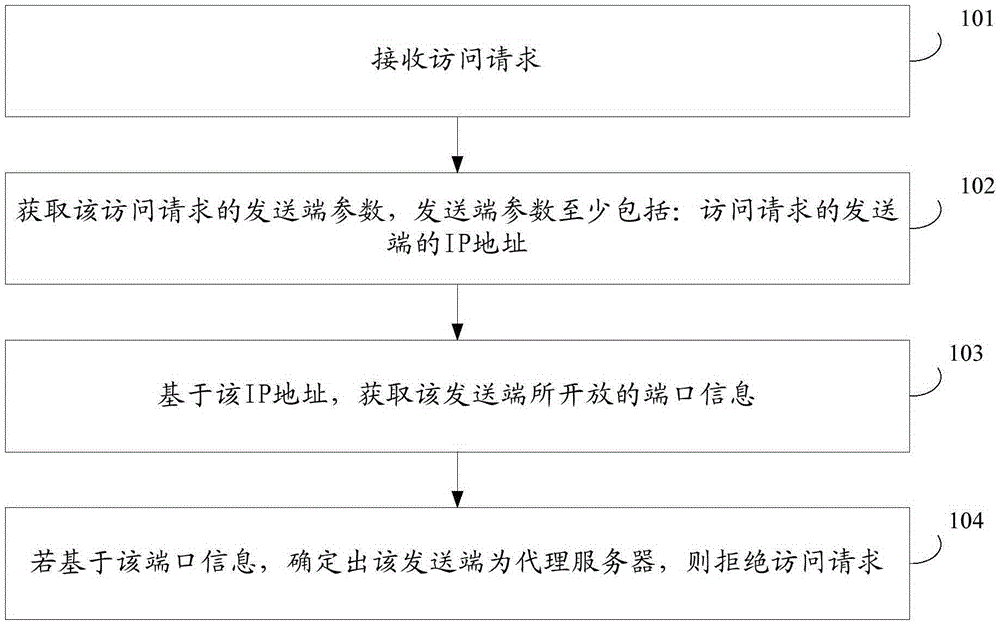
Access control method, device and server
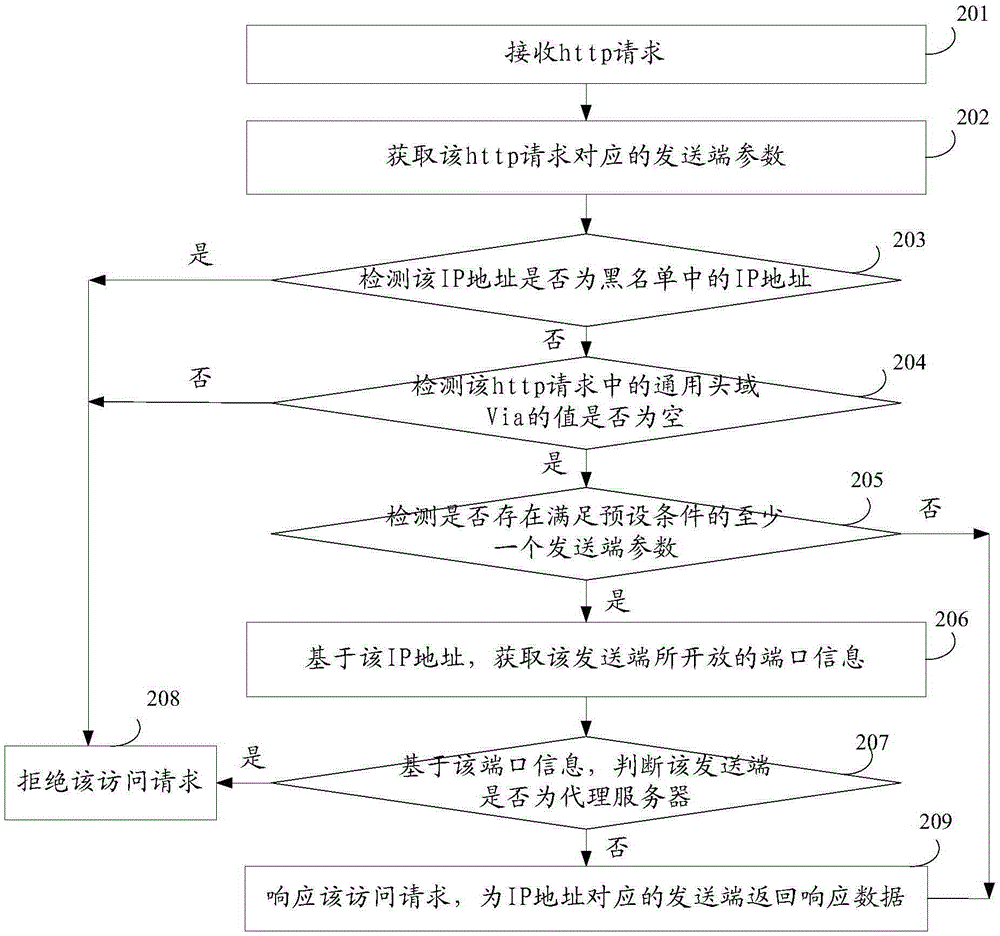
ActiveCN106789858ARestricted access behaviorReduce access behaviorUser identity/authority verificationIp addressProxy server
The present application provides an access control method, a device and a server. The method includes: receiving an access request; determining the IP address of the sending end of sending the access request; based on the IP address, obtaining the information of an open port of the sending end; if it is determined that the sending end is a proxy server based on the port information, denying the access request. The method, device and server can reduce the risk of data leaking of the server and improve the data safety.
Owner:ALIBABA (CHINA) CO LTD
Decentralized identity authentication system based on block chain
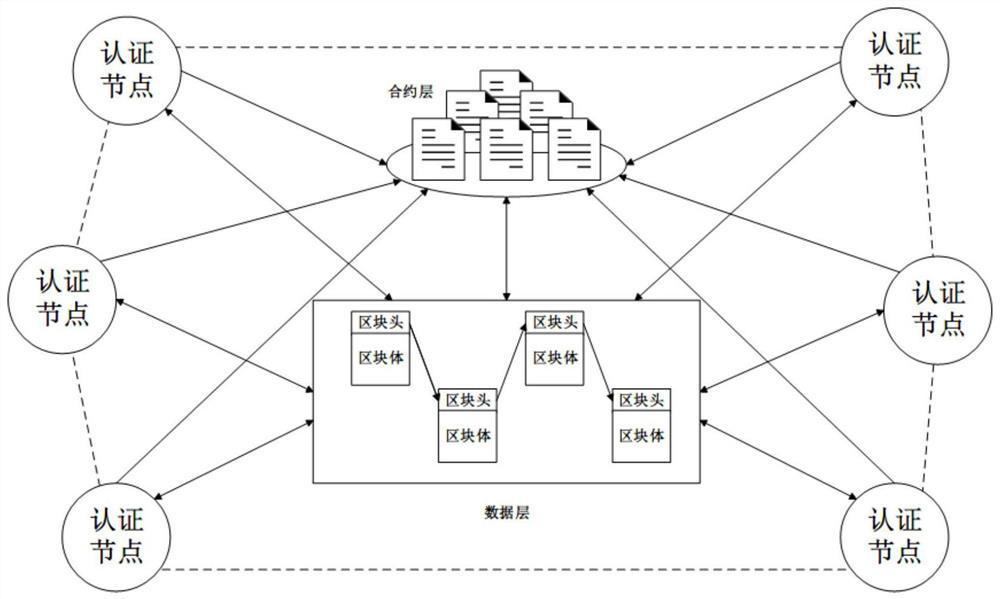
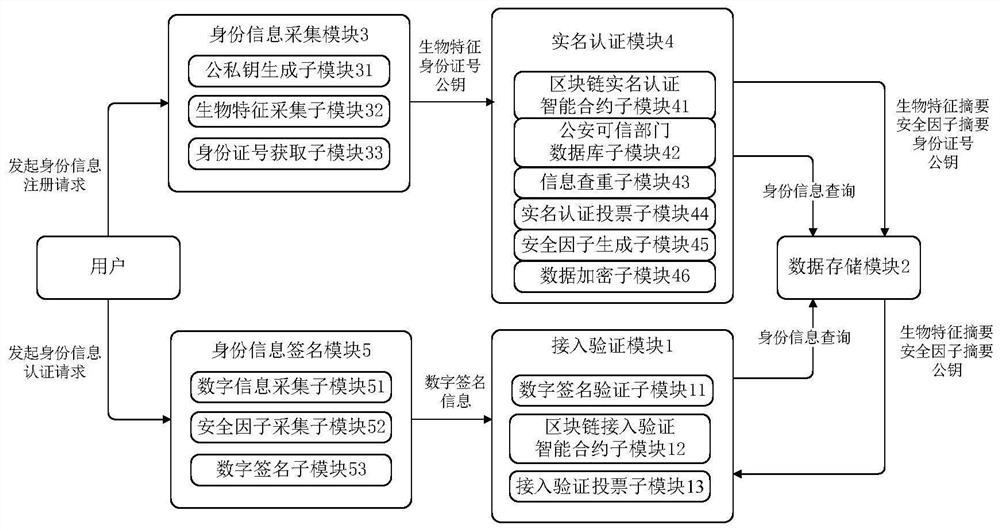
ActiveCN113259311AReduce the risk of fraudulent useComplete and secure authentication processKey distribution for secure communicationPublic key for secure communicationEngineeringAuthentication system
The invention provides a decentralized identity authentication system based on a block chain. The decentralized identity authentication system mainly solves the problems that in the prior art, user identity information is likely to be illegally used and leaked, and the system stability is poor. The system comprises a plurality of server nodes with the same function and power, namely authentication nodes, and each authentication node comprises an identity information acquisition module, a real name authentication module, a data storage module, an identity information signature module and an access verification module. The identity information acquisition module is responsible for acquiring identity registration information of a user, the real-name authentication module is responsible for performing real-name authentication and encryption on the identity registration information of the user, the data storage module is used for storing the encrypted identity information of the user by adopting a block + chain structure, and the identity information signature module is responsible for acquiring identity signature information of the user; and the access verification module is responsible for performing access verification on the identity signature module of the user. According to the invention, the security and stability of the decentralized identity authentication system are improved, and the method can be used for computers and computer networks.
Owner:XIDIAN UNIV
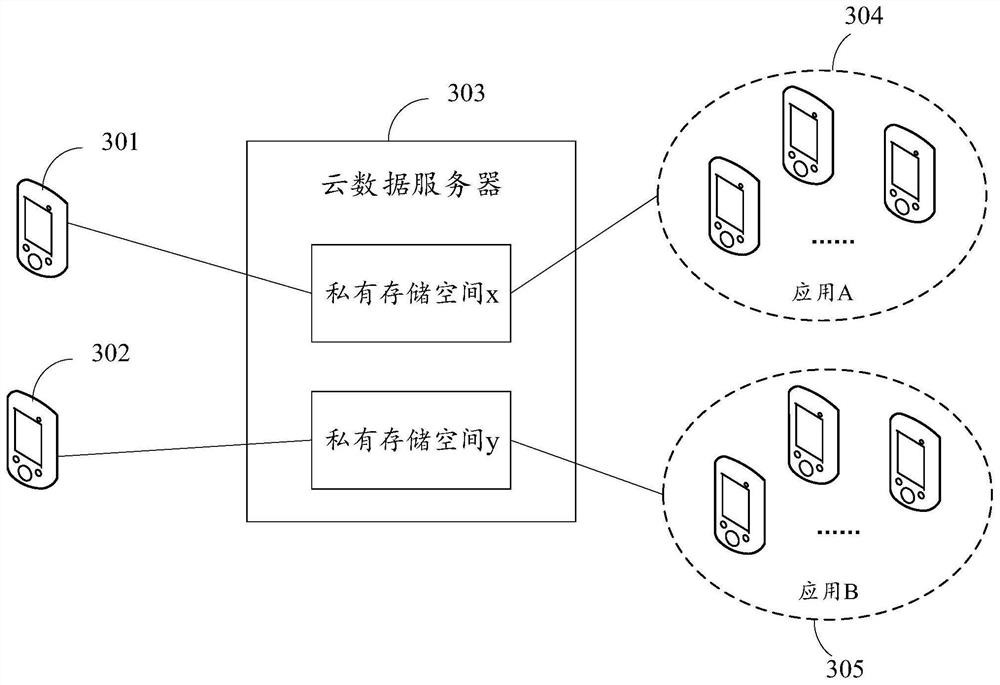
Data management method and device, computer equipment and storage medium
PendingCN112380568ARealize processingReduce the risk of being leakedDigital data protectionDigital data authenticationEngineeringCloud data
The embodiment of the invention discloses a data management method and device, computer equipment and a storage medium, and belongs to the technical field of computers. The method comprises the following steps: a cloud data server is provided with a private storage space, the private storage space closes local access permission, and the cloud data server decrypts encrypted user data in the privatestorage space in response to a data processing request to obtain decrypted user data; the decrypted user data is processed in the private storage space; and a processing result is sent to a management terminal. The encrypted user data is decrypted and processed in the private storage space, and the private storage space closes the local access permission, so that the cloud data server cannot obtain the decrypted user data, the process of processing and decrypting the user data in the private storage space is unknown to the cloud data server, and thus the user data can be processed, the risk that the user data is leaked can be reduced, and the security of the user data is ensured.
Owner:TENCENT TECH (BEIJING) CO LTD
Biological recognition payment method and device, gateway equipment and storage medium
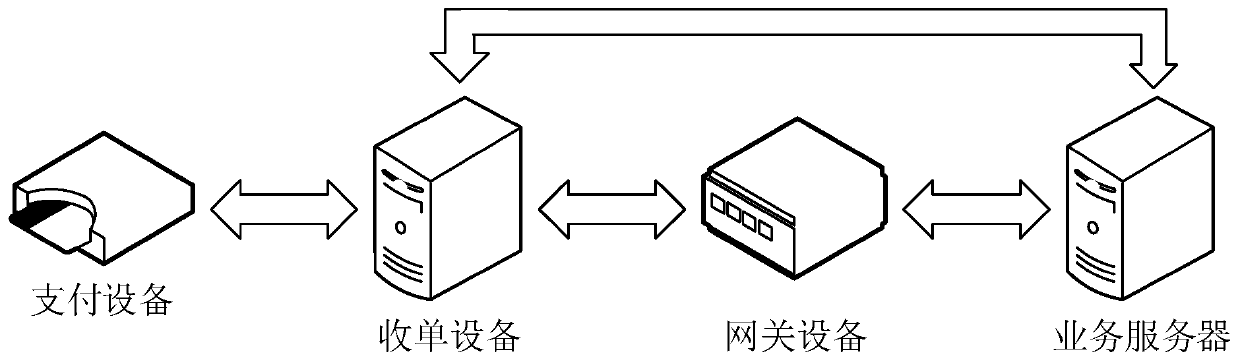
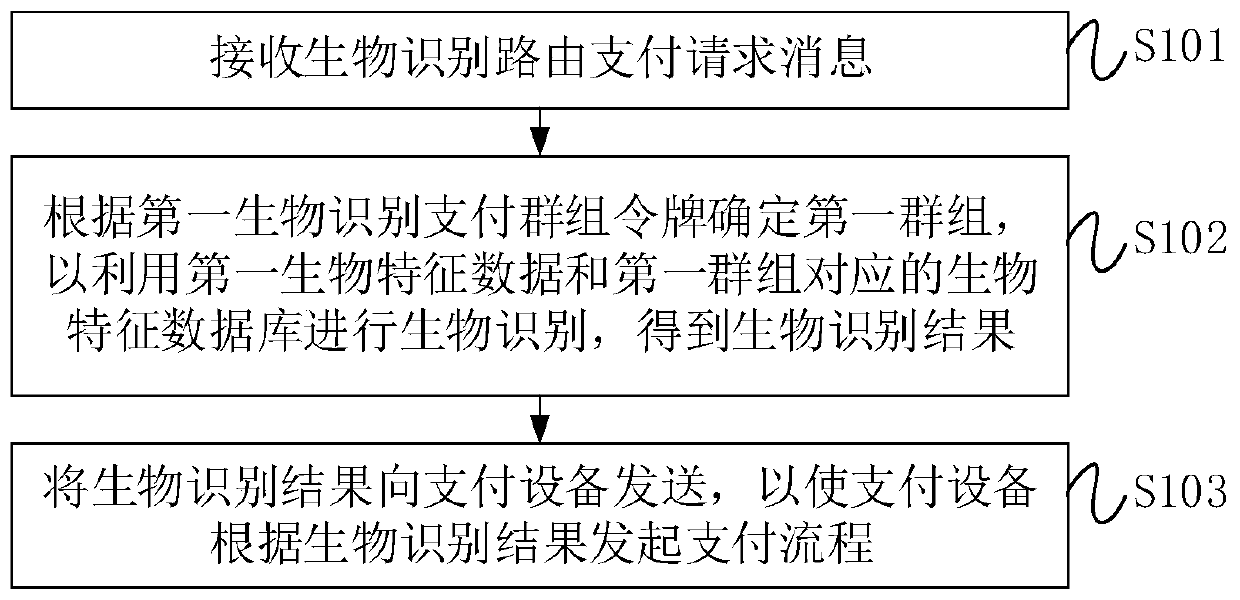
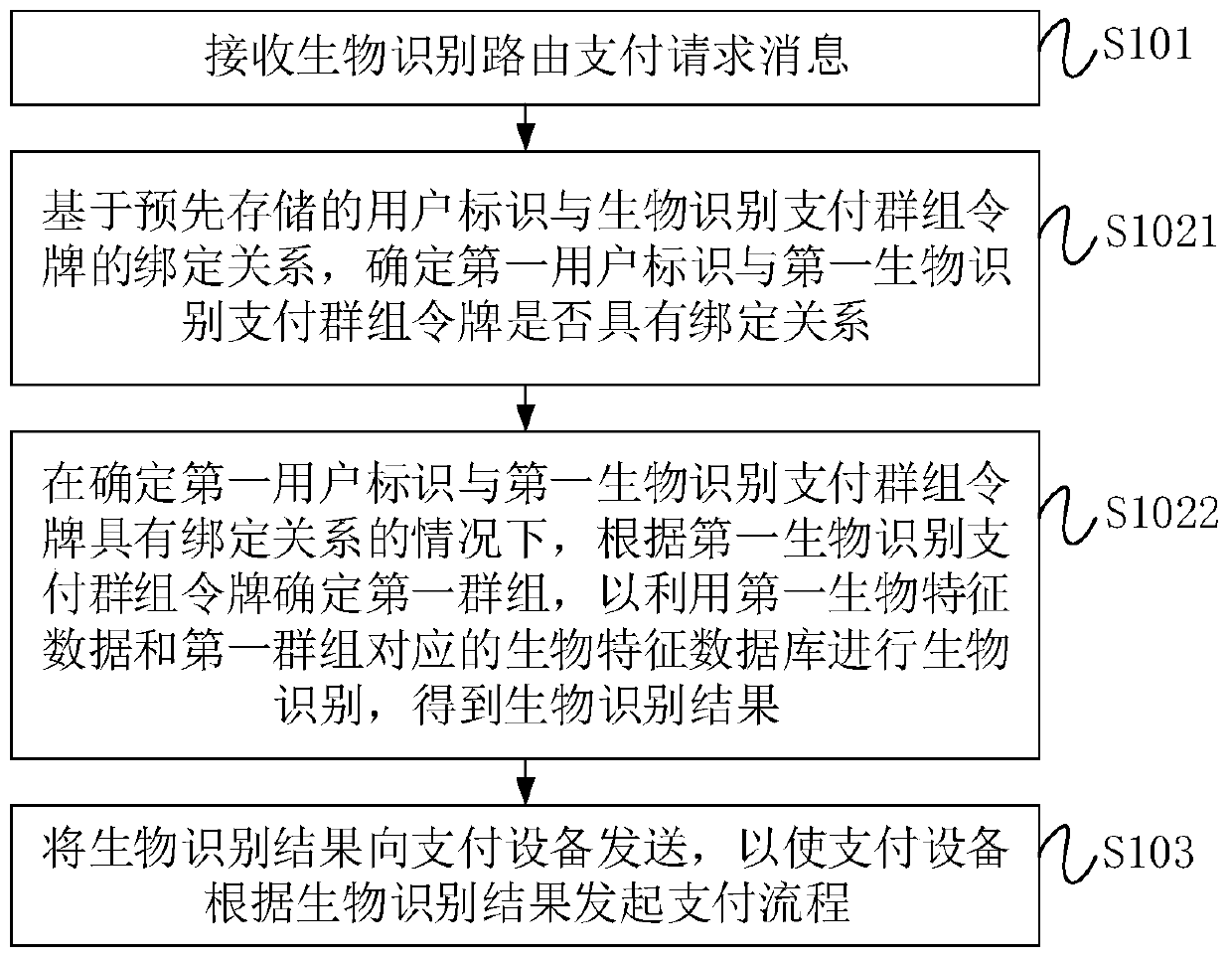
PendingCN111539732AImprove securityReduce the risk of abuseData switching networksProtocol authorisationPaymentComputer network
The invention provides a biological recognition payment method and device, gateway equipment and a storage medium, and relates to the field of data processing. The biometric identification payment method comprises: receiving a biometric identification routing payment request message, wherein the biometric identification routing payment request message comprises a first biometric identification payment group token and first biometric characteristic data, and the first biometric identification payment group token is used for representing that an initiating user of the biometric identification routing payment request message has biometric identification payment permission in the first group; determining a first group according to the first biometric identification payment group token, and performing biometric identification by using the first biometric characteristic data and a biometric characteristic database corresponding to the first group to obtain a biometric identification result;and sending the biological recognition result to payment equipment, so that the payment equipment initiates a payment process according to the biological recognition result. By means of the technicalscheme, the safety of biological recognition payment of the user can be improved.
Owner:CHINA UNIONPAY
Method and device for processing file/application program on mobile communication terminal
InactiveCN103488942AEasy to operateReduce the risk of being leakedPlatform integrity maintainanceTime rangePrivacy protection
The invention discloses a method and a device for processing a file / application program on a mobile communication terminal. The method includes the steps: monitoring the motion state of the mobile communication terminal and an operated event of the file / application program; determining the operated file / application program as an object needing to be protected as privacy information if the operated event of the file / application program and the motion state of the mobile communication terminal meeting preset conditions within a preset time range are monitored; correspondingly protecting the operated file / application program according to a preset privacy protection operation mode to avoid leakage of the operated file / application program. By the method and the device, the privacy information of a user can be more effectively protected in the process of protecting the object needing to be protected as the privacy information on terminal equipment.
Owner:BEIJING QIHOO TECH CO LTD +1
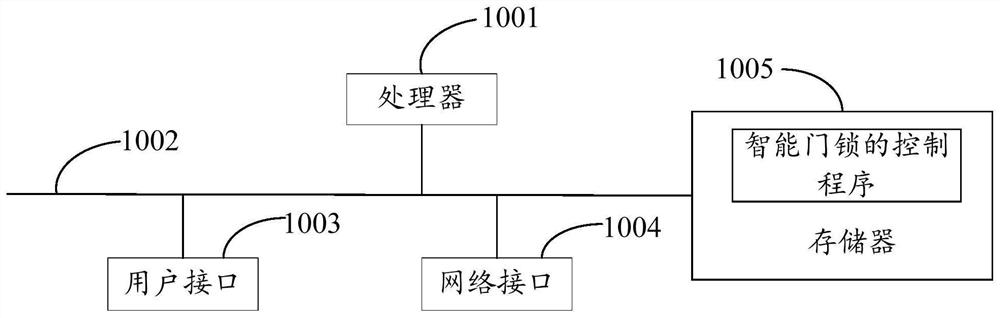
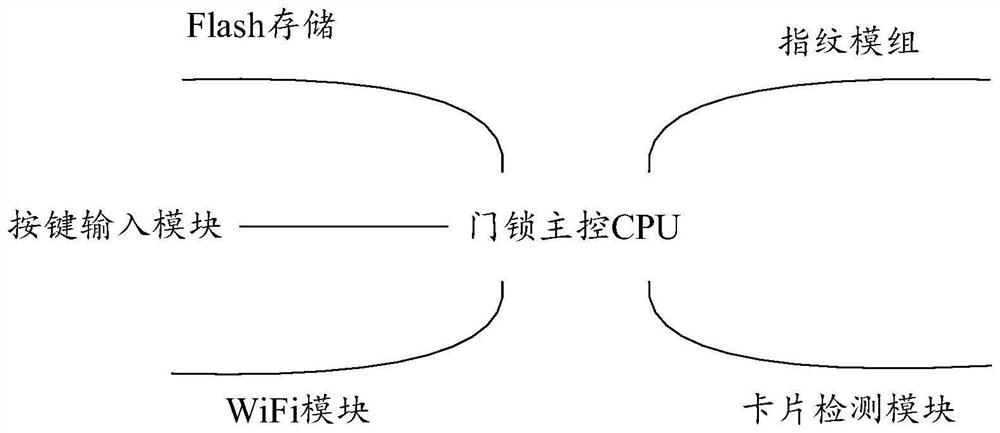
Intelligent door lock control method, intelligent door lock and storage medium
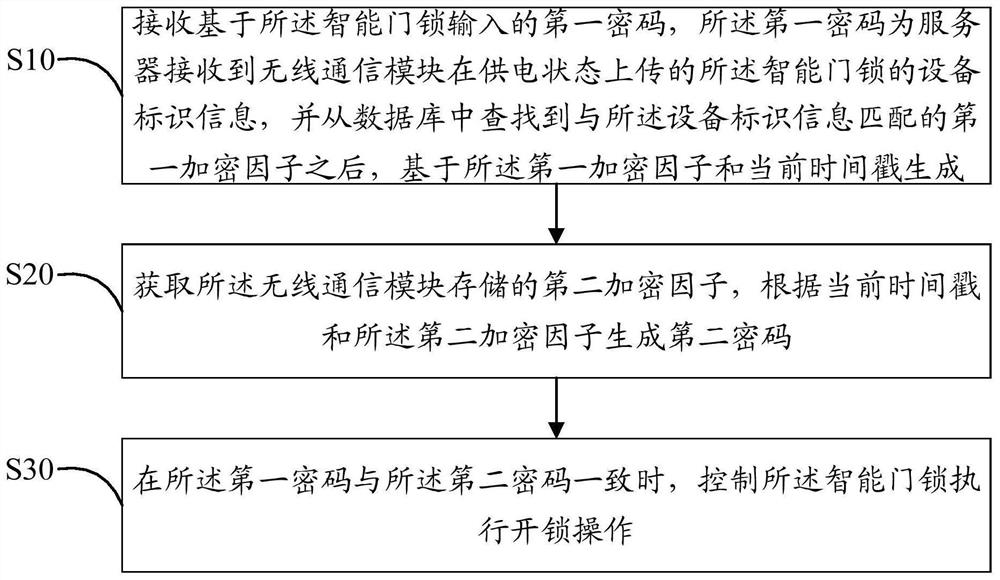
PendingCN112419549AImprove securityAvoid the risk of hijackingKey distribution for secure communicationUser identity/authority verificationTimestampPassword
The invention discloses an intelligent door lock control method, which comprises the steps of: receiving a first password input based on an intelligent door lock, wherein the first password is equipment identification information, uploaded by a wireless communication module in a power supply state, of the intelligent door lock received by a server, searching a first encryption factor matched withthe equipment identification information in a database, and then generating a first password based on the first encryption factor and a current timestamp; acquiring a second encryption factor stored in a wireless communication module, and generating a second password according to the current timestamp and the second encryption factor; and when the first password is consistent with the second password, controlling the intelligent door lock to execute an unlocking operation. The invention further discloses an intelligent door lock and a computer readable storage medium. Only the equipment identification information is interacted through the wireless network, the encryption factors can be prevented from being hijacked by the network, password leakage can be avoided by generating an unlockingpassword through the current timestamp and the encryption factor, and the safety of the intelligent door lock is improved.
Owner:SHENZHEN TCL NEW-TECH CO LTD
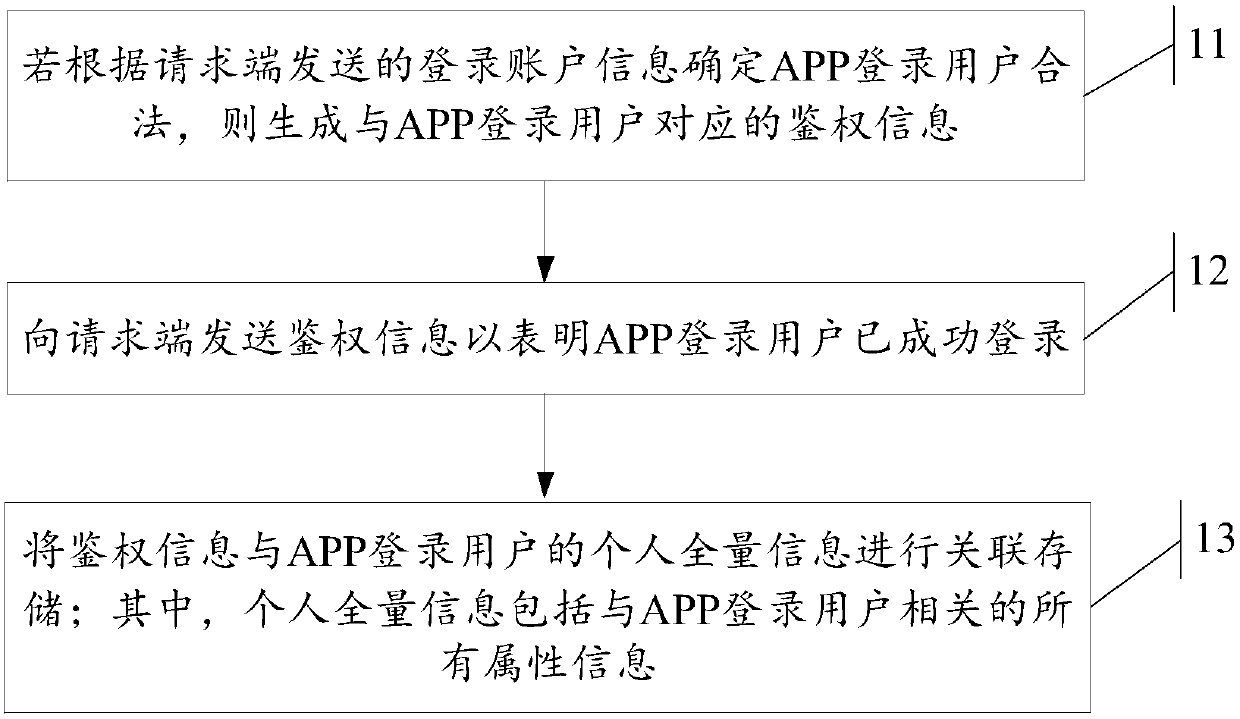
Information processing method and device, server and readable storage medium
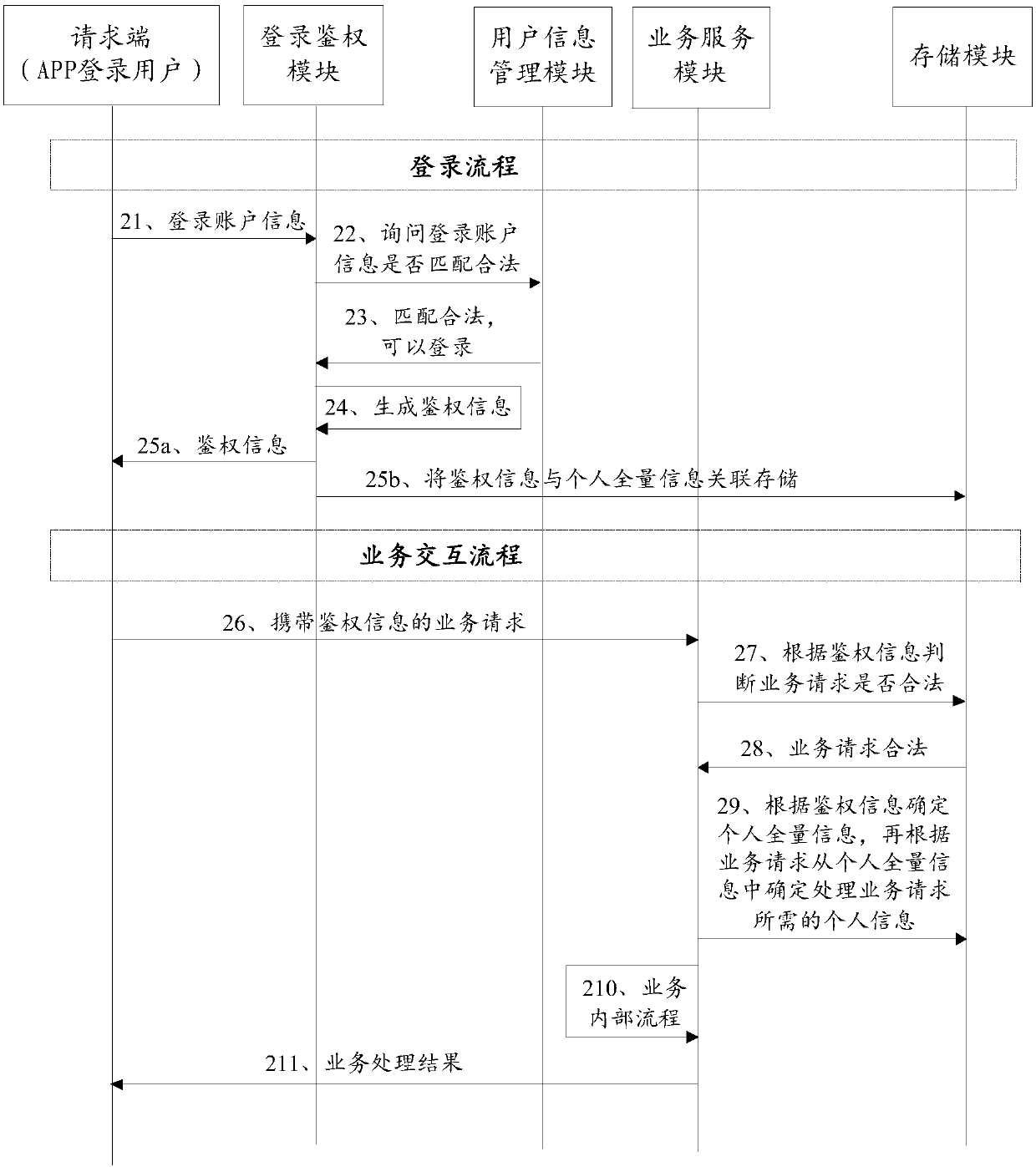
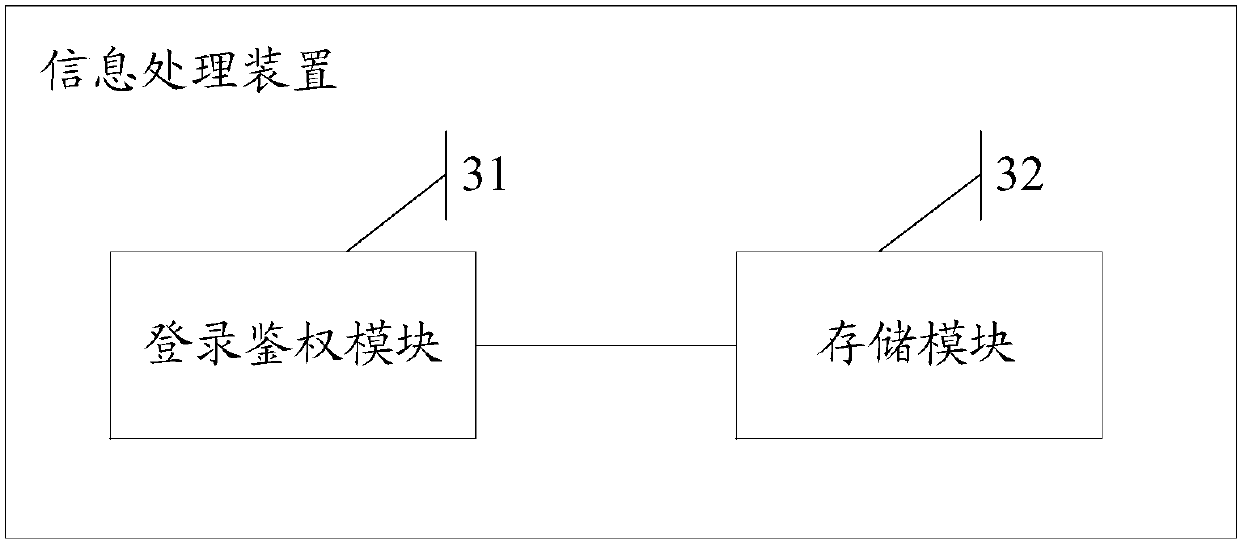
ActiveCN109818915AImprove securityReduce transmissionTransmissionInformation processingInformation function
The invention discloses an information processing method and device, a server and a readable storage medium, which are used for solving the technical problems that the authentication information function is single and user information is easy to leak and is lack of security in the prior art, so that the authentication information function is enhanced and the security of the user information is improved. The method comprises the steps that if it is determined that an APP login user is legal according to login account information sent by a request end, authentication information corresponding tothe APP login user is generated; sending the authentication information to the request end to indicate that the APP login user logs in successfully; performing associated storage on the authentication information and the personal total information of the APP login user; wherein the personal total information comprises all attribute information related to the APP login user.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
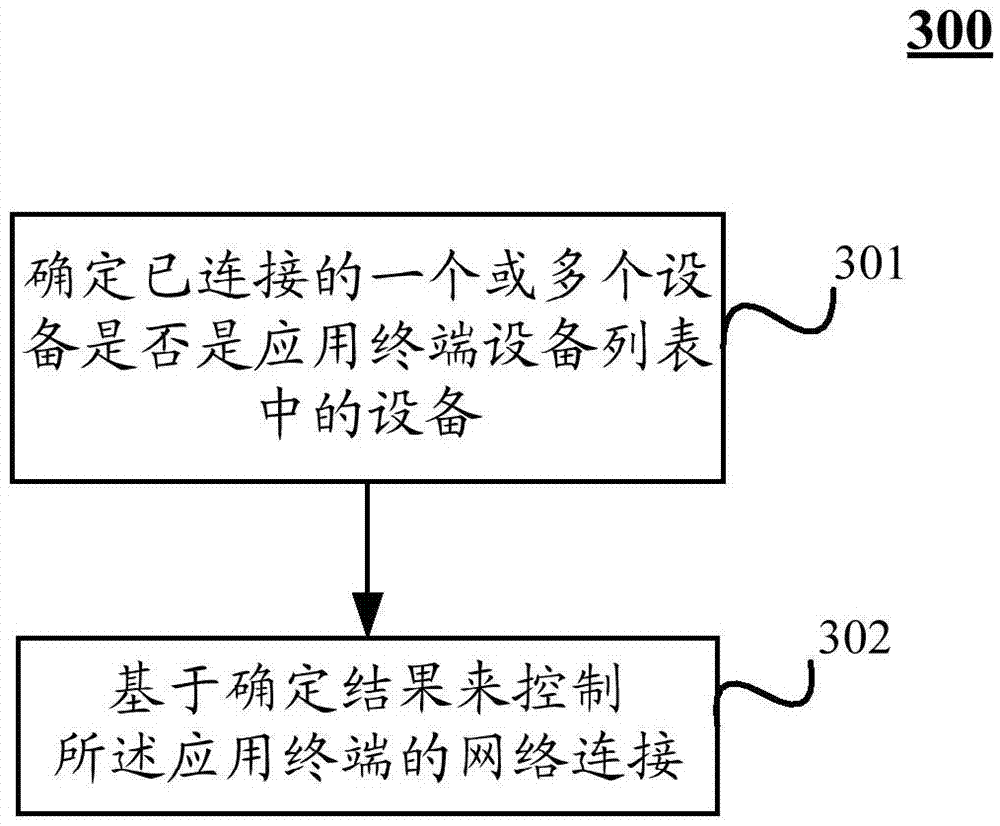
Method and device for controlling network connection of application terminal
ActiveCN107172002AReduce the risk of data breachesReduce the risk of being leakedAssess restrictionNetwork topologiesConnected devicePower consumption
The invention relates to a method and device for controlling network connection of an application terminal. The method comprises the steps of: determining whether one or more connected devices are devices in an application terminal device list or not; and, on the basis of a determination result, controlling network connection of the application terminal. Thereby, according to the embodiment of the invention, the application terminal can automatically control network connection according to the connected devices, instead of being always connected with a network; therefore, the data leakage risk of users is reduced; and simultaneously, the power consumption of the application terminal is reduced.
Owner:BOE TECH GRP CO LTD
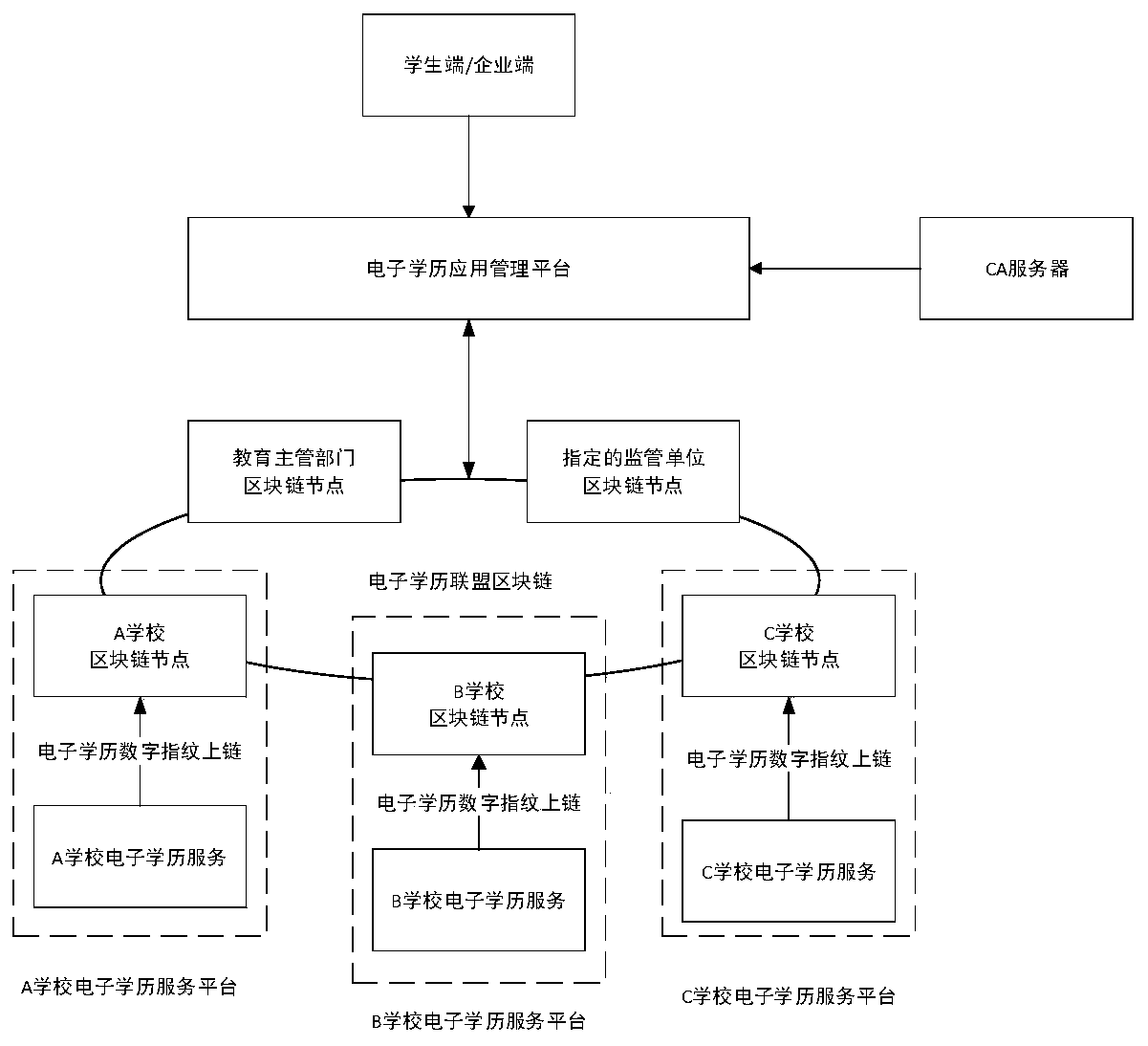
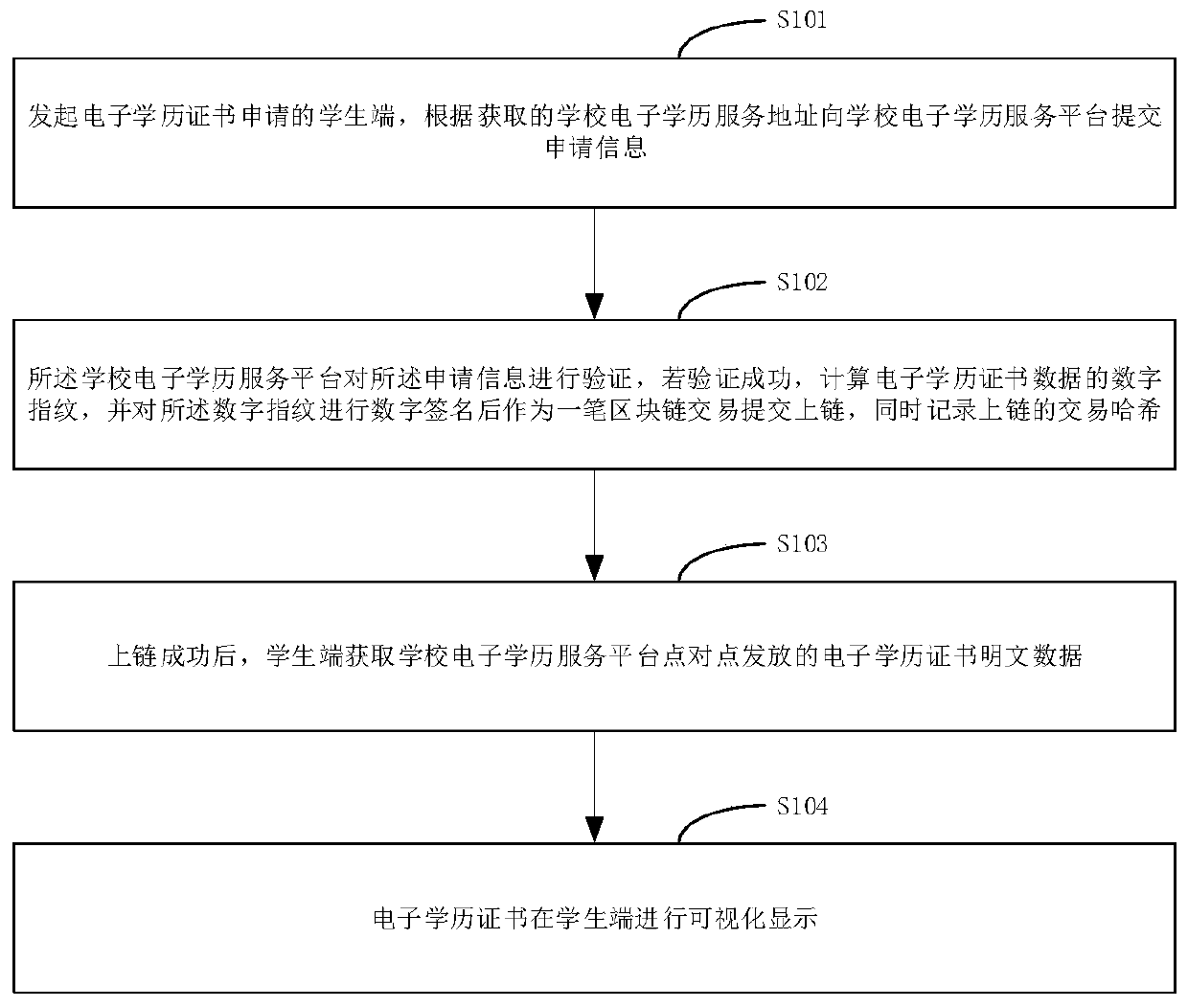
Decentralized electronic education background management system and method
ActiveCN110909388AAchieve decentralizationAddressing the risks of centralizationData processing applicationsDigital data protectionData setKnowledge management
The invention relates to a decentralized electronic education background management system and method, and belongs to the technical field of electronic education background certificate acquisition, solving the problems of electronic education background certificate application and inspection. The decentralized electronic education background management system comprises an electronic education background alliance block chain and a client, wherein the electronic education background alliance block chain processes the electronic education background certificate application and check request and performs uplink storage on the electronic education background application data; and the client establishes connection with the electronic education background alliance block chain, initiates an electronic educational background application request to the electronic educational background alliance block chain, and acquires electronic educational background plaintext data from school block chain nodes in the electronic education background alliance block chain in a point-to-point manner, or initiates an electronic education background check request to the electronic education background allianceblock chain, and judges the authenticity of the electronic education background. According to the decentralized electronic education background management system, decentralization is realized, and anapplication mode of a traditional centralized education background authentication platform based on data collection is changed, so that the risk of data centralization is solved, and the security isimproved.
Owner:YGSOFT INC
Anti-attack arbitration device
ActiveCN105512573AReduce the risk of being leakedImprove securityInternal/peripheral component protectionEmbedded systemResponse period
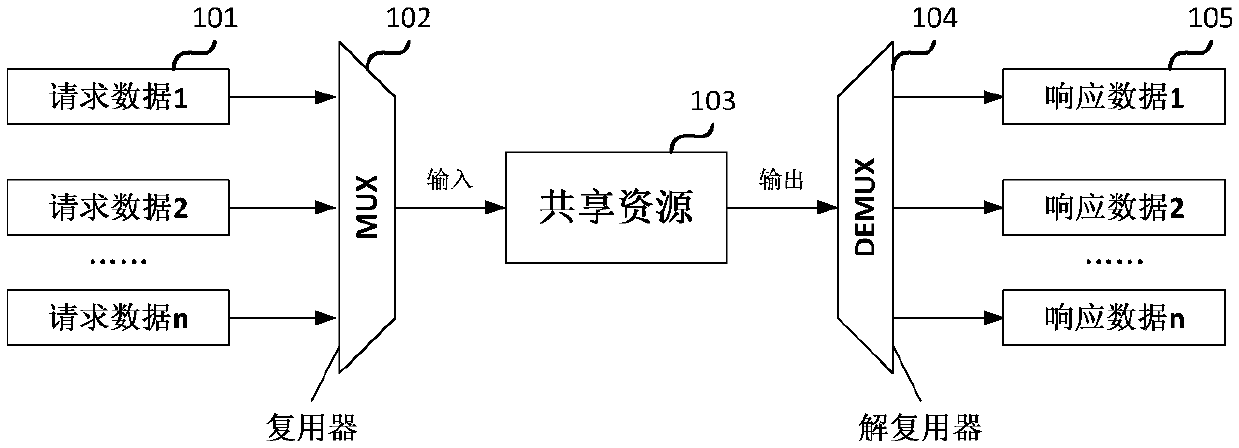
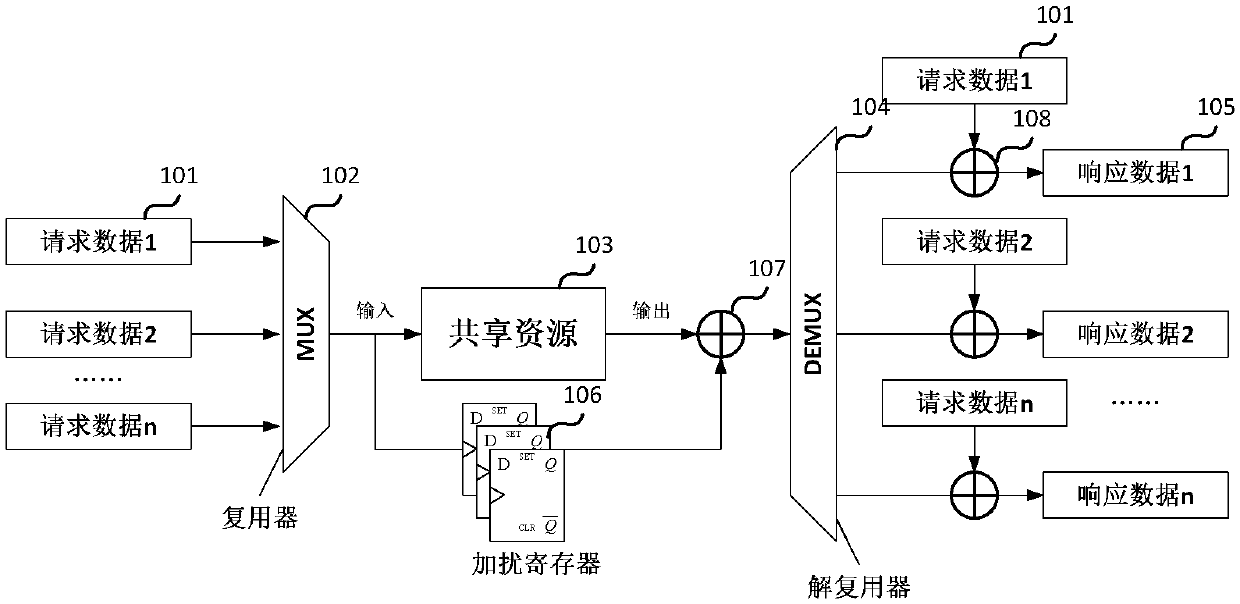
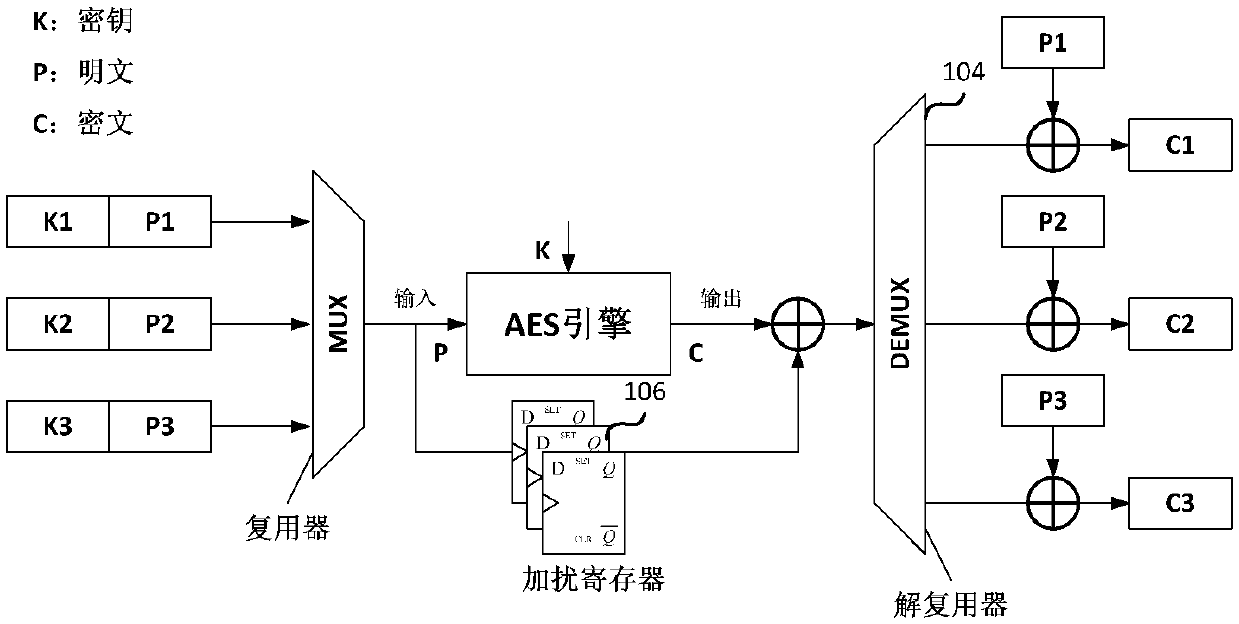
The invention discloses an anti-attack arbitration device comprising a multiplexer, a sharing resource module and a demultiplexing device and further comprises a scrambler and descramblers. The scrambler is added to conduct xor operation before the demultiplexer to scramble original response data; and a plurality of descramblers are employed to increase xor operation after the demultiplexing device to demultiplex for the scrambled response data. When a request response and an output response of the arbitration device are not finished in the same clock period, a scrambling register has to be added to save request data responded during the request response period and then finish xor operation with the original response data during the output response period; and safety performance of the arbitration device can be improved and anti-attack property can be enhanced.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Data storage method and device
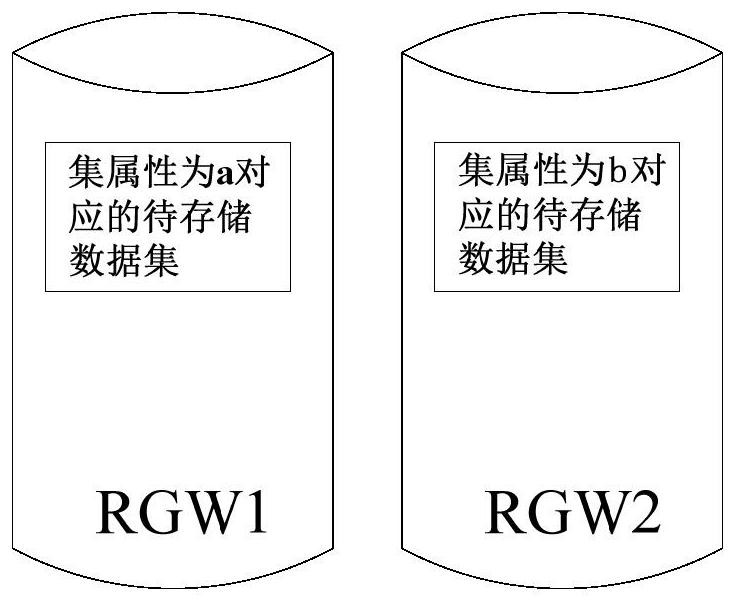
PendingCN112685778AImprove securityReduce the risk of being leakedDigital data protectionData setEngineering
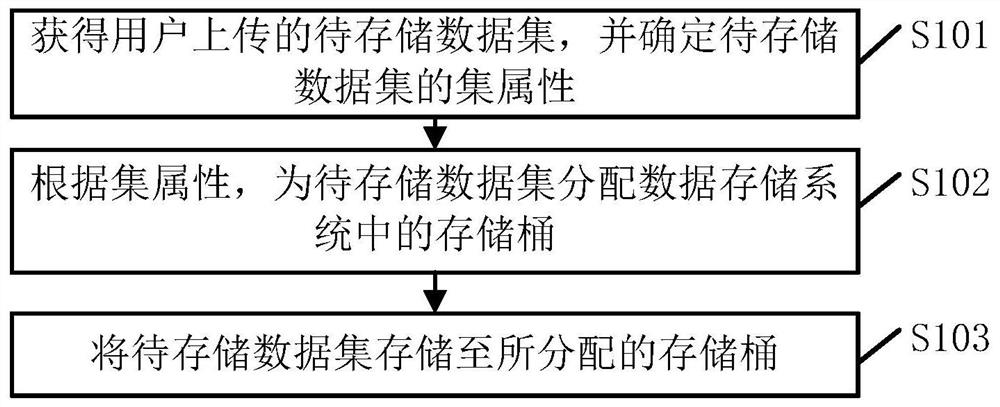
The embodiment of the invention provides a data storage method and device, and the method comprises the steps of obtaining a to-be-stored data set uploaded by a user, and determining the set attribute of the to-be-stored data set; according to the set attribute, distributing a storage bucket in a data storage system to the to-be-stored data set, and the storage bucket being a storage space which has unified access permission and is used for storing data; and storing the to-be-stored data set in the allocated storage bucket. When the scheme provided by the embodiment is applied to data storage, the risk of data leakage can be reduced.
Owner:北京聚云科技有限公司
Secure transmission method and device, computer equipment and storage medium
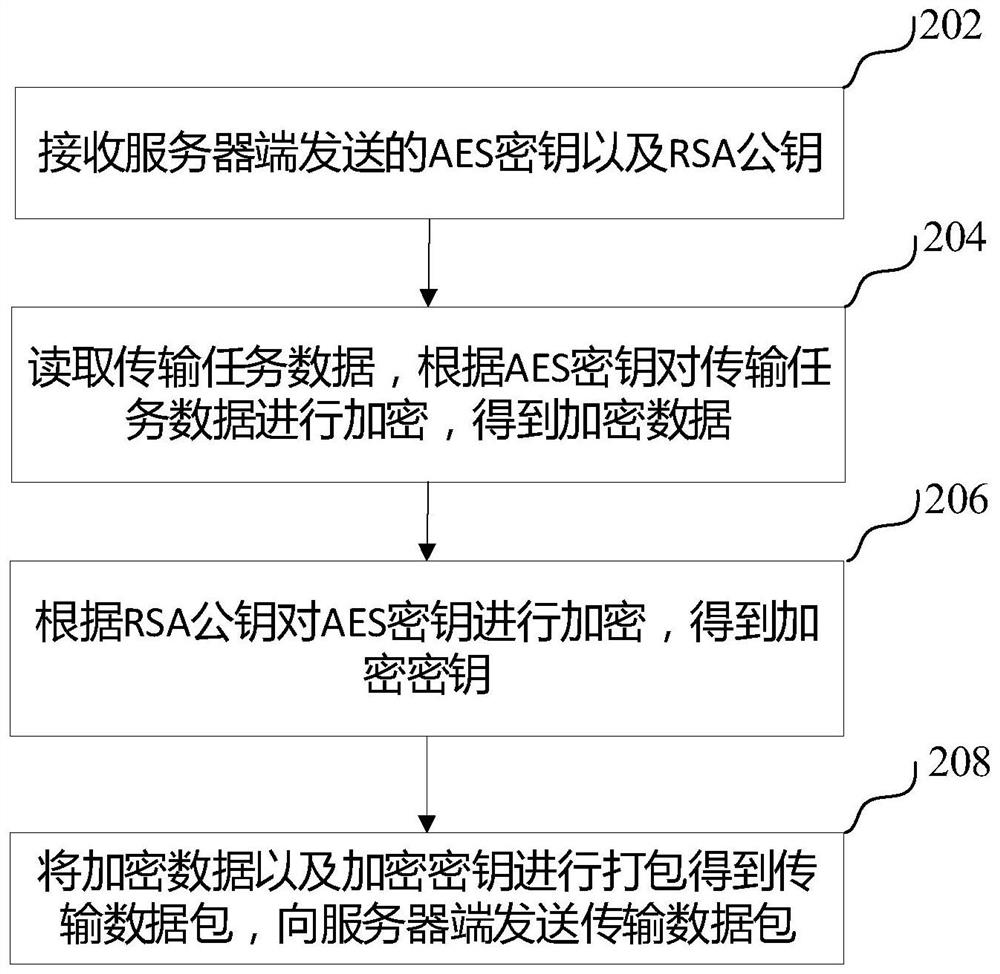
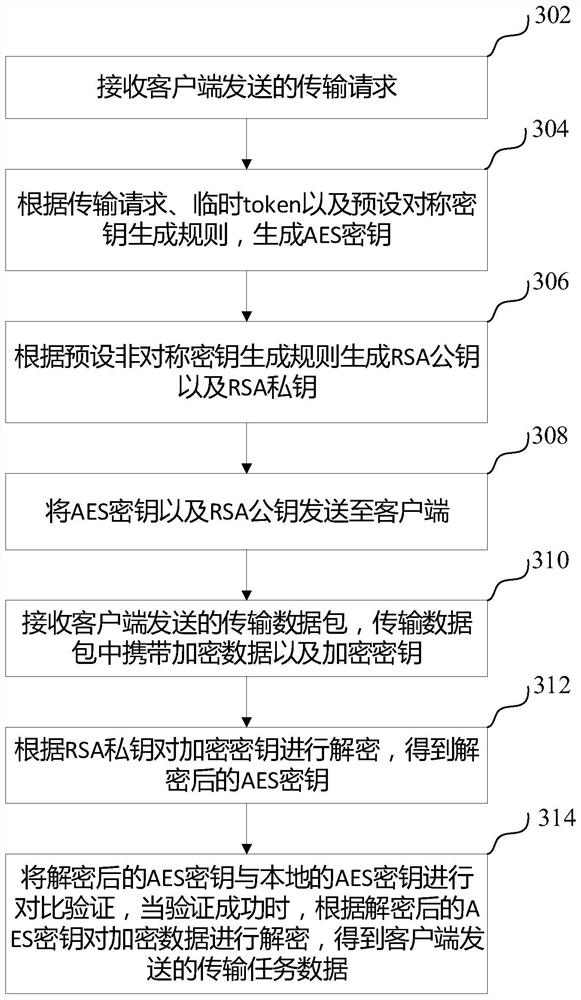
PendingCN114124440AReduce the risk of being leakedEnsure safetyEncryption apparatus with shift registers/memoriesPublic key for secure communicationSecure transmissionEngineering
The invention relates to the technical field of computer network security, and provides a secure transmission method and device, computer equipment and a storage medium. The method comprises: a client receives an AES key and an RSA public key sent by a server, the AES key being generated by the server according to a temporary token and having a period of validity; encrypting the transmission task data according to the AES key to obtain encrypted data; encrypting the AES secret key according to the RSA public key to obtain an encrypted secret key; and packaging the encrypted data and the encryption key to obtain a transmission data packet, and sending the transmission data packet to a server side. According to the method, the server side encrypts the transmission task data according to the AES secret key generated by the temporary token, the token is temporarily generated by the server side, the timeliness of the AES secret key generated according to the temporary token is limited, the risk that the secret key is leaked is reduced, the AES secret key is encrypted according to the RSA public key, and the encryption efficiency is improved. And the security of the transmission task data and the security of the key are ensured.
Owner:PING AN PENSION INSURANCE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com