Key generation and management method and server
A key generation and server technology, which is applied in the computer field, can solve problems such as easy leakage of keys, and achieve the effects of improving security, reducing the risk of being leaked, and increasing the difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
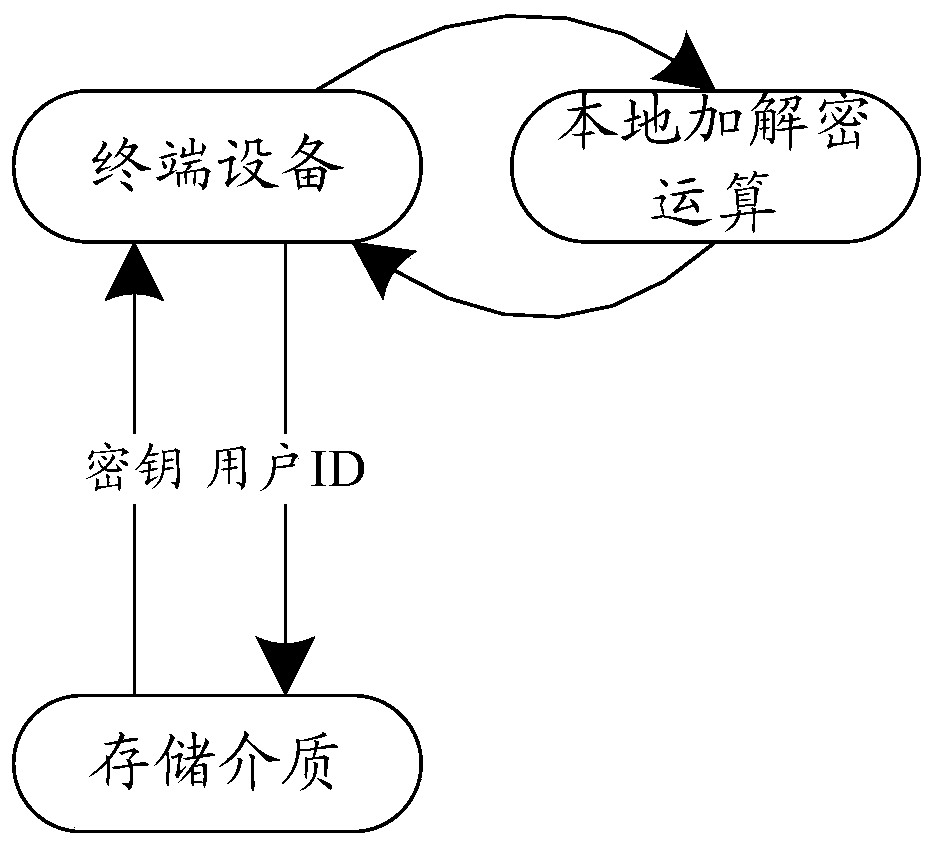
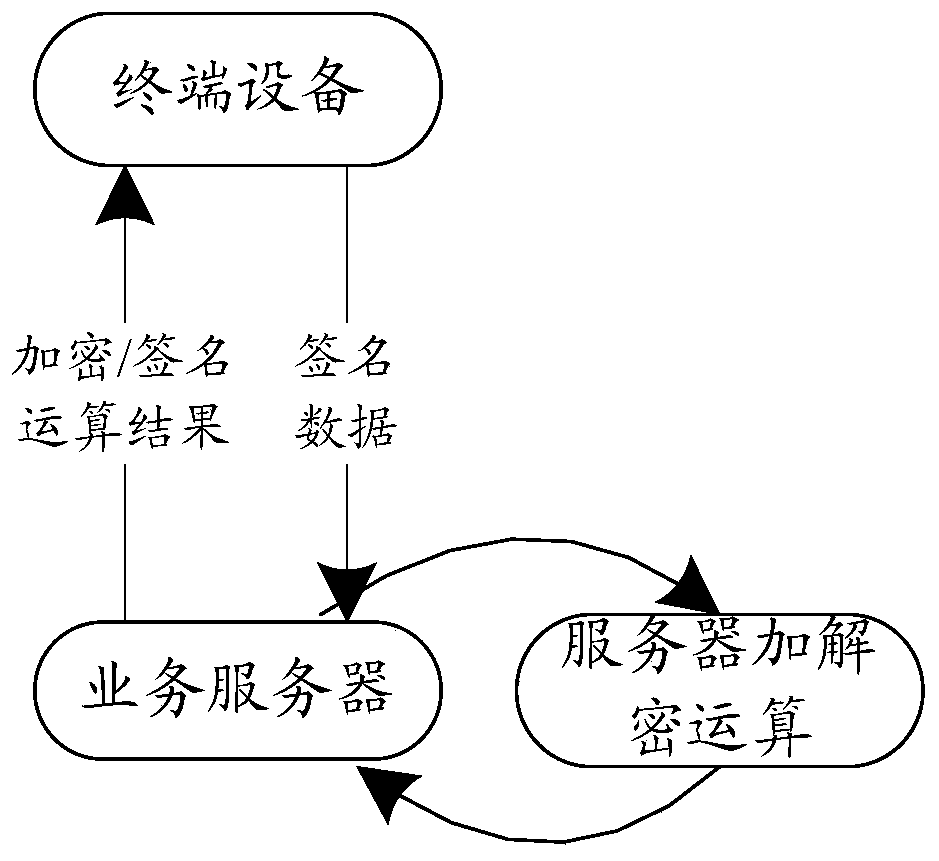
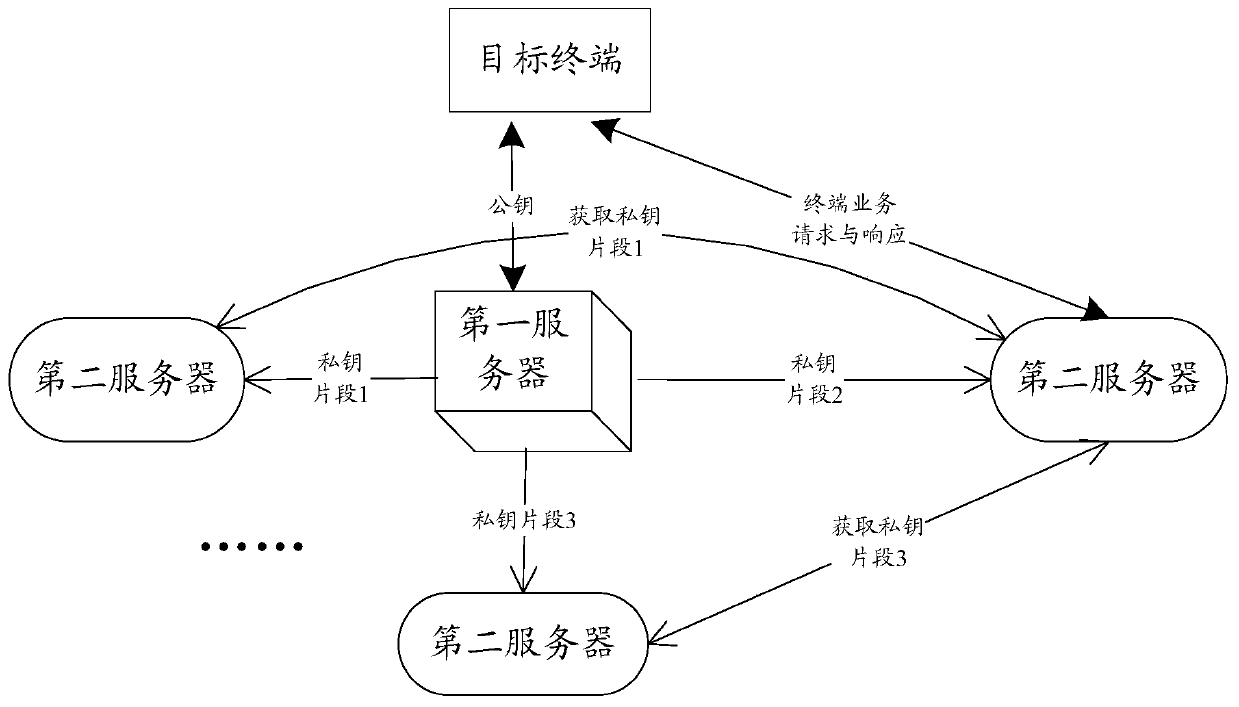
[0041] In order to solve the technical problem of high risk of key disclosure in the prior art, in the embodiment of the present application, a key pair is generated on the first server, and then the private key in the key pair is segmented, respectively store in different second servers, and notify the user terminal of the corresponding complete public key at the same time; when a service request encrypted by the terminal with the public key arrives, the second server that undertakes the request goes to other second servers to obtain the stored private key. The key fragments are then spliced into a complete private key, and the spliced private key is used to decrypt and verify the terminal request.
[0042] Below in conjunction with accompanying drawing, the optional implementation mode of this application is described in further detail:
[0043] The embodiment of the present application provides a key generation method and a key management method, which are implemented b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com