Information security method and system based on data access process in high-trust environment
A data access and information security technology, applied in digital data protection, electronic digital data processing, computer security devices, etc., can solve the problem of "data immobility" and achieve the effects of ensuring privacy, convenient review, and increasing illegal costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
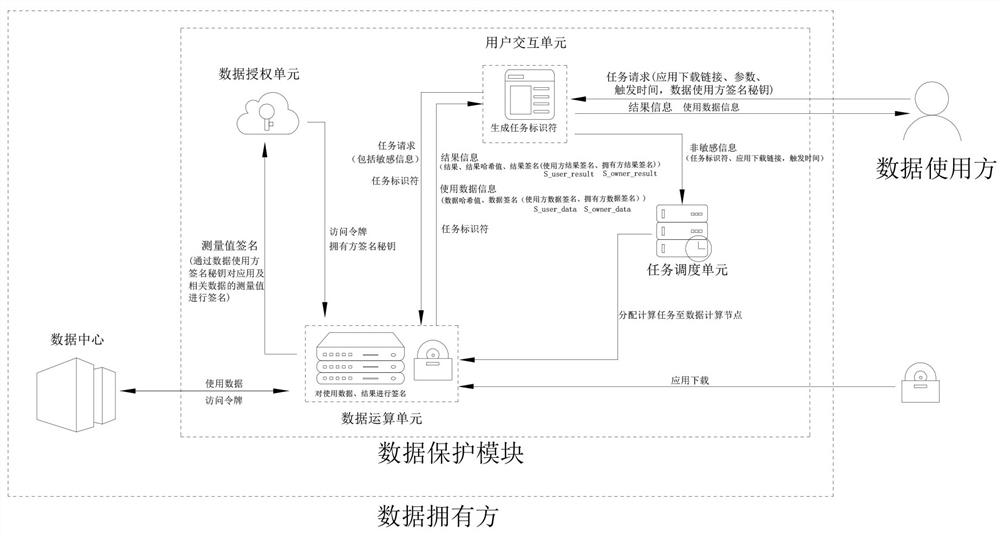
[0098] This embodiment is similar to Embodiment 1, the difference is that the application scenario of this embodiment is based on a certain basis of trust between the data owner and the data user, such as two relatively independent corporate entities under the same head office, or a government-affiliated entity. Between different departments that are completely independent, the data authorization unit does not verify the measured value, such as whether the application is on the white list of the data owner. Since both parties have a certain basis of trust, the verification of the measured value is omitted. It can improve the efficiency of data access. In this embodiment, after verifying the validity of the measured value signature, an access token is directly generated for the task request and sent to the data operation unit, and the measured value and the measured value signature are saved to support trusted traceability. Let the dishonesty leave a mark, so that the responsibi...
Embodiment 3
[0101] This embodiment is similar to Embodiment 1, except that the owner's data signature and owner's result signature in this embodiment are secondary signatures for the user's data signature and user's result signature respectively.
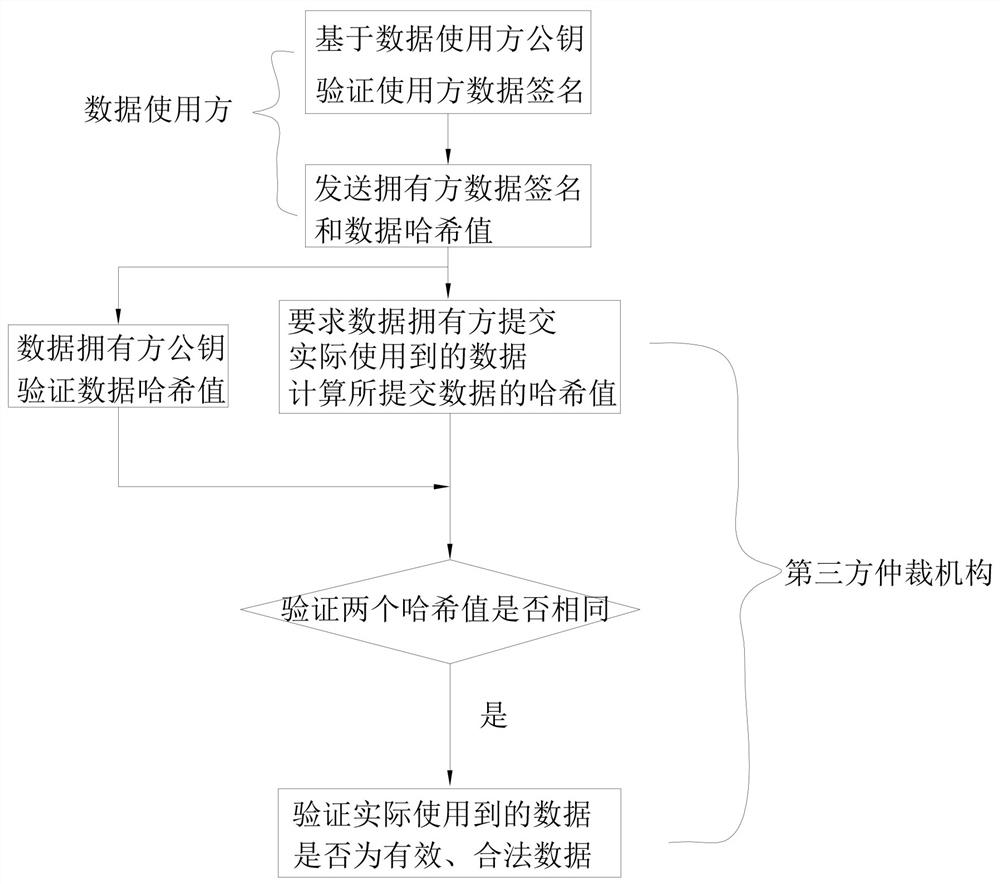
[0102] That is, in step 10, the data user's signature key K_user_sign_priv digitally signs the data hash value of the data used to obtain the user's data signature S_user_data, and the data owner's signature key K_owner_sign_priv performs a second signature on the user's data signature S_user_data to obtain the owner Party data signature S_owner_data;
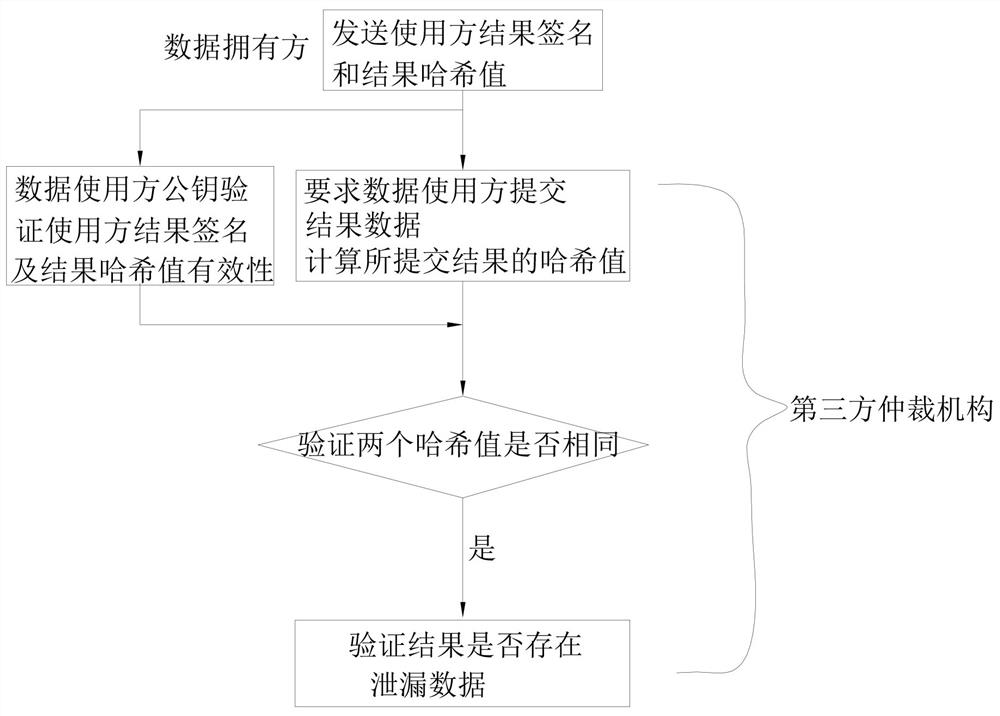
[0103] That is, in step 12, the data operation unit calculates the hash value of the result to obtain the result hash value, and obtains the user result signature S_user_result based on the data user signature key K_user_sign_priv, and the data owner signature key K_owner_sign_priv signs the user result S_user_result Perform secondary signature to obtain owner result signature S_owner_result.
Embodiment 4
[0105] This embodiment is similar to Embodiment 1, the difference is that the signature key of the data user in this embodiment is trusted and securely stored in the data authorization unit, when the data user uses the data in the data center again in the future , directly extract the signature key of the corresponding data user, without sending the signature key every time the data center is used. The signature key is credibly and securely stored in the data authorization unit, which can be based on solidified technology of hardware trusted computing, such as IntelSGX Sealing.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com