Method and system for protecting internet chat privacy
An Internet and privacy technology, applied in the field of Internet information technology transmission security, can solve the problems of unprotected chat records, high difficulty in technical means, privacy, etc., achieve fast chat privacy protection, reasonable allocation of manpower and time, and solve chat privacy leaked effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
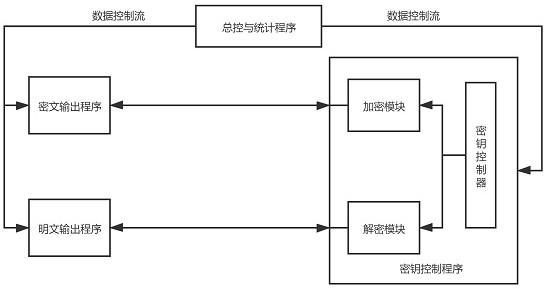
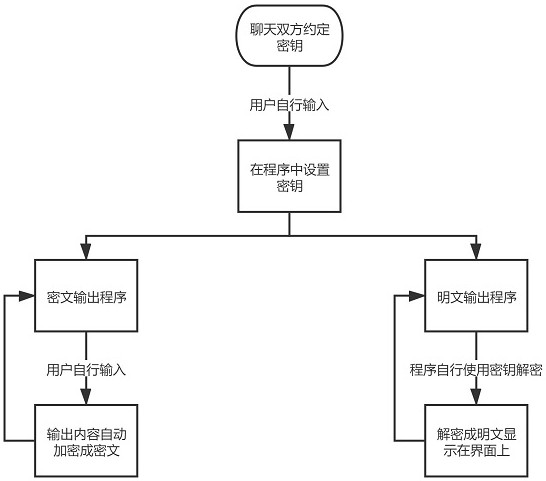
[0051] This embodiment proposes a method for protecting the privacy of Internet chatting. A privacy protection system is embedded in the Internet terminals of both parties or more than two parties in the chat, and then the following operations are performed on sending chat content and receiving chat content: figure 1 , figure 2 Shown:
[0052] For sending chat content:
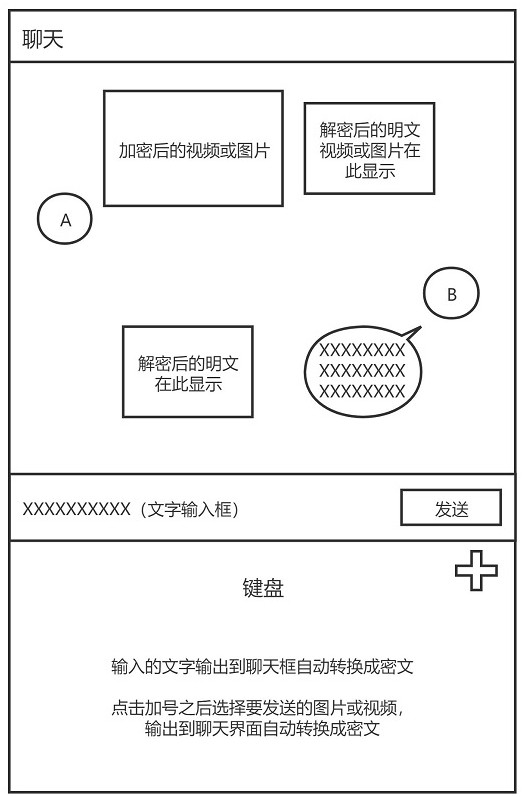
[0053] Step 1: input chat content through the input module of the privacy protection system; the chat content includes text, video and image;
[0054] Step 2: Send the chat content input by the input module to the key control program through the master control and statistics program;
[0055] Step 3: In the key control program, the chat content is sent to the encryption module for encryption after the key is set by the key controller;
[0056] Step 4: Output the encrypted chat content as encrypted chat content through the ciphertext output program and send it to the chat software of the Internet terminal of ...
Embodiment 2
[0063] This embodiment is based on the above-mentioned embodiment 1, in order to better realize the present invention, further, as Figure 4 , Figure 5 As shown, the encryption module and the decryption module use the twofish online encryption algorithm to perform encryption operations.
[0064] The operation of the encryption module to encrypt the text is: use the twofish online encryption algorithm to cut the text input by the chat sender into 128-bit blocks, then encrypt the 128-bit blocks with a variable-length key, and then use the sub-block generated by the key controller. The key is encrypted.
[0065] Example:
[0066] User A intends to send "hello" to user B.
[0067] User A finishes typing through the ciphertext output program, and then selects "Hello".
[0068] Under UTF-8 encoding, a Chinese character has 24 binary digits, and "Hello" has 48 digits in total, which is less than 128 digits. The program will automatically add '\0' to the text until 128 digits are...
Embodiment 3
[0079] In this embodiment, on the basis of any one of the above-mentioned embodiments 1-2, in order to better realize the present invention, further, in the operation of encrypting the chat content by the encryption module, a function is used to iterate the encryption process 16 times. During an iterative encryption process, the relevant replacement of the key is carried out, and the relevant replacement of the key and data is also carried out at the same time.
[0080] Other parts of this embodiment are the same as those of any one of Embodiments 1-2 above, so details are not repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com