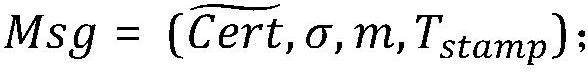Batch authentication method for privacy protection in Internet-of-Vehicles environment
A technology of privacy protection and authentication method, which is applied in the direction of services based on specific environments, vehicle communication, vehicle parts, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
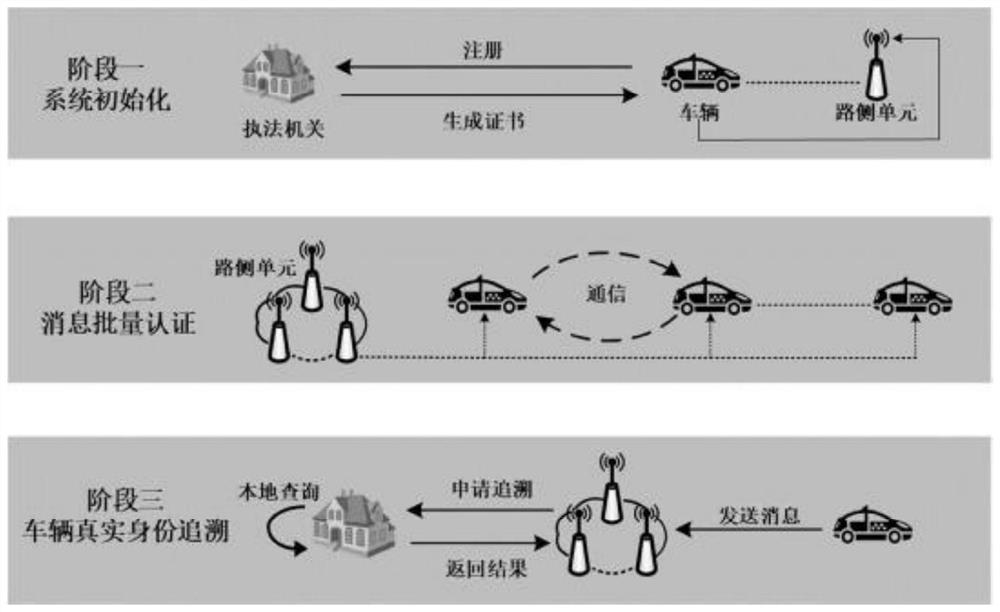
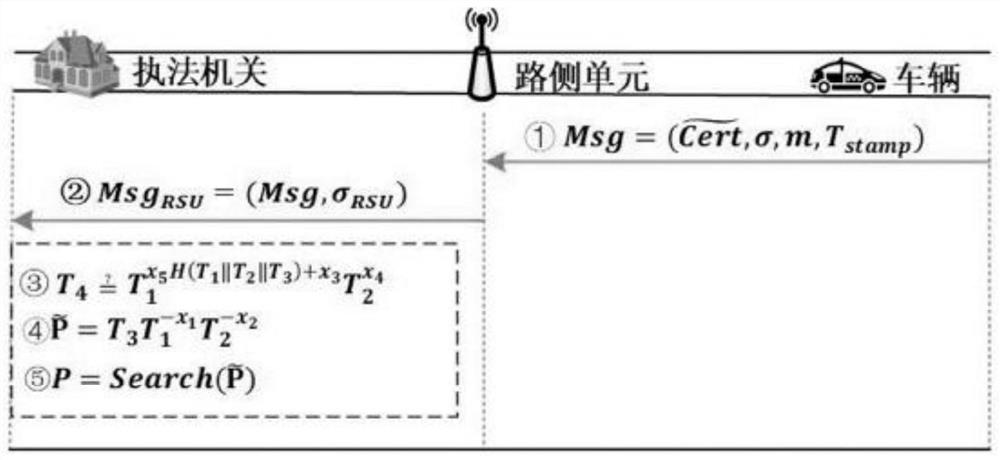
[0057] This example assumes that the three vehicles are Vehicle 1 、Vehicle 2 and Vehicle 3 , the roadside unit is the RSU, and the law enforcement agency is the LEA. Take this as an example to specifically illustrate the above-mentioned links.
[0058] Link i (system initialization generates corresponding parameters):
[0059] The law enforcement agency LEA generates a bilinear map e: G×G→G T , where G is the additive cyclic group, G T is a multiplicative cyclic group of order q. Next, LEA selects the generator g in G, and in G r Choose two different generators g=e(g,g) and h=e(h,h) in . LEA sets the public parameter as para=(q, G, G T , g, g, h, e); Based on the above parameters, LEA selects x, y, x 1 , x 2 , x 3 , x 4 , x 5 , λ∈Z q ,calculate Then the LEA public key pk LEA =(λ, h, Y 1 , Y 2 , Y 3 , Y 4 , Y 5 ), private key sk LEA =(x 1 , x 2 , x 3 , x 4 , x 5 ).
[0060] Stage ii (the corresponding participant completes the registration):
[0061...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com