Active defense method and system for information network security
An information network and active defense technology, applied in the field of network security management, can solve problems such as difficulty in adapting defense measures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
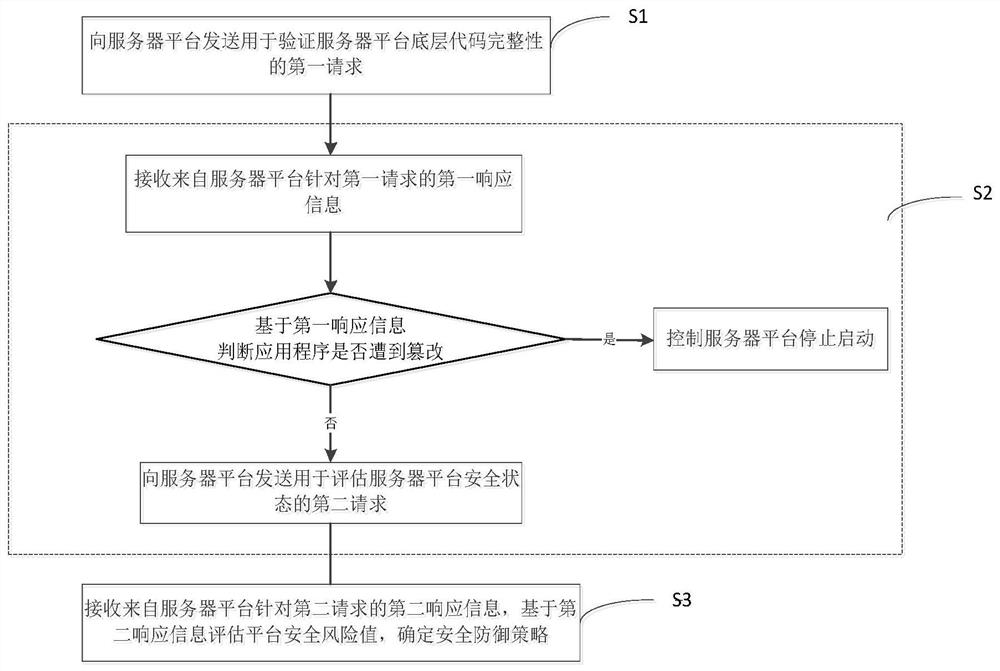
[0056] Embodiment 1: Embodiment 1 of the present invention provides an active defense method for information network security, such as figure 1 As shown, the method includes the following steps:
[0057] S1 sends to the server platform a first request for verifying the integrity of the underlying code of the server platform;
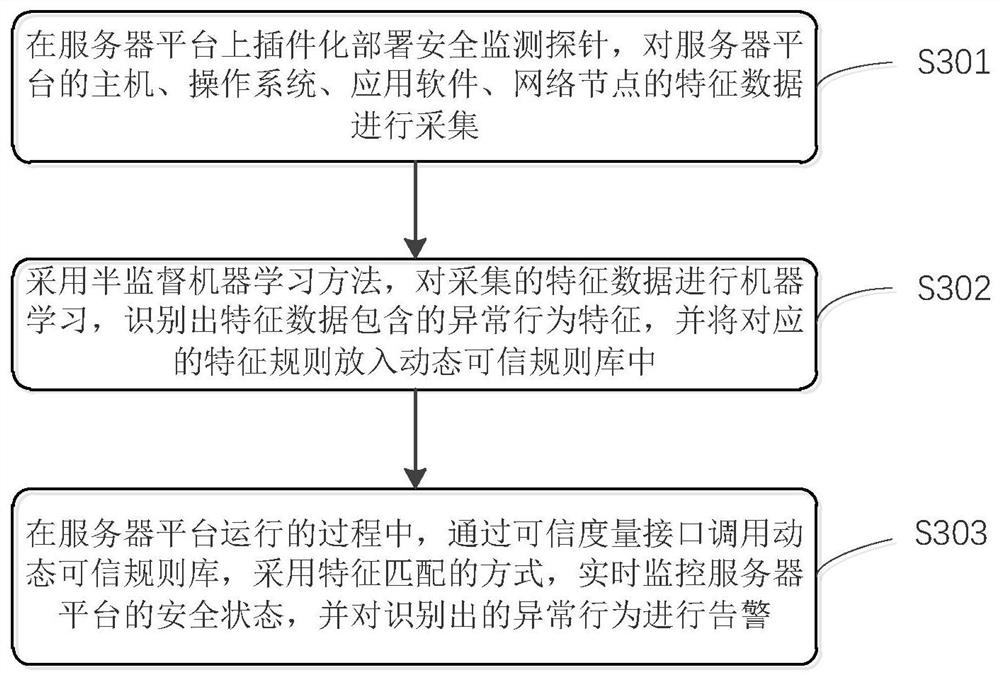
[0058] S2 receives the first response information from the server platform for the first request, and judges whether the application program has been tampered with based on the first response information; if so, then controls the server platform to stop starting; if not, then reports to the server platform sending a second request for evaluating the security status of the server platform; wherein the first response information includes a code hash value collected during startup of the server platform; and comparing the hash value of the code with the initial trust The underlying code integrity verification results obtained by the difference between valu...
Embodiment 2
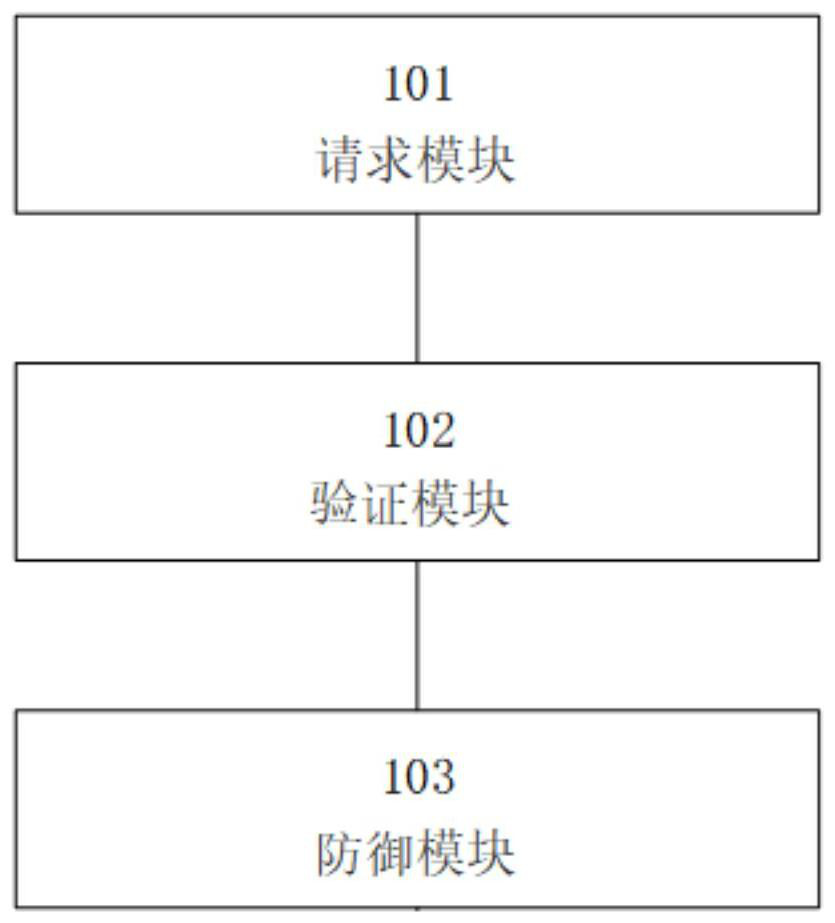
[0092] Based on the same technical concept, Embodiment 2 of the present invention also provides an active defense system oriented to information network security, such as image 3 As shown, the system includes:
[0093] The request module 101 is configured to send to the server platform a first request for verifying the integrity of the underlying code of the server platform;
[0094]The verification module 102 is configured to receive first response information from the server platform for the first request, and judge whether the application program has been tampered with based on the first response information; if so, control the server platform to stop starting; if not , then send a second request for evaluating the security status of the server platform to the server platform; wherein, the first response information includes the code hash value collected during the startup process of the server platform; and by comparing the hash value of the code The bottom code integrit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com