Adapter signature generation method based on SM2 algorithm
An adapter and algorithm technology, applied in digital transmission systems, user identity/authority verification, secure communication devices, etc., can solve problems such as lack of adapter signatures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
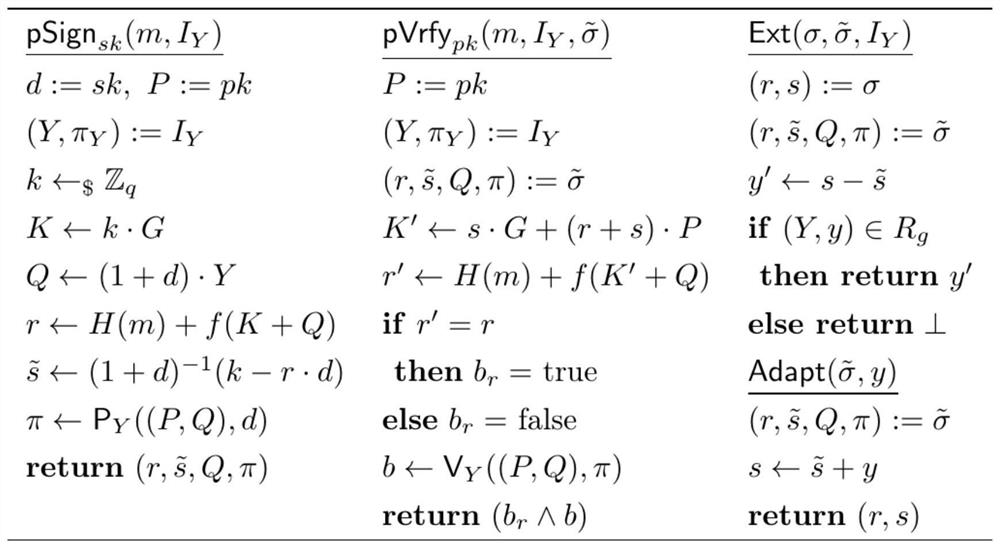
[0022] First, explain the symbols and definitions involved in this embodiment.
[0023] The group of elliptic curves whose order is a prime number q, whose elements are points on the elliptic curve.
[0024] G: cyclic group A generator of .
[0025] The set of integers consisting of the integers 1, 2, ..., q-1.
[0026] mod n: modulo n operation.
[0027] H( ): cryptographic hash function
[0028] m; message value
[0029] σ: signature value
[0030] ||: bit string concatenation
[0031] The four algorithms involved in this embodiment are introduced below: a pre-signature generation algorithm, a pre-signature verification algorithm, an adaptation algorithm, and an extraction algorithm.
[0032] Suppose the security parameter λ is input, the system parameter is The signer generates its public-private key pair according to the key generation algorithm of the SM2 signature algorithm, and records its private key sk as Its public key pk is P=sP. Discrete Logarithm ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com