Network information security protection device and use method thereof
A security protection device, network information technology, applied in the field of protection devices, can solve the problems of unavoidable computer, computer damage, damage and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
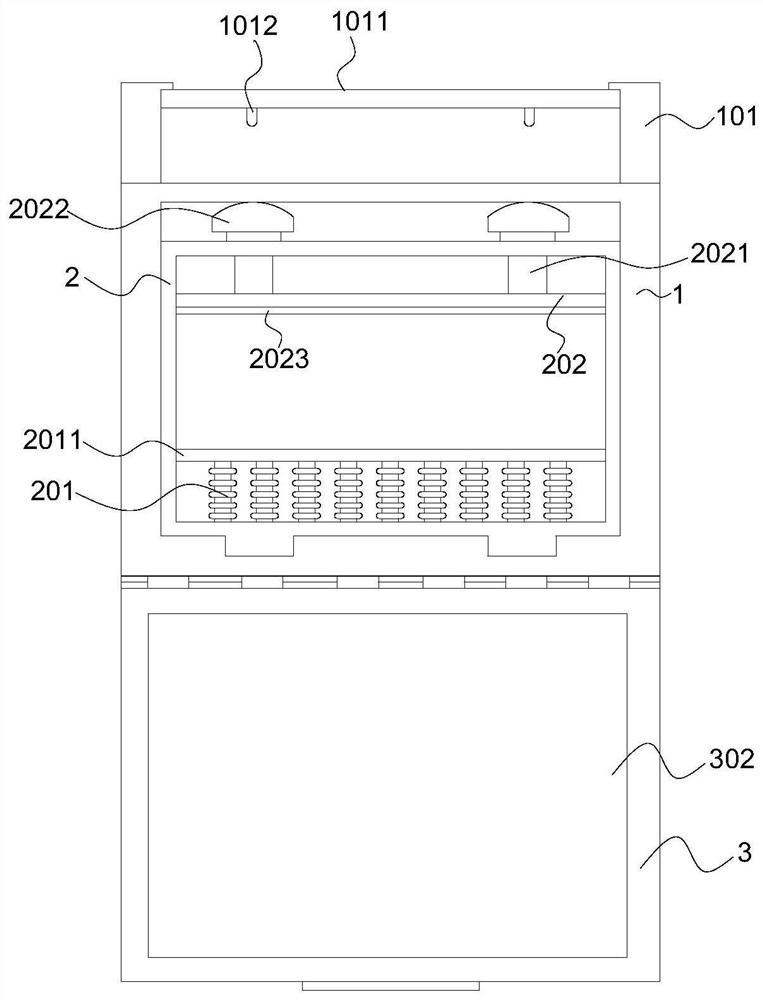
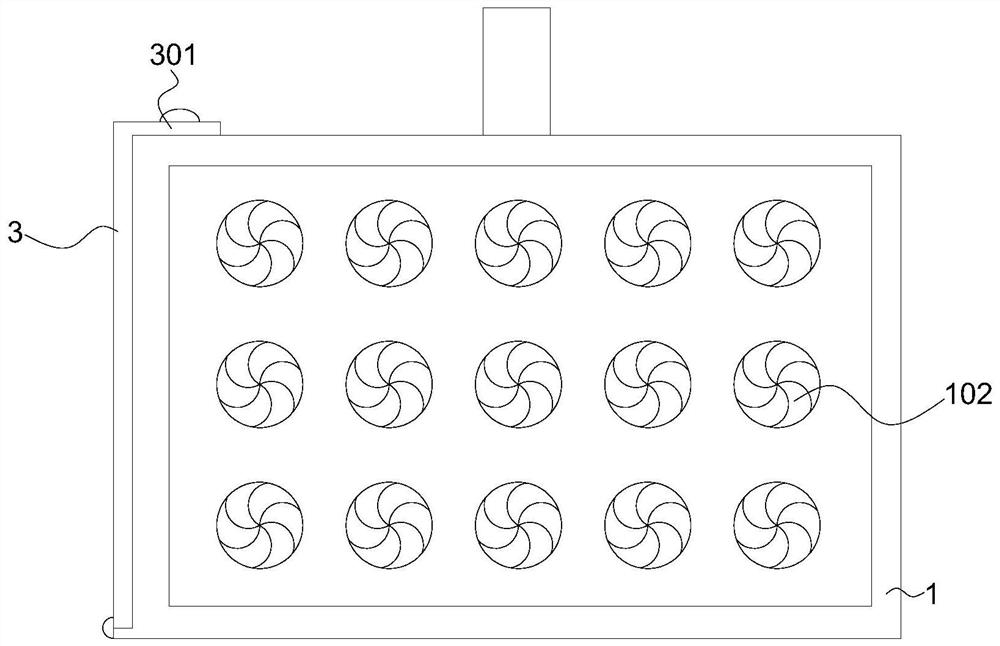
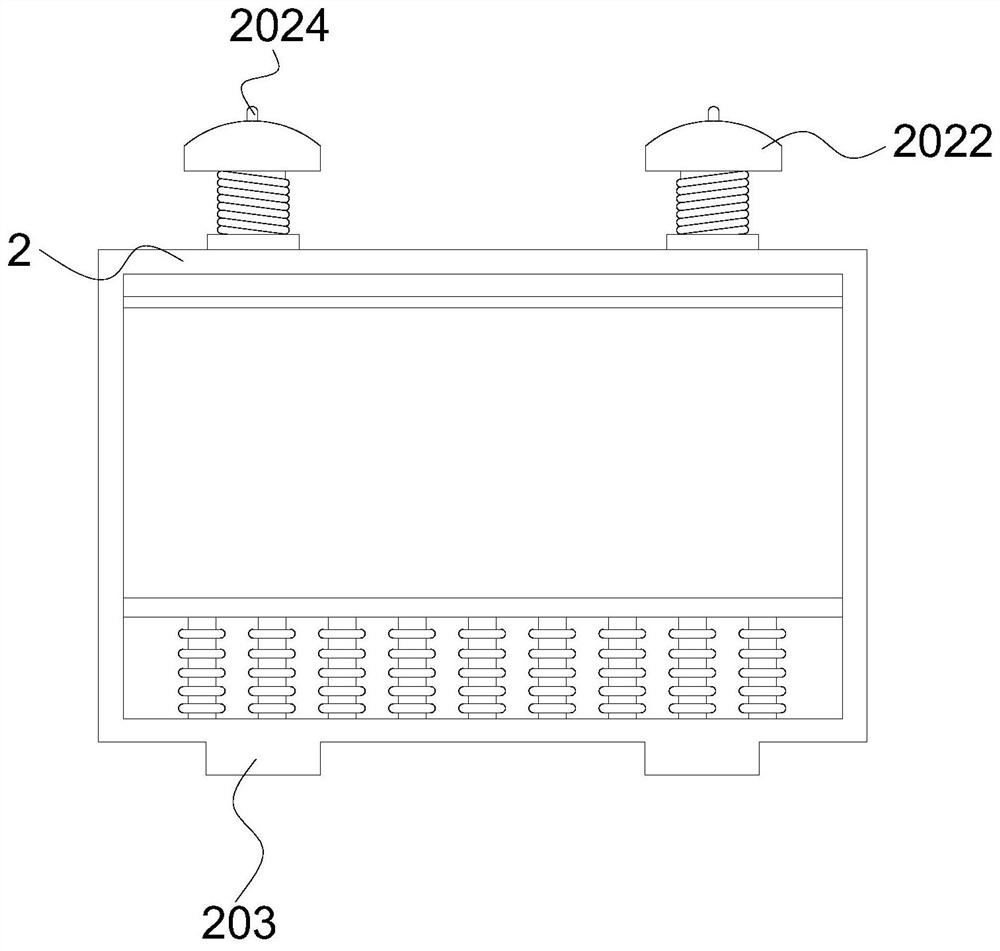
[0042] Please refer to figure 1 with figure 2 , figure 1 It is a schematic diagram of the unfolded structure of the protective device according to the embodiment of the present invention; figure 2 It is a schematic diagram of the side view structure of the protective device according to the embodiment of the present invention;
[0043] The embodiment of the present application provides a network information security protection device, which includes a box body 1 and a protective shell 2 slidably arranged in the box body 1. A plurality of shock absorbers 201 are installed on the inner bottom of the protective shell 2, and a plurality of shock absorbers 201 The top is connected with a bottom plate 2011, and the top of the protective shell 2 is equipped with an elastic locking mechanism. The top of the protective shell 2 is provided with a top plate 202 connected with the elastic locking mechanism. The elastic locking mechanism includes a limit block 2022, a spring and a conn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com