Design method of intrusion detection system based on Bayesian neural network
An intrusion detection system and neural network technology, applied in the field of intrusion detection system design, can solve the problems of poor interval and delay, dependence, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
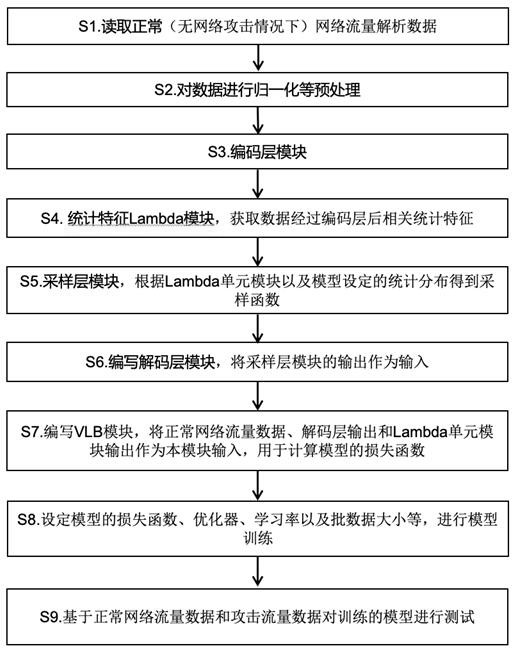
[0039] Such as figure 1 As shown, a design method of intrusion detection system based on Bayesian neural network, including the following steps:
[0040] S1. Read the normal traffic analysis data and the Mirai zombie traffic analysis data respectively, and merge them. In this embodiment, there are 1,098,677 pieces of traffic analysis data, and each piece of data has 115 analysis fields;
[0041] S2. Preprocessing the data, the preprocessing includes the following steps:
[0042] S201: Perform a shuffle operation on the original data, with the purpose of disrupting the arrangement order;
[0043] S202: Divide the data after the shuffle operation into a training set, a verification set, and a test set;
[0044] S203: Perform mean / variance normalization processing on the training set, in order to prevent data leakage, perform normalizat...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap