Safety visual management method and management device
A technology of management devices and management methods, applied in the field of security visualization management methods and management devices, can solve problems such as poor coordination, safety environment risks, and paralysis, and achieve the effect of improving stability and ensuring the scope of monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
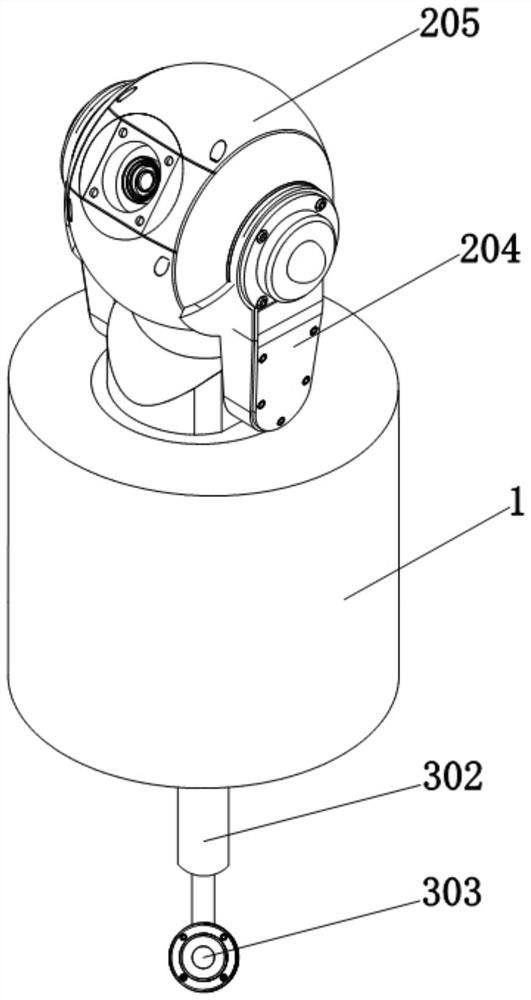
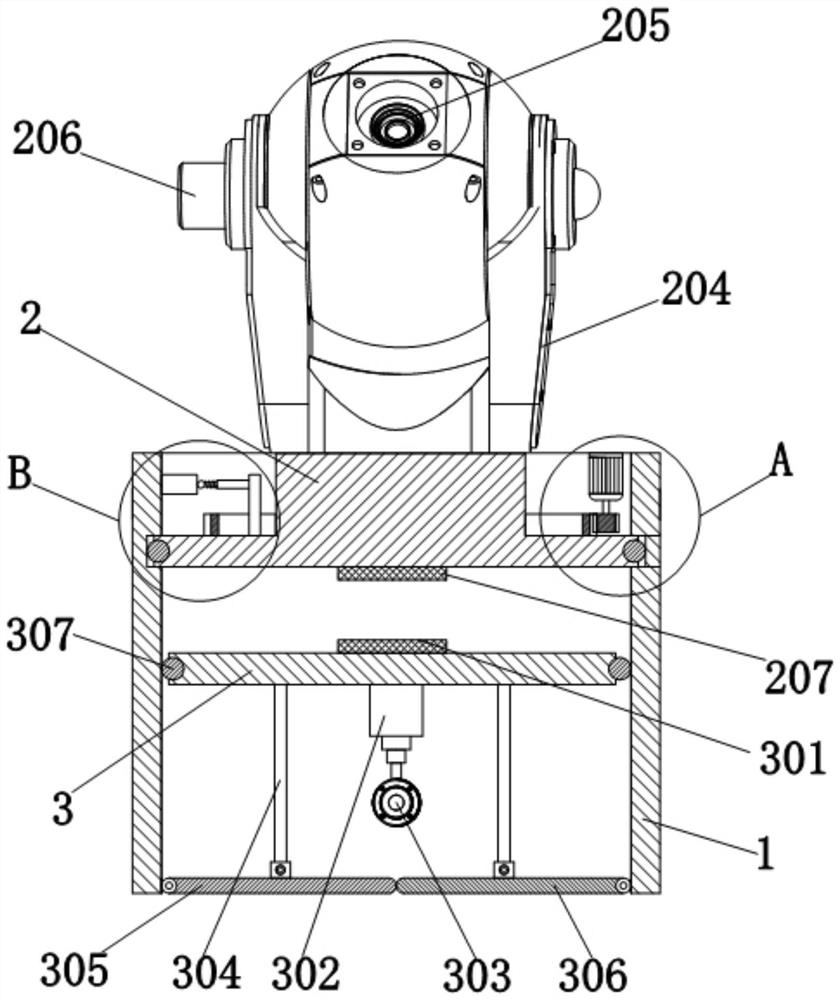
[0032] see Figure 1 to Figure 6 , a safety visualization management device, used to implement a safety visualization management method, the management device includes a support part 1 for supporting the entire device, and one side of the support part 1 is provided with a bracket for fixing the entire management device;
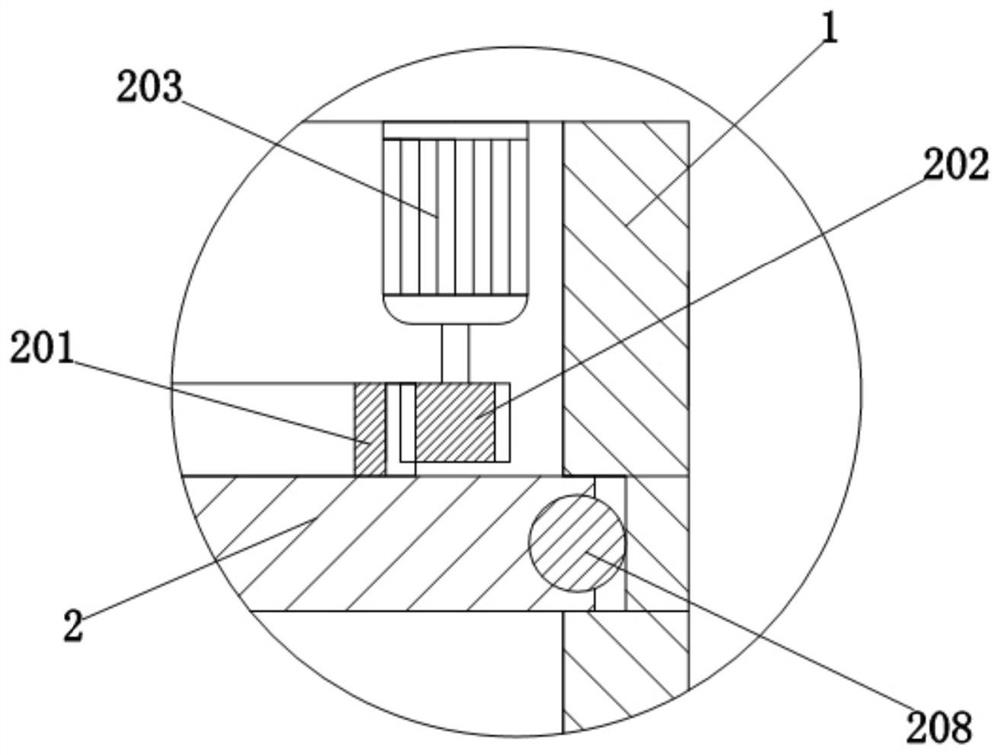
[0033] A first rotating platform 2 is movably embedded in the cavity of the supporting part 1, and the first rotating platform 2 is used to support and adjust the first camera 205; specifically, an annular chute is provided on the inner wall of the supporting part 1, and the first rotating platform 2 is used to support and adjust the first camera 205; Free-rotating sliding balls 208 are evenly embedded on the outer circumference of the rotating platform 2 , and the outer circumference of the first rotating platform 2 and the sliding balls 208 are located in the chute. During the rotation of the first rotating platform 2, its outer circumference and the slidin...
no. 2 example
[0044] When the damaged management device is severely damaged and the first camera 205 is destroyed, the real-time shooting picture cannot be obtained. Even if the first driving motor 203 is controlled to work remotely through the control platform, the shooting picture of the first camera 205 cannot be obtained. Also just can't determine whether the first drive motor 203 works normally, if the first drive motor 203 is damaged, will not be able to drive the first rotating platform 2 to rotate by the first driving motor 203, and then also cannot drive the second rotation by the first rotating platform 2 The platform 3 rotates, and the shooting angle of the second camera 303 cannot be accurately adjusted to capture the personal characteristics of the saboteur. Therefore, before the relevant device works according to the working principle in Embodiment 1, it must be confirmed whether the first driving motor 203 is intact; If the first drive motor 203 is intact, the relevant devices...
no. 3 example
[0050] A security visualization management method, the security visualization management method involves invoking a management device for security management, such as Figure 7-8 As shown, the management method includes the following steps:
[0051] Set up multiple sets of management devices, so that the first camera 205 of any one of the management devices is located within the field of view of the first camera 205 of the adjacent management device, and the second camera 303 of any one of the management devices is located in the adjacent management device within the field of view of the second camera 303 of the device; to ensure that when the first camera 205 of any management device is artificially destroyed, the angle of the first camera 205 of the nearest or adjacent management device can be remotely adjusted by the control platform , to capture the information of saboteurs, so that each management device can cooperate with each other, and improve the stability of monitoring...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com