A privacy protection method for encrypted smart contracts based on trusted execution environment
A smart contract and execution environment technology, applied in digital data protection, secure communication devices, instruments, etc., can solve the problems of high communication overhead, inability to protect the privacy of smart contract code, identity confirmation, etc., and achieve the effect of ensuring safe execution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
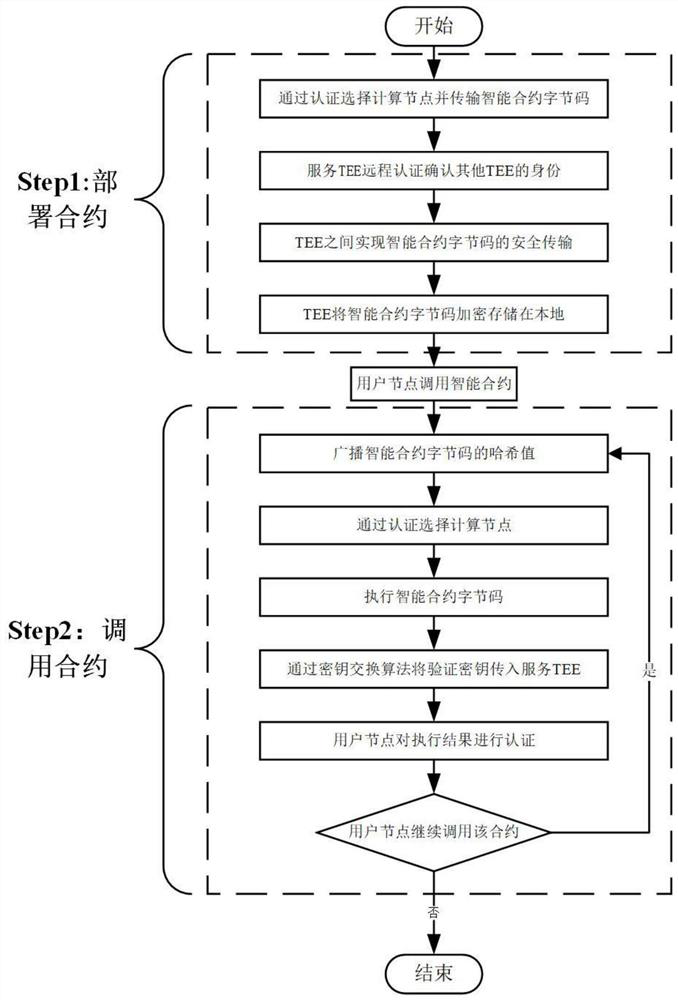
[0034] Embodiment 1: A smart contract privacy protection method based on a trusted execution environment and encryption, the method includes three types of nodes: a user node, a computing node and an authentication center, and two steps: contract deployment and contract invocation, as follows:
[0035] Three kinds of nodes:
[0036] 1) User node, user_node: a node that can initiate requests to computing nodes, including contract deployment and contract invocation;
[0037] 2) Compute node, compute_node: a node that carries TEE and can execute smart contract bytecodes in TEE;
[0038] 3) Certification center, certificate_authority: a node containing all legal TEE information, which can be used to verify whether the TEE carried by the node is legal;
[0039] like figure 1 Two steps shown:
[0040] Step1 Contract deployment: The user node user_node uses the legal computing node table legal_table provided by the certificate_authority of the certification center to select a comp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com