Signature and decryption method and system based on SM2 algorithm
An algorithm and key technology, applied in transmission systems, digital transmission systems, and key distribution, can solve the problems of increased computational overhead, low efficiency, and low security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
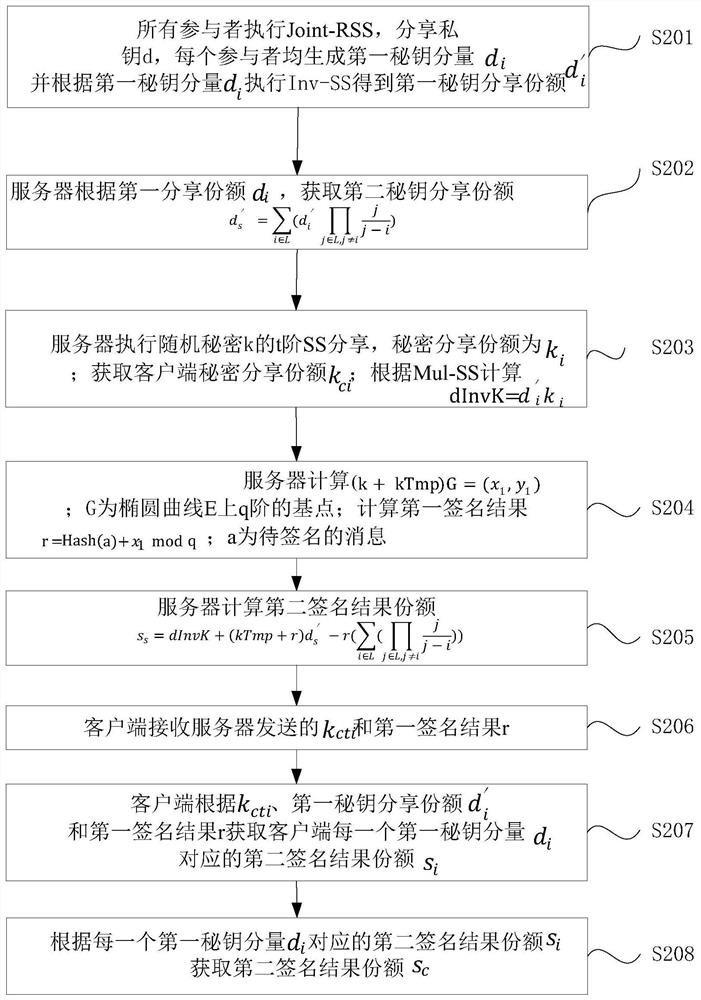
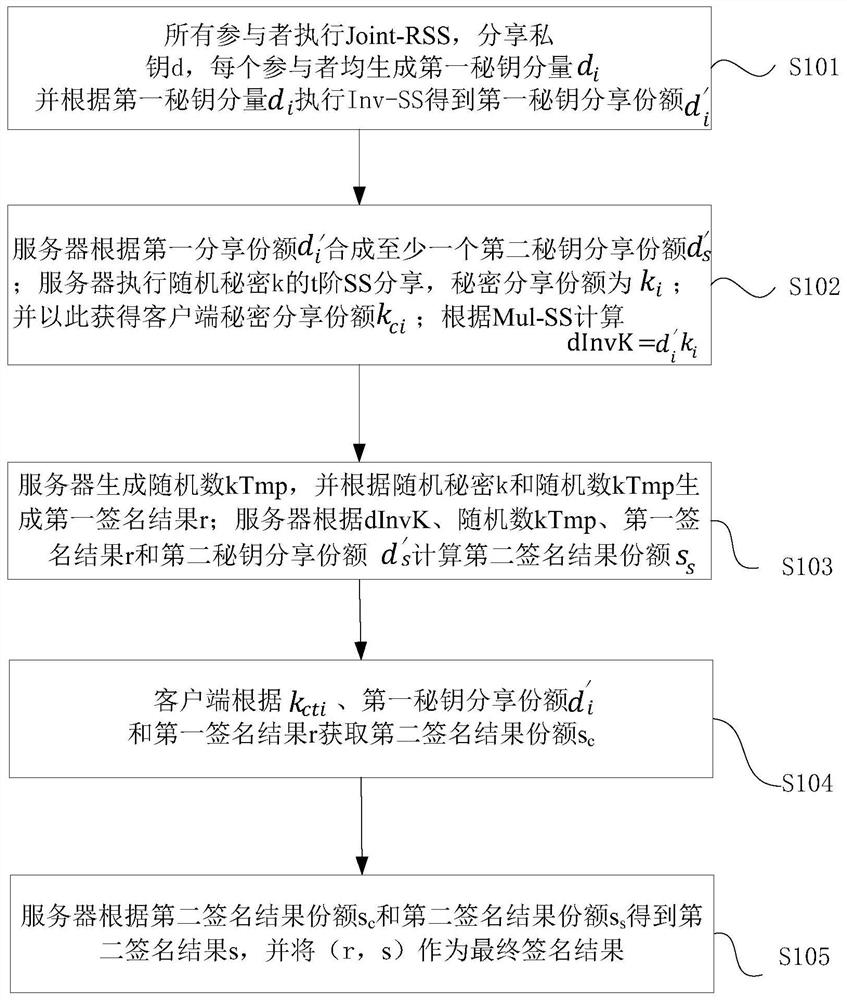
[0038] Such as figure 1 as shown, figure 1 It is a schematic flowchart of a signature method based on the SM2 algorithm provided by the embodiment of the present invention. The embodiment of the present invention provides a signature method based on the SM2 algorithm, which is applicable to multiple data contributors (participants) providing joint data usage In the field of authorization features, the method can be implemented by a signature system based on the SM2 algorithm.
[0039] In this embodiment, the server includes m participants; the client includes n participants. Both m and n are positive integers; among them, n≤t, m≥t+1, m+n≥2t+1; t is the threshold value. In this embodiment, the devices involved in the signature and decryption process include a server and at least one client. In this embodiment, a client and a server are used as an example to illustrate, where the server includes m participants, and the client includes n Participants, limit the threshold value...
Embodiment 3
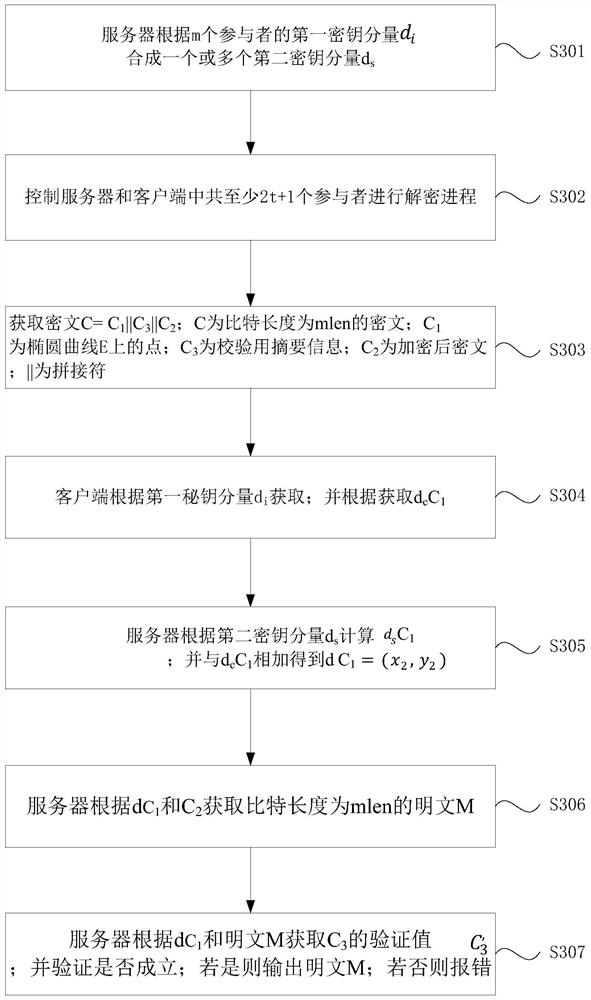
[0080] like image 3 as shown, image 3 It is a schematic flowchart of a decryption method based on the SM2 algorithm provided by the embodiment of the present invention. The embodiment of the present invention provides a decryption method based on the SM2 algorithm, which is applicable to multiple data contributors (participants) providing joint data usage In the field of authorization characteristics, the method can be performed by a decryption system based on the SM2 algorithm. In this embodiment, the server and the client are not less than 2t+1 participants to perform the relevant process, which specifically includes the following steps:
[0081] S301. According to the first key component d of m participants, the server i synthesize one or more second key components d s .
[0082] The server may send multiple first key components d i synthesize a second key component d s , then the server synthesizes at least one second key component d according to the first key compo...
Embodiment 4
[0115] continue to refer Figure 5 , Figure 5 It is also a schematic structural diagram of a decryption system based on the SM2 algorithm provided by the embodiment of the present invention. This embodiment provides a decryption system based on the SM2 algorithm, and the system includes:
[0116] Client 51, the client includes n participants; each participant generates the first secret key component d i ; The client is used to get d i C 1 ; and get d c C 1 ;d c is the first secret key component d in the client i The synthetic key component of ;
[0117] Server 52, the server includes m participants; each participant generates a first key component; the server synthesizes one or more second key components d according to the first key components of m participants s ; and get d s C 1 ; and d s C 1 with d c C 1 Add up to get dC 1 ; The server is also used to 1 Obtain the plaintext M corresponding to the ciphertext C, and verify the plaintext M; both m and n are po...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com