V2X communication system, communication key distribution method and implicit authentication method
A communication system and communication key technology, applied in the field of intelligent vehicle communication, can solve problems such as low security, and achieve the effects of ensuring security and reliability, improving reliability and security, and improving security and reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
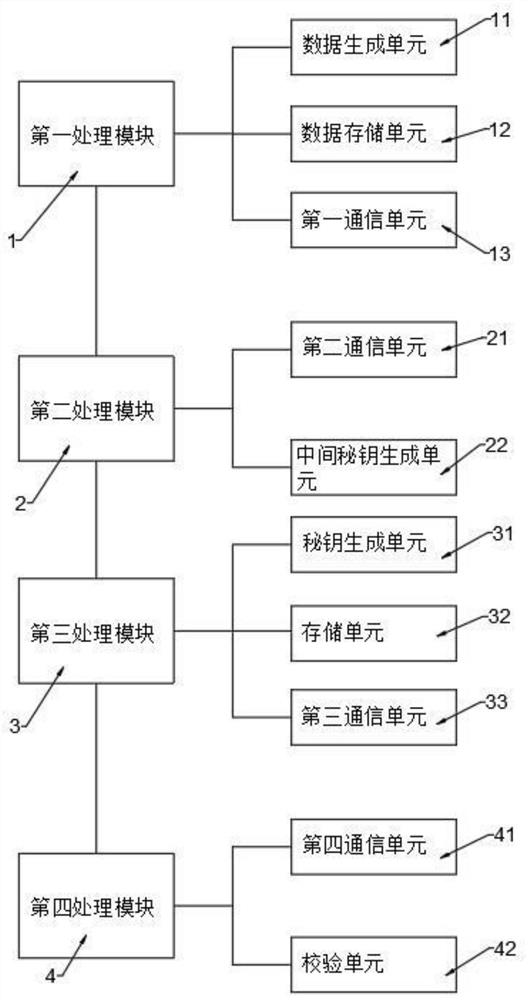
[0069] This embodiment is regarded as a basic embodiment of the present invention, such as figure 1 As shown, it discloses a V2X communication system, including a first processing module 1, a second processing module 2, a third processing module 3 and a fourth processing module 4, the first processing module 1 is built in the vehicle end, The first processing module 1 includes a data generation unit 11 and a data storage unit 12, wherein the registration certificate generated based on the real identity information of the vehicle is stored in the data storage unit 12, and the private key and the return certificate are also stored in the data storage unit 12. And verify the pseudonym certificate passed; the data generation unit 11 generates the first request information for applying for the pseudonym certificate according to the registration certificate, and also generates the second request information for interactive communication in the system according to the vehicle key pack...
Embodiment approach 2
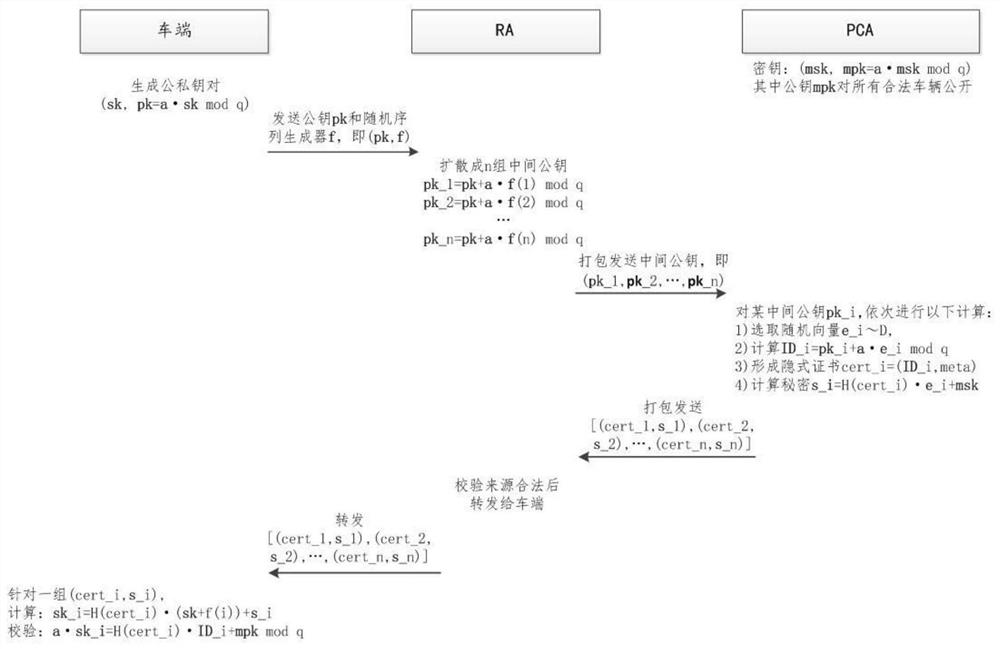
[0074] This embodiment is regarded as a preferred embodiment of the present invention, such as figure 2 As shown, it discloses a V2X communication key distribution method, including the following steps:
[0075] S1. The vehicle presets a registration certificate bound to the real identity when leaving the factory, and the customer sends a request to activate the registration certificate to the second processing module through the first processing module or sends a VIN code to the second processing module for activation;
[0076] Generate the first request information by the first processing module, and send the first request information to the second processing module; the message of the first request information includes: pseudonym certificate application request, statement number n, random function f(·) and Certificate of Registration;
[0077] S2. Receive the first request information, analyze the first request information, and extract the application number n and the ran...
Embodiment approach 3
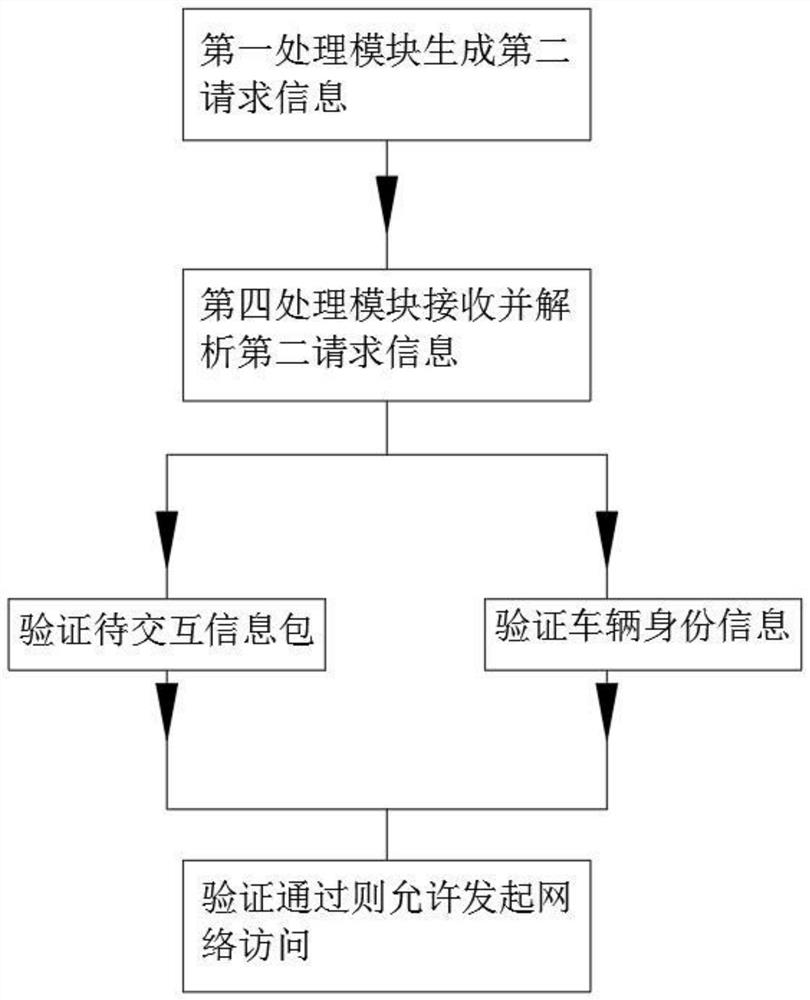
[0095] This embodiment is regarded as a preferred embodiment of the present invention, such as image 3 As shown, it discloses a V2X key implicit authentication method, including the following steps:
[0096] S1. The first processing module randomly selects a set of corresponding signature key pairs and implicit certificates from the stored valid pseudonym certificates, and randomly selects {0, 1} coefficient polynomial e;
[0097]Calculate the signature according to the signature private key pair, and combine the communication information M to be sent to generate the information packet to be exchanged. The expression of the signature is Sign=sk'+H(M||Timestamp||cert||t)×emodq, Wherein said t=a*emodq;
[0098] Generate the information package to be interacted with according to the signature, and then integrate the vehicle identity information and the information to be interacted into the second request information, wherein the expression of the information package to be inter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com