PHP static code analysis method based on taint analysis
A static code and taint analysis technology, applied in the field of network security, can solve problems such as inability to correctly identify, inability to adapt to new version of PHP syntax features, new feature false positives, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The technical solution of the present invention will be specifically described below in conjunction with the accompanying drawings.
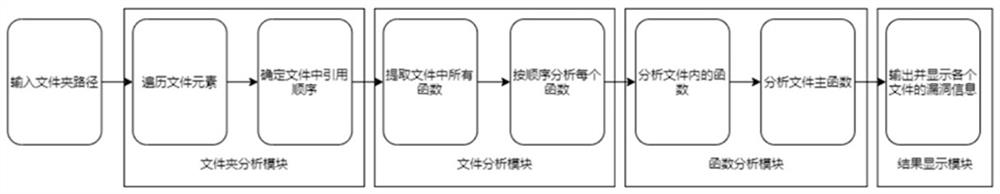
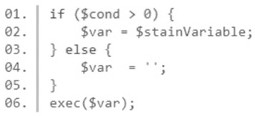
[0028] A PHP static code analysis method based on taint analysis in the present invention, firstly, lexical analysis and syntax analysis are performed on PHP static code, and an abstract syntax tree corresponding to the code is constructed; secondly, the abstract syntax tree is divided into different sub-functions, and the taint is used The analysis technology marks the tainted data flow in each function; finally, according to the nature of the parameters of the confluence point of the tainted data flow, it is determined whether there is a vulnerability.
[0029] Based on a PHP static code analysis method based on taint analysis of the present invention, the present invention realizes a PHP static code vulnerability detection prototype tool based on taint analysis, that is, the static code analysis tool is introduced into the coding stage,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com