Method for identifying flow of application program under SSR proxy based on machine learning
An application and traffic identification technology, applied in the field of network security, can solve the problem of low application identification accuracy, improve the identification accuracy and reliability, and complete the identification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
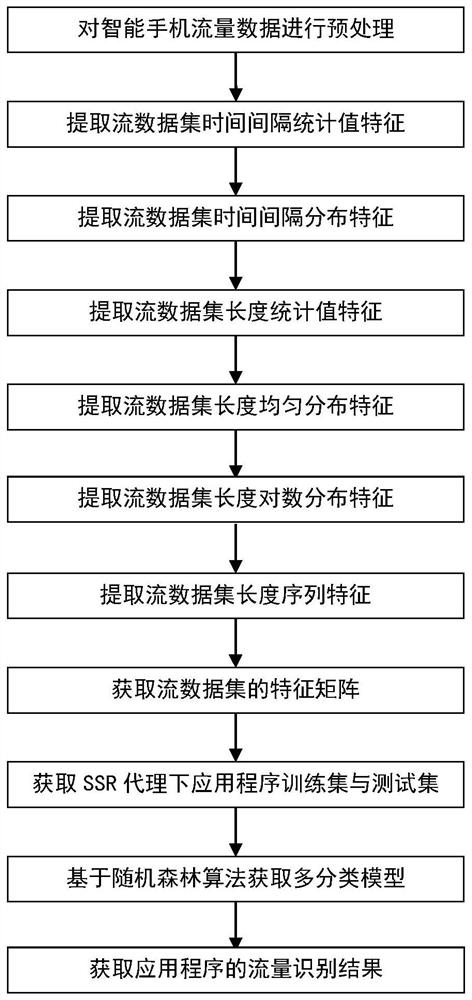
[0084] Embodiment one: refer to figure 1 and figure 2 , the application traffic identification method under the SSR agent based on machine learning proposed by the present invention, specifically includes the following steps:
[0085] Step 1. Obtain the traffic data of the smart phone, and preprocess it according to the following steps:
[0086] (1a) select the TCP data packet in the non-retransmission data packet in the traffic data to form the original data set;
[0087] (1b) According to the arrival time of the data packets in the original data set, sort all the data packets in ascending order, and obtain the original data set after sorting;
[0088] (1c) Group the data packets in the sorted original data set according to the following rules to obtain the burst data set B:
[0089] (1c1) taking the first data packet in the original data set after sorting as the first data packet of the first data burst group;
[0090] (1c2) After traversing the data packets in the orig...
Embodiment 2
[0155] Embodiment 2: The implementation steps of this embodiment are the same as those of Embodiment 1. For some of the settings and parameters given preferred values, the technical solution of the present invention is further described as follows:
[0156] Step 1) Obtain smart phone traffic data, and preprocess the smart phone traffic data:
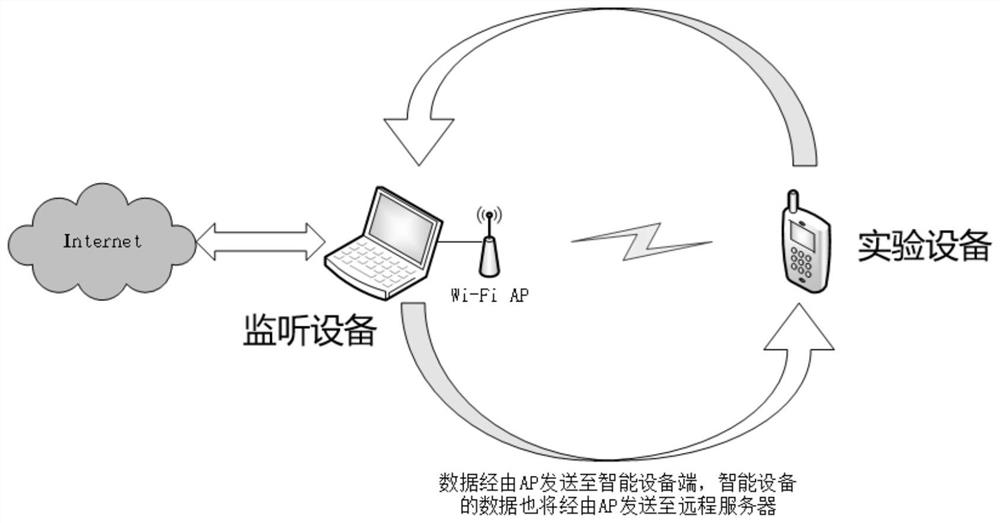
[0157] Step 1a) needs to turn on the hotspot of the computer with the wireless network card, and connect the smartphone used for the experiment to the hotspot. Open the ShadowsocksR agent on the smartphone, run the applications Telegram, Youtube, Twitter and Instagram respectively, and clean up all the applications that can be closed in the background when running an application. At this time, the traffic generated by the smartphone will all flow through the computer with the hotspot turned on. By enabling WireShark packet capture on the computer with the hotspot enabled, you can obtain all the traffic of the corresponding application t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com