Symmetric key dynamic generation method based on Internet of Things
A symmetric key and dynamic generation technology, applied in the field of encryption, can solve problems such as ciphertext cracking, and achieve the effects of ensuring security, preventing hijacking by middlemen, and achieving differentiation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
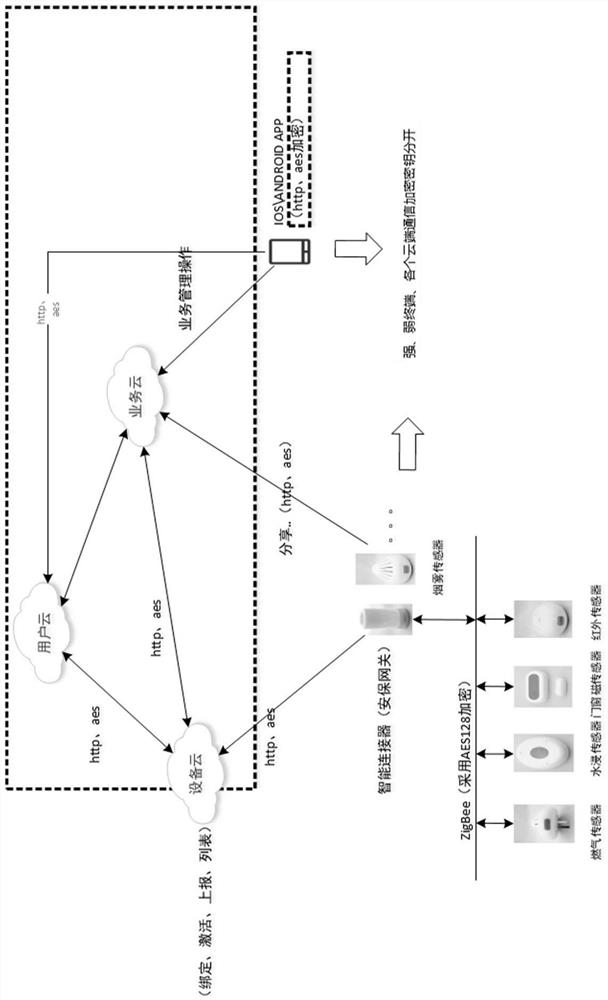
[0022] combined with figure 1 As shown, a method for dynamically generating a symmetric key based on the Internet of Things uses the generated byte array as a partial symmetric encryption key. The key is persistently stored in the cloud corresponding to the terminal SN and version number, and the terminal is prefabricated to save this part The symmetric key and version number, the other part of the key is randomly and dynamically generated, and the version number is attached to the ciphertext and transmitted through the network to the cloud or terminal. When using the key, the dynamic key is combined with the previous static key to form a complete key for decryption. The specific implementation plan and steps are as follows:
[0023] Step 1. The cloud randomly generates no less than 6 groups of byte arrays as partial keys. If a random character string is used as the key, the character string includes 0~9, a~z, A~Z and special characters. The range of converting these charac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com