Malicious domain name detection method and device based on deep reinforcement learning
A technology of reinforcement learning and domain name detection, applied in the field of network security, can solve the problem of data imbalance between benign domain names and malicious domain names
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below through specific embodiments and accompanying drawings.
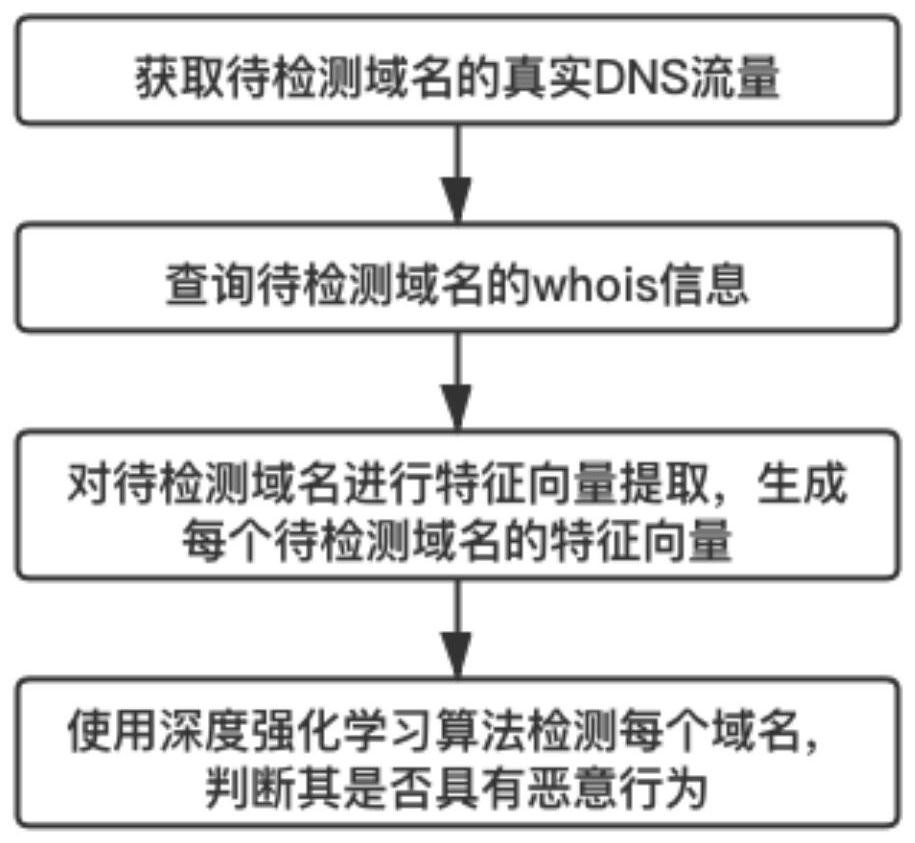
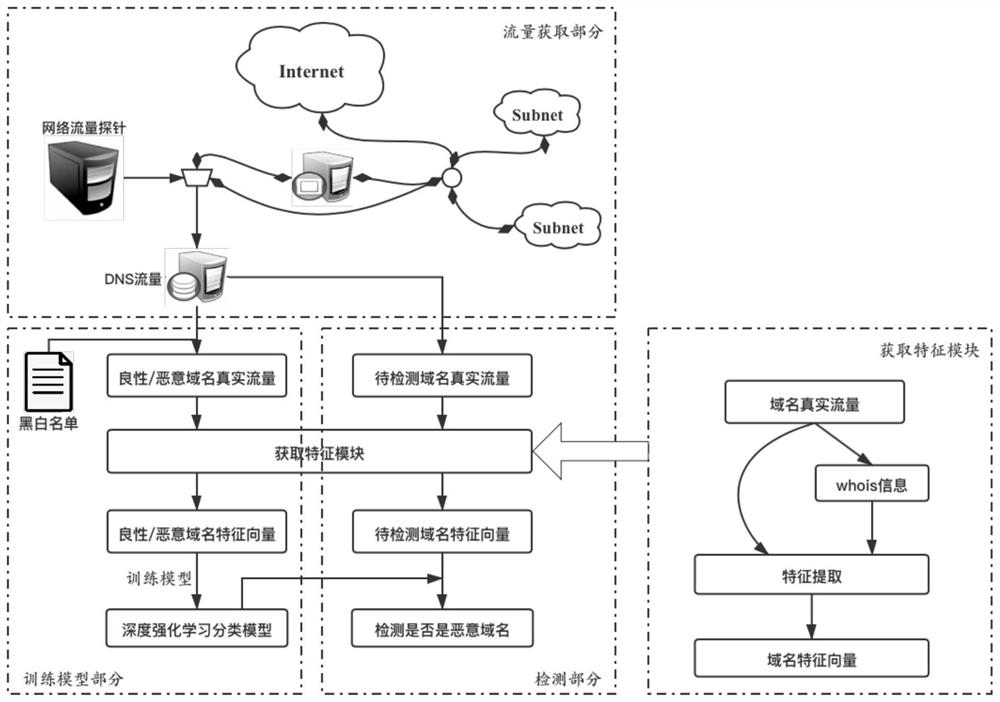
[0035] The invention provides a method for judging a malicious domain name. It first obtains the domain name to be detected through real DNS traffic, and after querying whois information, extracts features of the domain name to be detected, and finally inputs the feature vector into the deep reinforcement learning model to obtain each Whether the domain name to be detected has malicious behavior.
[0036] The workflow of the present invention is as figure 1 shown.
[0037] 1) Obtain the real DNS traffic of the domain name to be detected: set up a network probe in the network, obtain real DNS traffic data for several days, and store it in the traffic database.
[0038] 2) Supplement whois information: query and record their whois information for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com