SDN flow table overflow attack detection and mitigation method based on machine learning
An attack detection and machine learning technology, applied in machine learning, instruments, computer components, etc., to achieve high accuracy, real-time detection and mitigation, and precise classification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described below in conjunction with the accompanying drawings.
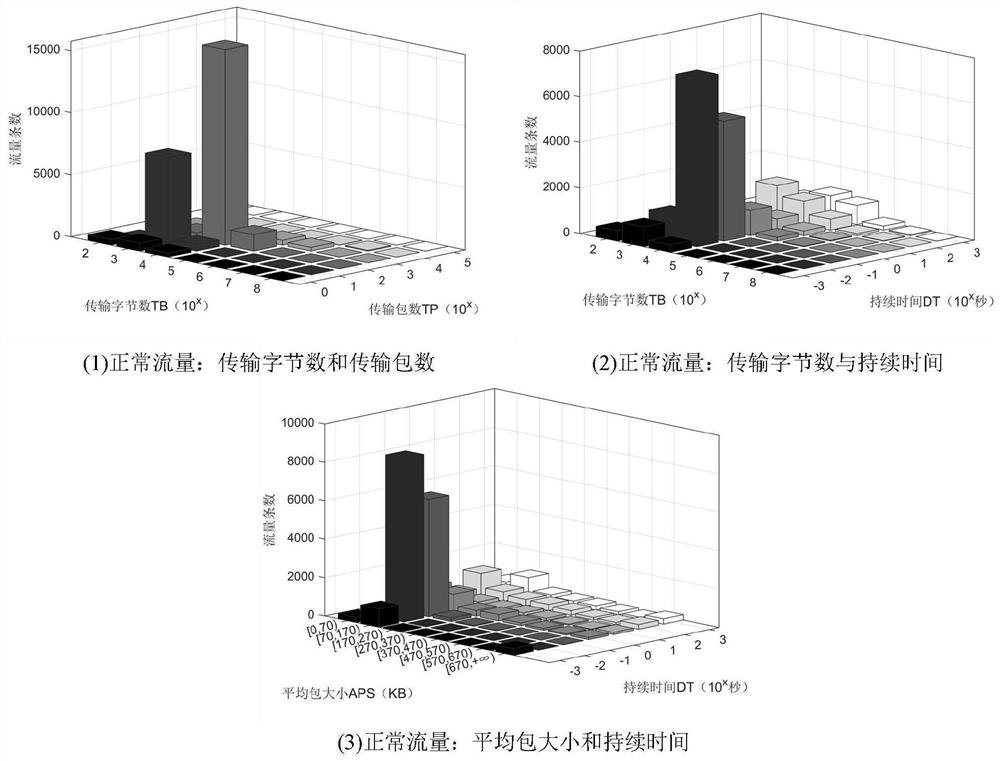
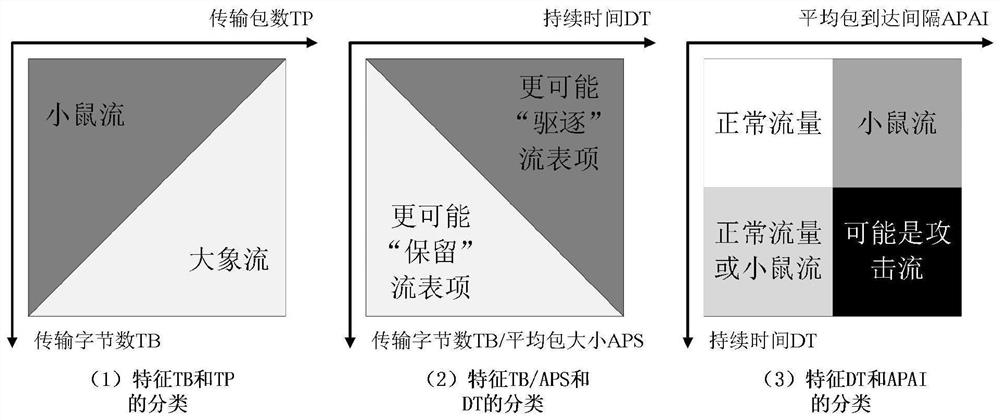
[0023] Such as Image 6 As shown, the detection method of the flow table overflow attack mainly includes six steps: flow table data sampling, flow table field division, traffic type marking, classification model training, attack determination detection, and flow table overflow mitigation.
[0024] 1. Stream table data sampling. Use the OpenFlow message event OFPFlowStatsRequest / OFPFlowStatsReply or the OpenvSwitch command line program to poll and sample the flow table of the switch to obtain all the information in the flow table of the current switch.
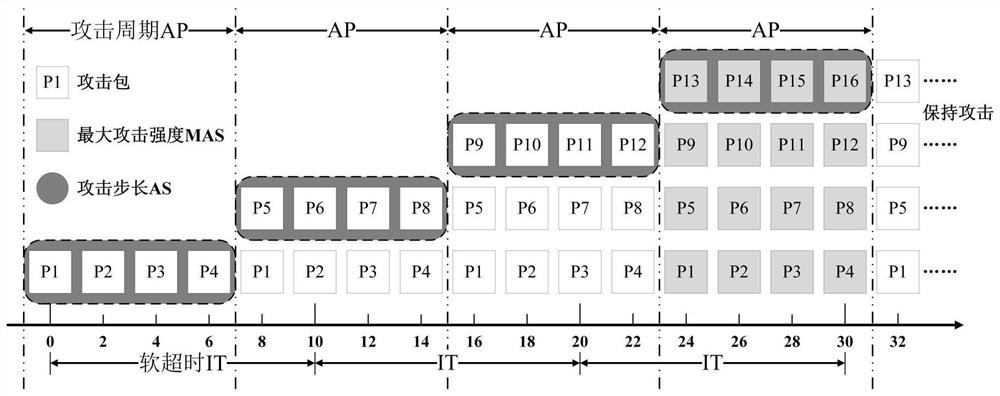
[0025] The polling sampling interval for the switch flow table is the same as the soft timeout configured for the SDN flow table, so as to prevent inactive flow table entries from generating a large number of duplicate data entries in the data set.
[0026] When polling the switch flow table, count the number of flow ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com