A privacy protection biological authentication method and device, electronic equipment
A technology of biometric authentication and privacy protection, applied in the field of privacy protection identity authentication, can solve the problem of large data storage, and achieve the effect of ensuring secure communication, reducing storage, and easy to use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0084] Example 1: Polynomial:
[0085] One of the most natural and simple ideas is to use polynomials , making the polynomial Satisfy , where the polynomial The coefficients are the data structure of OKVS . When decrypting, we only need to and Do the inner product, you can decrypt to get . From the description, we can know that the polynomial-based OKVS technology is a linear OKVS technology.
example 2
[0086] Example 2: Dense Matrix:
[0087] if there is a Row A random matrix of columns that satisfies , then the probability of linear correlation in this matrix is less than . Based on this, we have a way to construct OKVS by putting map to domain random vector in , then solve the following system of linear equations
[0088]
[0089] Get the data structure of OKVS .
example 3
[0090] Example 3: 3H-GCT (3-Hash Garbled Cuckoo Table)
[0091] 3H-GCT is a form of hash that contains three different hash functions, , assuming this hash table we denote as ,we use represented in the hash table in the elements, then any value If inserted into 3H-GCT, then it will be represented as . The structure of 3H-GCT's OKVS is a linear OKVS. The hash table T is used as the encrypted data structure S in OKVS, and a The upper value is 1, the remaining positions are 0, and the binary vector of length equal to the length of S is used as the mapping of k .
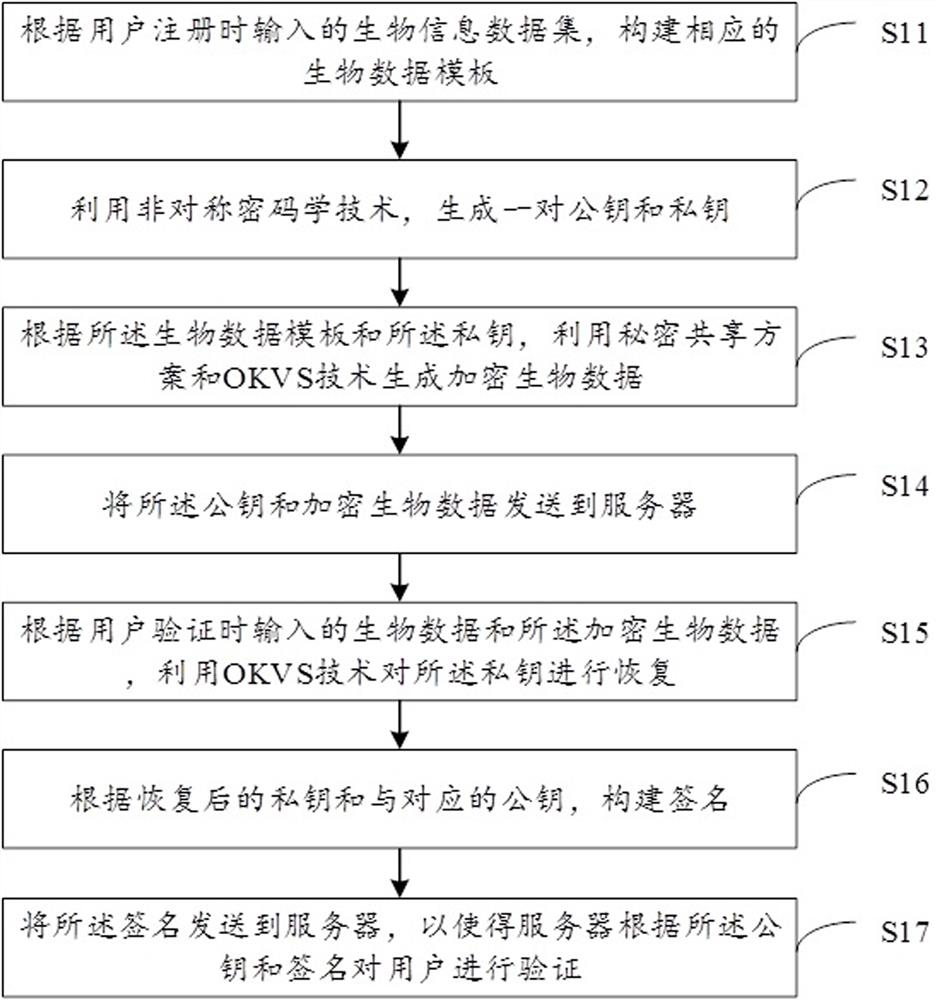
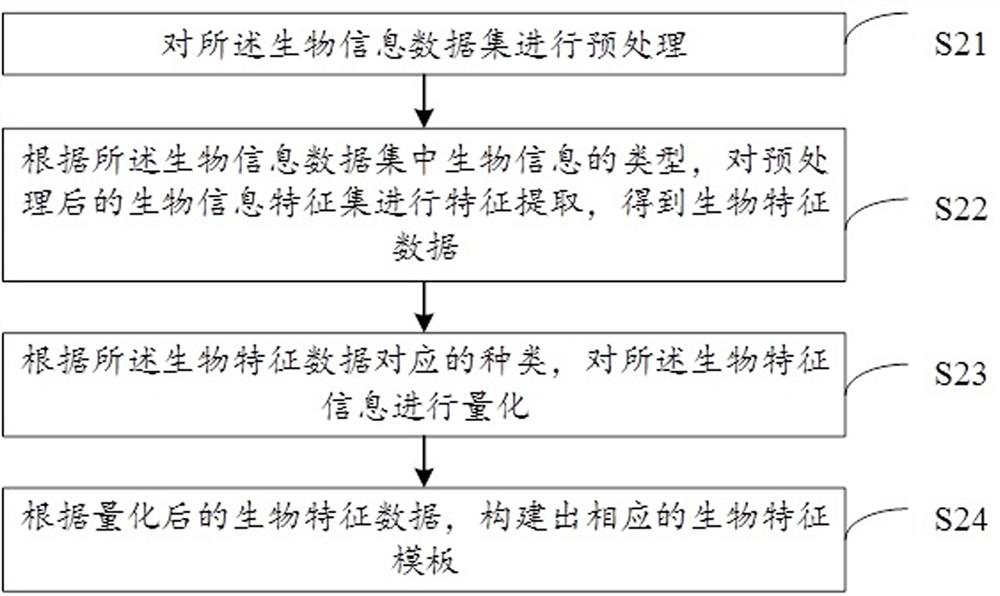
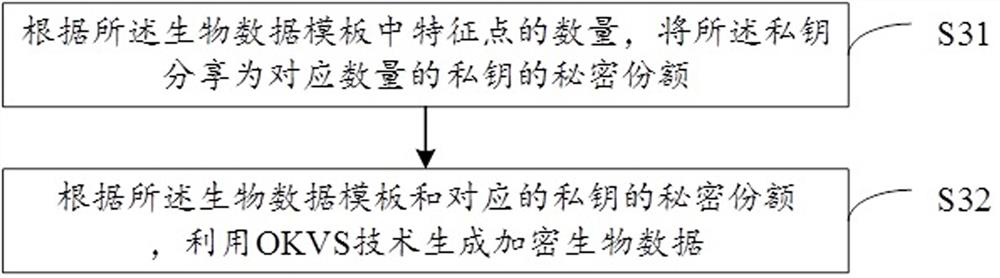
[0092] Assuming that user A needs to use the service provided by the network platform B, then A needs to register account information on the platform and log in to enjoy the service. Both user A and network platform B want to use a privacy-preserving and convenient identity authentication method. User A hopes to use biometric information instead of traditional password keys for identity authentication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com