Tail gas remote sensing data uploading encryption method and system
A technology of remote sensing data and encryption method, applied in digital transmission systems, transmission systems, electrical components, etc., can solve the problems of being easily attacked and tampered, and cannot guarantee the security of exhaust remote sensing detection data, etc., to reduce mutual authentication steps and save money. Pairing time, the effect of enhancing transmission efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
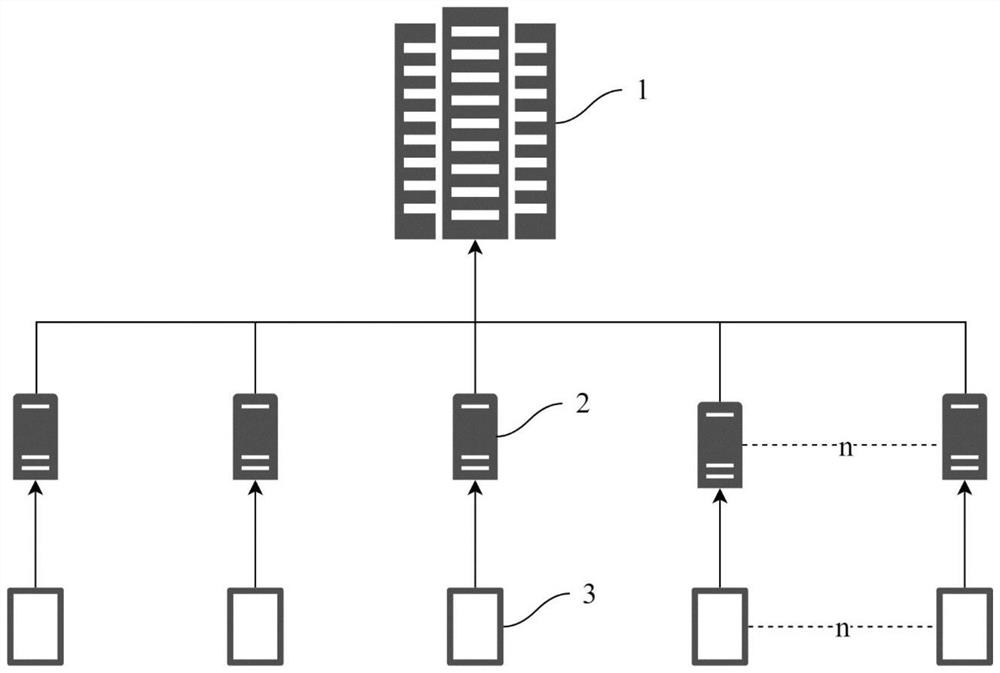
[0051] It is worth noting that the receiving end of the server is the server 1 arranged in the supervision center, and the sending end of the user is the industrial computer 2 arranged on the road. Each industrial computer 2 is equipped with an exhaust remote sensing monitoring device, which is used for monitoring The tail gas pollutant content of motor vehicles running on the road can be uploaded to the industrial control computer 2 in real time.
[0052] In addition, how many industrial computers 2 are connected to one server 1 through the bus depends on the actual situation, and no further limitation is made here.
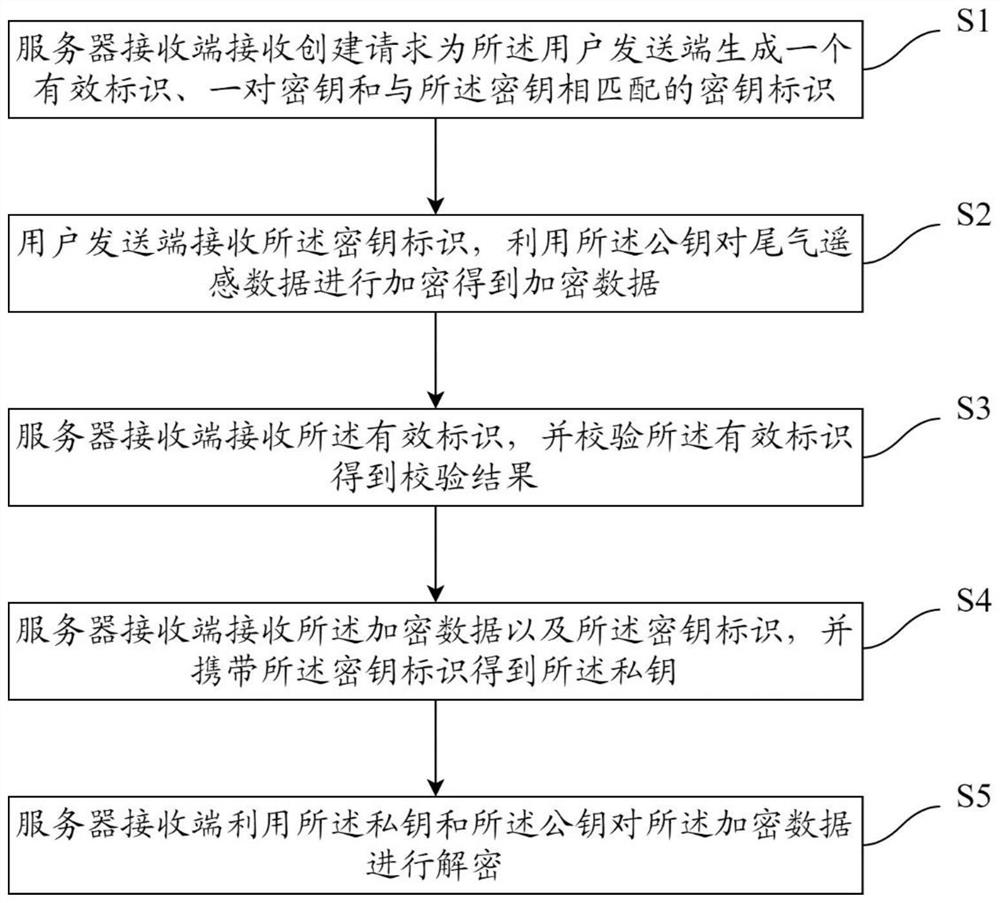
[0053] Refer to attached Figure 1~2 As shown, the present invention provides a technical solution: a method for uploading and encrypting tail gas remote sensing data, comprising the following steps:
[0054] S1, the receiving end of the server receives the creation request and generates a valid identification, a pair of keys and a key identification matching the...
Embodiment 2
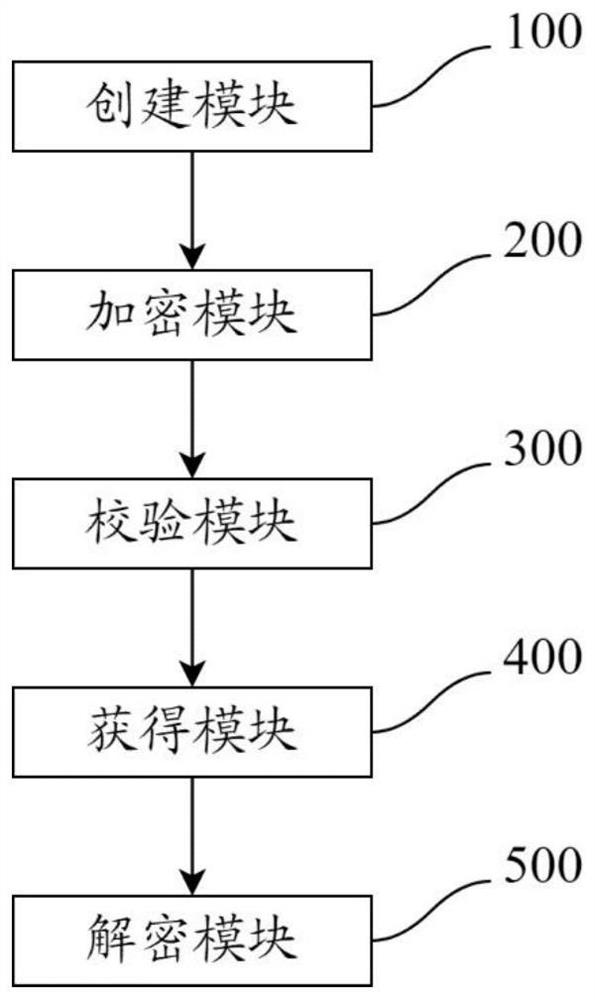
[0071] The embodiment of the present invention also discloses a system for uploading and encrypting tail gas remote sensing data. figure 1 and 3 shown, including:
[0072] The creation module 100 is used for the receiving end of the server to receive the creation request and generate a valid identification, a pair of keys, and a key identification matching the key for the user sending end; wherein, the pair of keys includes a public key and private key;
[0073] The encryption module 200 is used for the user sending end to receive the key identification, and utilize the public key to encrypt the tail gas remote sensing data to obtain encrypted data;
[0074] Checking module 300, is used for server receiving end to receive described valid identification, and checks described valid identification to obtain verification result;
[0075] Obtaining module 400, used for the server receiving end to receive the encrypted data and the key identification, and carry the key identifica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com