Seed optimization method based on vulnerability prediction model
A predictive model and optimization method technology, applied in the field of network security, to achieve the effect of improving effectiveness and easy to find vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
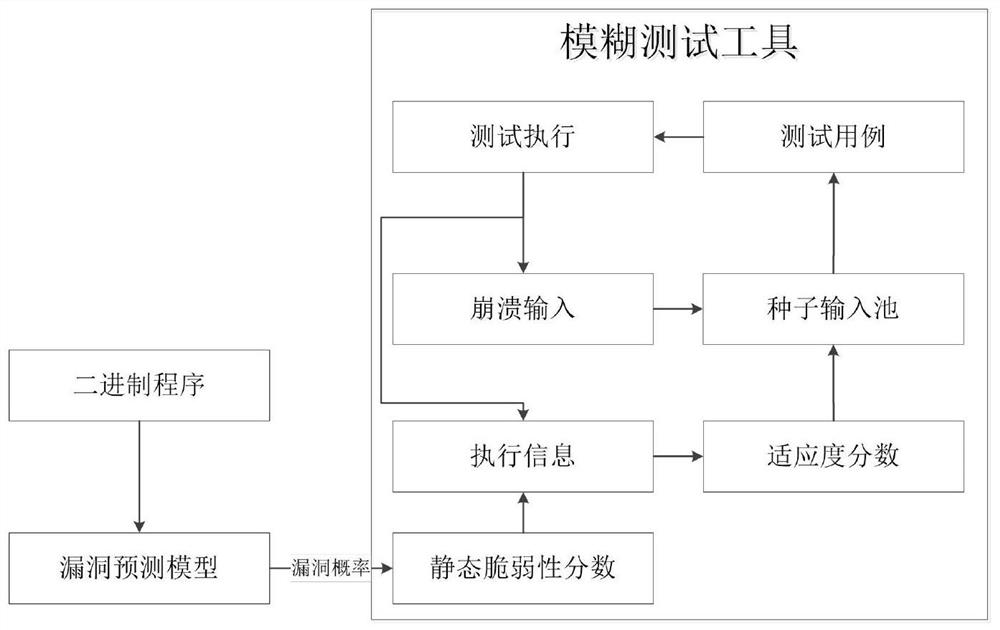
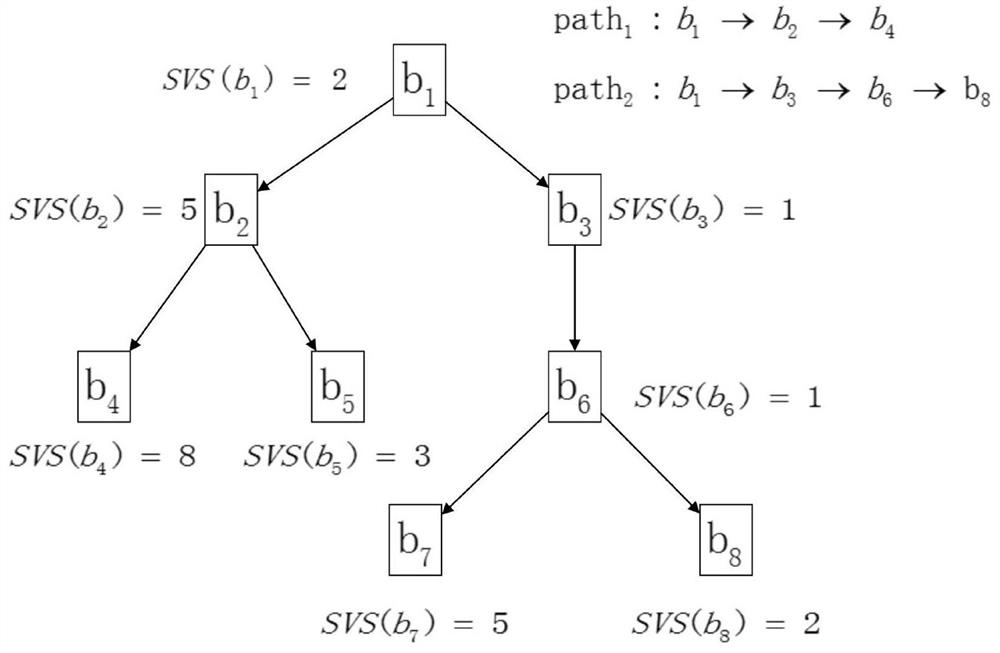
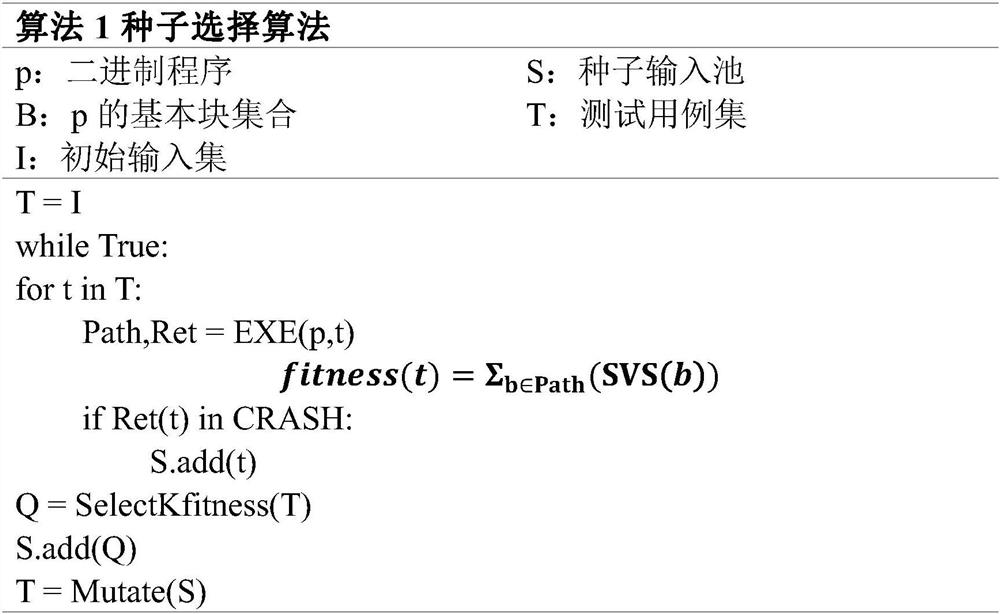
[0019] In order to better understand the contents of the present invention, an example is given here. figure 1 It is the implementation flowchart of the method of the present invention; figure 2 It is an example diagram of fitness calculation in the present invention.
[0020] The present invention is aimed at the shortcomings of a large number of redundant calculations in Libfuzzer and AFL, and proposes a set of fuzzing technology solutions based on the vulnerability prediction model. It is a tool to test the vulnerability probability of functions in the target code, guide the direction of fuzz test seed optimization based on the vulnerability probability, and design more test cases for functions with higher vulnerability probability to trigger more vulnerabilities.
[0021] Fuzz testing is a cyclic process. For the part of test case generation, the fuzz testing tool will maintain a seed input pool to save the input that is more likely to cause a crash.
[0022] The invent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com