Method and system for identifying illegal access equipment in wireless local area network
A wireless local area network and wireless local area technology, applied in the information field of the Internet of Things, can solve the problems of potential safety hazards, the update speed of the feature database is not as fast as that of new equipment, and equipment identification can no longer meet the needs, so as to achieve the effect of ensuring accurate identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
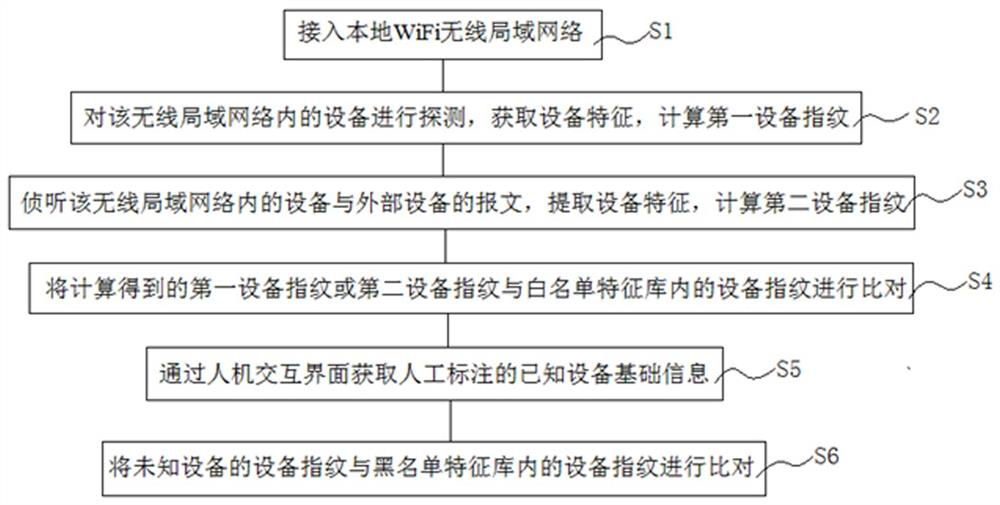
[0034] Reference attached figure 1 , the first embodiment of the present invention is a method for identifying illegal access devices in a wireless local area network, comprising the following steps:
[0035] The first step is to access the local WiFi wireless local area network.
[0036] Usually, multiple smart / IoT devices are connected to a WiFi network. By accessing the WiFi network, other devices in the WiFi network can send messages for information exchange.
[0037] In the second step, the devices in the wireless local area network are detected to obtain device characteristics, and a first device fingerprint corresponding to the devices is calculated based on the obtained device characteristics.
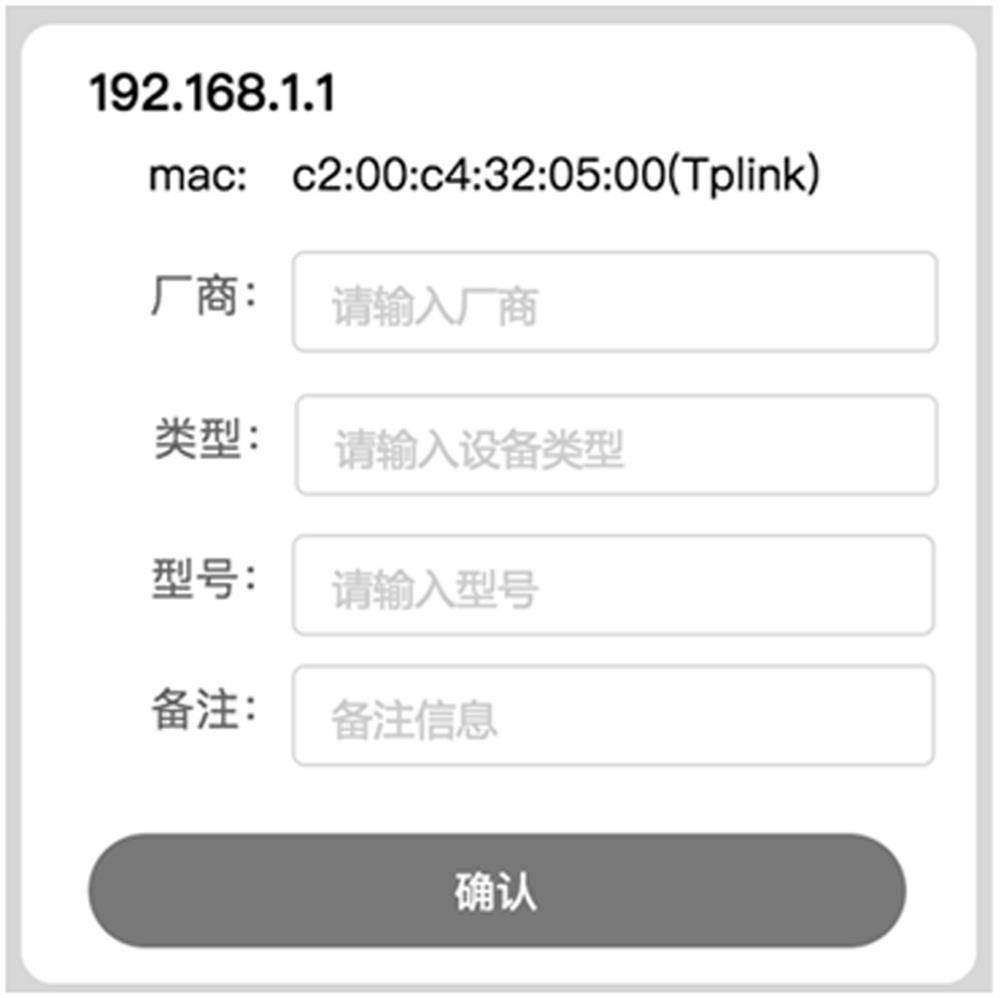
[0038] As a preferred implementation, in this embodiment, the specific detection methods are:
[0039] Send multiple preset types of messages to the device first, then receive the device response message, and extract the preset field value in the response message as the devic...
Embodiment 2
[0074] The second embodiment of the present invention is a system for identifying illegal access devices in a wireless local area network, including: configured on a mobile terminal:
[0075] Wifi module, used to access WiFi wireless local area network;
[0076] The first detection module is configured to detect devices in the wireless local area network one by one, obtain device characteristics, and calculate a first device fingerprint corresponding to the device based on the obtained device characteristics;
[0077] The second detection module is used to listen to the request / response data sent by the device in the wireless local area network to the device outside the local area network, or to listen to the request / response message sent by the device outside the local area network to the device in the wireless local area network, from which extracting preset field values as device features, and calculating a second device fingerprint based on the extracted device features;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com