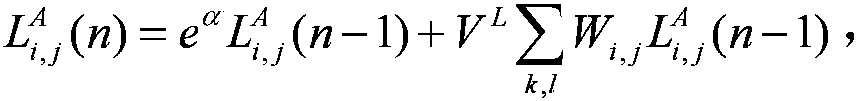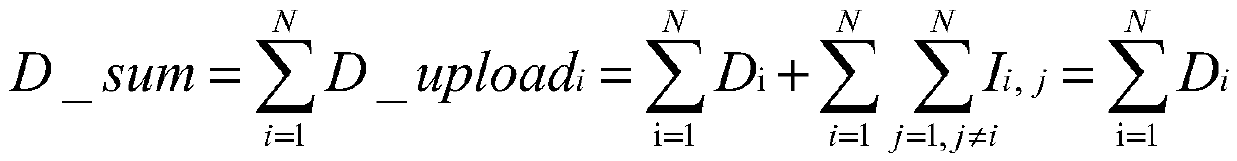Patents
Literature
33results about How to "Privacy is not leaked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
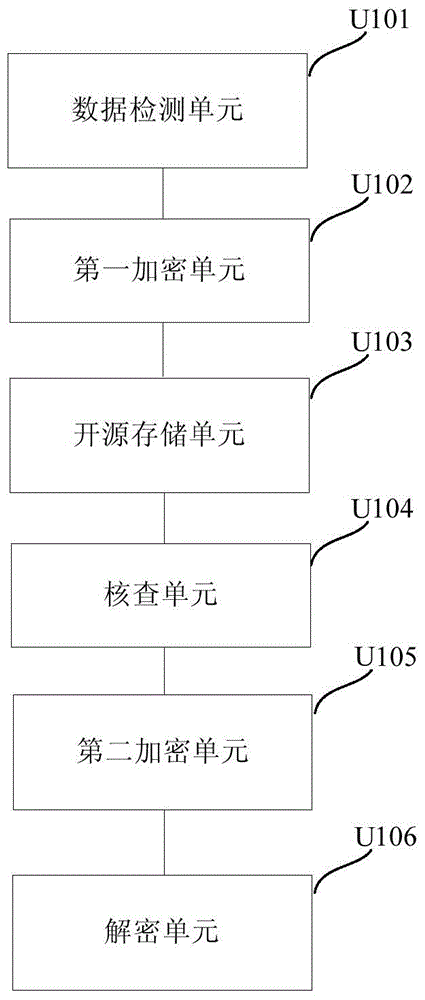
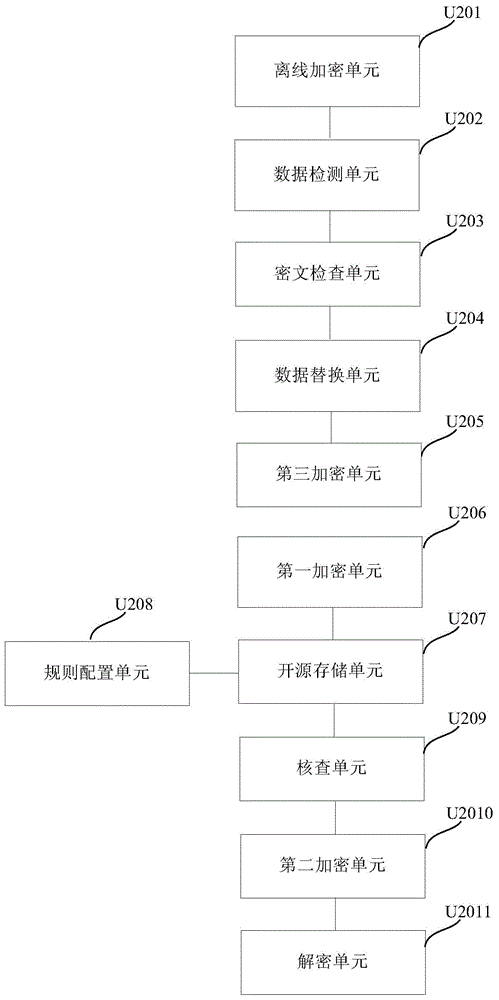
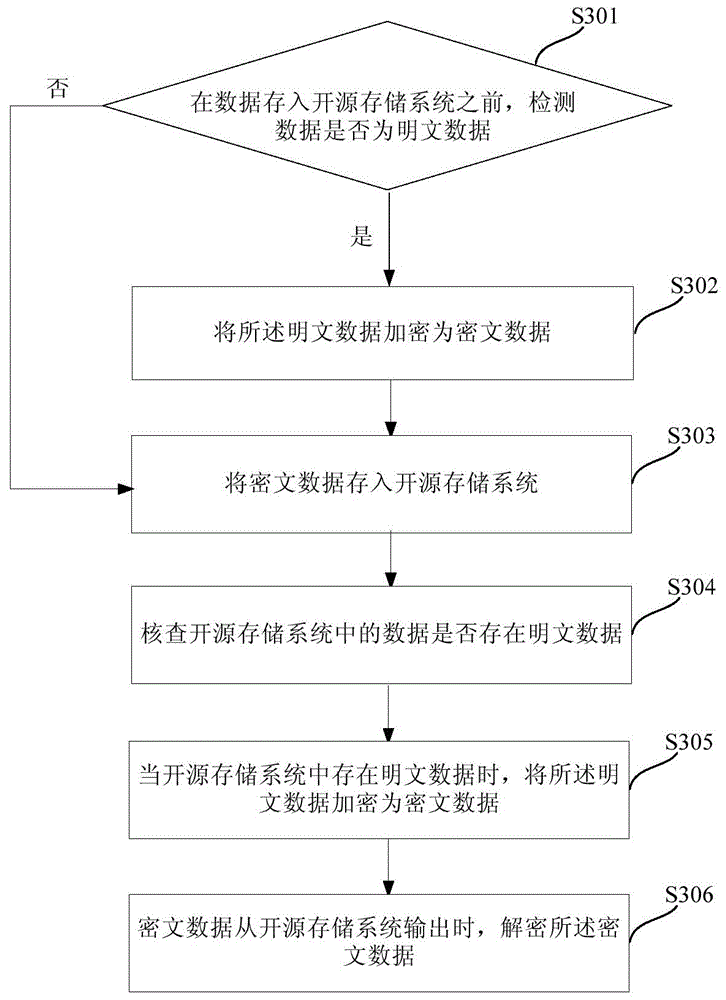
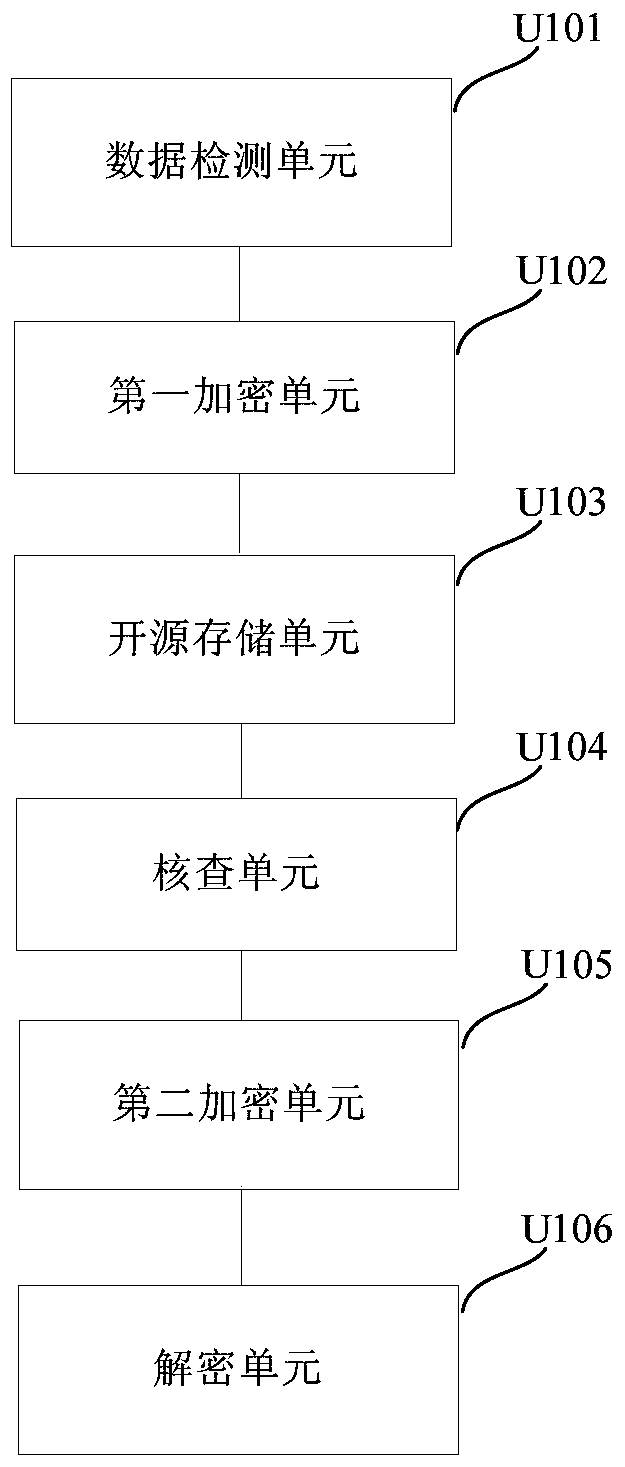
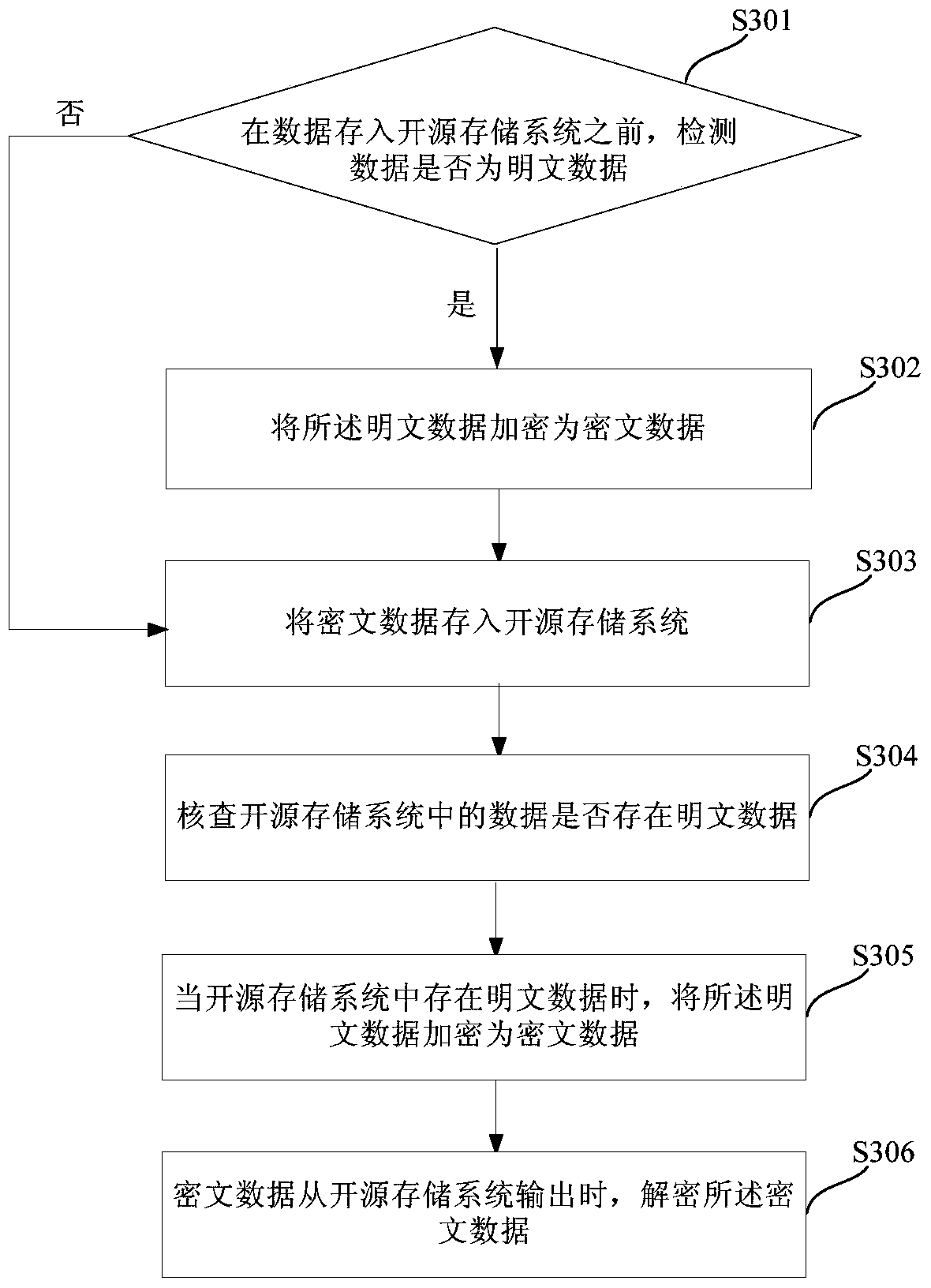
Big data encryption and decryption processing method and system
ActiveCN105574424AEnsure safetyDoes not affect normal displayDigital data protectionPlaintextCiphertext
The embodiment of the invention discloses a big data encryption and decryption processing method and system. The method comprises following steps: before data are stored in an open source storage system, detecting whether the data are plaintext data; if the data are plaintext data, encrypting the data into ciphertext data; storing the ciphertext data in the open source storage system; verifying whether there are plaintext data in the open source storage system; when there are plaintext data in the open source storage system, encrypting the plaintext data into ciphertext data; and when outputting the ciphertext data from the open source storage system, descrypting the ciphertext data. According to the method and the system of the invention, the data stored in the open source storage system are encrypted; the data are decrypted and recovered when outputting the data; and therefore, the data security is ensured and the privacy of the user is not leaked on the basis of not influencing the normal display and processing of the data.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD +1
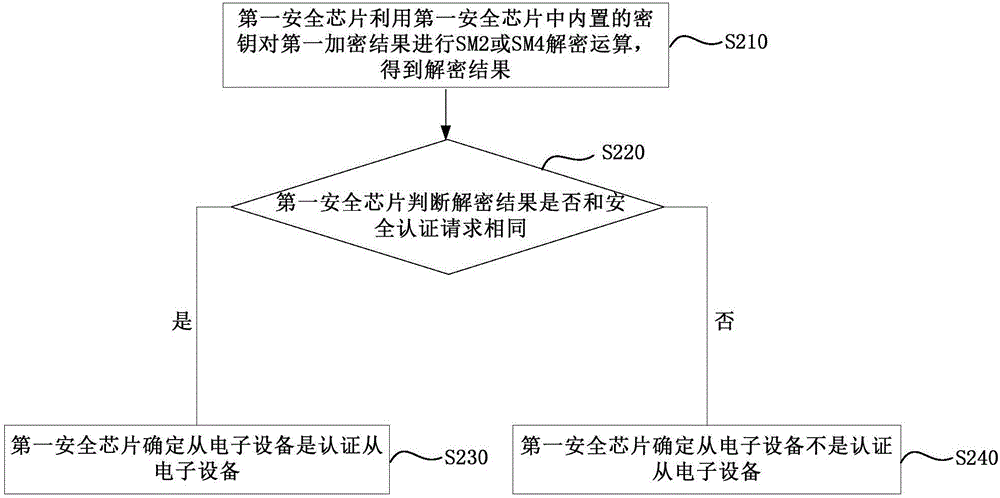
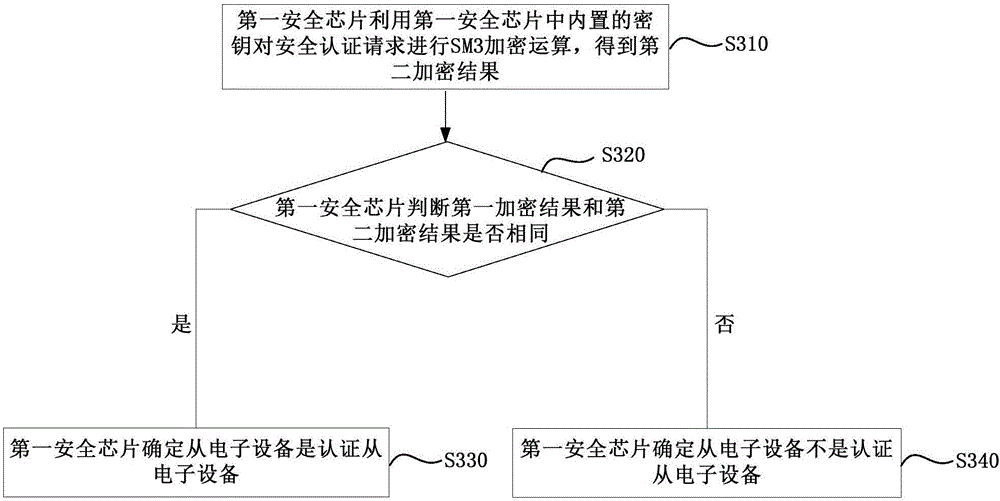
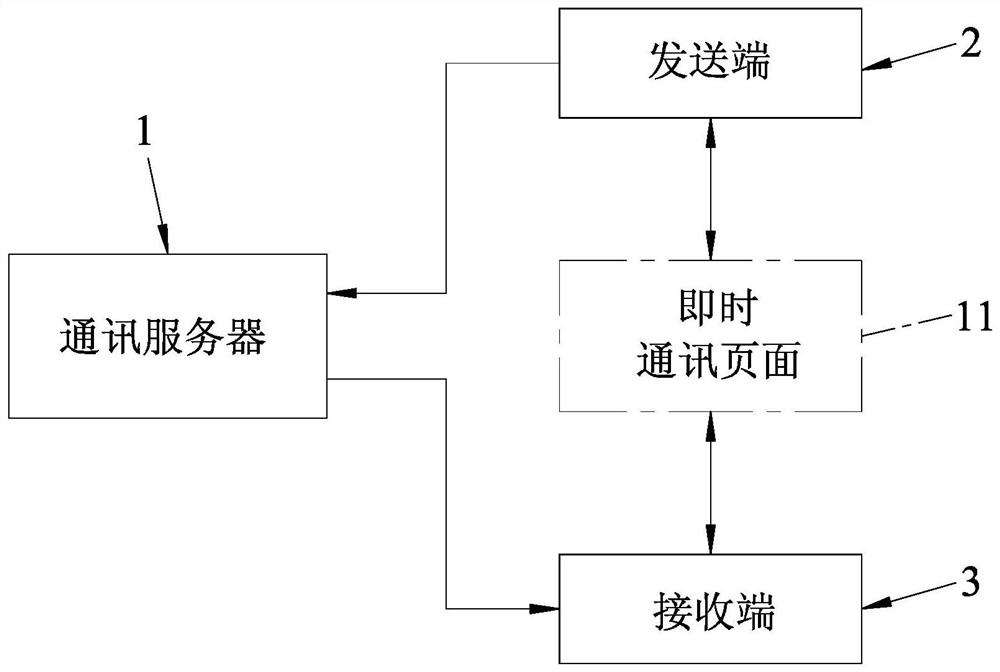
Security authentication method, master electronic device and slave electronic device
InactiveCN106330455AImprove securityEasy to useKey distribution for secure communicationPublic key for secure communicationUser privacySecurity authentication
The invention discloses a security authentication method, a master electronic device and a slave electronic device. The master electronic device comprises a master control chip and a security chip, and is in communication connection with the slave electronic device. The security authentication method comprises the following steps: the security chip receives a request generation instruction sent by the master control chip; the security chip generates a security authentication request comprising a group of random numbers; the security chip sends the security authentication request to the master control chip, so that the master control chip sends the security authentication request to the slave electronic device; when the security chip receives a first encryption result sent by the master control chip, the security chip judges whether the slave electronic device is an authenticated slave electronic device according to the first encryption result, the security authentication request and a built-in key in the security chip; and if so, the security chip sends an authentication pass instruction to the master control chip, so that the master control chip provides services for the slave electronic device. The scheme can avoid the influence of the use of the slave electronic device to the service life and the secure use of the master electronic device, and protect the user privacy from being leaked.
Owner:BEIJING HUADA INFOSEC TECH
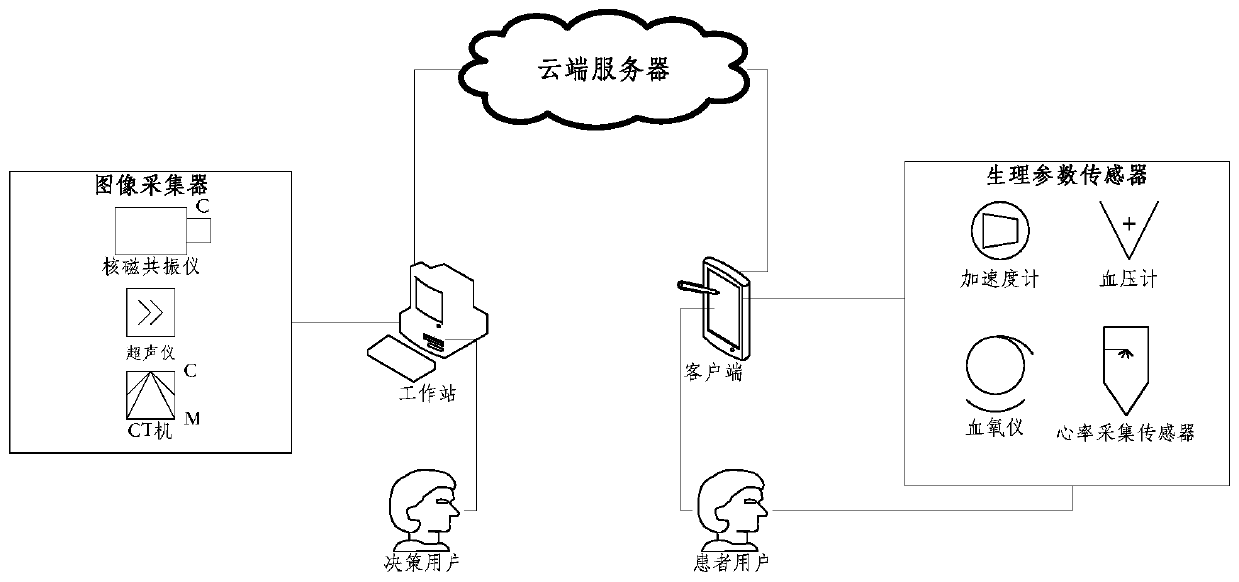
Comprehensive medical system capable of performing diagnosis monitoring in similarity matching manner and matching method of comprehensive medical system
ActiveCN110584605AReduce labor intensityReal-time monitoring statusUltrasonic/sonic/infrasonic diagnosticsEvaluation of blood vesselsPerformed DiagnosisLaboratory test
The invention relates to a comprehensive medical system capable of performing diagnosis monitoring through a similarity matching manner. The comprehensive medical system comprises a client, a workstation, a cloud server, an image collecting device and a physiological parameter sensor, wherein a patient user uploads essential information of the patient user through the client to the cloud server; adecision user uploads case general information, main symptoms and physical signs of the patient user, result of laboratory test, pathological information, the fundamental judgment of the illness state of the patient user, treatment means, postoperative symptoms, nursing suggestions and strategies to the cloud server through the workstation; a diagnosis and treatment case database is stored in thecloud server, and the cloud server is used for integrating all kinds of uploaded information to form cases; and the decision user performs retrieve on the diagnosis and treatment case database through the workstation, and finds out the most similar case in the diagnosis and treatment case database according to similarity matching.
Owner:SUZHOU HENSUN INFORMATION TECH CO LTD
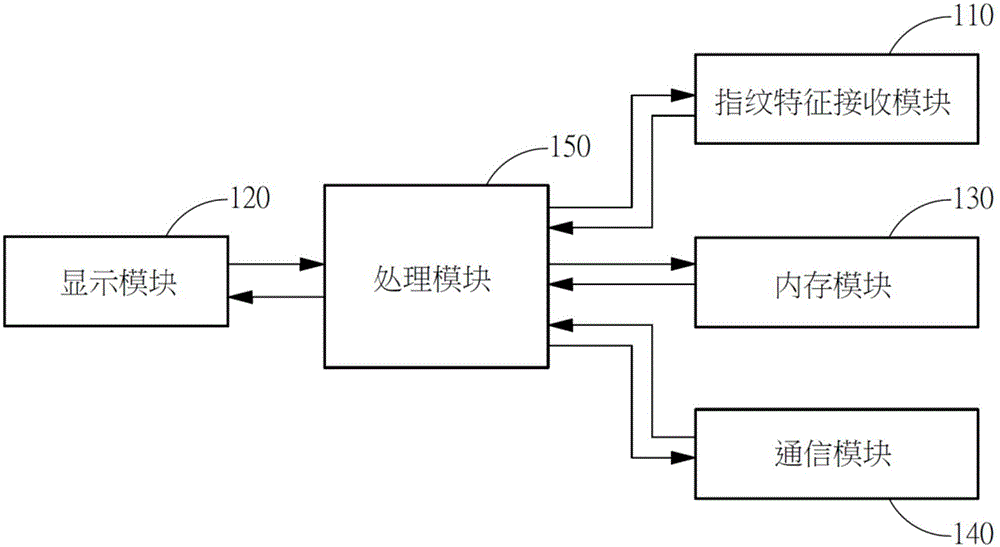
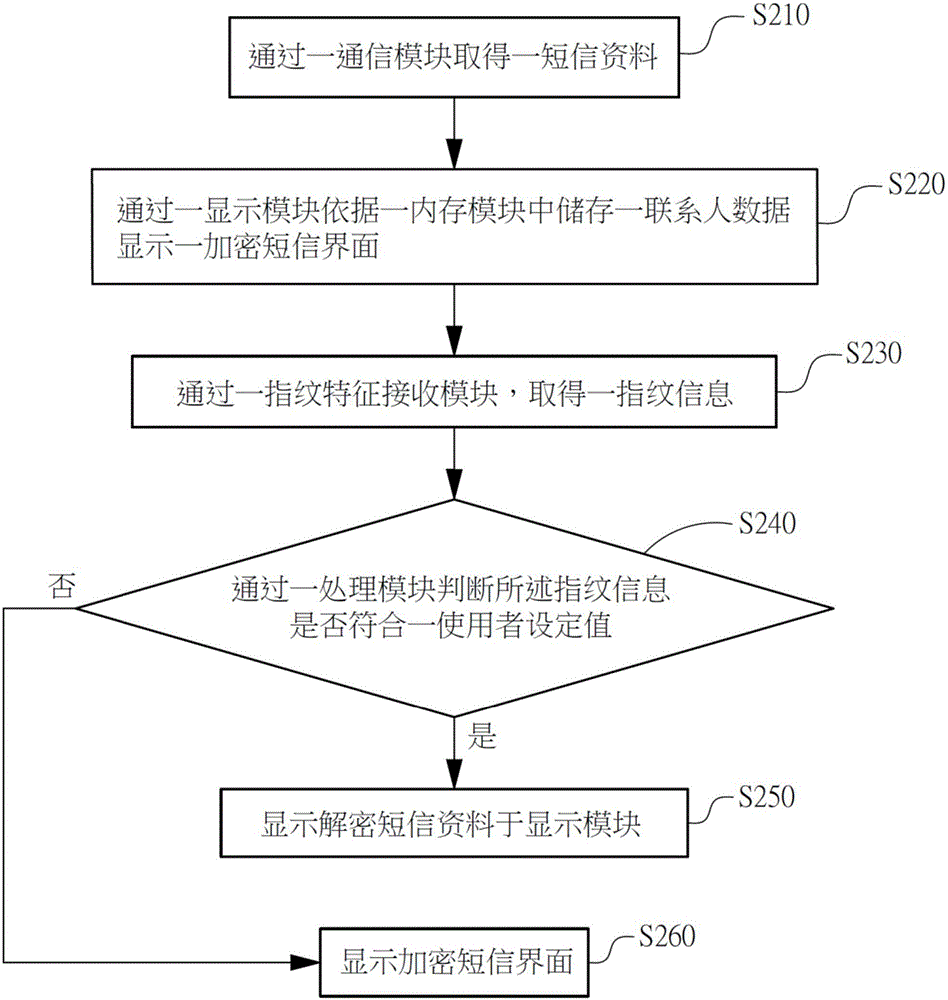
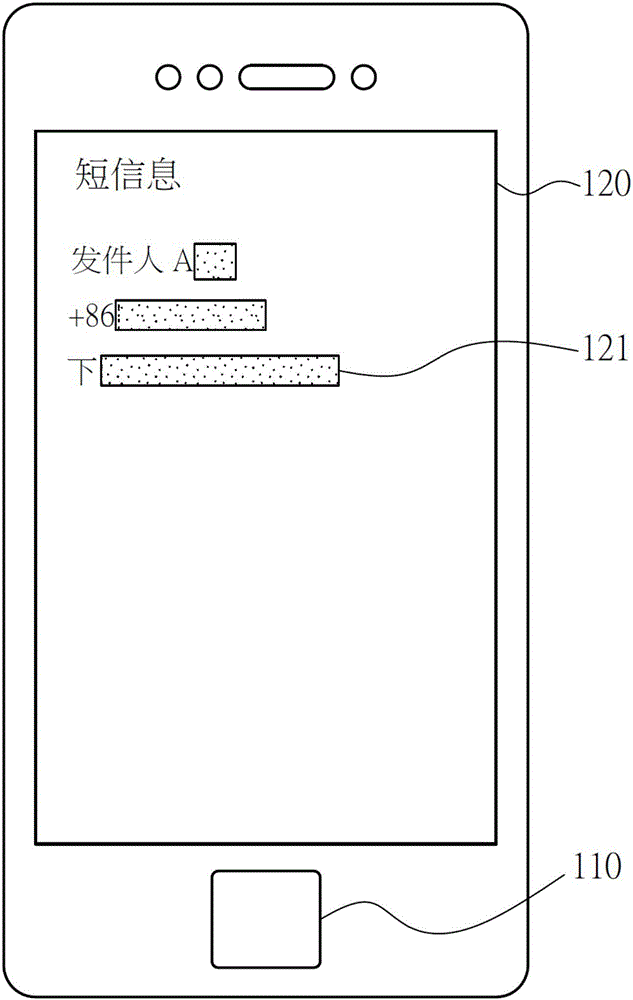
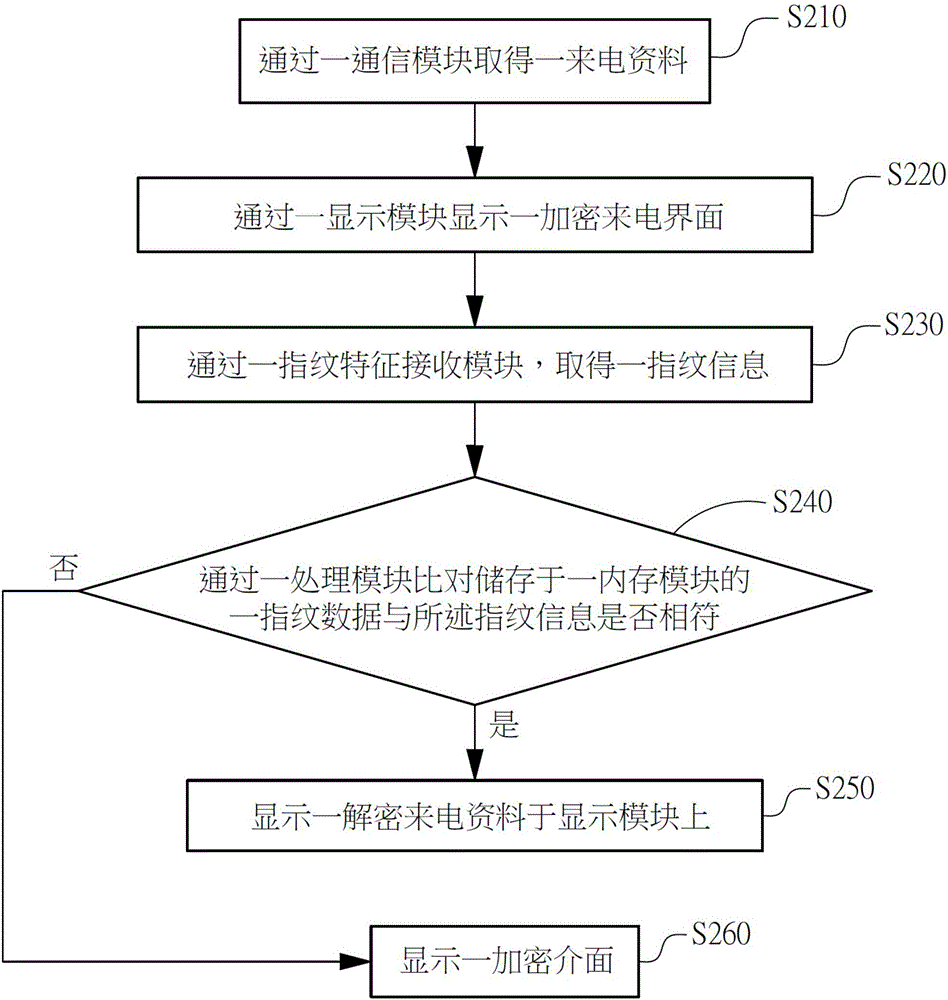
Method and system for rapidly decrypting and identifying protected short message through fingerprint verification manner
InactiveCN106228053AAvoid the dilemma of not being able to identify sensitive contactsPrivacy is not leakedDigital data protectionDigital data authenticationComputer moduleData storing
The invention relates to a method and system for rapidly decrypting and identifying a protected short message through a fingerprint verification manner. The method is characterized by comprising the following steps: obtaining short message information through a communication module and displaying an encrypted short message interface through a display module; obtaining fingerprint information through a fingerprint feature receiving module; and comparing whether fingerprint data stored in a memory module accords with the fingerprint or not through a processing module, and displaying decrypted short message data on the display module.
Owner:SHENZHEN TINNO WIRELESS TECH
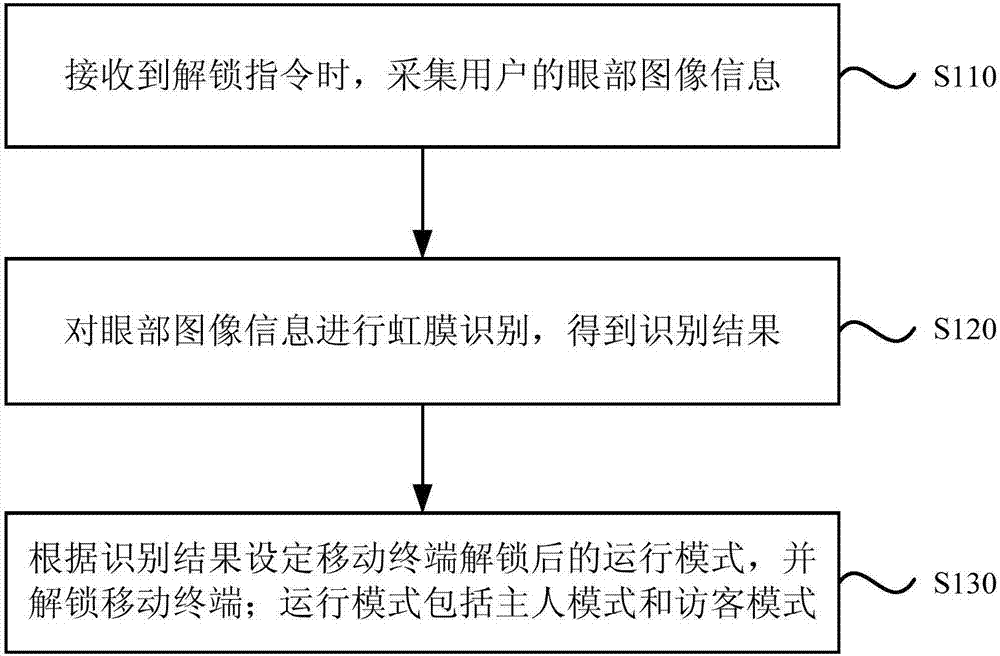
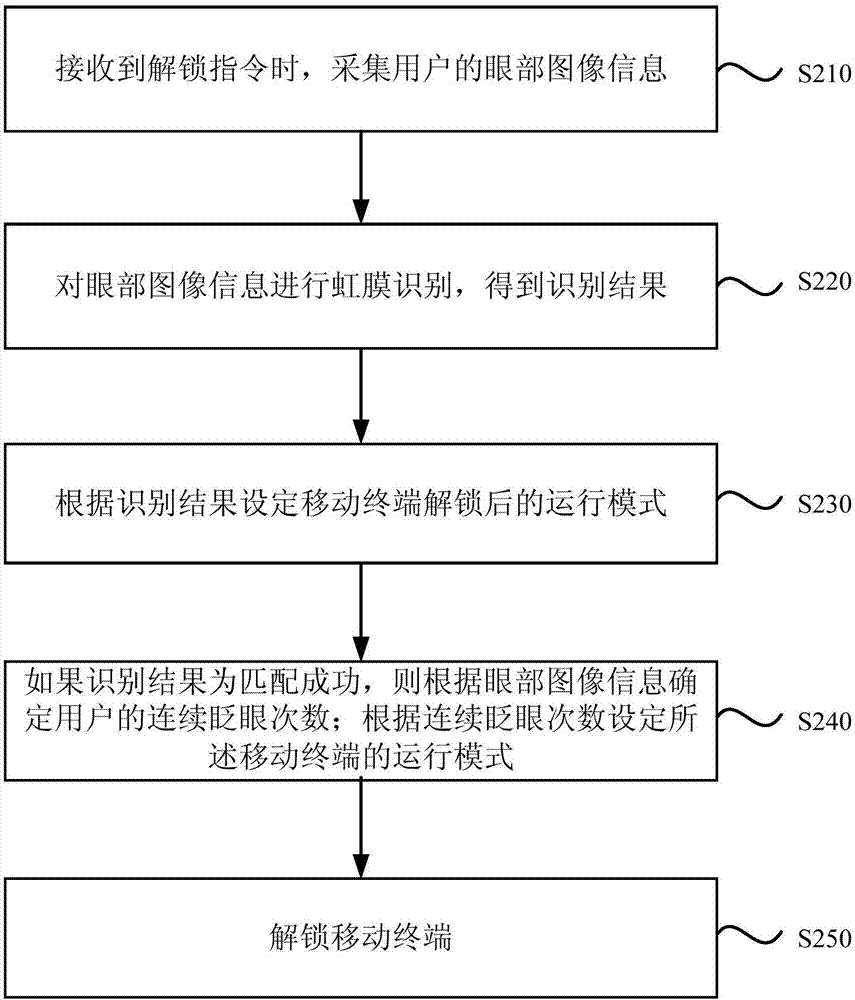
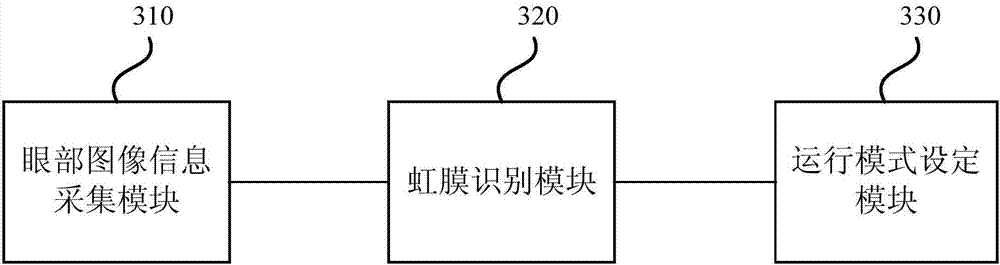
Unlocking method, device and equipment for mobile terminal, and storage medium
InactiveCN107273732ASolve the problem of low privacy securityPrivacy is not leakedDigital data authenticationTerminal equipmentComputer terminal
The embodiment of the invention discloses a mode switching method, a mode switching device and mode switching equipment based on iris recognition, and a storage medium. The method comprises the steps of collecting eye image information of a user when an unlocking command is received; performing iris recognition on the eye image information to acquire a recognition result; setting a running mode of the mobile terminal after unlocking according to a recognition result, and unlocking the mobile terminal, wherein the running modes comprise a master mode and a visitor mode. According to the method, device and equipment provided by the invention, iris recognition is performed on the eye image information to acquire the recognition result; the running mode of the mobile terminal after unlocking is set according to the recognition result, and the mobile terminal is unlocked, so that the problem that the current terminal equipment has low privacy security is solved, information with different privacy is displayed under different modes, and thus the condition that privacy of the owner is not leaked is ensured.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
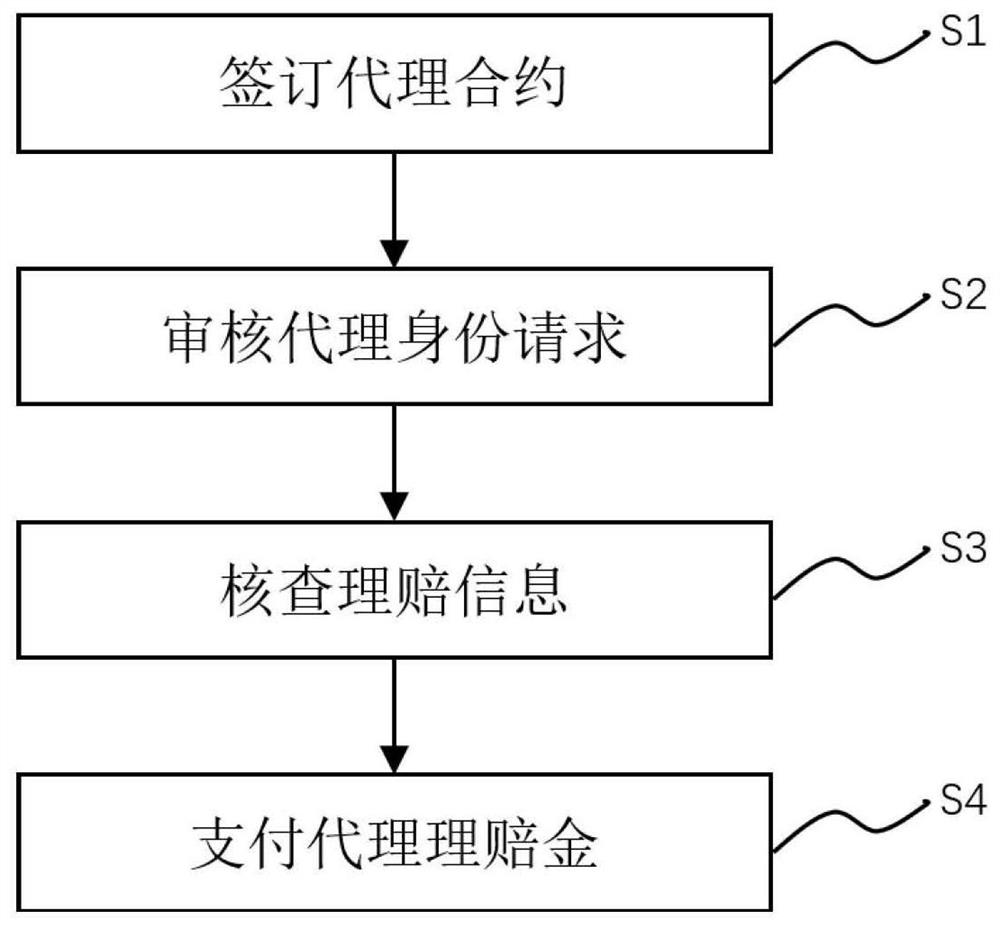
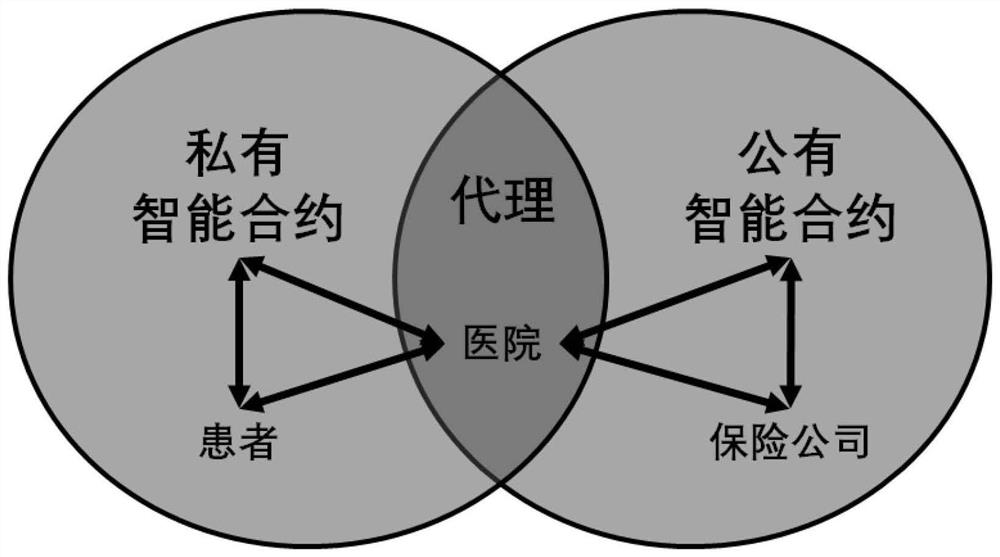
Insurance claim settlement device and method based on hybrid smart contract
ActiveCN113469827APrivacy is not leakedEasy to operateFinancePayment circuitsSmart contractComputer science
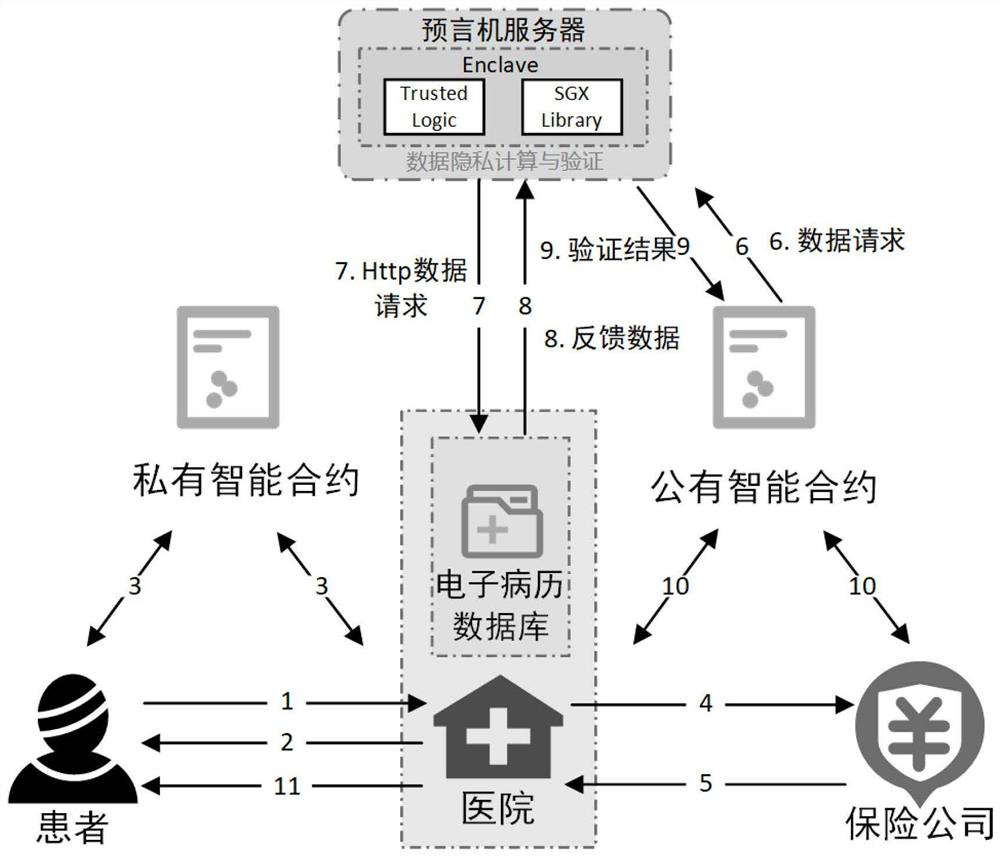
The invention discloses an insurance claim settlement device and method based on a hybrid smart contract. The method comprises the steps: signing an agency contract based on a symmetric encryption scheme, and entrusting a hospital agent to execute medical insurance claim settlement; carrying out proxy auditing through an identity authentication method based on the off-chain zero-knowledge proof generation tool Zokrates and providing the identity proof for privacy security; checking the claim settlement information based on a block chain oracle machine verification method, and assisting the smart contract to verify the real claim settlement amount; and carrying out payment of the claim settlement amount under the automatic control of the public and private smart contract to finish automatic claim payment of the patient. Therefore, the operation process of the patient is simplified, the claim settlement efficiency of an insurance company is remarkably improved, and the privacy of the patient is protected from being leaked.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Information processing method and device and storage medium
InactiveCN110610452APrivacy is not leakedGeometric image transformationCharacter and pattern recognitionInformation processingComputer graphics (images)
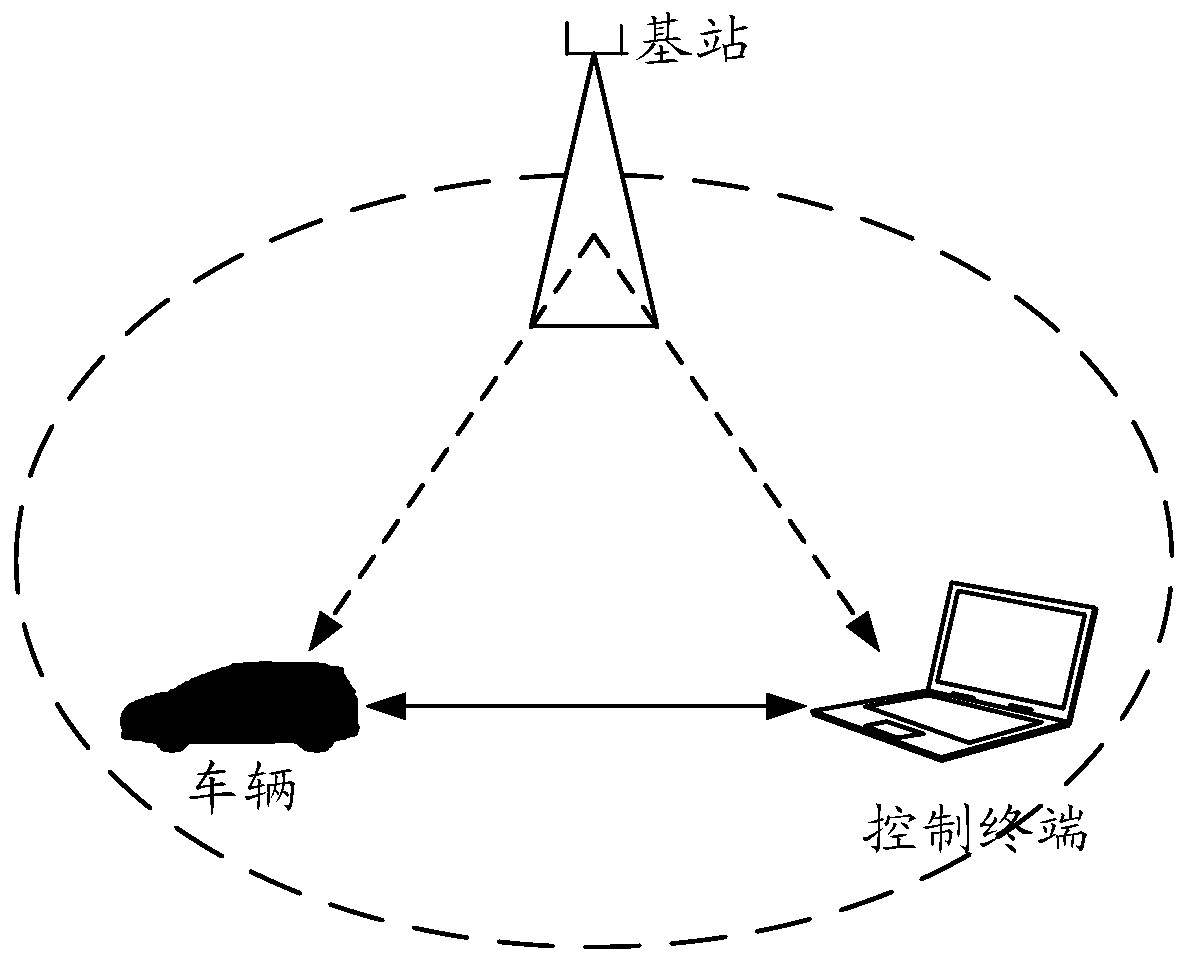
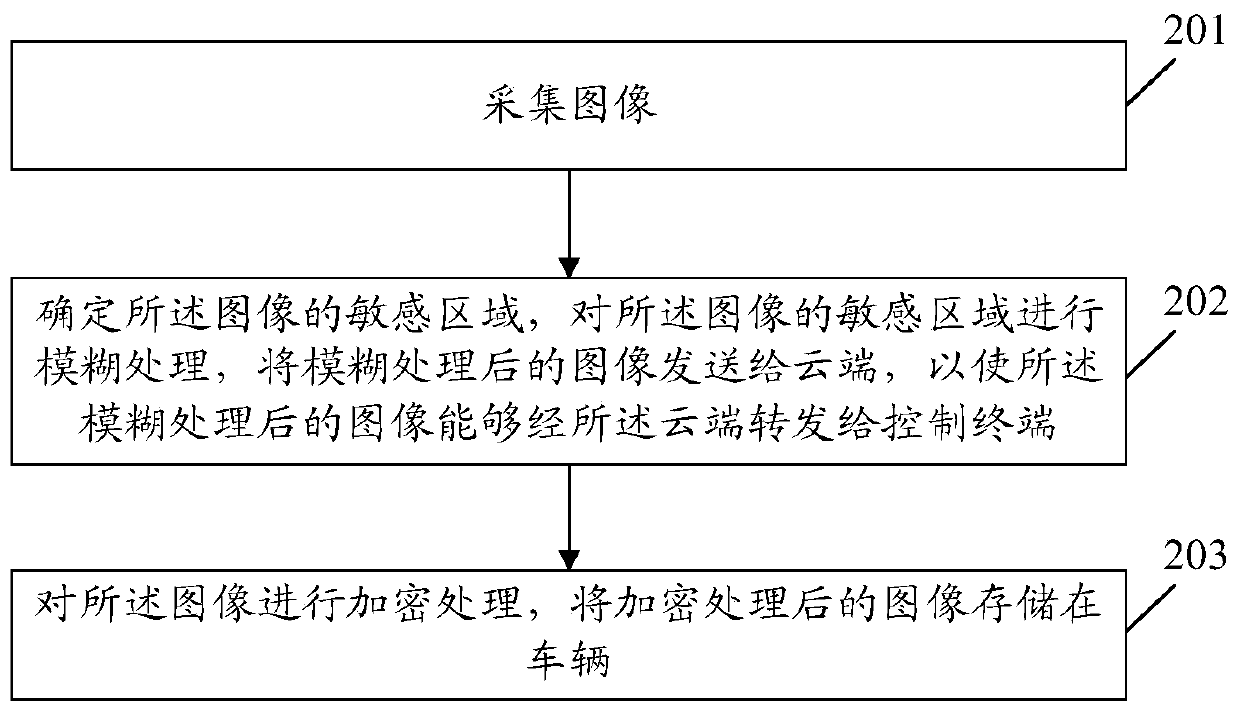
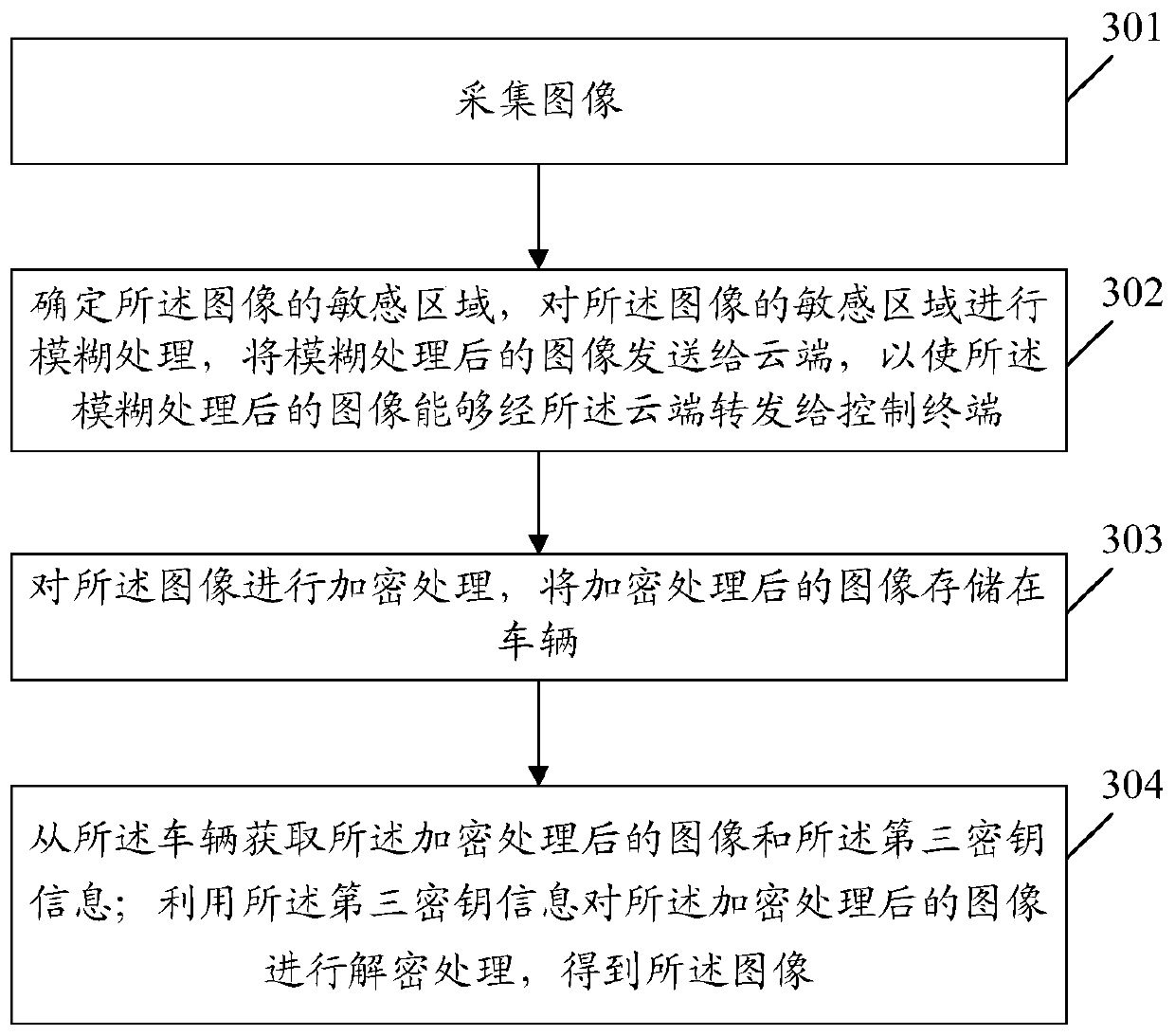
The embodiment of the invention provides an information processing method and device and a storage medium. The method comprises the steps that an image is collected; determining a sensitive area of the image, performing fuzzy processing on the sensitive area of the image, and sending the image subjected to fuzzy processing to a cloud end, so that the image subjected to fuzzy processing can be forwarded to a control terminal through the cloud end; and the image is encrypted, and the encrypted image is stored in the vehicle. By performing fuzzy processing and encryption processing on the image,the privacy of the image can be protected from being leaked on the premise of not influencing remote control or monitoring normal operation of the vehicle.
Owner:NINEBOT (CHANGZHOU) TECHCO LTD
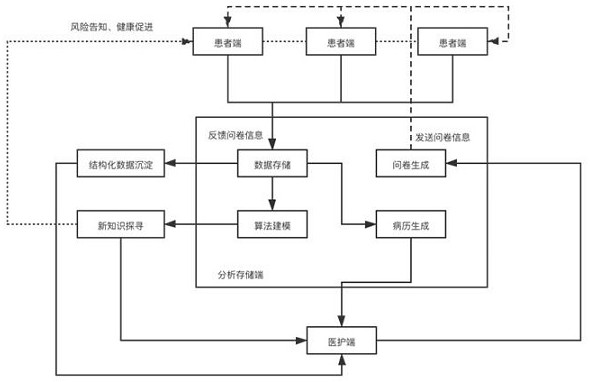
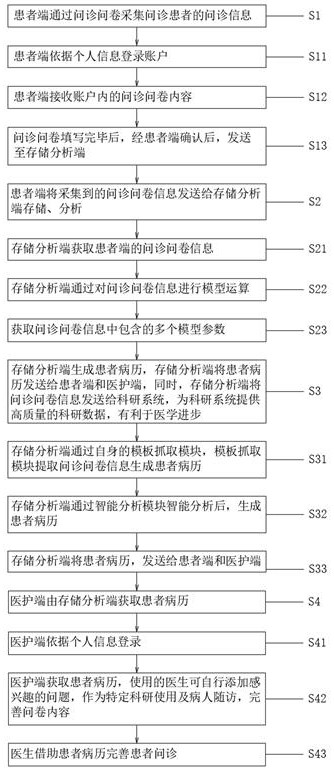
Inquiry information acquisition and analysis system and method
PendingCN112133385APromote medical awarenessSimplify the consultation processMathematical modelsHealth-index calculationMedical recordMedical knowledge
The invention provides an inquiry information collection and analysis system and method. The system comprises a patient terminal, a storage and analysis terminal, and a medical care terminal, the patient terminal is provided with a questionnaire, and the questionnaire is sent to the storage and analysis terminal after an inquiry patient fills in the questionnaire. The storage analysis terminal generates patient medical records by using the questionnaire information and feeds back the patient medical records to the patient terminal and the medical care terminal, and the medical care terminal receives the patient medical records of the storage analysis terminal and assists in completing patient inquiry. Structured data deposited at the storage and analysis end can be used as scientific research materials, analysis is conducted through artificial intelligence and other methods, and new medical knowledge is explored. Information is collected in a questionnaire survey mode, machine learningand artificial intelligence are introduced into processing of a corresponding database of a patient, a corresponding analysis model and algorithm are constructed, various indexes and conditions of the patient in the database are comprehensively processed through different dimensions, so materials are quickly collected, information is stored, medical records are generated, results are analyzed, new knowledge is explored, and various risks are prompted.
Owner:黄军彩
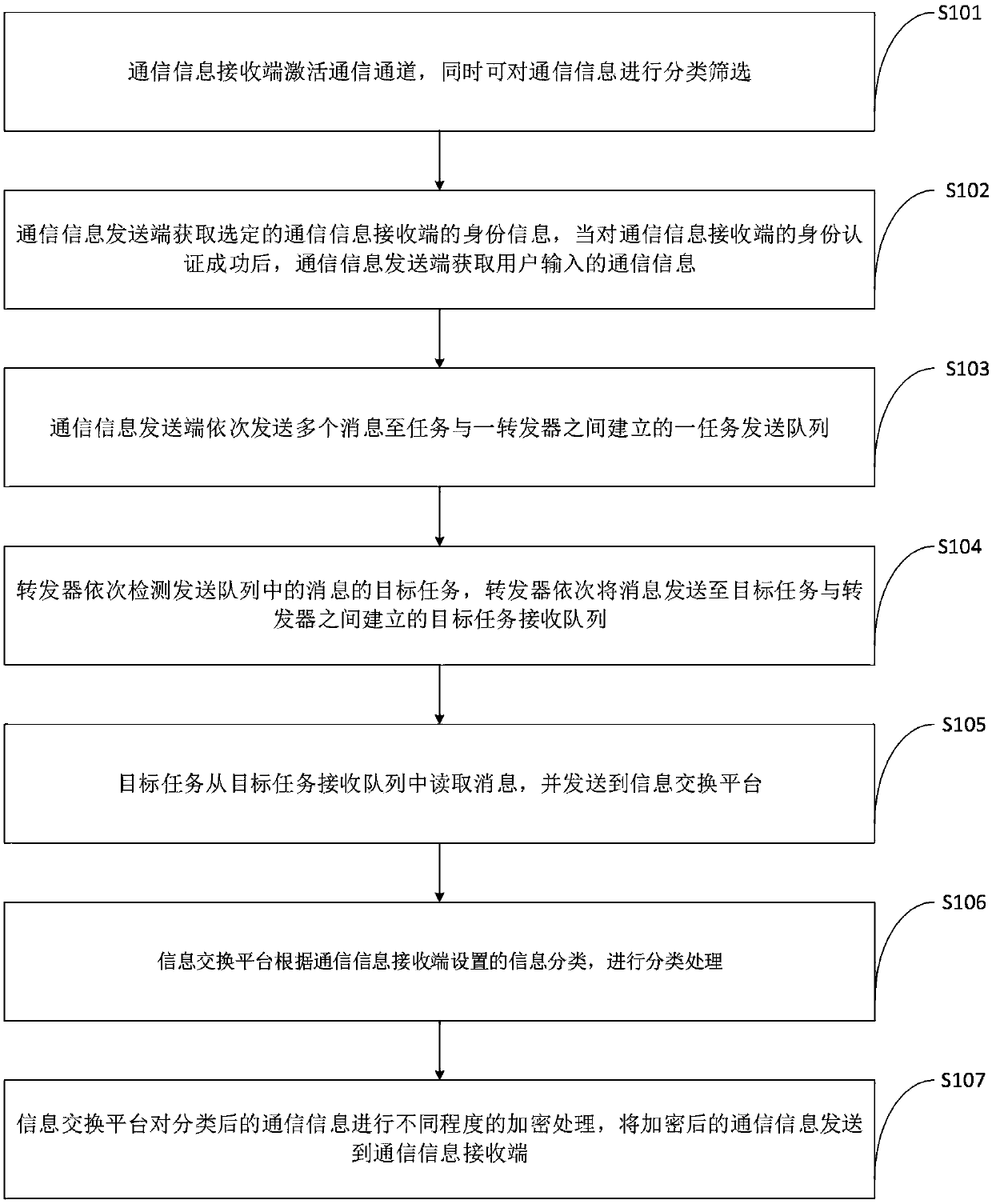
Efficient communication information processing method
The invention belongs to the technical field of communication, and discloses an efficient communication information processing method. A communication channel is activated through a communication information receiving end, and meanwhile, communication information can be subjected to classified sifting; identity information of the communication information receiving end is obtained and utilized toconduct identity authentication on the communication information receiving end, then the communication information is encrypted and sent to the communication information receiving end so that only thecommunication information which is subjected to identity authentication can obtain the communication information; besides, the communication information is not easily obtained by any third party, theobtained communication information is encrypted, the privacy of the communication information can be well protected, and the safety is improved. In the meanwhile, by means of the efficient communication information processing method, transmission of messages among different tasks is achieved through the combination of a transponder and a queue, the mode of messages in the queue is changed throughcontrol over attributes of the transmission queue, and the using range of the communication method can further be expanded.
Owner:HUBEI NORMAL UNIV
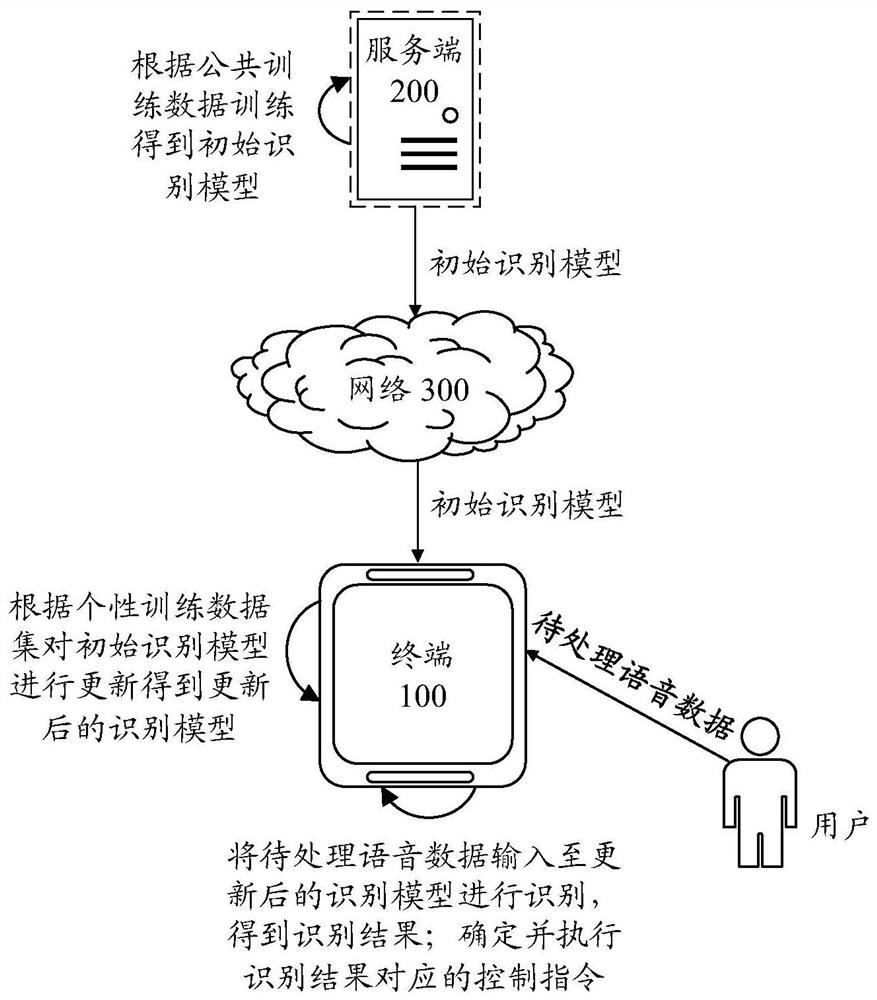
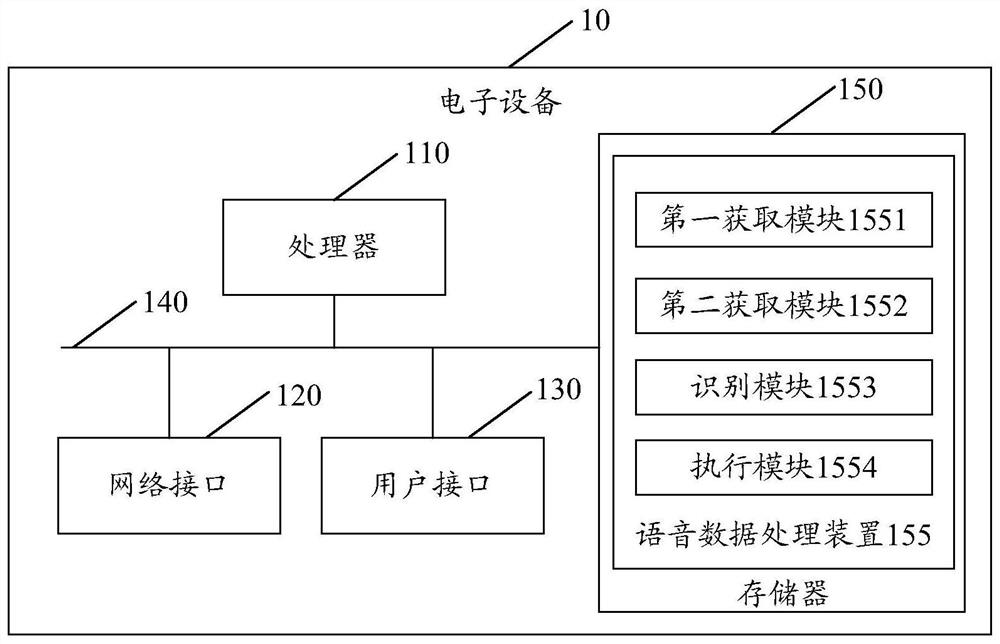
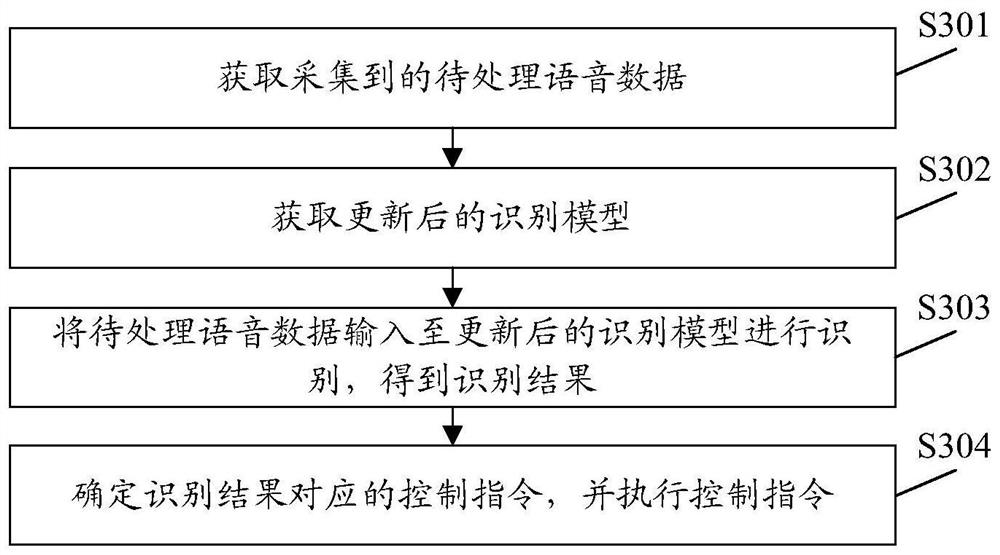
Voice data processing method and device, equipment, storage medium and program product
PendingCN113744739AImprove recognition accuracyPrivacy is not leakedSpeech recognitionPersonalizationData set
The invention provides a voice data processing method and device, equipment, a storage medium and a program product. The method comprises the steps of obtaining collected to-be-processed voice data; obtaining an updated recognition model, wherein the updated recognition model is obtained by updating an initial recognition model by a terminal according to a personalized training data set, the initial recognition model is obtained by training through a server terminal based on public training data, and the personalized training data set at least comprises the collected voice data; inputting the to-be-processed voice data into the updated recognition model for recognition to obtain a recognition result; and determining a control instruction corresponding to the recognition result, and executing the control instruction. According to the invention, on the premise of ensuring that the user voice data is not out of the local and ensuring that the user privacy is not leaked, personalized voice recognition service with high recognition accuracy is realized.
Owner:WEBANK (CHINA)
Method and system for identifying illegal access equipment in wireless local area network
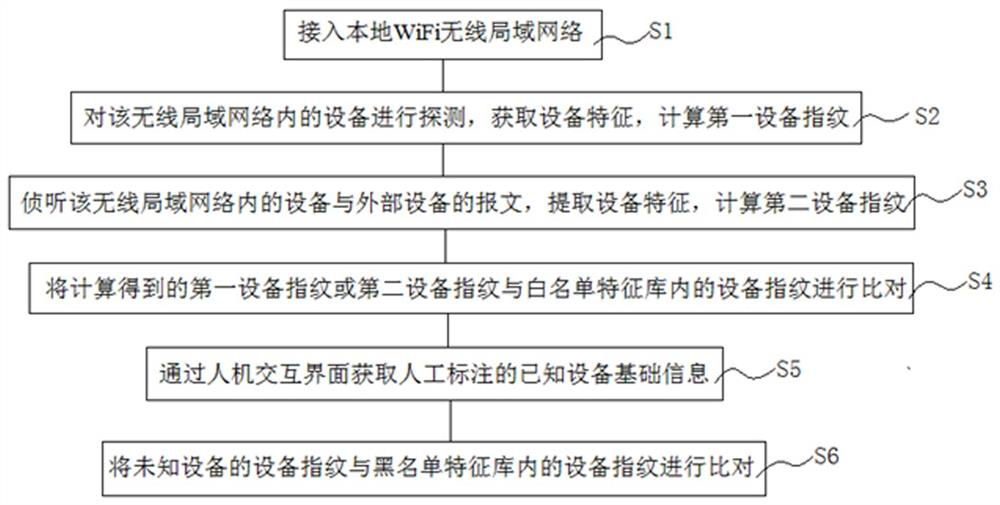
ActiveCN114143783AEfficient identificationPrivacy is not leakedSecurity arrangementHigh level techniquesEngineeringWireless lan
The invention provides a method for identifying illegal access equipment in a wireless local area network. The method comprises the following steps: accessing a local WiFi wireless local area network; equipment in the wireless local area network is detected, equipment characteristics are obtained, and a first equipment fingerprint is calculated; monitoring a request / response message of local area network external equipment in the wireless local area network, extracting equipment characteristics, and calculating a second equipment fingerprint; comparing the calculated first / second device fingerprint with the device fingerprint in the white list feature library, and if the device fingerprint corresponding to the device is not in the white list feature library, judging whether the device is a known device; if the device is a known device, obtaining manually labeled device basic information, and updating the white list feature library, if the device is an unknown device, comparing the unknown device with the device fingerprint in the blacklist feature library, and if the device fingerprint corresponding to the unknown device is in the blacklist feature library, giving out alarm information; otherwise, manual judgment is carried out.
Owner:杭州优云科技有限公司
Diagnosis monitoring comprehensive medical system for color image fusion and fusion method thereof
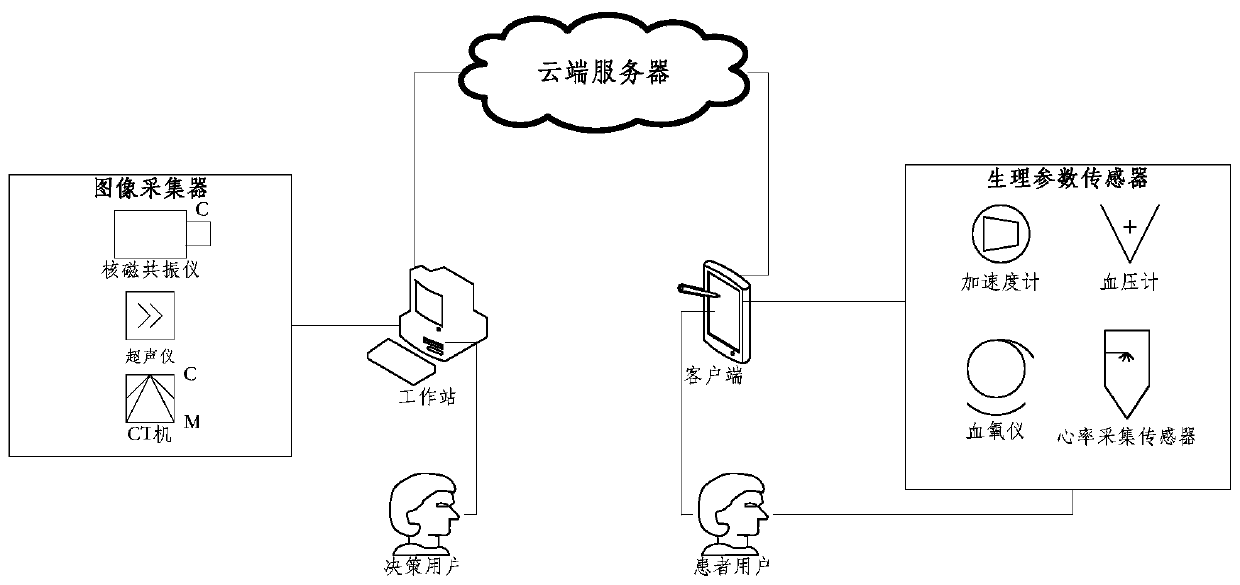
PendingCN110600109AReal-time monitoring statusPrivacy is not leakedMedical automated diagnosisMedical imagesColor imageWorkstation
A diagnosis monitoring comprehensive medical system for color image fusion includes a client, a workstation, a cloud server, an image acquisition device, and a physiological parameter sensor. The image acquisition device is connected to the workstation and uploads acquired images to the cloud server. The workstation fuses, by image fusion, the acquired CT images, ultrasound images, and MRI imagesin pairs, and uploads the fused images to the cloud server. The workstation and the cloud server use an encryption algorithm to communicate with each other, and use the ultrasound images and the MRI images to generate focus color images.
Owner:秦学玉
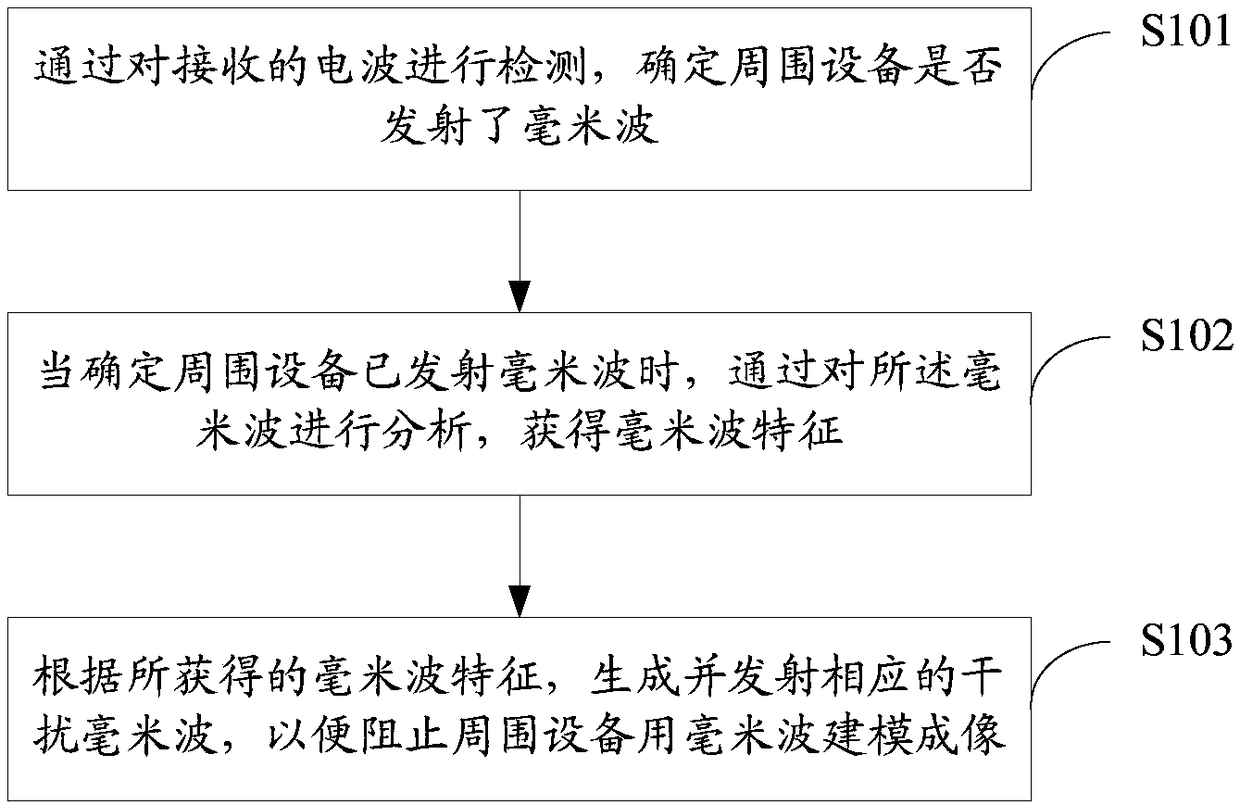
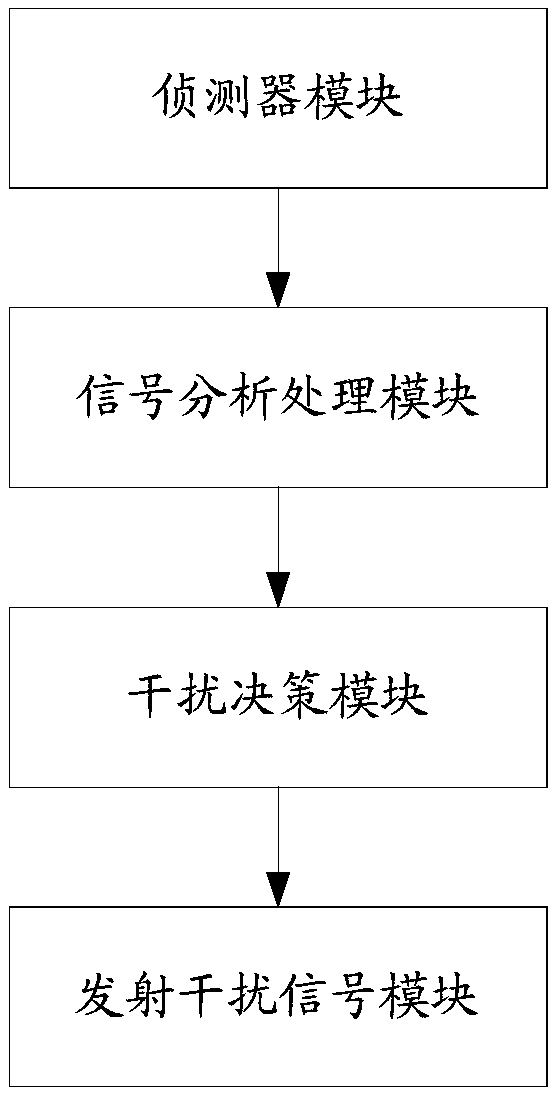
Method and device for preventing millimeter wave modeling imaging
PendingCN109490879AGuaranteed not to be leakedPrivacy is not leakedCommunication jammingRadio wave reradiation/reflectionMillimeterRadio wave
The invention discloses a method and device for preventing millimeter wave modeling imaging, and relates to the technical field of millimeter wave imaging. The method comprises the steps that a received radio wave is detected to determine whether or not a millimeter wave is emitted by peripheral equipment; when it is detected that the millimeter wave is emitted by the peripheral equipment, the millimeter wave is analyzed to obtain millimeter wave characteristics; a corresponding interfering millimeter wave is generated and emitted according to the obtained millimeter wave characteristics to prevent the peripheral equipment from modeling imaging using the millimeter wave.
Owner:ZTE CORP
Visual query method and device for multi-data-source merged data
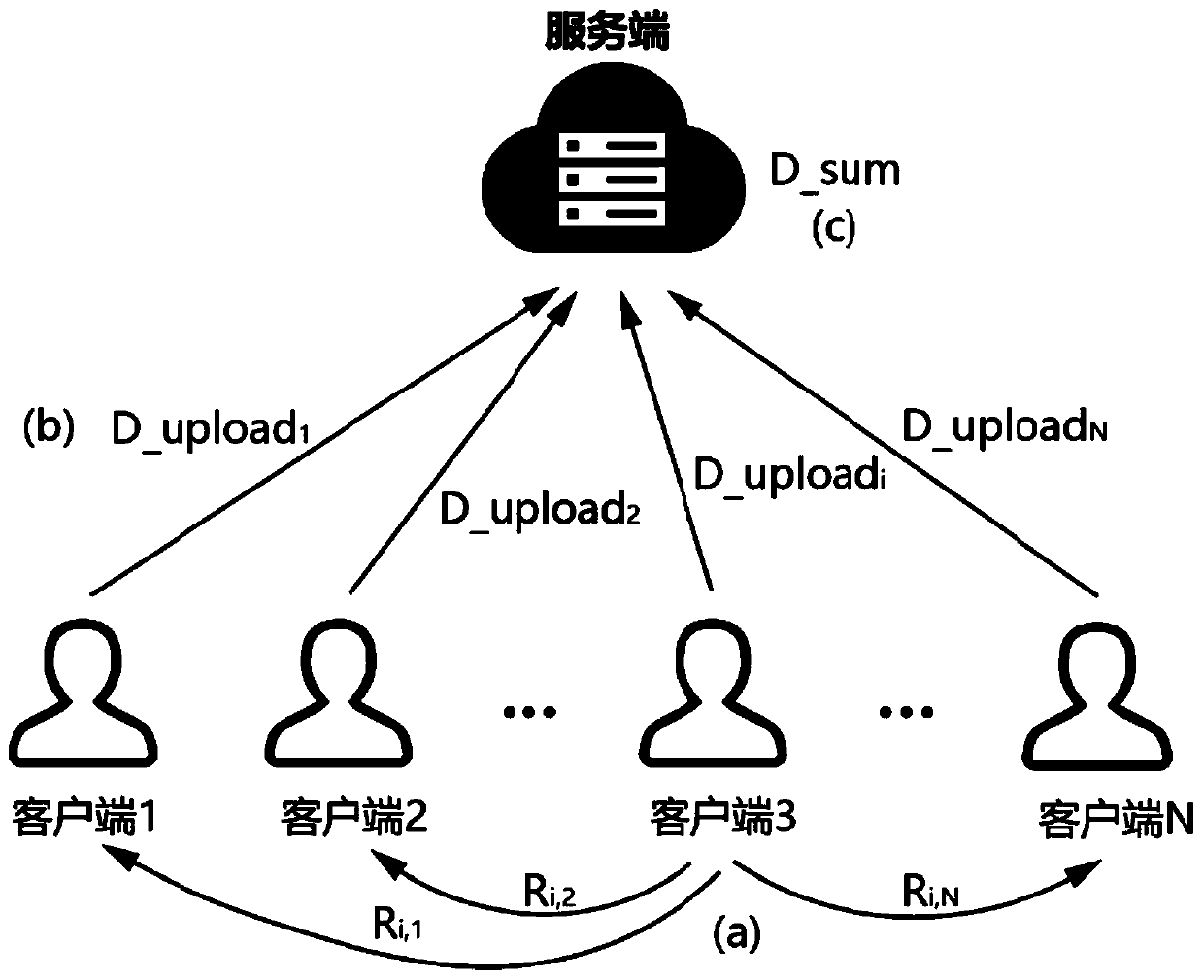
ActiveCN111078725APrivacy is not leakedAccurate visual query resultsDigital data protectionGeographical information databasesPrivacy protectionData source
The invention discloses a visual query method and device for multi-data-source merged data, belongs to the field of visual query and privacy protection, and comprises the following steps: 1) a serveris established among N participants; 2) according to the visual request, each participant calculates local data Di, and i belongs to [1, N]; 3) a random number vector is exchanged between every two participants, and the local data Di, the received random number vector and the sent random number vector are fused; meanwhile, a fusion result of the N participants is uploaded to the server; and 4) theserver merges the fusion results uploaded by the N participants and returns the merged results to the front end for visual analysis by the front end, so that the data of the plurality of clients is merged without iteration, an accurate visual query result can be obtained only by one-time processing, and the privacy of the data can be prevented from being leaked.
Owner:ZHEJIANG UNIV
Network structure learning method based on differential privacy
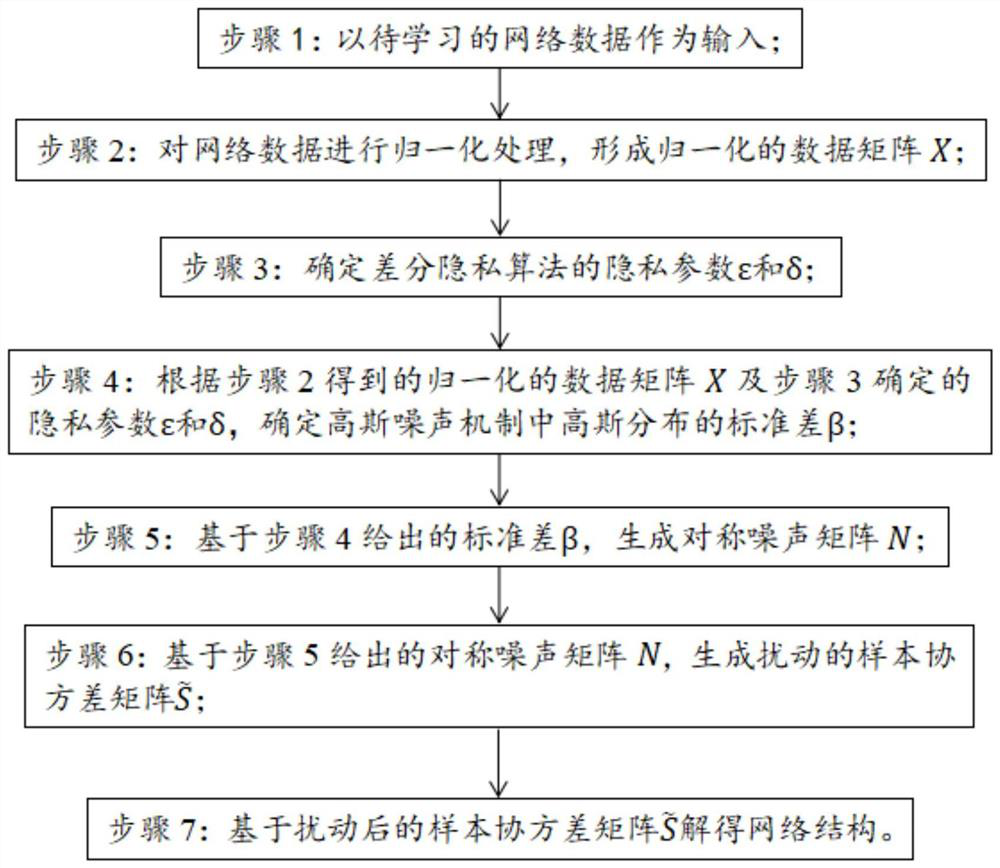
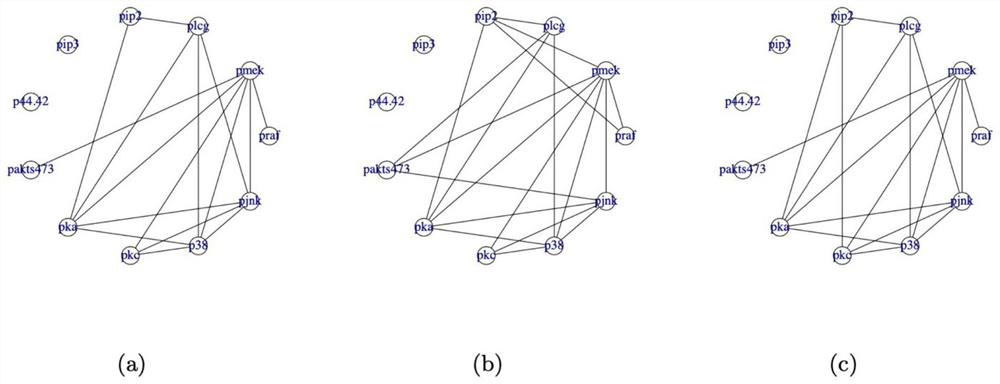
PendingCN112364380APrivacy leakImprove usabilityDigital data protectionMachine learningUndirected graphTheoretical computer science
The invention provides a network structure learning method based on differential privacy, and belongs to the field of machine learning. The method comprises the steps: taking to-be-learned network data as an input; normalizing the network data to form a normalized data matrix XX; determining privacy parameters epsilon and delta delta of the differential privacy algorithm; determining a standard deviation beta beta of Gaussian distribution in a Gaussian noise mechanism; generating a symmetric noise matrix NN; and generating a disturbed sample covariance matrix, and solving a network structure based on the disturbed sample covariance matrix. According to the method, the differential privacy is satisfied through the network structure learned in each step, that is, the method has a privacy protection capability, and the privacy of individuals in the data cannot be leaked. While privacy is protected, a network structure learning result also has relatively high availability, and a real potential network structure of data can be reflected; the differential privacy solving problem of a classic Graphical lasso model in an undirected graph model is solved, and it is guaranteed that the privacy of individuals in data is not leaked in the network structure learning process.
Owner:陕西数盾慧安数据科技有限公司
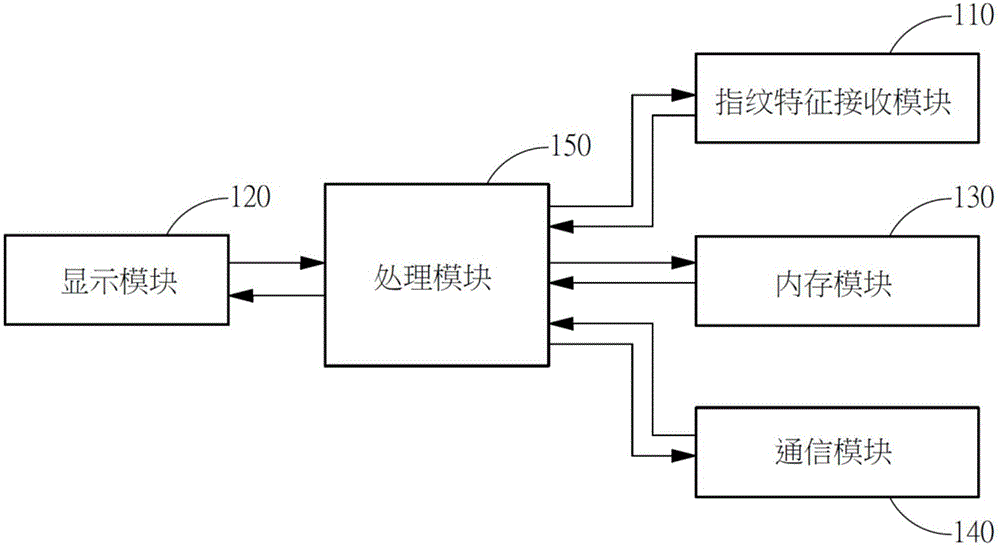
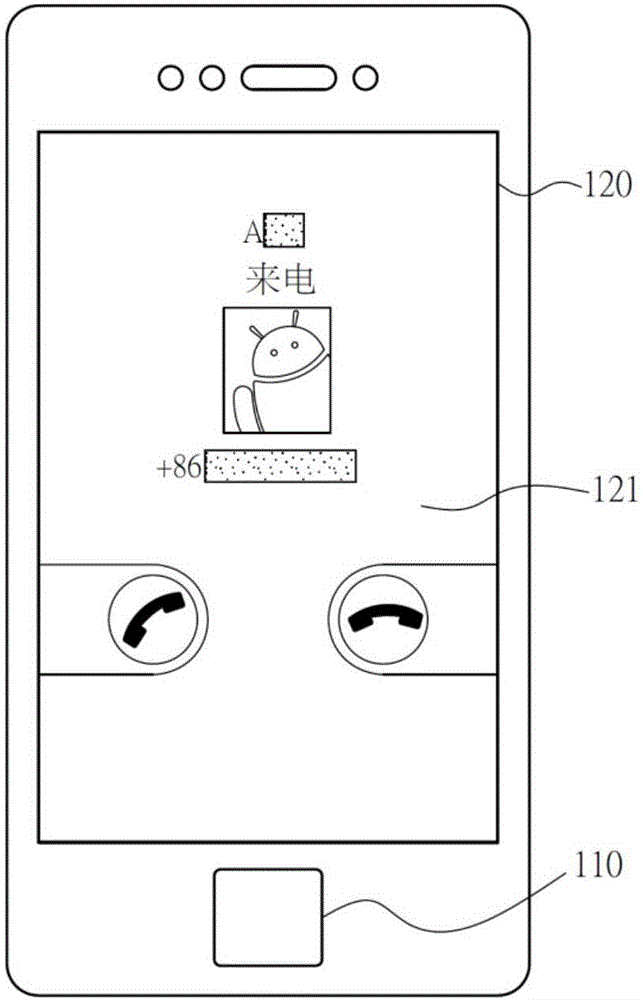
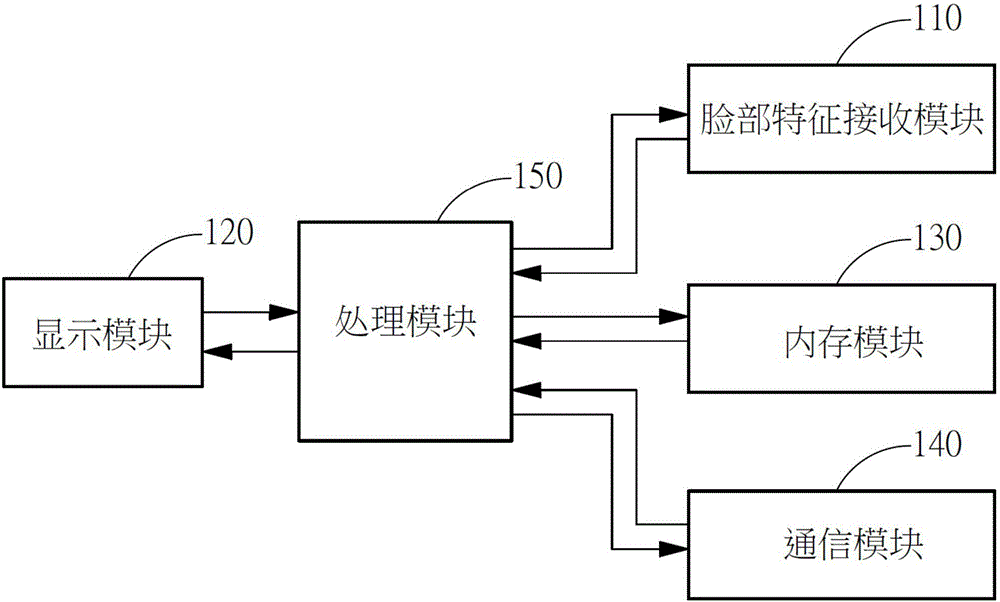
System and method for quickly decrypting and identifying information of protected contact through biological feature verification mode
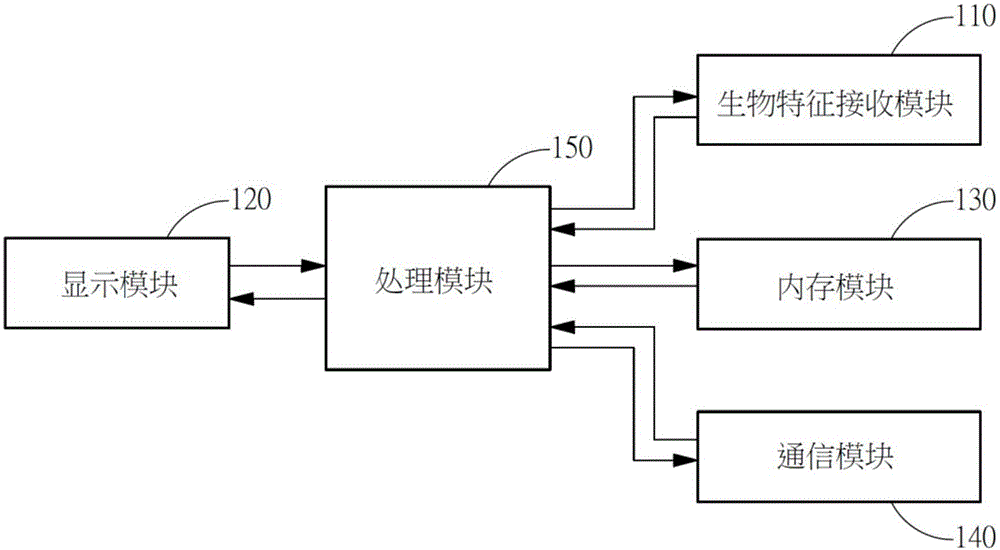
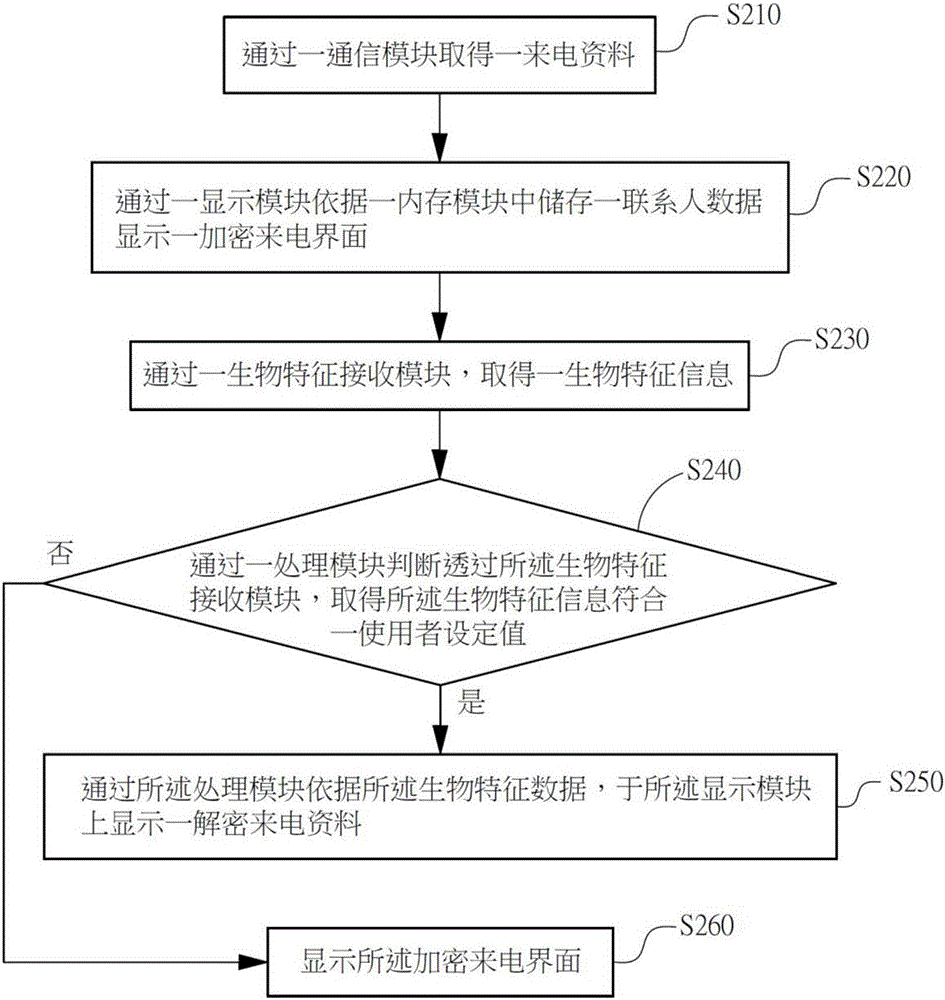
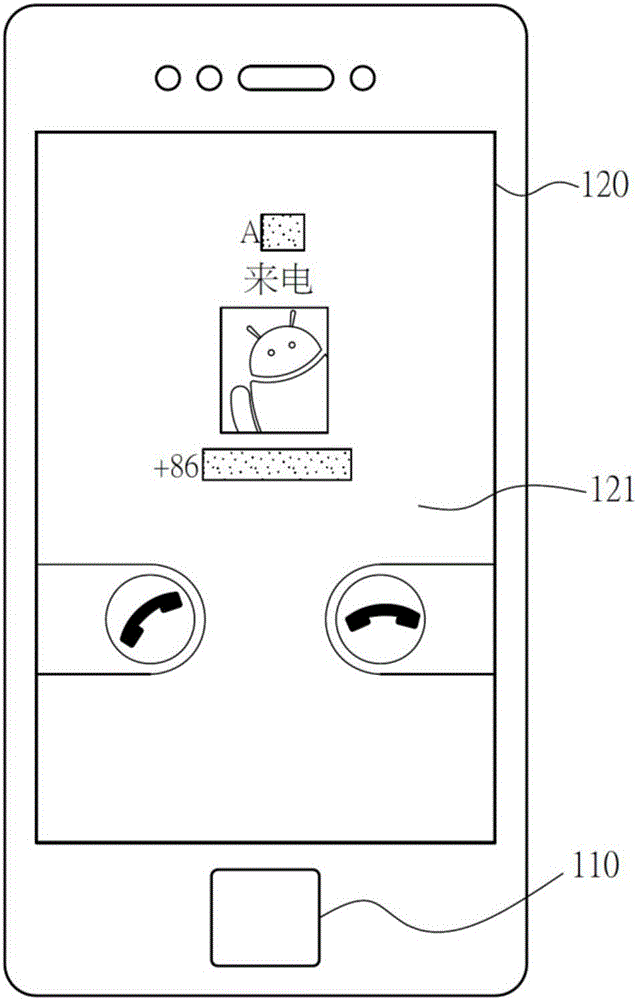
InactiveCN106060096AEasy to operateAvoid the dilemma of not being able to identify sensitive contactsTransmissionSecurity arrangementInformation systemMemory module
The invention discloses a system and a method for quickly decrypting and identifying information of a protected contact through a biological feature verification mode. The system comprises a biological feature receiving module, a display module, a memory module, a communication module and a processing module. The biological feature receiving module is used for acquiring biological feature information; the display module is used for displaying an encrypted incoming call interface; the memory module is used for storing contact data and biological feature data; the communication module is used for acquiring an incoming call material; the processing module is used for receiving the incoming call material according to the communication module, displaying the encrypted incoming call interface at the display module and acquiring the biological feature information through the biological feature receiving module; and wherein, when the processing module judges that the biological feature information acquired through the biological feature receiving module meets a user set value, the processing module displays the decrypted incoming call material according to the biological feature data.
Owner:SHENZHEN TINNO WIRELESS TECH
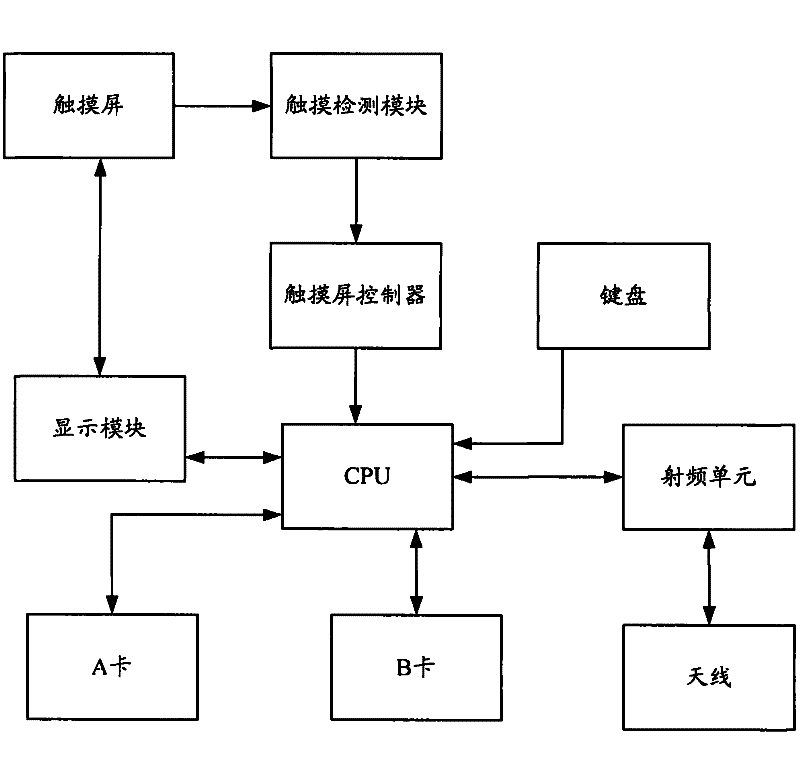
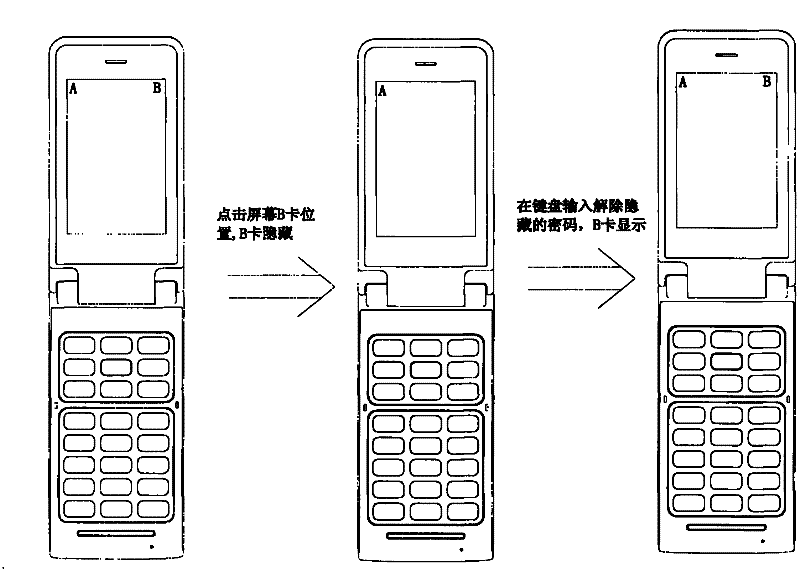
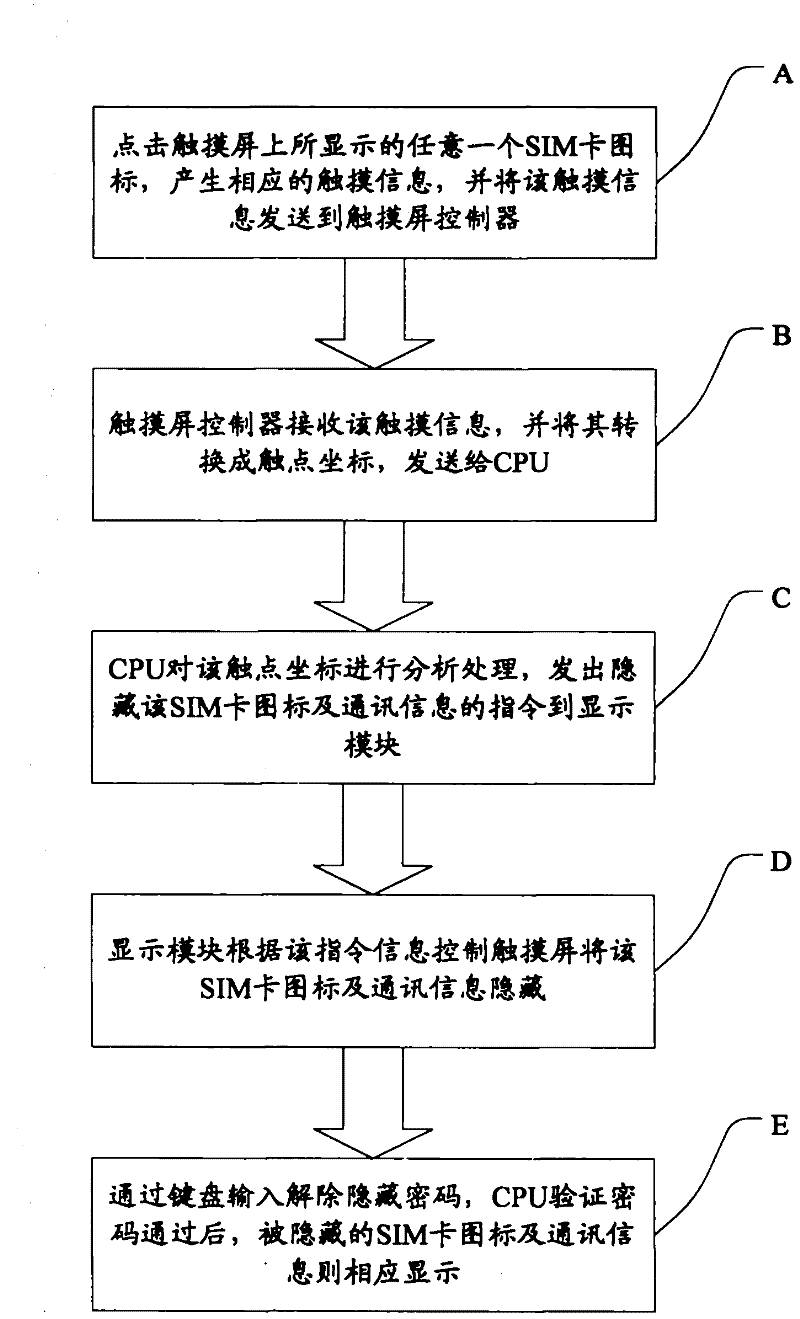
System and method for realizing single-card hiding in dual-card dual-standby mobile phone
InactiveCN102264062AGuaranteed to answer normallyGuaranteed functionNetwork data managementComputer hardwareTouchscreen
The invention discloses a system and method for realizing single-card hiding in a dual-card dual-standby mobile phone. Firstly, after clicking any SIM card icon displayed on the touch screen for a certain period of time, the SIM card icon has more corresponding icons and all related All communication information will be hidden, but its actual communication function still exists. It can answer calls and receive text messages normally, but cannot make calls or send messages. The dual-card dual-standby mobile phone also shows that there is only one SIM card, which gives people a feeling It is a single card single standby mobile phone. Compared with the prior art, the present invention can keep the privacy of the mobile phone user from being leaked under certain circumstances, and at the same time can ensure the normal answering and short message receiving functions of the SIM card with private information.
Owner:SHENZHEN GIONEE COMM EQUIP
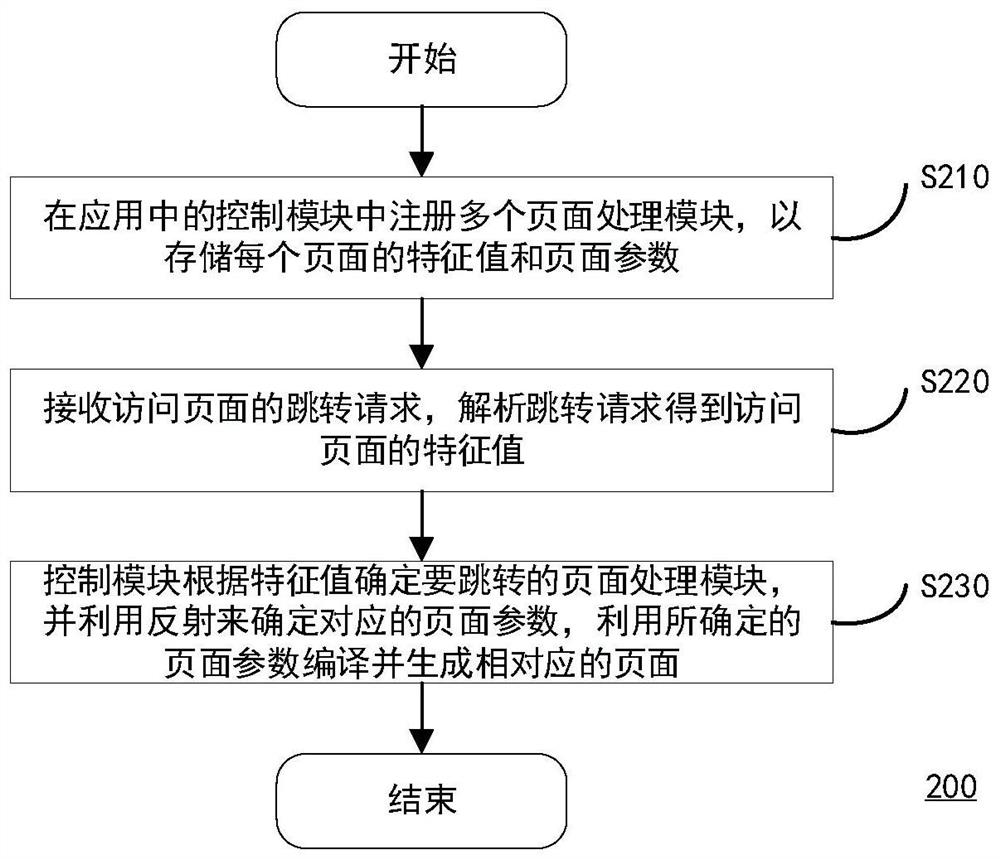
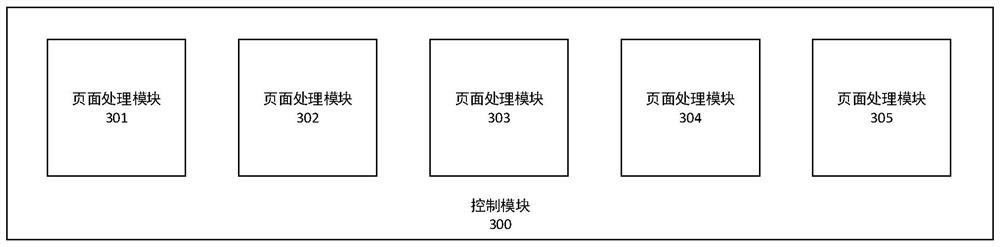
Page skipping method, computing equipment and storage medium
PendingCN112380480AJump request speed upQuick responseWebsite content managementSpecial data processing applicationsSoftware engineeringProcessing
The invention discloses a page skipping method which is suitable for being executed in computing equipment, an application comprising a plurality of pages is stored in the computing equipment, and themethod comprises the following steps: registering a plurality of page processing modules in a control module in the application so as to store a characteristic value and a page parameter of each page; receiving a page skip request, and analyzing the skip request to obtain a feature value of a target skip page; and the control module determines a page processing module corresponding to the targetskip page according to the feature value, determines associated page parameters by utilizing a reflection mechanism, compiles and generates the target skip page by utilizing the determined page parameters, and skips to the page. The invention further discloses the computing equipment and a computer readable storage medium.
Owner:BEIJING CHESHANGHUI SOFTWARE
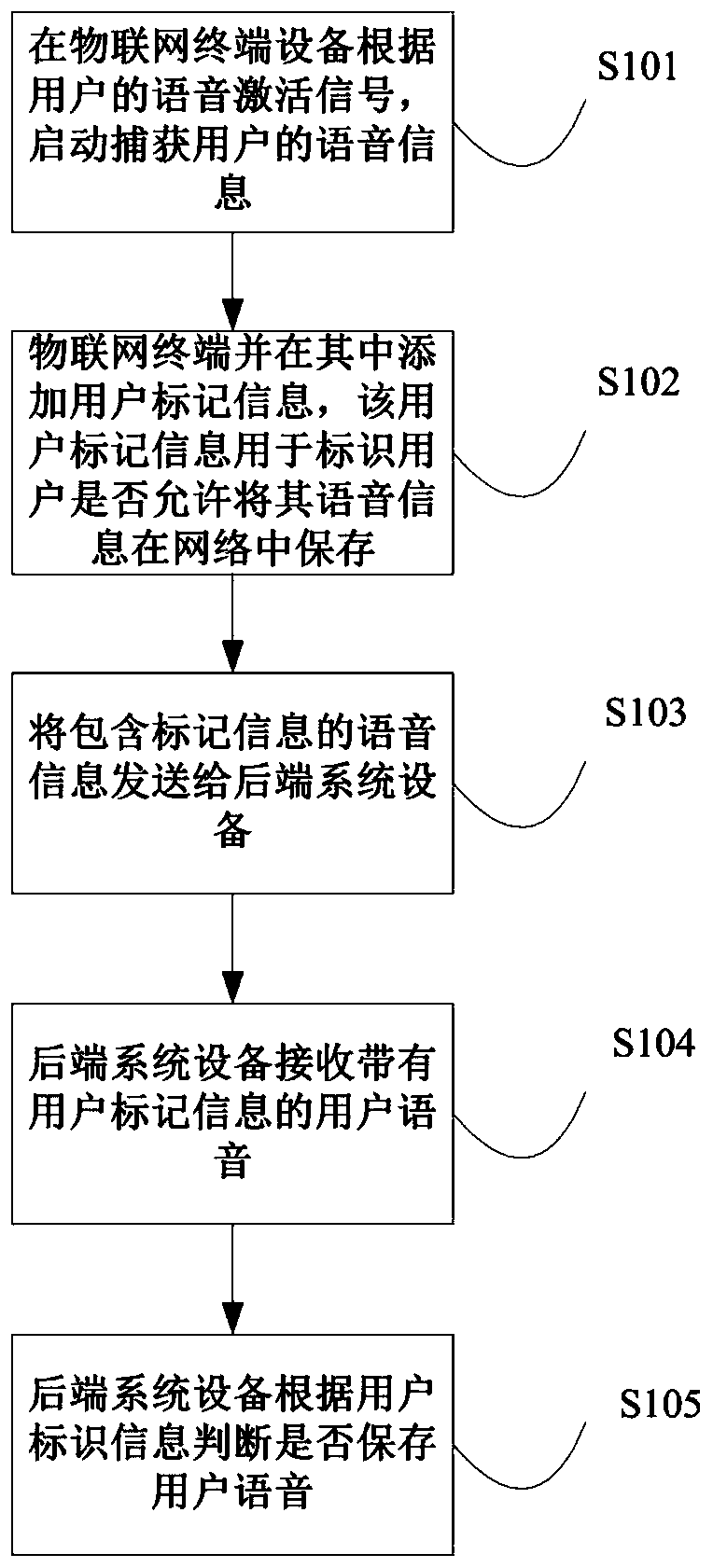
Method for privacy protection of internet of things device and system thereof
The invention provides a method for privacy protection of Internet of Things equipment and a system thereof, and the method comprises the steps: starting to capture voice information of a user at theInternet of Things terminal equipment according to a voice activation signal of the user, and adding user mark information which is used for identifying whether the user allows the voice information to be stored in a network or not; sending to a back-end system device; receiving the voice of the user of the user mark information by the back-end system device; acquiring the voice information of theuser by the back-end system equipment, determining whether the user allows the privacy information to be stored or not according to the user mark information, if the user mark information shows thatthe voice information of the user is not allowed to be stored, discarding the voice information by the back-end system equipment, according to the scheme, user privacy can be effectively protected, and the voice information of the user is prevented from being illegally acquired.
Owner:CHINA ELECTRONICS STANDARDIZATION INST +1
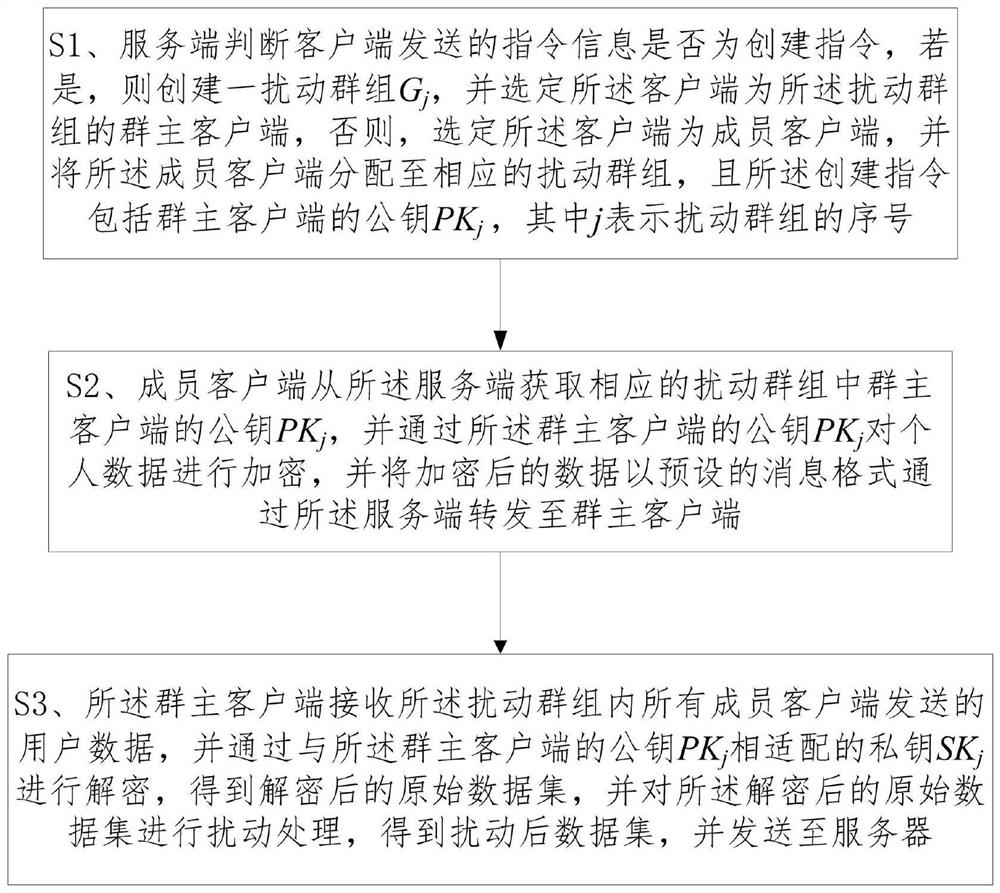
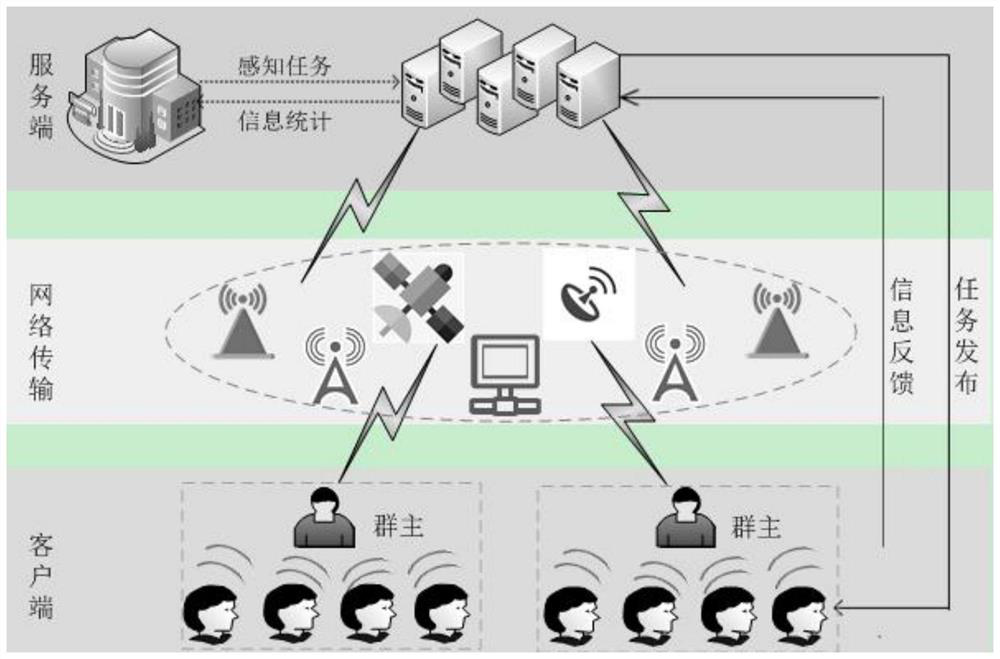
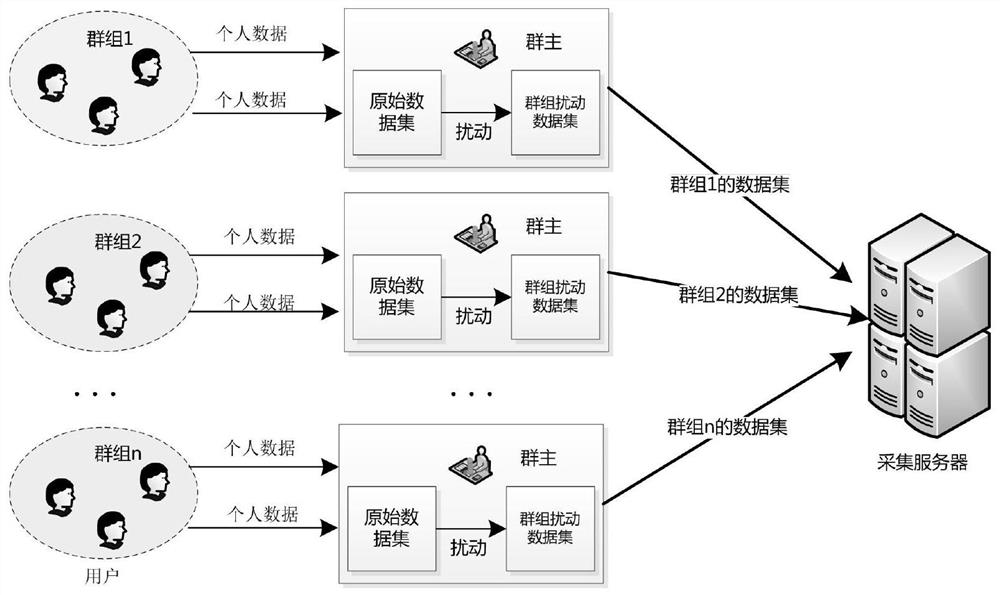
A method for collecting sensitive data
ActiveCN111046423BImprove securityProtect privacy and securityDigital data protectionData setOriginal data
The method for collecting sensitive data provided by the present invention is to create a disturbance group or join a disturbance group through the client, and the member client uses the public key PK of the group owner client j Encrypt personal data, and forward the encrypted data to the group owner client through the server in a preset message format, and the group owner client receives user messages sent by all member clients in the disturbance group data, and PK with the public key of the group owner client j Matching private key SK j Decrypt to obtain the decrypted original data set, and disturb the decrypted original data set to obtain the disturbed data set and send it to the server, which can avoid the intervention of third-party servers and improve the security of personal data collection Resilience, while satisfying the availability of data, it can resist the attacks of internal malicious users and untrusted servers, protect the privacy of data, and ensure that the privacy of users is not leaked.
Owner:HENGRUITONG FUJIAN INFORMATION TECH CO LTD
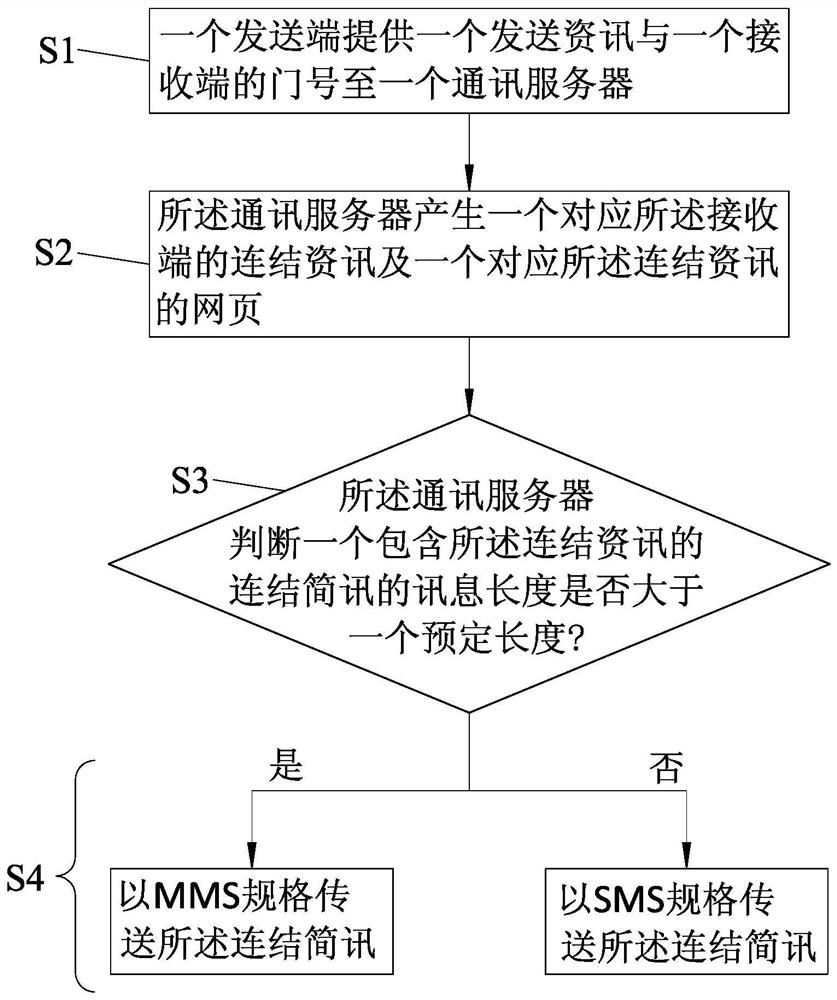
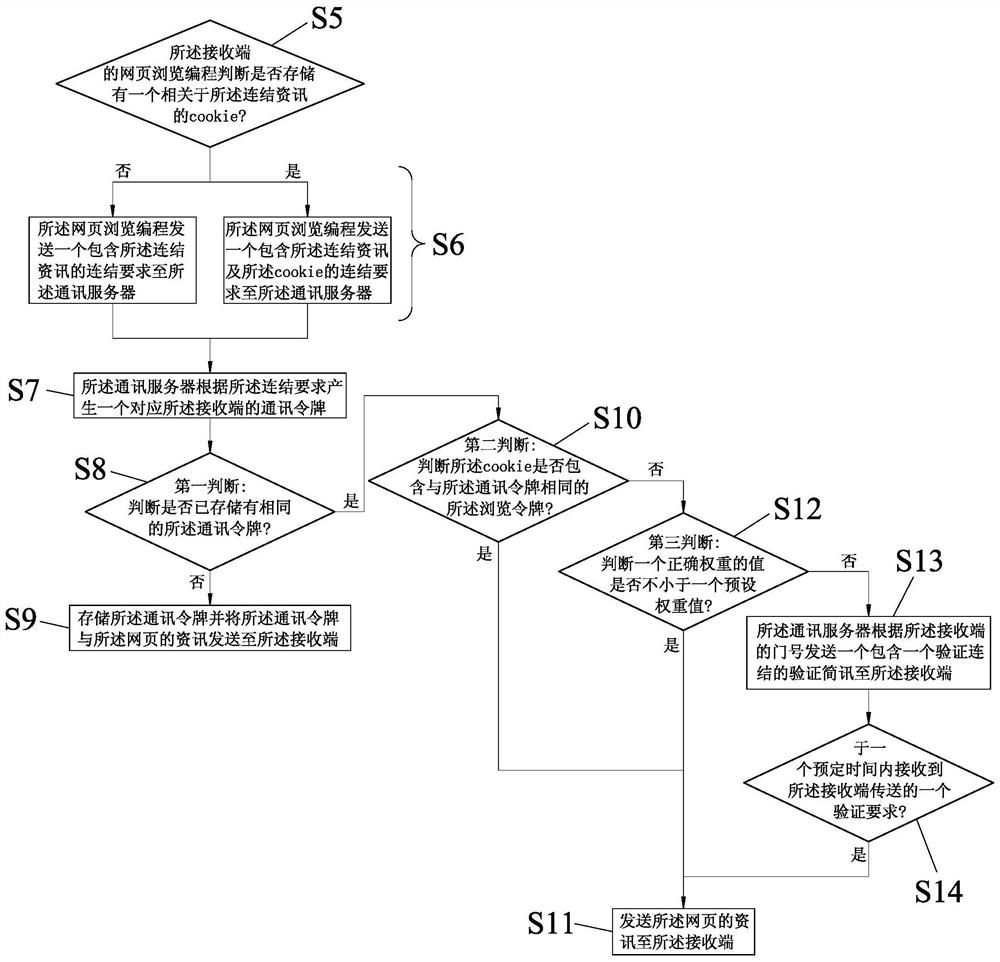
Identity identification method for short message starting webpage
PendingCN112395538APrivacy is not leakedDigital data protectionDigital data authenticationInternet privacyWeb page
An identity identification method of a short message starting webpage is applied to a communication server, and comprises the following steps that a communication server sends a connection short message containing connection information to a receiving end; the receiving end sends a connection request to the communication server, and determines whether the connection request contains a browsing token according to whether cookie related to the connection information is stored or not; the communication server generates a communication token and carries out first judgment; if the judgment result is negative, the communication server sends the information of the communication token and the webpage to the receiving end, and the receiving end stores the communication token as the browsing token;if the judgment result is positive, the communication server carries out second judgment; and if the judgment result is negative, the communication server sends the information of the webpage to the receiving end; if the judgment result is negative, the communication server sends a verification short message, and sends the information of the webpage after receiving a verification request. Therefore, merchants can control the marketing information and protect the privacy of consumers.
Owner:INTERACTION
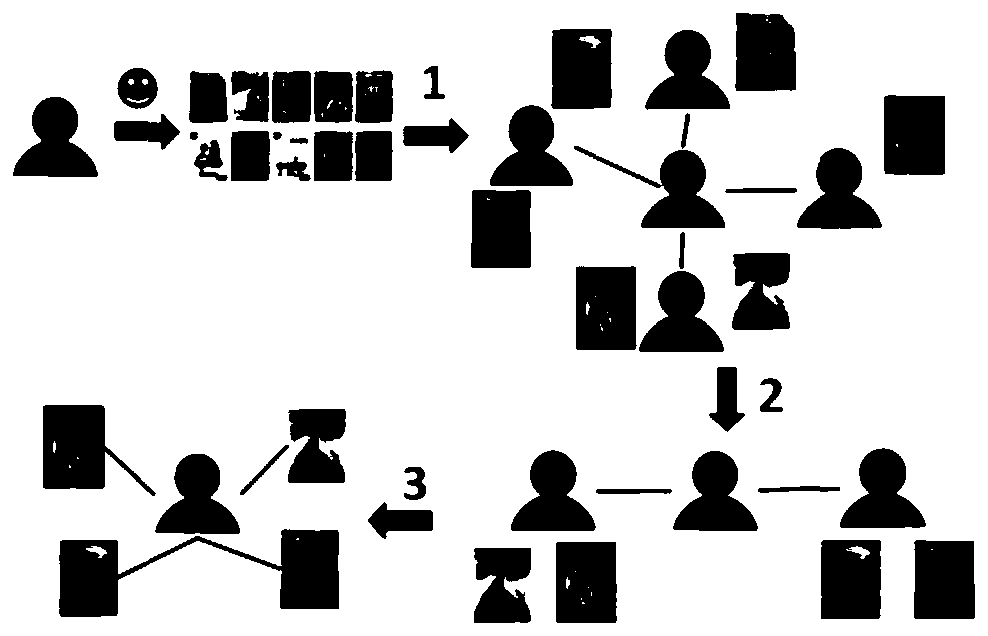
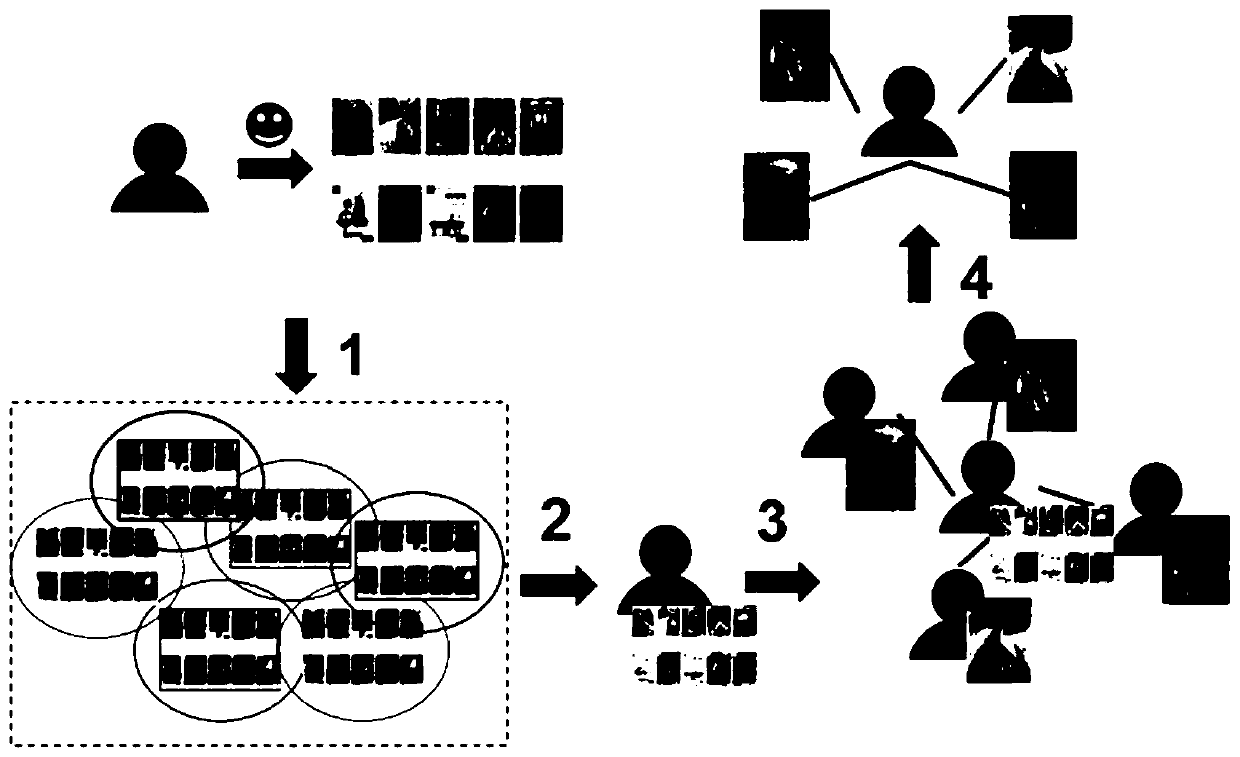
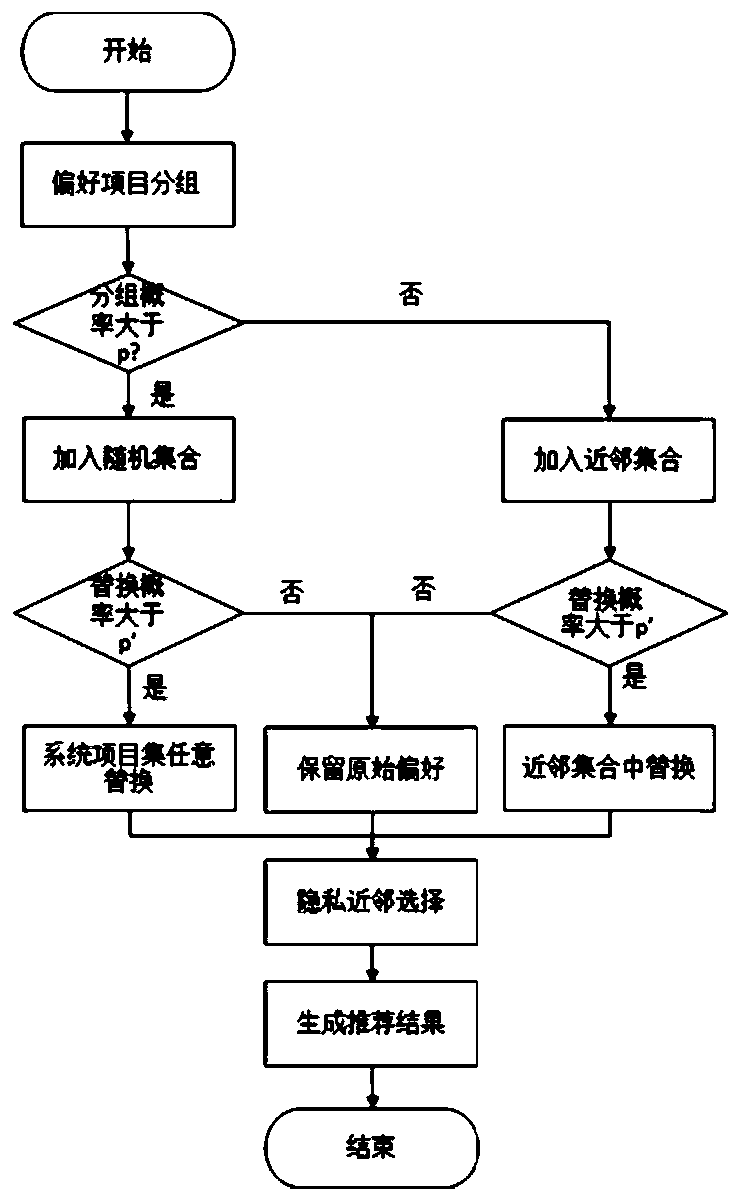
A Collaborative Filtering Recommendation Method Satisfied with Differential Privacy
ActiveCN107229876BPrivacy is not leakedGood recommendation resultDigital data information retrievalDigital data protectionTheoretical computer scienceDifferential privacy
The invention discloses a collaborative filtering recommendation method satisfying differential privacy. The method comprises the steps of firstly, calculating a grouping probability of a preference project of a target user, and according to the value of the grouping probability, determining whether the project is classified into a random set or a neighbor set; secondly, according to a replacement probability P', determining to execute three processes including arbitrary project replacement, neighbor project replacement and existing project retaining separately to complete the reconstruction of user's preference, and choosing neighbors of the target user according to a reconstructed preference application index mechanism; finally, generating a recommendation result according to the neighbors. The collaborative filtering recommendation method satisfying the differential privacy can ensure that the privacy of the user is not disclosed in the best way.
Owner:CENT SOUTH UNIV
Method and system for controlling requests for sensitive data
ActiveCN107426435BPrivacy is not leakedUser identity/authority verificationSubstation equipmentApplication procedureIntelligent equipment
The invention provides a method and a system for controlling sensitive data requests. When an application program needs to access sensitive data, the method can perform selection operation on the accessed sensitive data, selects sensitive data which cannot be accessed, and shields the sensitive data which cannot be accessed, so that the application program cannot obtain the sensitive data which is shielded. Thus, the application program can obtain some sensitive data in a selective manner, privacy of users is protected and is not leaked. The system is installed in an intelligent device, and protects privacy of users in the intelligent device from being leaked.
Owner:JINGZAN ADVERTISING SHANGHAI CO LTD
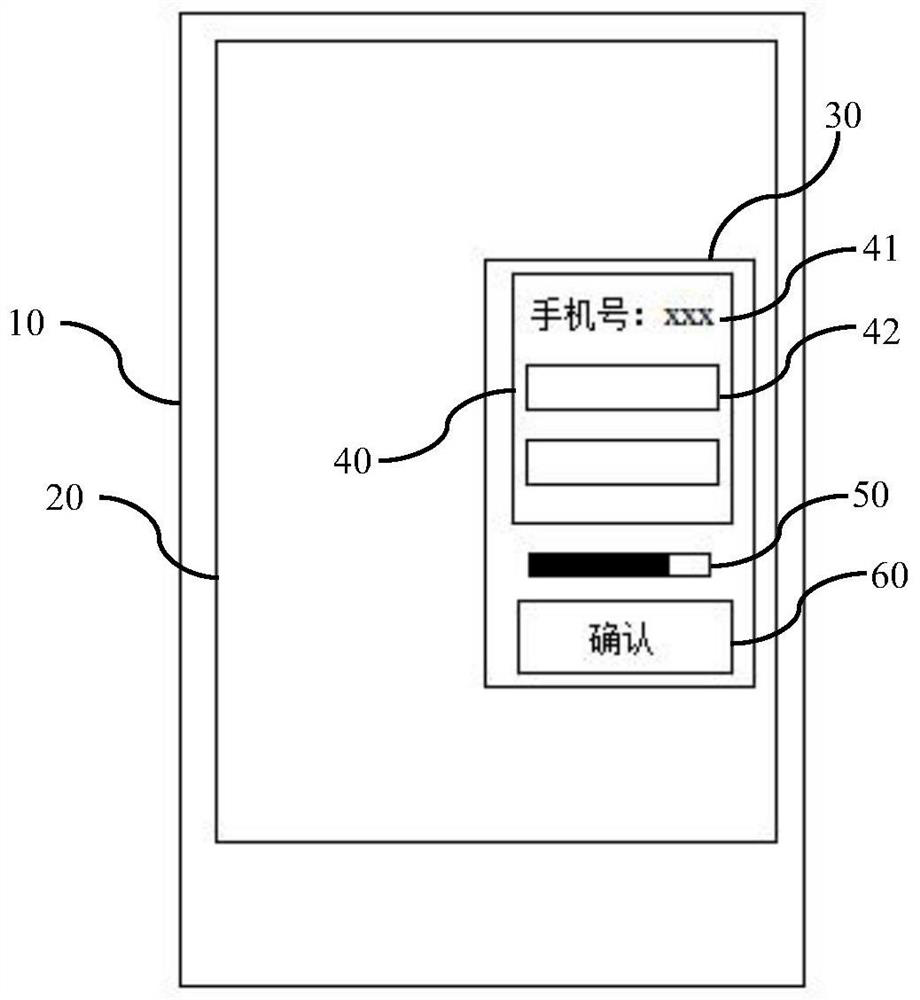
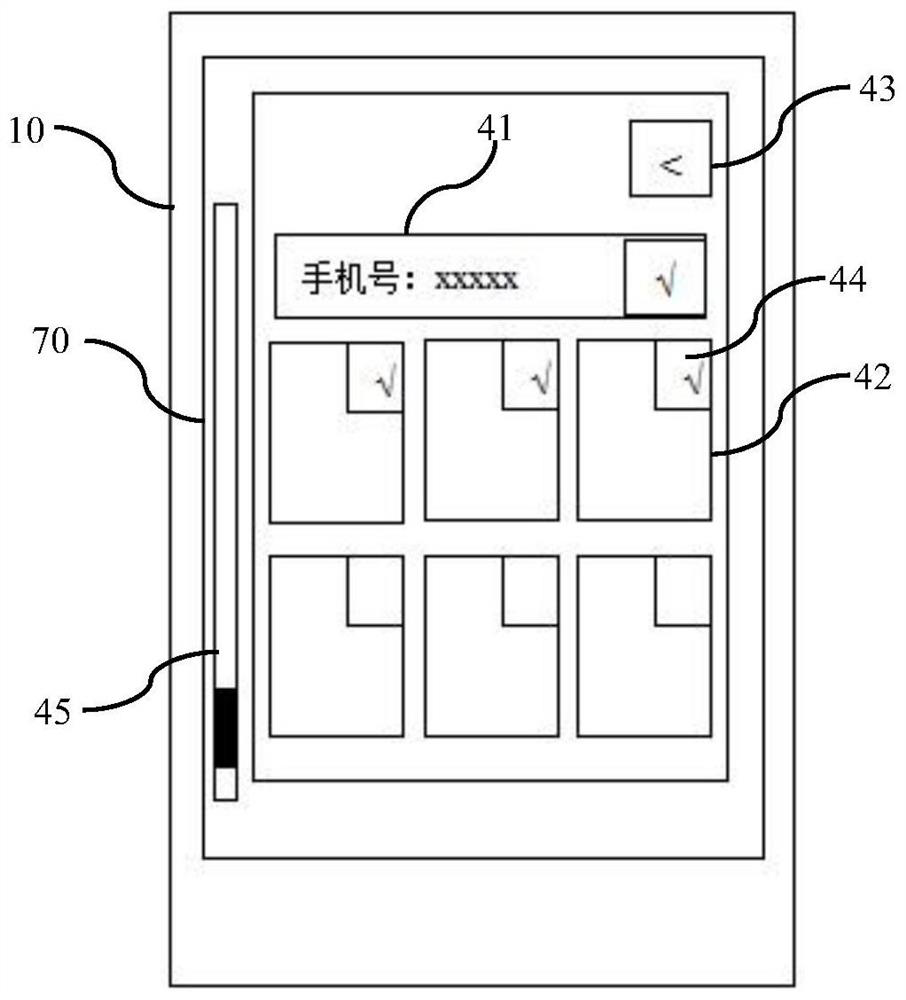
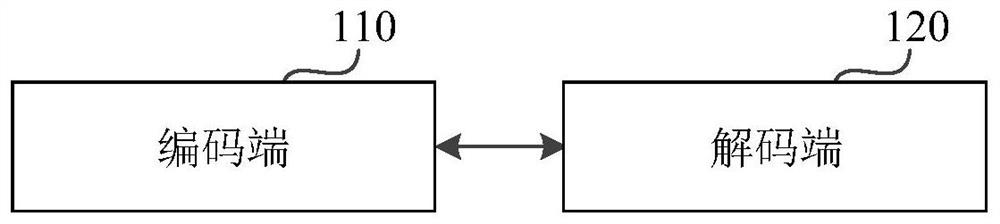
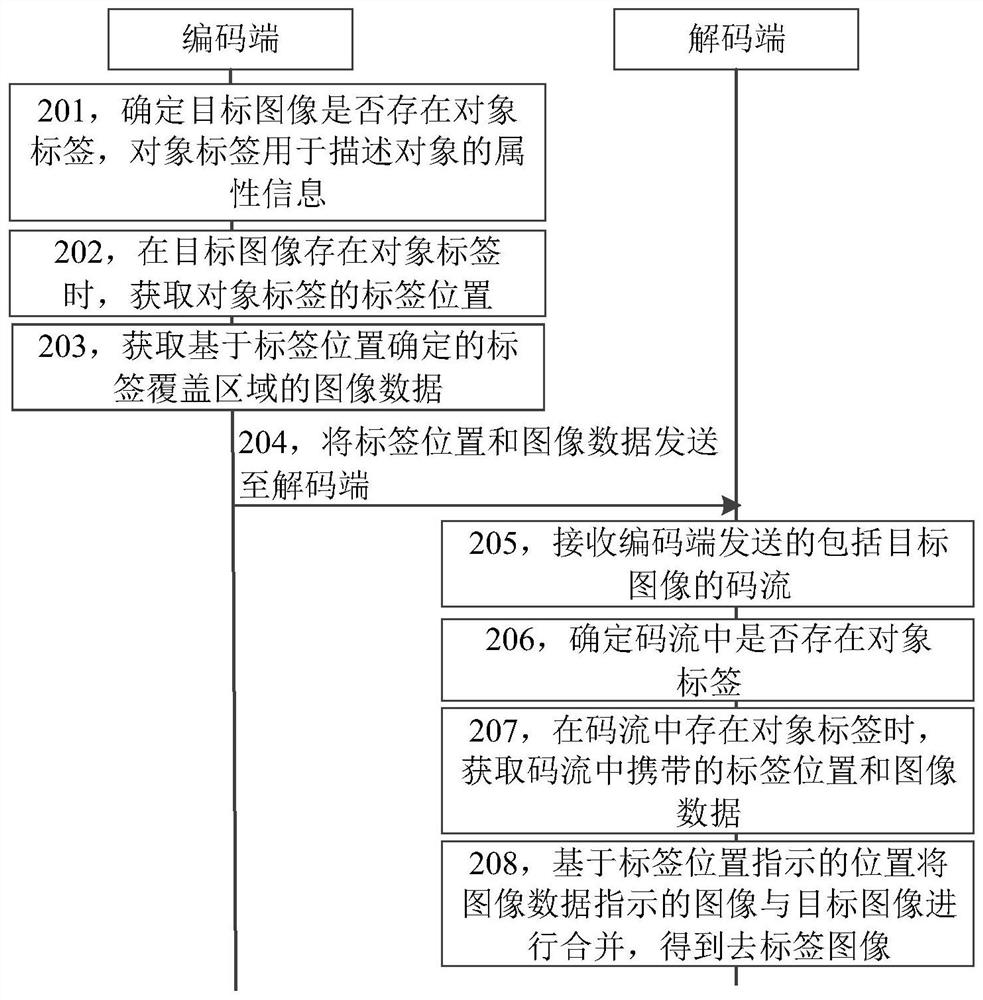
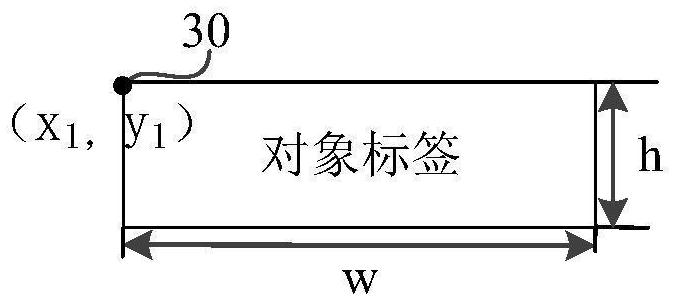
Image processing method, device and storage medium
ActiveCN109783658BDoes not affect the playback effectAchieve erasureDigital data information retrievalSpecial data processing applicationsImaging processingRadiology
The invention relates to an image processing method and device and a storage medium, and belongs to the technical field of image processing, and the method comprises the steps: determining whether anobject tag exists in a target image, and the object tag is used for describing attribute information of an object; when the object label exists in the target image, obtaining a label position of the object label; obtaining image data of a label coverage area determined based on the label position; sending the label position and the image data to a decoding end, so that the decoding end displays acorresponding image at a position indicated by the label position by using the image data. The problem that object labels can leak privacy of participants can be solved, and it can be guaranteed thatprivacy of the participants is not leaked; And the target image can be restored to an image which is not covered by the object label, so that the playing effect of the image is not influenced.
Owner:SUZHOU KEDA TECH
Method and system for quickly decrypting and identifying information of protected contact through fingerprint verification mode
The invention discloses a method and a system for quickly decrypting and identifying information of a protected contact through a fingerprint verification mode. The method is characterized by comprising steps: obtaining an incoming call material through a communication module, and displaying an encrypted incoming call interface through a display module, acquiring fingerprint information through a fingerprint feature receiving module, further comparing fingerprint data stored in a memory module is consistent with the fingerprint through a processing module, and displaying a decrypted incoming call material at the display module.
Owner:SHENZHEN TINNO WIRELESS TECH
Operating room nursing worker management method and system and storage medium
PendingCN112614574AFill in the information gapPrivacy is not leakedCo-operative working arrangementsDigital data protectionInformatizationOperating room management
The invention relates to the technical field of hospital nursing worker management, in particular to an operating room nursing worker management method and system and a storage medium. The method includes steps of: receiving task data issued by an operating room management terminal and creating an identification code containing the task data; sending confirmation information to the functional department management terminal; if confirmation information of the functional department management terminal is received, task information and the identification code are sent to a nursing worker mobile terminal; if the confirmation information of the functional department management terminal is not received or the return information of the functional department management terminal is received, not sending the task information; after receiving the receiving task information of the nursing worker mobile terminal, counting the task execution time of the nursing worker mobile terminal and task nodes; and after task completion information of the nursing worker mobile terminal is received, storing data information executed by the task of the nursing worker mobile terminal. The informatization blank of operating room nursing staff business is filled up, and a business closed loop among an operating room, a functional department and nursing staff is formed.
Owner:江苏达实久信数字医疗科技有限公司
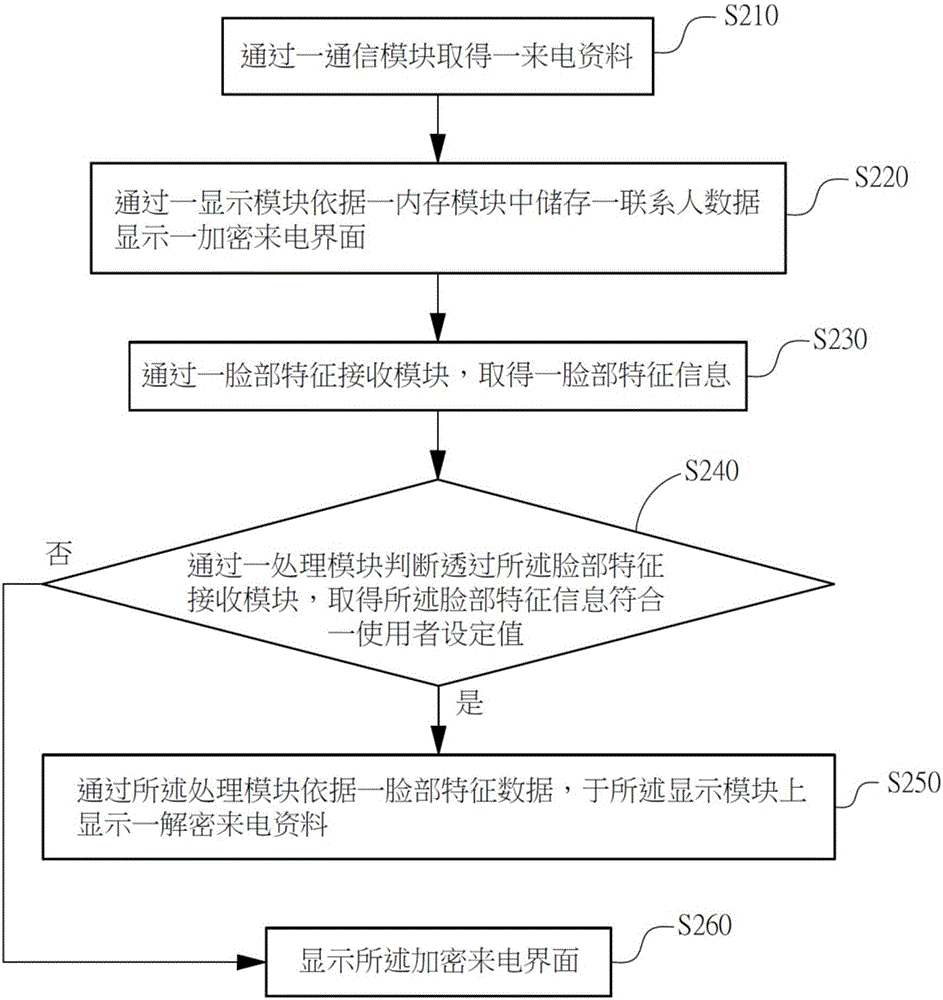
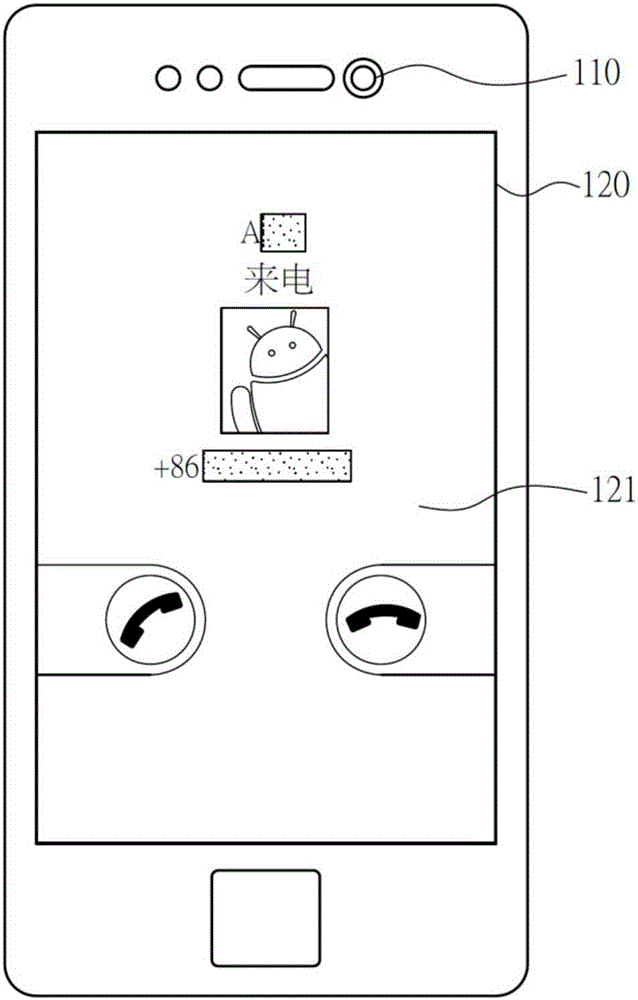
System and method for quickly decoding and identifying information of protected contact through facial feature verification
InactiveCN106302994AEncryption in timeHidden in timeUnauthorised/fraudulent call preventionValue setFeature data
The invention relates to a system and a method for quickly decoding and identifying the information of a protected contact through facial feature verification. The system comprises a facial feature receiving module, a display module, a memory module, a communication module, and a processing module. The facial feature receiving module obtains facial feature information; the display module displays an encrypted incoming call interface; the memory module stores contact data and facial feature data; the communication module obtains incoming call information; and the processing module receives incoming call information according to the communication module, displays the encrypted incoming call interface on the display module, and obtains the facial feature information through the facial feature receiving module. When the processing module judges that facial feature information obtained through the facial feature receiving module is in accordance with a value set by a user, the processing module displays decrypted incoming call information according to the facial feature data.
Owner:SHENZHEN TINNO WIRELESS TECH
A kind of big data encryption and decryption processing method and system
The embodiment of the invention discloses a big data encryption and decryption processing method and system. The method comprises following steps: before data are stored in an open source storage system, detecting whether the data are plaintext data; if the data are plaintext data, encrypting the data into ciphertext data; storing the ciphertext data in the open source storage system; verifying whether there are plaintext data in the open source storage system; when there are plaintext data in the open source storage system, encrypting the plaintext data into ciphertext data; and when outputting the ciphertext data from the open source storage system, descrypting the ciphertext data. According to the method and the system of the invention, the data stored in the open source storage system are encrypted; the data are decrypted and recovered when outputting the data; and therefore, the data security is ensured and the privacy of the user is not leaked on the basis of not influencing the normal display and processing of the data.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD +1
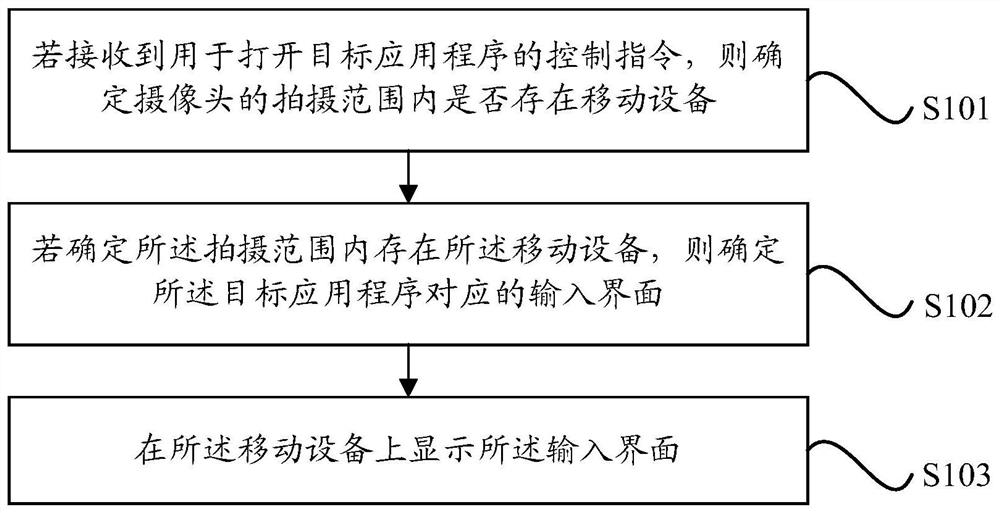
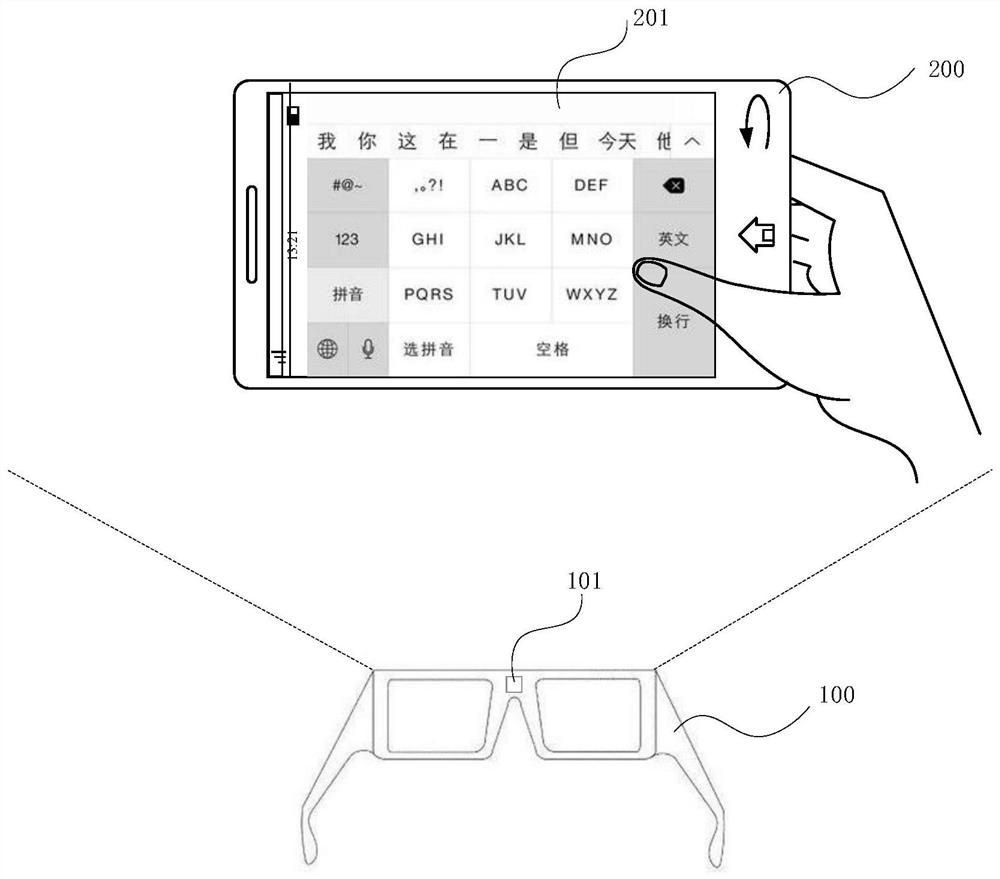
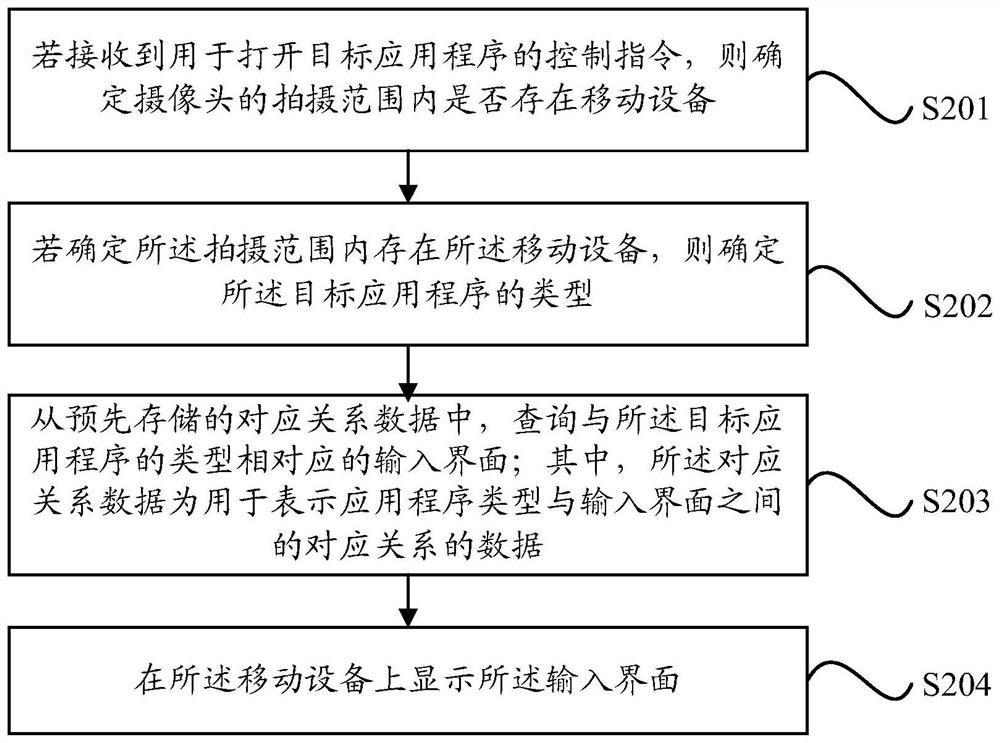
Input interface display method, device, electronic device
ActiveCN107656616BImprove accuracyAvoid misidentificationInput/output for user-computer interactionCharacter and pattern recognitionComputer hardwareUser privacy
The present disclosure relates to an input interface display method, device, and electronic device. The method includes: if a control instruction for opening a target application program is received, determining whether there is a mobile device within the shooting range of the camera; If the mobile device exists within the range, then determine the input interface corresponding to the target application program; and display the input interface on the mobile device. The present disclosure receives a control instruction for opening a target application program, determines whether there is a mobile device within the shooting range of the camera, and then determines the input interface corresponding to the target application program, so as to display the input interface on the mobile device, so as to realize through the input interface Inputting information can improve the accuracy of information input and improve user experience; in addition, compared with the way of voice input in related technologies, it can also avoid information recognition errors caused by noise interference and ensure that user privacy is not leaked.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Calling method for license plate recognition, computer device and readable storage medium
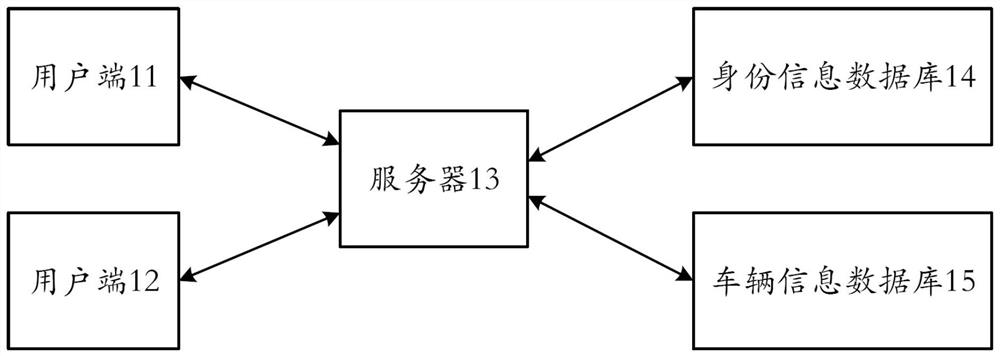
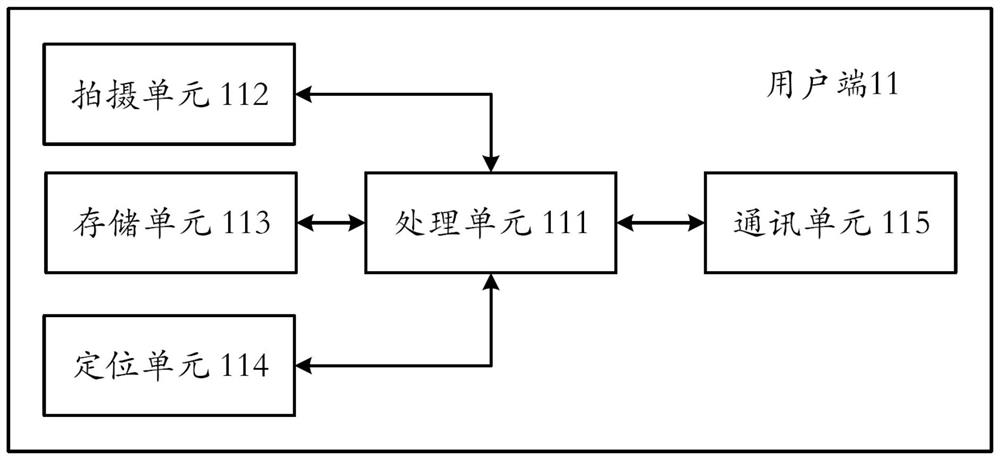
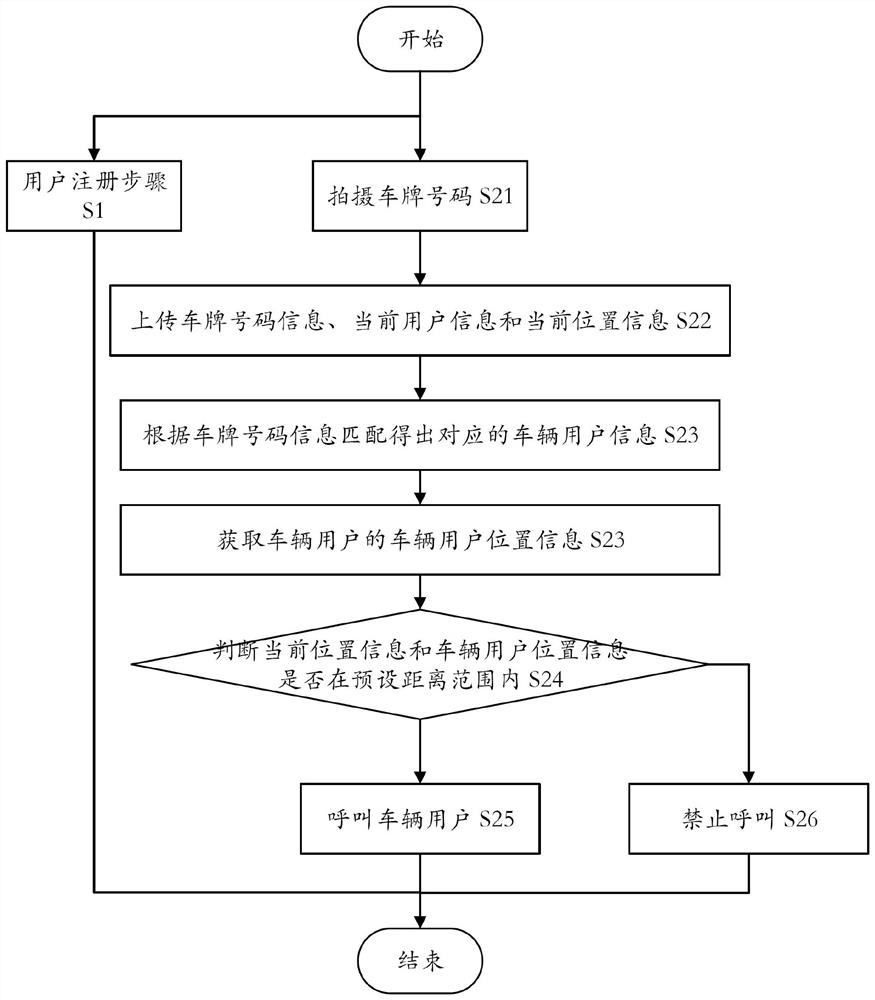
PendingCN114422945AEasy accessAvoid harassmentAssess restrictionLocation information based serviceEngineeringSpeech input
The invention provides a license plate recognition calling method, a computer device and a readable storage medium. The license plate recognition calling method comprises the steps of obtaining license plate number information, current user information and current position information; corresponding vehicle user information is obtained through matching according to the license plate number information; obtaining vehicle user position information of a vehicle user; comparing whether the distance between the current position information and the vehicle user position information is within a preset distance range; and if so, calling the vehicle user. According to the scheme, the license plate number image is obtained through photographing, the license plate number can also be obtained through scanning, manual input or voice input, then the vehicle user information is obtained through matching in the system, then the current position information of the calling end user is compared with the vehicle user position information, if the current position information is not within the preset range, calling is forbidden, crank calls are avoided, and the user experience is improved. And calling the vehicle user in a preset range. The automatic calling process greatly improves the communication efficiency, so that the two parties can effectively communicate to solve the problem as soon as possible.
Owner:李毓思
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com