Disassembly function hijacking method and device based on Linux system and storage medium
A storage medium and disassembly technology, applied in the field of network security, can solve problems such as malicious program evasion, inability to parse complex function parameters, abnormal impact caused by system applications, etc., to avoid hijacking failure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
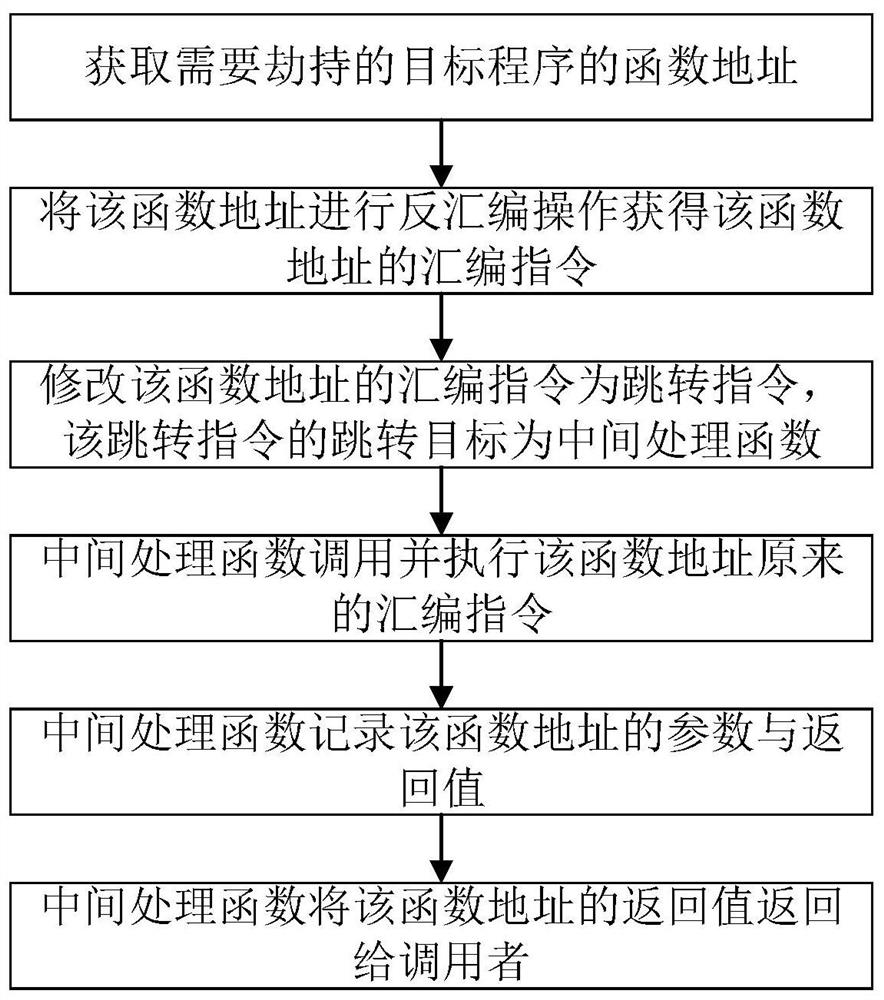
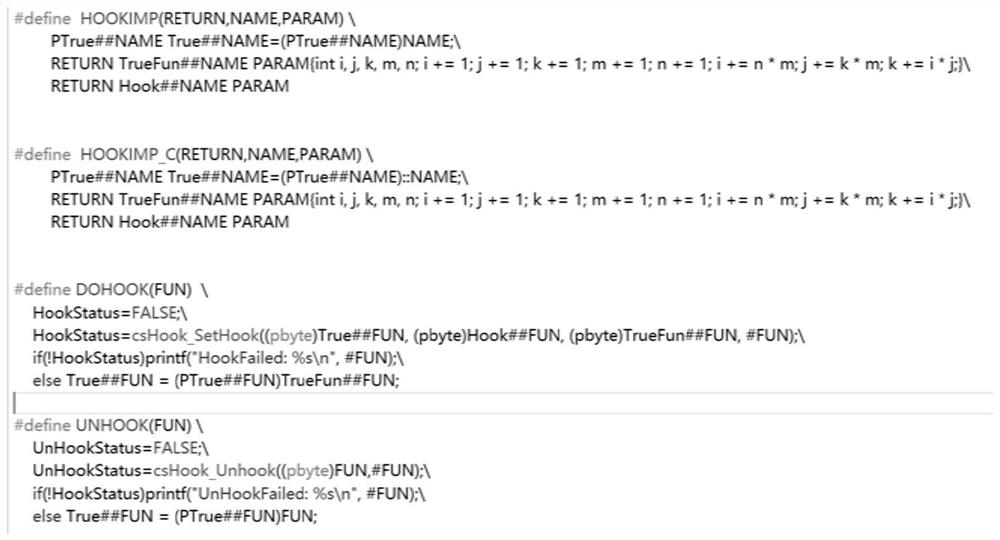
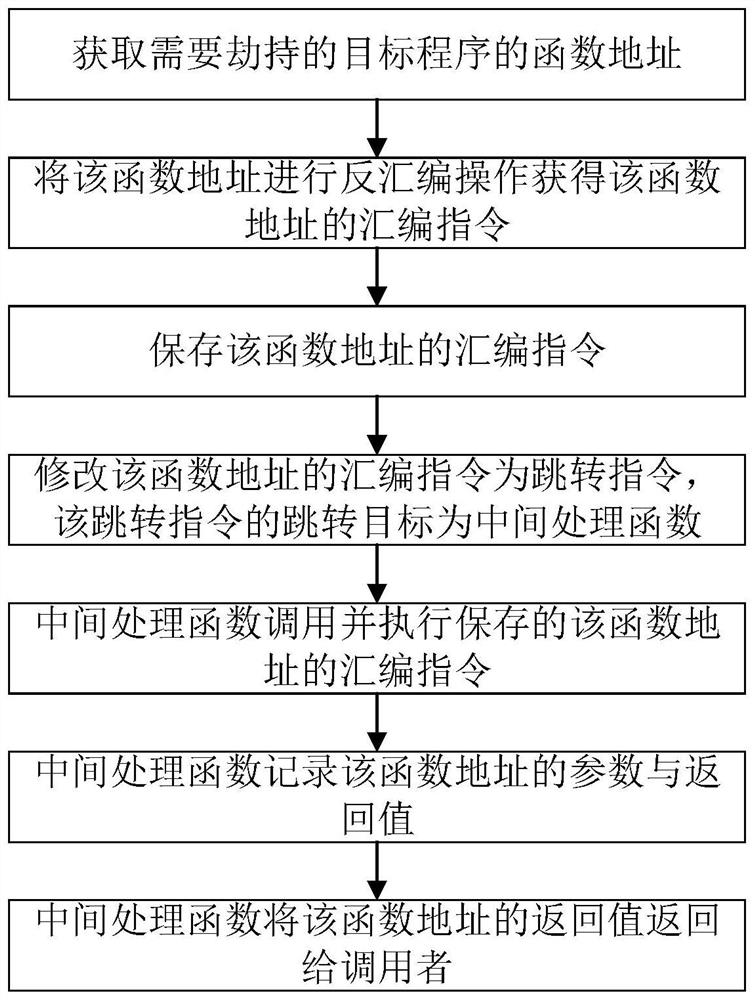
[0034] In order to solve the problems existing in the function hijacking method under the current Linux system, this embodiment proposes a disassembly function hijacking method based on the Linux system, so as to be able to hijack all dynamic library functions and system API functions at the application layer, and obtain The parameters and return values of the function, so that it can more accurately determine whether the executable program has dangerous behavior, thereby reducing the loss caused by the threat program. Such as figure 1 As shown, the present embodiment proposes a disassembly function hijacking method based on Linux system, comprising the following steps:
[0035] (1) Obtain the function address of the target program that needs to be hijacked;
[0036] (2) performing a disassembly operation on the function address to obtain an assembly instruction of the function address;
[0037] (3) the assembly instruction of modifying the function address is a jump instr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com