Multi-cell network secure transmission method based on artificial noise
A technology of artificial noise and network security, applied in security devices, transmission systems, radio transmission systems, etc., can solve problems such as inability to adapt to dynamic changes in wireless networks, limit algorithm applications, etc., achieve a wide range of application scenarios, enhance security performance, and improve reliability sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
[0061] A preferred embodiment of the present invention is as follows:
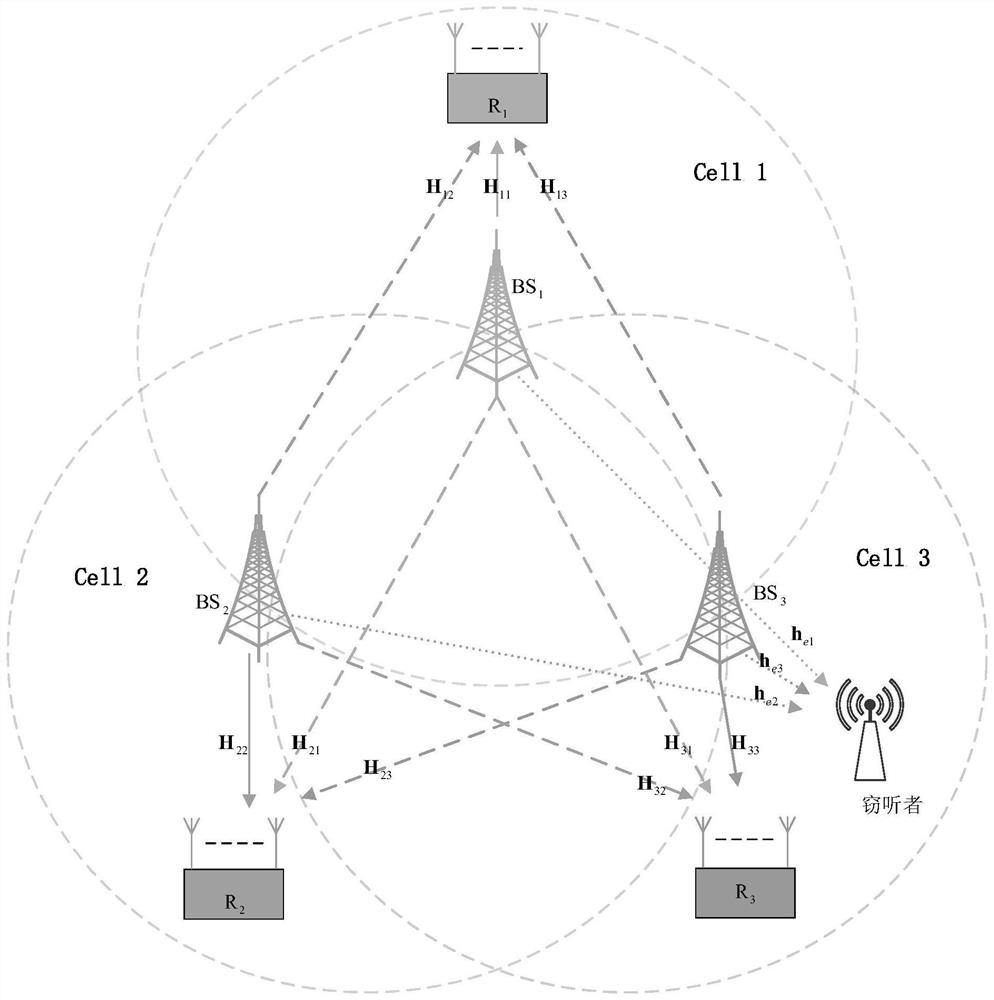
[0062] Such as figure 1 As shown, it is assumed that there is a base station BS in the cell 1 、BS 2 and BS 3 To 3 legitimate users R in the cell 1 , R 2 and R 3 Send information, user k, k∈{1,2,3} represent user R respectively 1 , R 2 and R 3 ; Among them, the base station BS 3 to user R 3 Send a secure message, the passive eavesdropping node eavesdrops on the message, BS 3 to R 3 While transmitting security messages, artificial noise AN is also transmitted to interfere with eavesdropping nodes; the base stations BS of the other two cells 1 with BS 2 Only useful signals are transmitted and no additional interference is introduced to legal transmissions in the network. Assume that the number of transmitting antennas equipped with three base stations is M 1 , M 2 , M 3 , the number of receiving antennas equipped by three legitimate users is N 1 ,N 2 ,N 3 , while the eavesdropping node has...
specific Embodiment approach
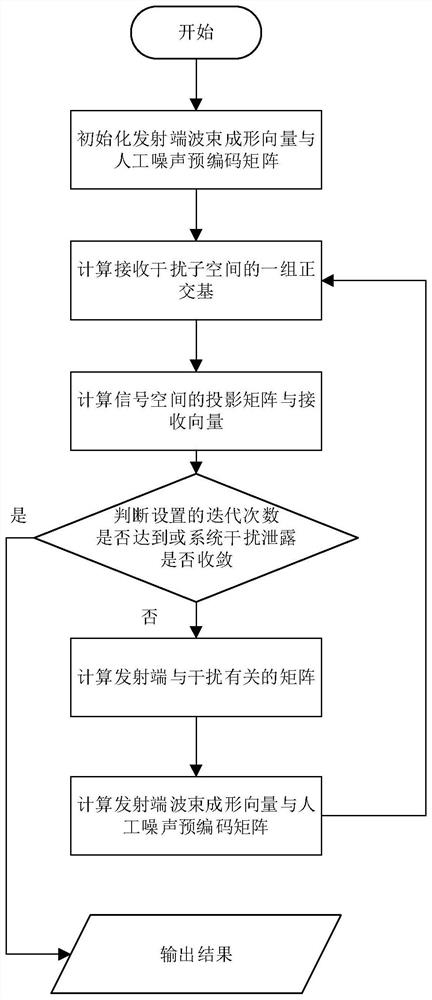
[0069] A specific implementation manner of processing received information using an interference alignment algorithm that minimizes AN alternately is as follows:
[0070] Initialize the transmit beamforming vector v j and artificial noise precoding matrix w 3 , j=1,2,3, set the number of iterations;
[0071] Calculate the receiving interference matrix Q according to the beamforming vector at the transmitting end and the artificial noise precoding matrix k and a set of orthonormal bases C of the received interference subspace k ,satisfy
[0072]
[0073] C k =x l [Q k ],l=1,...,N k -1 and k=1,2,3
[0074] Among them, Q k Represents the receiving interference matrix, H kj Indicates the channel matrix from base station j to user k, H k3 Indicates base station BS 3 channel matrix to user k, v j Denotes the transmit beamforming vector of base station j, w 3 Represents the artificial noise precoding matrix, C k represents an orthonormal basis, x l [Q k ] repres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com