Big data activity project log analysis and resource allocation method
An activity project and resource allocation technology, which is applied in the field of big data activity project log analysis and resource allocation, can solve the problems of low resource allocation efficiency and long time required for activity projects, so as to improve efficiency and timeliness, and ensure security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
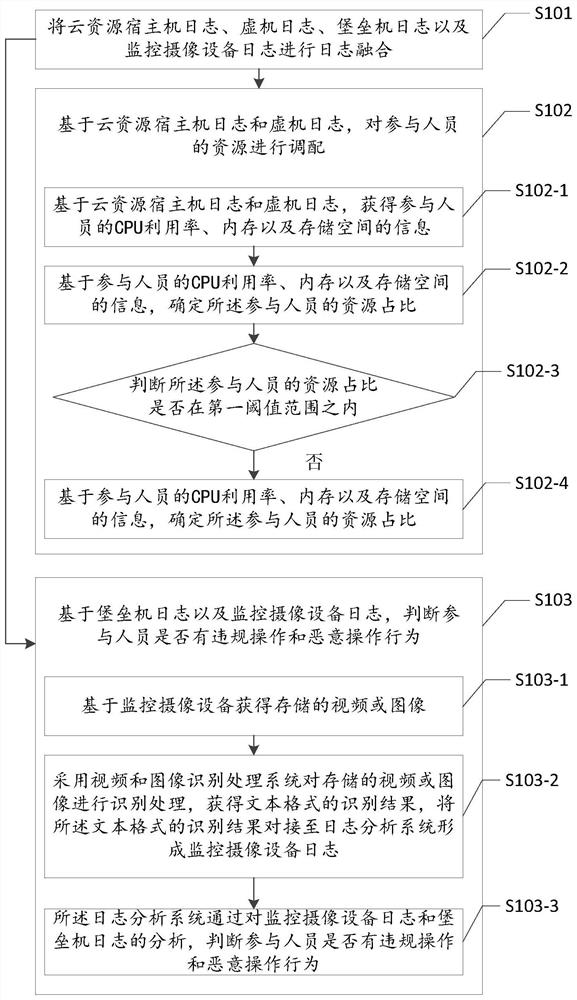
[0051] The embodiment of the present invention provides a big data activity project log analysis and resource allocation method, figure 1 It is a flow chart of the big data activity project log analysis and resource allocation method in the embodiment of the present invention, please refer to figure 1 , the method includes the following steps:
[0052] Step S101, performing log fusion on the cloud resource host machine log, virtual machine log, bastion machine log and monitoring camera equipment log;
[0053] Step S102, based on the cloud resource host machine log and the virtual machine log, allocate the resources of the participants;
[0054] Step S103, based on the log of the bastion machine and the log of the monitoring camera equipment, it is judged whether the participants have illegal operations or malicious operations;
[0055] Wherein step S102 comprises the following steps:
[0056] Step S102-1, based on the cloud resource host machine log and the virtual machine ...
Embodiment 2
[0072] On the basis of embodiment 1, when judging whether the resource ratio of the participant is outside the first threshold range, it is judged whether the resource ratio of the participant is within the second threshold range; the second threshold a range greater than said first threshold range;
[0073] If not, perform a second resource allocation on the resources of the participants;
[0074] When it is judged that the resource proportion of the participant exceeds the first threshold range or the second threshold range, an early warning display is performed by issuing an alarm.
[0075] The working principle of the above technical solution is: the solution adopted in this embodiment is to judge whether the resource ratio of the participant is within the second threshold range when judging whether the resource ratio of the participant is outside the first threshold range within; the second threshold range is greater than the first threshold range; if not, perform a seco...
Embodiment 3
[0078] On the basis of Embodiment 1, the first resource allocation of the resources of the participants includes:
[0079] When the resource ratio of the participant reaches the maximum value of the first threshold range, the resource allocation of the participant is increased; the increase of the resource allocation of the participant includes a combination of one or more of the following situations: Improve the resource allocation of CPU utilization, improve the resource allocation of memory, and improve the resource allocation of storage space;
[0080] When the resource ratio of the participant is lower than the minimum value of the first threshold range, reduce the resource allocation of the participant; the reduction of the resource ratio of the participant includes reducing the CPU utilization of the participant resource allocation.
[0081] The working principle of the above technical solution is: the solution adopted in this embodiment is to allocate the resources of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com