Self-adaptive elastic tracking control method and system with spoofing attack
A technology of deception attack and tracking control, applied in the field of information security, which can solve the problems of unavailability of system state, difficulty in tracking, and destruction of system state.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
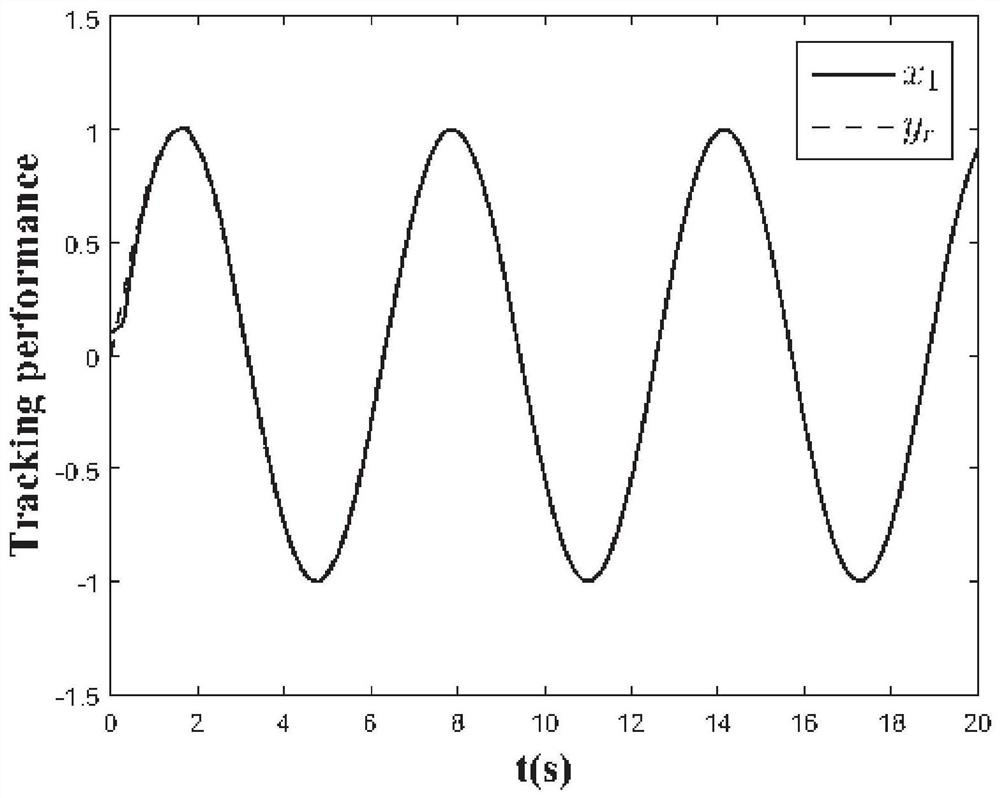
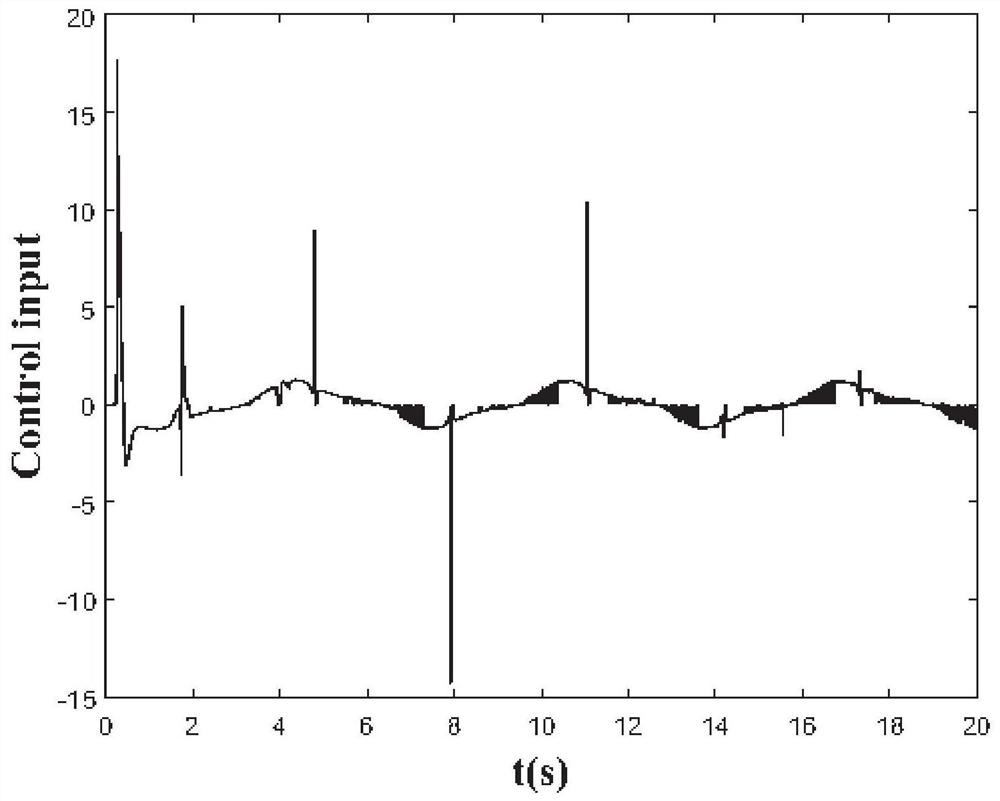
[0040] Such as figure 1 As shown, an adaptive elastic tracking control method with spoofing attack, including:
[0041] Obtain the relationship between the system state before the spoofing attack and the system state after the spoofing attack;
[0042] Construct a virtual controller and an actual controller according to the obtained system state relationship;
[0043] Build adaptive elastic tracking controllers using virtual controllers and real controllers;
[0044] Stable tracking of the target signal is achieved through an adaptive elastic tracking controller;
[0045] Among them, the adaptive elastic tracking controller is constructed by using the virtual controller and the actual controller, which is realized through the nonlinear cyber-physical system based on Nussbaum's spoofing attack.
[0046] Further, said obtaining the relationship between the system state before the spoofing attack and the system state after the spoofing attack includes constructing a model of t...
Embodiment approach
[0061] As one or more implementation manners, the constructing the nonlinear model of the cyber-physical system subjected to spoofing attack includes: considering the influence of the system state and the attack gain caused by the spoofing attack on constructing the nonlinear model of the cyber-physical system.
[0062] As one or more implementations, the introduction of a new Nussbaum technology and obtaining the basis for inferring that the system reaches global bounding includes: considering the needs of the present invention, selecting and constructing the correct Nussbaum technology and inferring the variables in the system according to this theorem Is there a bound.
[0063] As one or more implementations, the introduction of a new coordinate transformation includes: designing a new coordinate transformation, which is different from the traditional coordinate transformation, successfully avoiding the disadvantage that the unattacked state cannot be obtained, using The co...
Embodiment 2
[0165] An adaptive elastic tracking control system with spoofing attack, comprising:
[0166] The state acquisition module is configured to obtain the relationship between the system state before the spoofing attack and the system state after the spoofing attack;
[0167] a controller module configured to construct a virtual controller and an actual controller according to the obtained system state relationship;
[0168] an adaptive module configured to construct an adaptive elastic tracking controller using the virtual controller and the actual controller;
[0169] The signal tracking module is configured to realize stable tracking of the target signal through an adaptive elastic tracking controller;
[0170] Among them, the adaptive elastic tracking controller is constructed by using the virtual controller and the actual controller, and Tongnuo is based on Nussbaum's nonlinear cyber-physical system with deception attack.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com